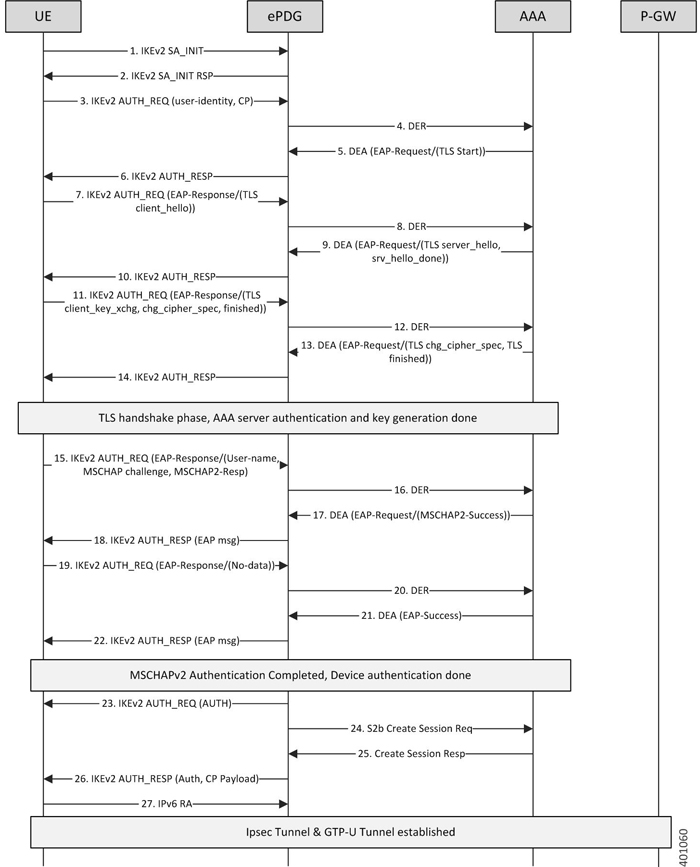
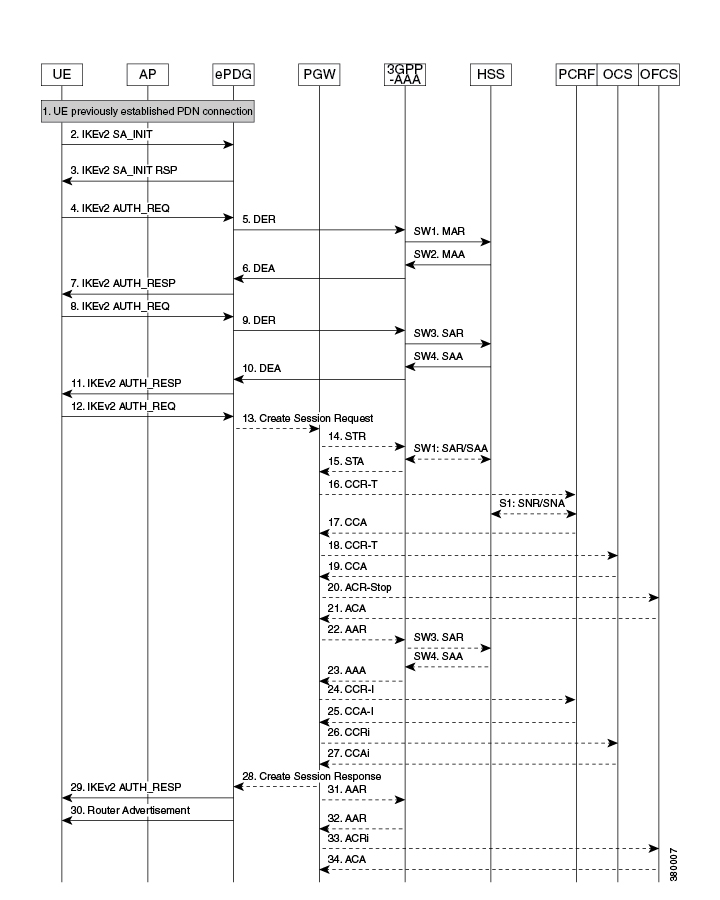
The EAP-TTLS based approach is useful when there is no certificate based infrastructure present for the operator to configure
certificate for each device. Unlike EAP-TLS it enables the device authentication without certificates using customized AVPs.
Here we have defined MSCHAPv2 based authentication mechanism. Here the AAA server needs to provide the key similar to MSK
to ePDG for validating/generating the AUTH payload during IKEv2 xchg. Following diagram shows the call flow for the EAP-TTLS
based authentication:
-
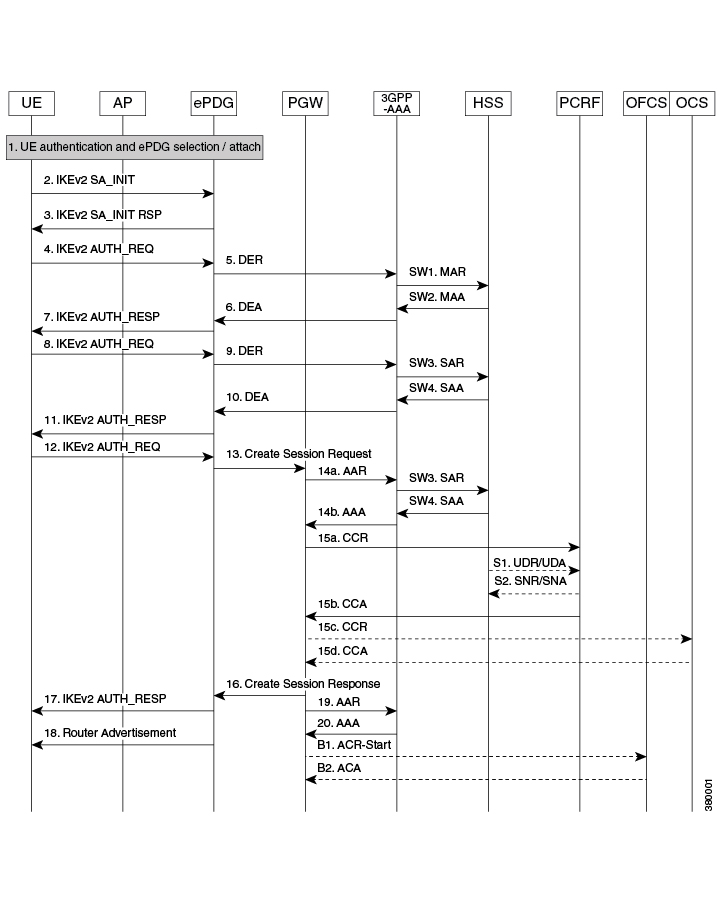
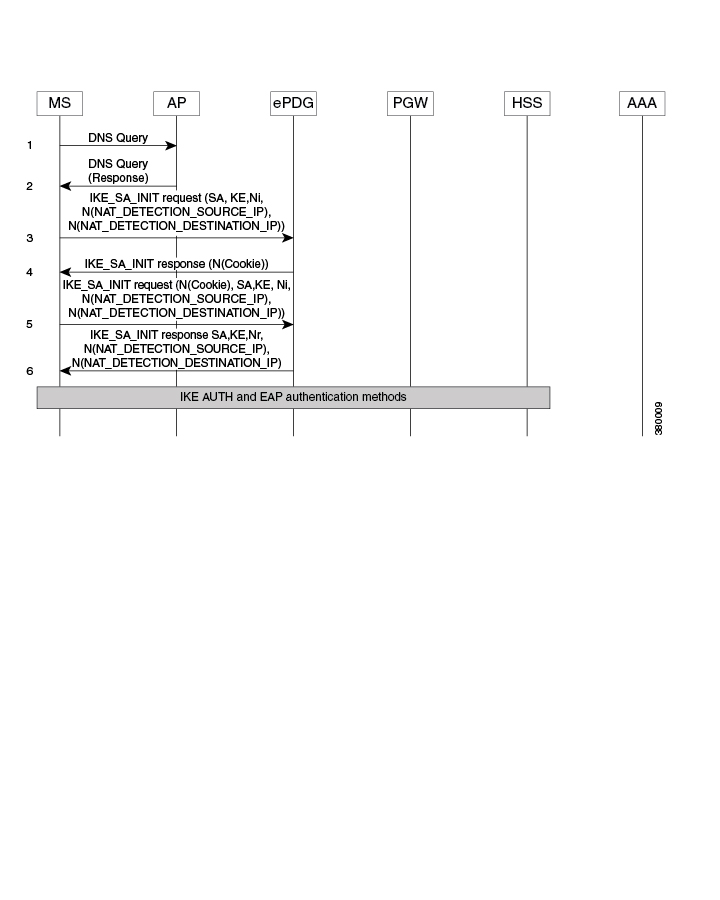
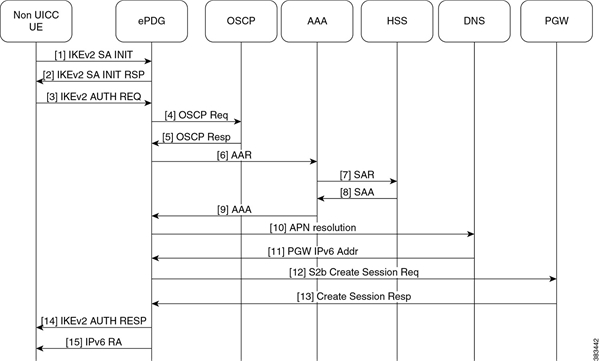
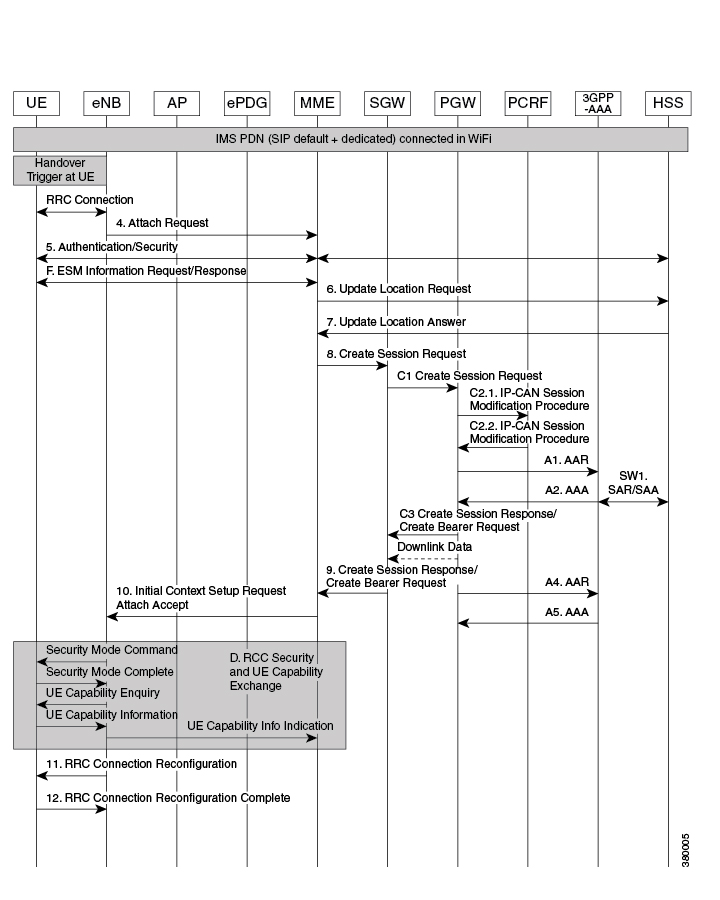
UE ePDG: IKEv2 SA_INIT UE (UICC based) sends IKE_SA_INIT Request (SA, KE, Ni, NAT-DETECTION Notify).
-
ePDG UE: IKEv2 SA_INIT RSP The ePDG responds with an IKE_SA_INIT Response (SA, KE, Nr payloads, NAT-Detection Notify).
-
UE ePDG: IKEv2 AUTH_REQ UE sends IKE_AUTH_REQ (IDi, [CERTREQ], IDr, SA, CP (CFQ_REQUEST (INTERNAL_IP6_ADDRESS, [INTERNAL_IP6_DNS],
[INTERNAL_IP6_PCSCF]), TSi, TSr)). The UE does not include AUTH payload to indicate that it will use the EAP-TTLS method for
authenticating itself to AAA. IDi contains the NAI in the form "A<IMSI> nai.epc.mnc<MNC>.mcc<MCC>.3gppnetwork.org". Per standards
the prefix can be 0/1 indicating EAP-AKA/EAP-SIM now as we shall be indicating to AAA server that use different authentication
method here EAP-TTLS so can indicate using "A". ePDG shall be transparent to received prefix and shall send to AAA server
so that operator is free to use any prefix except the defined ones.
-
ePDG AAA server :DER The ePDG sends the DER (Session-Id, Auth-Application-Id, Origin-Host, Origin-Realm, Destination-Host,
Destination-Realm, Auth-Request-Type(AUTHORIZE_AUTHENTICATE), EAP-Payload, User-Name (NAI), RAT-Type(WLAN), MIP6-Feature-Vector,
Visited-Network-Identifier) message to the 3GPP AAA Server. The EAP-Payload contains the UE identity encoded by ePDG.
-
AAA server ePDG: DEA The 3GPP AAA Server initiates the authentication challenge and responds with DEA (Session-Id, Base AVPs,
Auth-Request-Type and EAP-Payload). The EAP-Payload contains the EAP-TTLS/Start, the Start 'S' bit is set with no data.
-
ePDG UE: IKEv2 AUTH_RESP ePDG sends IKE_AUTH_RESP (IDr, [CERT (X509 CERTIFICATE SIGNATURE)], EAP Payload) The IDr is the identity
of the ePDG and if the UE requests for certificates then CERT is included. The EAP message received from the 3GPP AAA Server
(EAP-Request/Start) is included in order to start the EAP procedure over IKEv2.
-
UE ePDG: IKEv2 AUTH_REQ UE sends IKE_AUTH_REQ (EAP payload) containing the TLS client hello handshake message.
-
ePDG AAA server: DER The ePDG sends the DER (Session-Id, Auth-Application-Id, Origin-Host, Origin-Realm, Destination-Host,
Destination-Realm, Auth-Request-Type(AUTHORIZE_AUTHENTICATE), EAP-Payload, User-Name (NAI), RAT-Type(WLAN), MIP6-Feature-Vector,
Visited-Network-Identifier) message to the 3GPP AAA Server. The EAP-Payload shall contain the TLS client hello handshake message.
-
AAA server ePDG: DEA The 3GPP AAA Server initiates the authentication challenge and responds with DEA (Session-Id, Base AVPs,
Auth-Request-Type and EAP-Payload). The AAA server will then respond with an EAP-Request packet with EAP-Type=EAP-TTLS. The
data field of this packet will encapsulate one or more TLS records. These will contain a TLS server_hello handshake message,
possibly followed by TLS certificate, server_key_exchange, server_hello_done and/or finished handshake messages, and/or a
TLS change_cipher_spec message.
-
ePDG UE: IKEv2 AUTH_RESP ePDG sends IKE_AUTH_RESP (EAP Payload) The EAP payload contains the TLS message as received from
the AAA server.
-
UE ePDG: IKEv2 AUTH_REQ The UE sends EAP message in IKE_AUTH Request (EAP). The data field of this packet MUST encapsulate
one or more TLS records containing a TLS client_key_exchange, change_cipher_spec, and finished messages.
-
ePDG AAA server :DER The ePDG sends the DER (Session-Id, Auth-Application-Id, Origin-Host,Origin-Realm, Destination-Host,
Destination-Realm, Auth-Request-Type(AUTHORIZE_AUTHENTICATE), EAP-Payload) message to the3GPP AAA Server. The EAP-Payload
contains the message as sent by UE.
-
AAA server ePDG: DEA The 3GPP AAA Server on successful authentication responds with DEA (Session-Id, Base AVPs, Auth-Request-Type
and EAP-Payload) where EAP-Payload does contain the TLS finished message.
-
ePDG UE: IKEv2 AUTH_RESP ePDG sends IKE_AUTH_RESP (EAP Payload). The EAP payload contains the TLS message as received from
the AAA server. This stage the first phase of TTLS is done completing the TLS handshake and AAA server is authenticated by
device and keys are generated to secure subsequent message handling.
-
UE ePDG: IKEv2 AUTH_REQ The UE sends EAP message in IKE_AUTH Request (EAP) with user-name, MS-CHAP2- Response, MS-CHAP Challenge
AVPs.
-
ePDG AAA server: DER The ePDG sends the DER (Session-Id, Auth-Application-Id, Origin-Host, Origin-Realm, Destination-Host,
Destination-Realm, Auth-Request-Type(AUTHORIZE_AUTHENTICATE), EAP-Payload) message to the3GPP AAA Server. The EAP-Payload
contains the message as sent by UE.
-
AAA server ePDG: DEA The 3GPP AAA Server on successful authentication responds with DEA (Session-Id, Base AVPs, Auth-Request-Type
and EAP-Payload), Upon receipt of these AVPs from the UE, the AAA server MUST verify that the value of the MS-CHAP-Challenge
AVP and the value of the Ident in the client's MS-CHAP2-Response AVP are equal to the values generated as challenge material.
If either item does not match exactly, the AAA server MUST reject the UE. In success case, AAA encodes the MS-CHAP2-Success
attribute.
-
ePDG UE: IKEv2 AUTH_RESP ePDG sends IKE_AUTH_RESP (EAP Payload). The EAP payload contains the EAP-TTLS message as received
from the AAA server.
-
UE ePDG: IKEv2 AUTH_REQ The UE sends IKE_AUTH Request (EAP) with no data. Upon receipt of the MS-CHAP2-Success AVP, the UE
is able to authenticate the AAA. If the authentication succeeds, the UE sends an EAP-TTLS packet to the TTLS server containing
no data (that is, with a zero-length Data field). Upon receipt of the empty EAP-TTLS packet from the client, the TTLS server
considers the MS-CHAP-V2 authentication to have succeeded.
-
ePDG AAA server :DER The ePDG sends the DER (Session-Id, Auth-Application-Id, Origin-Host,Origin-Realm, Destination-Host,
Destination-Realm, Auth-Request-Type(AUTHORIZE_AUTHENTICATE), EAP-Payload) message to the 3GPP AAA Server. The EAP-Payload
contains the message as sent by UE.
-
AAA server ePDG: DEA The 3GPP AAA Server sends an EAP success (Session-Id, Auth-Application-Id: 16777264, Result-Code, Origin-Host,
Origin-Realm, Auth-Request-Type(AUTHORIZE_AUTHENTICATE), EAP-Payload User-Name(0<IMSI>mnc<mnc val>.mcc<mcc val>.pub.3gppnetwork.org),
EAP-Master-Session-Key, APN-Configuration (Context-Identifier, PDN-Type: IPv4v6, Service-Selection (apn name), MIP6-Agent-Info),
Auth-Session-State:STATE_MAINTAINED, Origin-State-Id). At this point mutual authentication is done and device is authorized
by AAA server.
-
ePDG UE: IKEv2 AUTH_RESP ePDG sends IKE_AUTH_RESP (EAP Payload) The EAP payload contains the TLS message as received from
the AAA server.
-
UE ePDG: IKEv2 AUTH_REQ UE sends IKE_AUTH request (AUTH) The UE takes its own copy of the MSK asinput to generate the AUTH
parameter to authenticate the first IKE_SA_INITmessage.
-
ePDG PGW: S2b Create Session Req ePDG sends Create Session Request (IMSI, [MSISDN],Serving Network, RAT Type (WLAN), Indication
Flags, Sender F-TEID for C-plane, APN, Selection Mode, PAA, APN-AMBR, [APCO], Bearer Contexts(), [Recovery], [Private IE (P-CSCF)]).
Selection Mode is set to "MS or network provided APN subscribed verified". The PGW performs the necessary interactions with
3GPP-AAA, PCRF and OCS/OFCS. ePDG shall set the HO in Indication flags IE and also the preserved IP address as received from
UE in PAA IE.
-
PGW ePDG: Create Session Resp The PGW allocates the requested IP address session and responds back to the ePDG with a Create
Session Response (Cause, PGW S2b F-TEID, PAA, [APN-AMBR],APCO, Bearer Contexts Created (EPS Bearer ID, Cause, [TFT], S2b-U
PGW F-TEID, Bearer Level QoS), [Recovery], [Private IE (P-CSCF)]) message.
-
ePDG UE: IKEv2 AUTH_RESP ePDG sends IKE_AUTH_RESP (AUTH, CP, SA, CFG_REPLY([INTERNAL_IP4_ADDRESS], [INTERNAL_IP4_NETMASK],[INTERNAL_IP4_DNS],
INTERNAL_IP6_ADDRESS,INTERNAL_IP6_SUBNET, INTERNAL_IP6_DNS, [P-CSCF]) TSi, TSr) At this stage the ePDG has completed the ipsec
SA and tunnel setup and also GTP-U tunnel setup thus completing the data path. The IP address provided by P-GW is communicated
to UE.
-
ePDG UE: IPv6 RA The assumption is that the IP stack needs the RA to initialize the address.




 Feedback
Feedback