Catalyst IW Access Points running in URWB mode support configuration from Cisco IoT Operations Dashboard (IoT OD) or using
local management interfaces. An access point (AP) with no configuration defaults to provisioning mode, which allows the initial
configuration to be sent to the access point from IoT OD.
Provisioning mode is a special mode where the AP attempts to request network configuration using dynamic host configuration
protocol (DHCP) and connect to IoT OD. If network connectivity exists, the AP connects to IoT OD. If there is no network connectivity,
the AP can be configured locally using the GUI or CLI, accessible using the console port or SSH.

Note
|
Use these default credentials to log into either the GUI or CLI:
-
Username: Cisco
-
Password: Cisco
|
The DHCP server assigns a default gateway and domain name system (DNS) server. IoT OD uses DNS geo-location to direct AP in
the United States to the US cluster. Other locations are directed to the EU cluster. Ensure your IoT OD organization is configured
to the correct cluster.
DHCP is only used in provisioning mode. A static IP address must be assigned for normal operation. If DHCP is unavailable
and configuration through IoT OD is required, the IP address, subnet, default gateway, and DNS can be manually configured.

Note
|
When the device is in provisioning mode, the AP attempts to get an IP address from a DHCP server. If the device fails to receive
an IP address through DHCP, the AP reverts to a fallback IP address of 192.168.0.10/24.
|
If the device is in provisioning mode, the device configurator interface is shown:
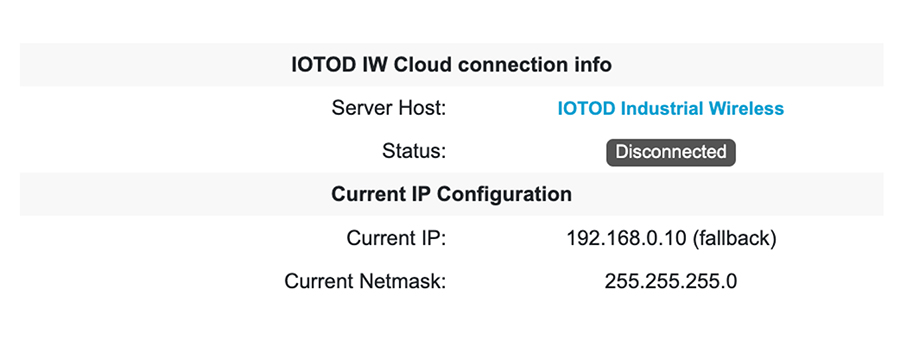

The device’s status and LEDs blink continuously and LEDs repeat this cycle until the device either enters a fallback condition,
or enters Online, or Offline mode. To know more about LED status, see LED Pattern for Catalyst IW9165 or LED Pattern for Catalyst IW9167.

Note
|
DHCP is used only in provisioning mode. A static IP address must be assigned for normal operation.
|
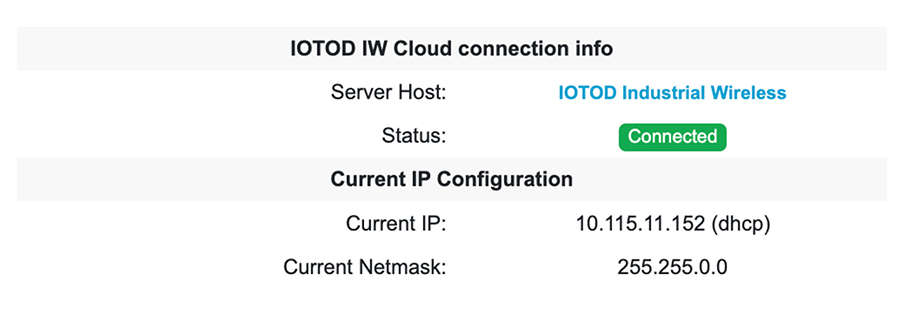
Ensure that the device is connected to a network that supports DHCP. If the connection to IoT OD is successful, the cloud
connection info status is shown as Connected.
To configure the fallback address, use the following CLI command:

Note
|
In the provisioning mode, the IP, netmask, default gateway, primary DNS, and secondary DNS configuration (IP command) are
allowed.
|
Device# configure ip address ipv4 [ static IP address [ static netmask [ IP address of default gateway [ dns1 ip [ dns2 ip ] ] ] ] ]
For example:
Device# configure ip address ipv4 static 192.168.10.2 255.255.255.0 192.168.10.1 192.168.10.200 192.168.10.201
The device sets the fallback address (192.168.0.10 by default) or the configured IP address automatically if it does not receive
an address from the DHCP server. If the device fails to connect to IoT OD IW, verify the following to reach IoT OD IW:
-
Check if the ethernet cable leading to the device is connected correctly.
-
Check if the local DNS server can fix the IP address of IoT OD IW cloud server and if the address can be reached.
-
Check if access point uses an outbound HTTPS connection on tcp/443 for the following domains:
-
device.ciscoiot.com
-
us.ciscoiot.com
-
eu.ciscoiot.com
-
If IoT OD IW is still offline, perform a local (offline) configuration using the device's configurator interface.
If the device fails to connect to the network in provisioning mode, follow these steps:
-
Enter alternative Local IP, Local Netmask, Default Gateway, Local Dns 1, and Local Dns 2 values as needed, using IoT OD IW image and click the Save fallback IP.
A reboot confirmation pop-up appears: 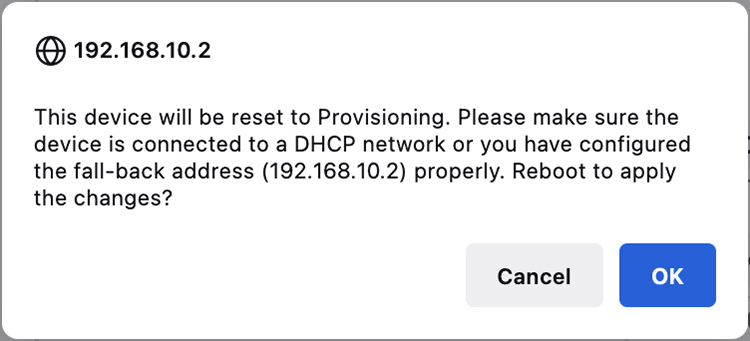
-
Click OK or Reset to go back to IoT OD IW and adjust the settings.
-
Once you click OK, the device reboots and remains in provisioning mode.
-
The device attempts to connect to the network using the new connection values.
-
If the device fails to connect to the network using the DHCP settings, IoT OD IW Cloud connection
Status is shows as Disconnected.

-
To verify if the device is in provisioning mode and not connected to IoT OD, use the following CLI command:
Device#show iotod-iw status
IOTOD IW mode: Provisioning
Status: Disconnected
The following CLI example shows that the device is in provisioning mode and retrieved the IP address from the DHCP server:Device#show ip
IP: 192.168.0.10
Network: 255.255.255.0
Gateway:
Nameservers:
DHCP Address (PROVISIONING Mode):
IP: 10.0.0.2
Network: 255.255.255.0
Gateway: 10.0.0.1
Nameservers: 8.8.8.8
Fallback Address (PROVISIONING Mode):
IP: 169.254.201.72
Network: 255.255.0.0
The following CLI example shows the device in provisioning mode fails to retrieve the IP address from the DHCP server and
using the default fallback IP address 192.168.0.10:Device#show ip
IP: 192.168.0.10
Network: 255.255.255.0
Gateway:
Nameservers:
DHCP Address (PROVISIONING Mode):
IP: 192.168.0.10
Network: 255.255.255.0
Gateway:
Nameservers: 127.0.0.1
Fallback Address (PROVISIONING Mode):
IP: 169.254.201.72
Network: 255.255.0.0










 Feedback
Feedback