Information About Service Insertion
Service insertion, also known as service chaining, refers to placing one or more network or security services into the path of specific data traffic within the Cisco Catalyst SD-WAN overlay fabric. These services are defined in a service chain, which is a set of services that traffic routes through. The traffic is routed according to service chain actions that you configure for a data policy.
A service chain can be in any device, and can be used in any topology, including full mesh, hub-spoke, and Cisco Catalyst SD-WAN Multi-Region Fabric (MRF).
Cisco Catalyst SD-WAN service chaining is flexible, fully automated, and can be deployed on a per VPN basis. Service chaining includes the following key feature:
-
Service chaining can be used for overlay, local ingress and egress, inter- and intra-VPN, transit, branch-to-branch, branch-to-internet, branch-to-cloud, and cloud-to-cloud traffic
-
Automatic forwarding of traffic through all services in a chain
-
Services attachment methods of IPv4, IPv6, dual stack, and tunneled
-
Configurable high availability across instances of a single service
-
Built-in load balancing across instances of a single service, which supports equal cost multipath routing (ECMP) across high availability pairs
-
Advanced service tracking
-
Service chain sharing across multiple user VPNs, which can be different or the same as user traffic VPNS
-
Traffic steering methods using control policy, data policy, interface ACL, and supported match conditions
-
Fall back and restrict behavior
-
Path preference and symmetric routing
-
Security services to and from service transports
-
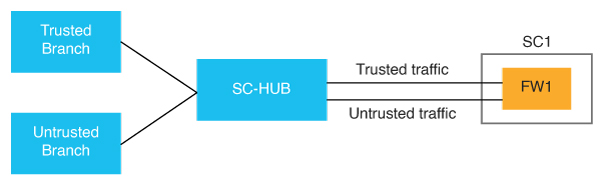
Trusted and untrusted high availability pairs and traffic marking (from Cisco Catalyst SD-WAN Manager Release 20.14.1)
-
Periodic on demand state notifications for serviceability
-
Cisco Catalyst SD-WAN Manager orchestration: Workflow based service chaining and traffic policy configuration
Service Insertion Capabilities
The following table provides information about the capabilities of the service chaining feature in releases before and afterCisco Catalyst SD-WAN Manager Release 20.13.1.
|
Capability |
Releases Before Cisco Cisco Catalyst SD-WAN Manager Release 20.13.1 |
Releases From CiscoCisco Catalyst SD-WAN Manager Release 20.13.1 |
|---|---|---|
|
Multiple services in a chain |
No native support |
Native support |
|
Traffic steering |
Control policy |
Control policy, data policy, interface ACL |
|
Policy binding |
Remote |
Remote and local |
|
Traffic type |
IPv4 |
IPv4, IPv6, dual stack, tunnel |
|
Load balancing |
Across 4 IP addresses that serve as service endpoints |
Across 4 instances of active-backup pairs for every traffic type |
|
High availability |
As provided by load balancing |
Active and backup pairs |
|
Tracking |
To one connection per service instance |
To every connection toward an abstract service |
|
Configurable tracker probes |
Not supported |
All trackers are individually configurable |
|
Behind-the-service tracking |
Not supported |
Supported |
|
Affinity (service routes and data policy) |
Not supported |
Supported |
|
TLOC preference |
Supported |
Supported |
|
Fall back, restrict |
Not supported |
Supported |
|
Tunnel connected services |
Not supported |
Supported |
|
Shared service VPN |
Not supported |
Supported |
|
To and from service transports |
Not supported |
Supported |
|
Trusted and untrusted postures |
Not supported |
Supported from Cisco Catalyst SD-WAN Manager Release 20.14.1 |
|
Periodic and on-demand serviceability |
Not supported |
Supported |
|
Cisco Catalyst SD-WAN Manager orchestration |
Uses feature templates |
Uses the Workflow Library and configuration groups (feature templates are not supported) |
|
Deployment |
On premises |
On premises, cloud, middle mile colocated |
|
Service instance type |
Physical |
Physical or virtual |
Service Insertion Key Concepts and Implementation
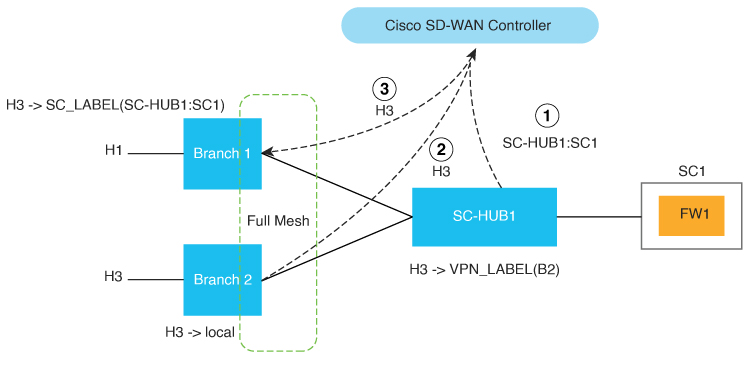
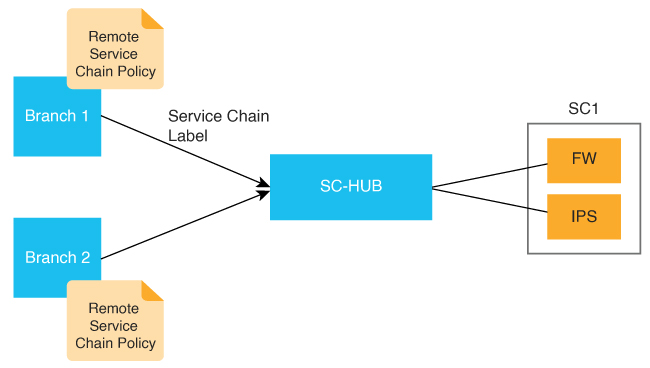
The following figure illustrates the basic concepts of service chaining and the general steps involved in service chain creation and execution.

|
1 |
Services bring up:
|
|
2 |
Service chain configuration and advertising:
|
|
3 |
Service chain policy:
|
|
4 |
Traffic steering:
|
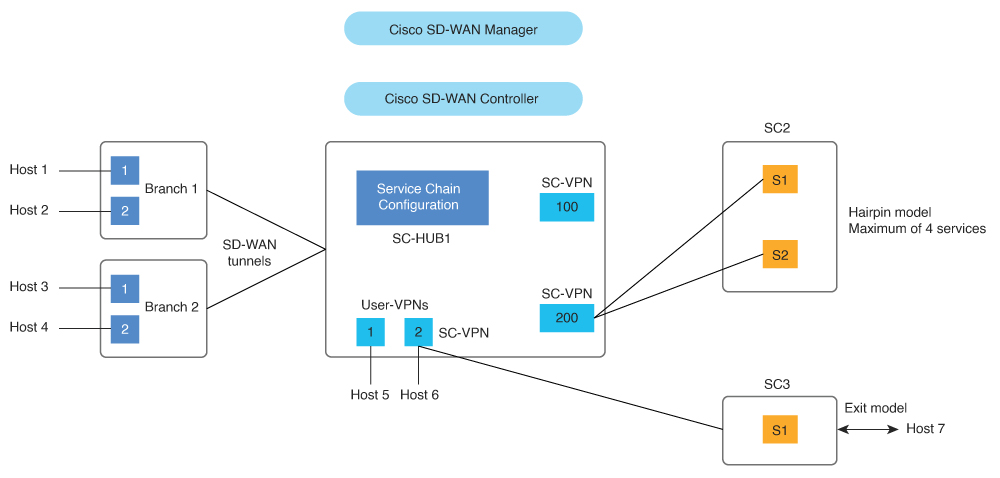
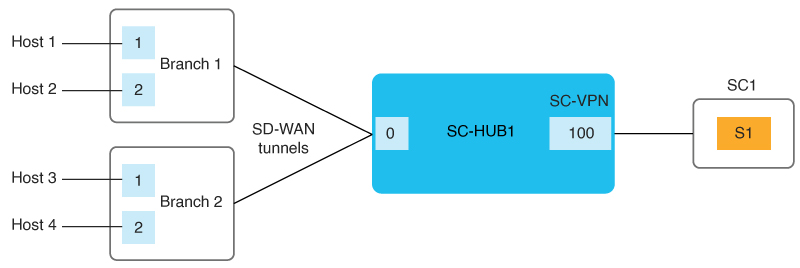
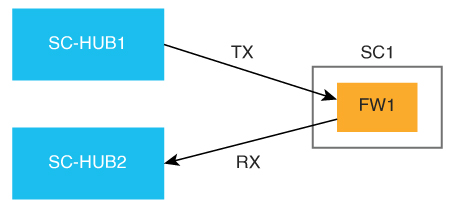
The following figure illustrates the key elements in service insertion. In this figure, SC-HUB1 is the router to which the service chain is attached.
In the hairpin model, traffic is sent by SC-HUB1 to a service in the service chain, and the service returns the traffic to SC-HUB1. SC-HUB1 then either forwards the traffic to the next service in the service chain or to the destination if the traffic is returning from the last service in the service chain.
In the exit Model, traffic is sent by SC-HUB1 to a service in a service chain, and the service forwards the traffic to the destination. Traffic may return from the destination to the service, which returns it to SC-HUB1.





 Feedback
Feedback