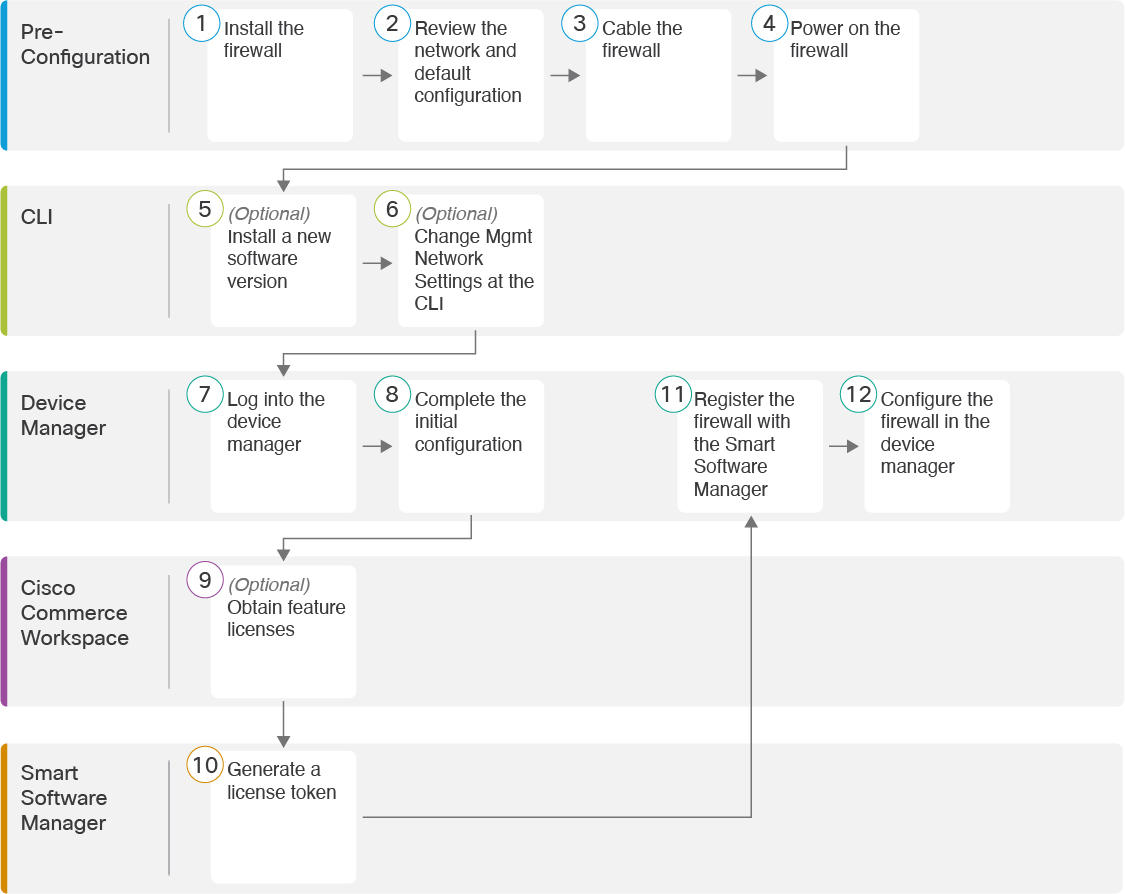
End-to-End Tasks
See the following tasks to deploy the threat defense with the device manager.
|
|
Pre-Configuration |
Install the firewall. See the hardware installation guide. |
|
|
Pre-Configuration |
|
|
|
Pre-Configuration |
|
|
|
Pre-Configuration |
|
|
|
CLI |
|
|
|
CLI |
|
|
|
Device Manager |
|
|
|
Device Manager |
|
|
|
Cisco Commerce Workspace |
(Optional) Obtain feature licenses (Configure Licensing). |
|
|
Smart Software Manager |
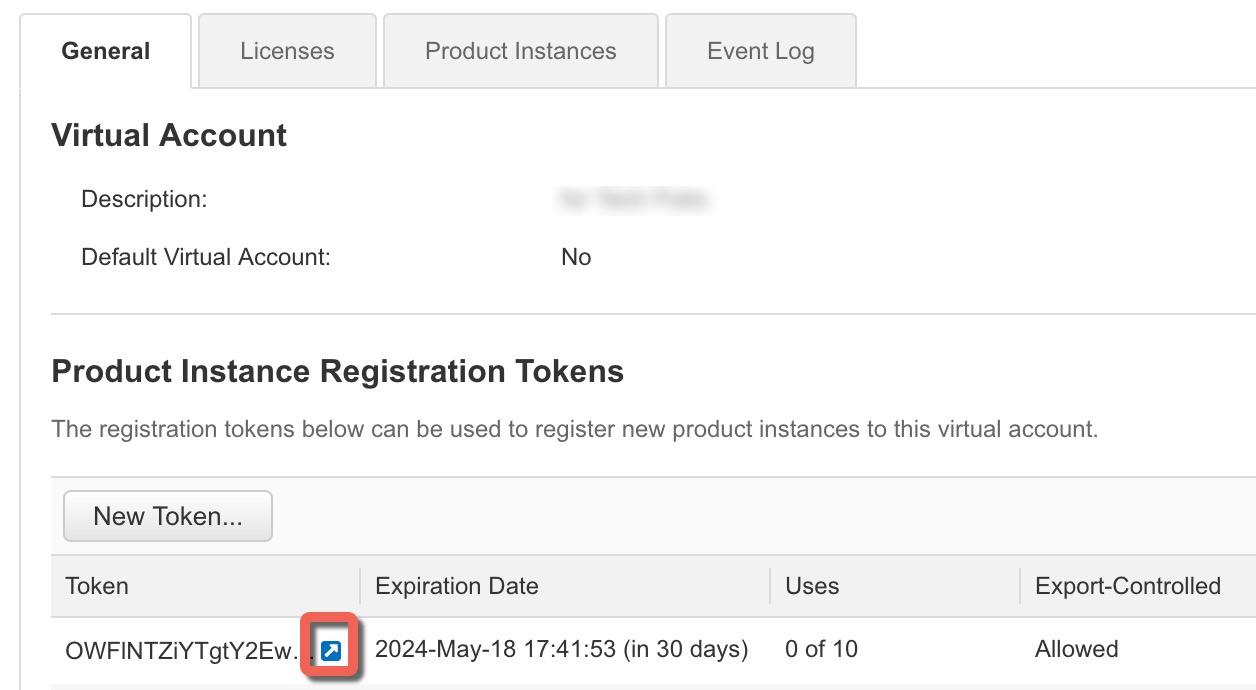
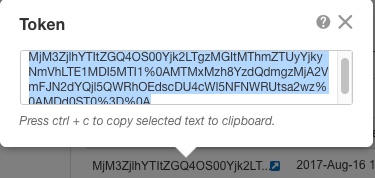
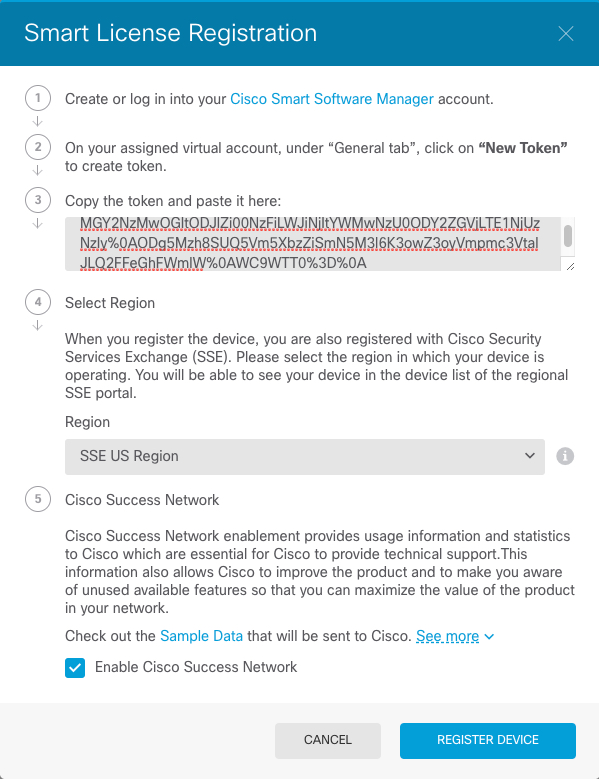
Generate a license token (Configure Licensing). |
|
|
Device Manager |
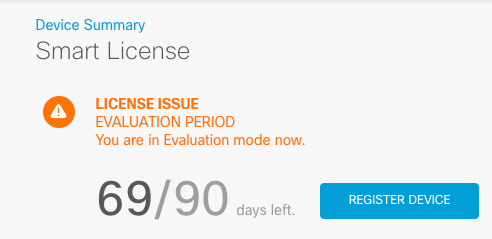
Register the device with the Smart Licensing Server (Configure Licensing). |
|
|
Device Manager |

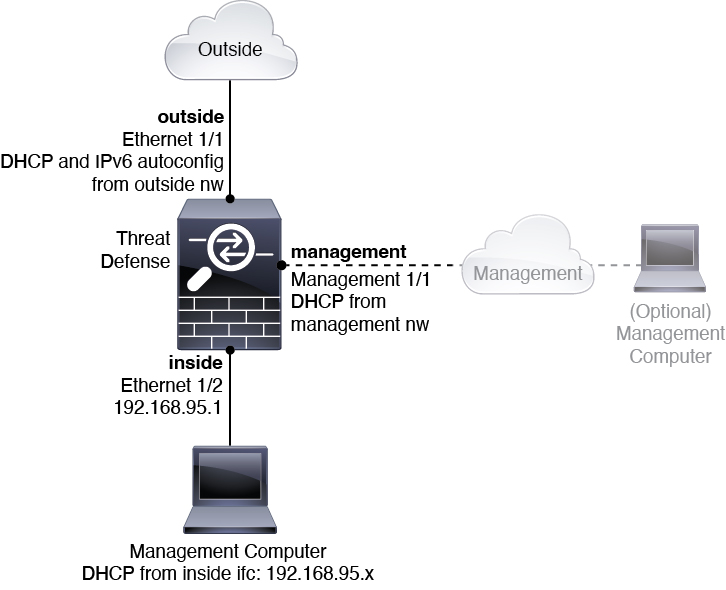
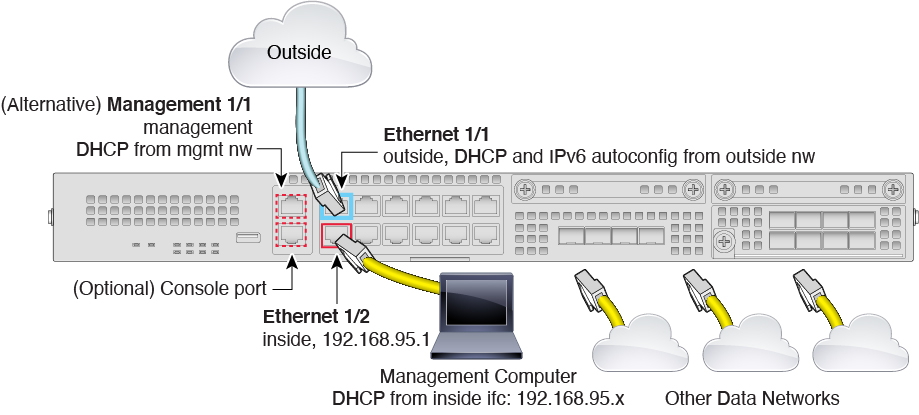


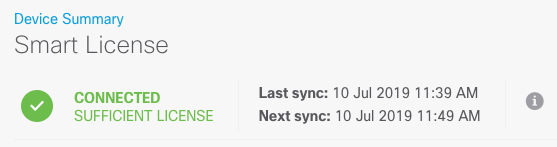


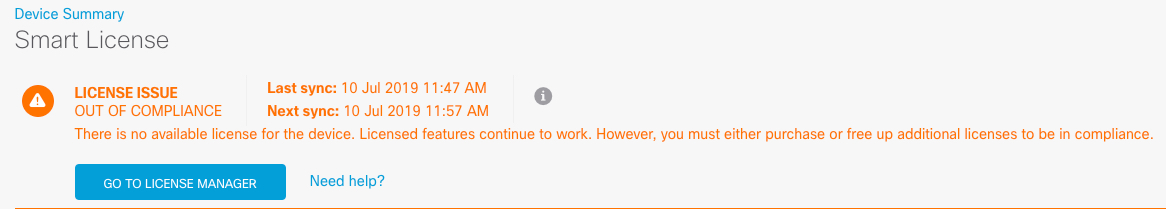
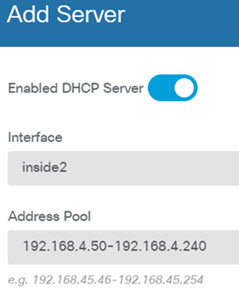
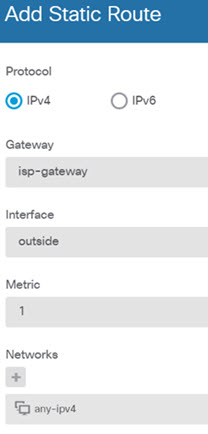
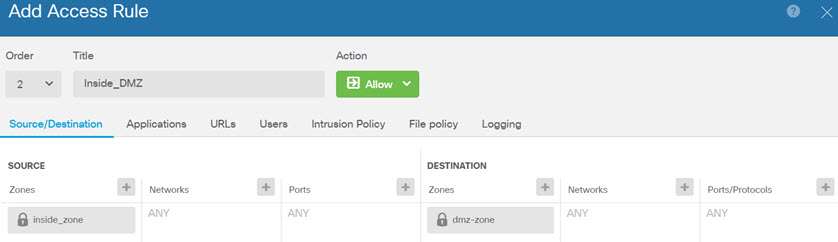
 ) for each interface to set the mode and define the IP address and other
settings.
) for each interface to set the mode and define the IP address and other
settings.
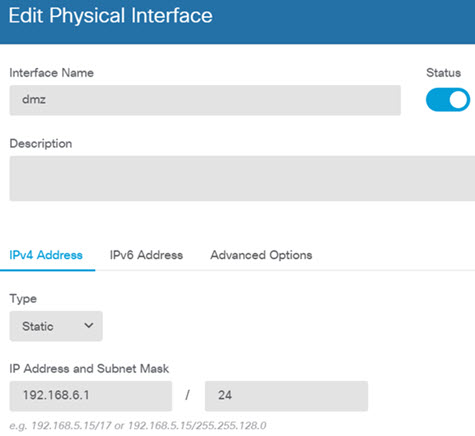

 ), to deploy your changes to the device.
), to deploy your changes to the device.
 Feedback
Feedback