About Network Malware Protection and File Policies
To detect and block malware, use file policies. You can also use file policies to detect and control traffic by file type.
Advanced Malware Protection (AMP) for Firepower can detect, capture, track, analyze, log, and optionally block the transmission of malware in network traffic. In the Secure Firewall Management Center web interface, this feature is called malware defense, formerly called AMP for Firepower. Advanced Malware Protection identifies malware using managed devices deployed inline and threat data from the Cisco cloud.
You associate file policies with access control rules that handle network traffic as part of your overall access control configuration.
When the system detects malware on your network, it generates file and malware events. To analyze file and malware event data, see the File/Malware Events and Network File Trajectory chapter in the Cisco Secure Firewall Management Center Administration Guide .
File Policies
A file policy is a set of configurations that the system uses to perform malware protection and file control, as part of your overall access control configuration. This association ensures that before the system passes a file in traffic that matches an access control rule’s conditions, it first inspects the file. Consider the following diagram of a simple access control policy in an inline deployment.
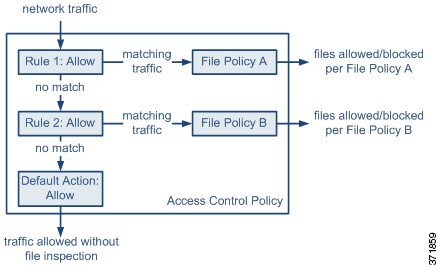
The policy has two access control rules, both of which use the Allow action and are associated with file policies. The policy’s default action is also to allow traffic, but without file policy inspection. In this scenario, traffic is handled as follows:
-
Traffic that matches
Rule 1is inspected byFile Policy A. -
Traffic that does not match
Rule 1is evaluated againstRule 2. Traffic that matchesRule 2is inspected byFile Policy B. -
Traffic that does not match either rule is allowed; you cannot associate a file policy with the default action.
By associating different file policies with different access control rules, you have granular control over how you identify and block files transmitted on your network.



 )
)


 )
) Feedback
Feedback