Auto Scale Solution for the Threat Defense Virtual ASA Virtual on AWS
The following sections describe how the components of the auto scale solution work for the ASA virtual on AWS.
Overview
Cisco provides CloudFormation Templates and scripts for deploying an auto-scaling group of ASA virtual firewalls using several AWS services, including Lambda, auto scaling groups, Elastic Load Balancing (ELB), Amazon S3 Buckets, SNS, and CloudWatch.
The ASA virtual auto scale in AWS is a complete serverless implementation (i.e. no helper VMs involved in the automation of this feature) that adds horizontal auto scaling capability to ASA virtual instances in the AWS environment. Starting from version 6.4, the auto scale solution is supported on managed by management center.
The ASA virtual auto scale solution is a CloudFormation template-based deployment that provides:
-
Completely automated configuration automatically applied to scaled-out ASA virtual instances.
-
Support for Load Balancers and multi-availability zones.
-
Support for enabling and disabling the auto scale feature.
Auto Scale using Sandwich Topology Use Case
The Use Case for this ASA virtual AWS auto scale Solution is shown in the use case diagram. Because the AWS Load Balancer allows only Inbound-initiated connections, only externally generated traffic is allowed to pass inside via the ASA virtual firewall.
 Note |
Secured ports need an SSL/TLS certificate, as described SSL Server Certificate in the Prerequisites. |
The Internet-facing load balancer can be a Network Load Balancer or an Application Load Balancer. All of the AWS requirements and conditions hold true for either case. As indicated in the Use Case diagram, the right side of the dotted line is deployed via the ASA virtual templates. The left side is completely user-defined.
 Note |
Application-initiated outbound traffic will not go through the ASA virtual. |
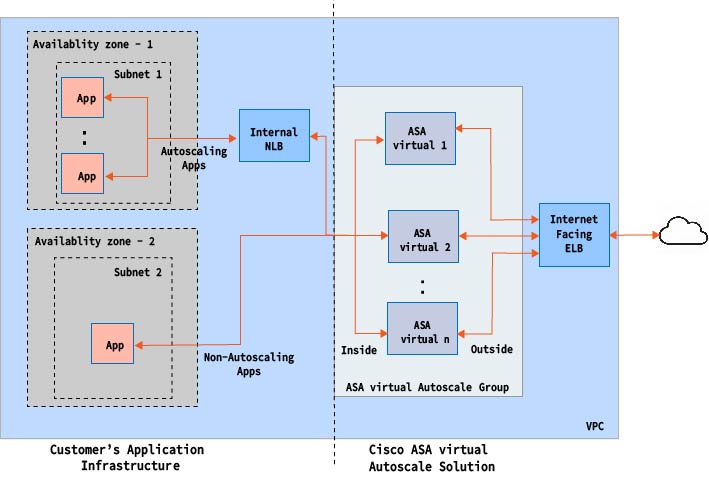
Port-based bifurcation for traffic is possible. This can be achieved via NAT rules. For example, traffic on Internet-facing LB DNS, Port: 80 can be routed to Application-1; Port: 88 traffic can be routed to Application-2.
Auto Scale Using AWS Gateway Load Balancer Use Case
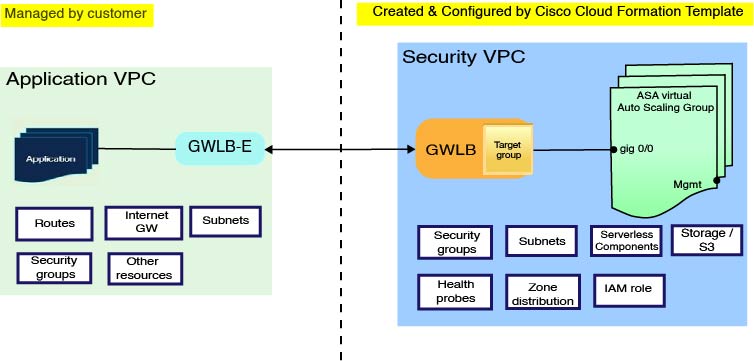
The use case for the ASA virtual AWS Gateway Load Balancer (GWLB) Auto Scale Solution is shown in the use case diagram. The AWS GWLB allows both Inbound and Outbound connections, hence both internally and externally generated traffic is allowed to pass inside via the Cisco ASA virtual firewall.
The Internet-facing load balancer can be a AWS Gateway Load Balancer Endpoint (GWLBe). The GWLBe sends traffic to the GWLB and then to ASA virtual for inspection. All the AWS requirements and conditions hold true for either case. As indicated in the Use Case diagram, the right side of the dotted line is ASA virtual GWLB Autoscale solution deployed via the ASA virtual templates. The left side is completely user-defined.
 Note |
Application-initiated outbound traffic will not go through the ASA virtual. |
How the Auto Scale Solution Works
To scale the ASA virtual instances in and out, an external entity called the Auto Scale Manager monitors metrics, commands an auto scale group to add or delete the ASA virtual instances, and configures the ASA virtual instances.
The Auto Scale Manager is implemented using AWS Serverless architecture and communicates with AWS resources and the ASA virtual. We provide CloudFormation templates to automate the deployment of Auto Scale Manager components. The template also deploys other resources required for complete solution to work.
 Note |
Serverless auto scale scripts are only invoked by CloudWatch events, hence they only run when an instance is launched. |
Auto Scale Solution Components
The following components make up the auto scale solution.
CloudFormation Template
The CloudFormation template is used to deploy resources required by auto scale solution in AWS. The template consists of:
-
Auto Scale Group, Load Balancer, Security Groups, and other miscellaneous components.
-
The template takes user input to customize the deployment.

Note
The template has limitations in validating user input, hence it is the user’s responsibility to validate input during deployment.
Lambda Functions
The auto scale solution is a set of Lambda functions developed in Python, which gets triggered from Lifecycle hooks, SNS, CloudWatch event/alarm events. The basic functionality includes:
-
Add/Remove Gig0/0, and Gig 0/1 interfaces to instance.
-
Register Gig0/1 interface to Load Balancer’s Target Groups.
-
Configure and deploy a new ASA virtual with the ASA configuration file.
Lambda Functions are delivered to customer in the form of a Python package.
Lifecycle Hooks
-
Lifecycle hooks are used to get lifecycle change notification about an instance.
-
In the case of instance launch, a Lifecycle hook is used to trigger a Lambda function which can add interfaces to an ASA virtual instance, and register outside interface IPs to target groups.
-
In the case of instance termination, a Lifecycle hook is used to trigger a Lambda function to deregister an ASA virtual instance from the target group.
Simple Notification Service (SNS)
-
Simple Notification Service (SNS) from AWS is used to generate events.
-
Due to the limitation that there is no suitable orchestrator for Serverless Lambda functions in AWS, the solution uses SNS as a kind of function chaining to orchestrate Lambda functions based on events.
 Feedback
Feedback