Update ASA Connection Credentials in Security Cloud Control
In the process of onboarding an ASA, you entered the username and password Security Cloud Control must use to connect to the device. If those credentials are changed on the device, use the Update Credentials device action to update those credentials on Security Cloud Control as well. This feature allows you to update the credentials on Security Cloud Control without having to re-onboard the device. The username and password combination you switch to must already exist on the ASA or Authentication, Authorization, and Accounting (AAA) server for that user. This process only affects the Security Cloud Control database; no changes to the ASA configuration are made when using the Update Credentials feature.
Procedure
|
Step 1 |
In the left pane, click . |
||
|
Step 2 |
Click the Devices tab and then click ASA. |
||
|
Step 3 |
Select the ASAs whose connection credentials it is you want to update. You can update the credentials on one or multiple ASAs at once. |
||
|
Step 4 |
In the Device Actions pane, click Update Credentials. |
||
|
Step 5 |
Select the Cloud Connector or the Secure Device Connector (SDC) you use to connect the ASA(s) to Security Cloud Control. |
||
|
Step 6 |
Enter the new username and password you want to use to connect to the ASAs. |
||
|
Step 7 |
After the credentials are changed, Security Cloud Control syncs the device.
|
Move an ASA from one SDC to Another
Security Cloud Control supports the use of more than one SDC per tenant. You can move a managed ASA from one SDC to another using this procedure:
Procedure
|
Step 1 |
In the left pane, click |
|
Step 2 |
Select the ASAs you want to move to the other SDC. |
|
Step 3 |
In the Device Actions pane, click Update Credentials. |
|
Step 4 |
Click the Secure Device Connector button and select the SDC you want to move the device to. |
|
Step 5 |
Enter the administrator username and password you used to onboard the ASA, and click Update. You do not have to deploy these changes to the device. |
 >
>  ) on the corresponding parameter highlights unsaved changes.
) on the corresponding parameter highlights unsaved changes.
 ) highlights parameters that use existing local values from the device.
) highlights parameters that use existing local values from the device.

 , it means that an error has occurred while applying the shared system settings policy to your devices. To troubleshoot the
issue, click the policy on the ASA System Settings page and in the
, it means that an error has occurred while applying the shared system settings policy to your devices. To troubleshoot the
issue, click the policy on the ASA System Settings page and in the  .
.
 ) icon in the right pane.
) icon in the right pane.
 ) button.
) button.
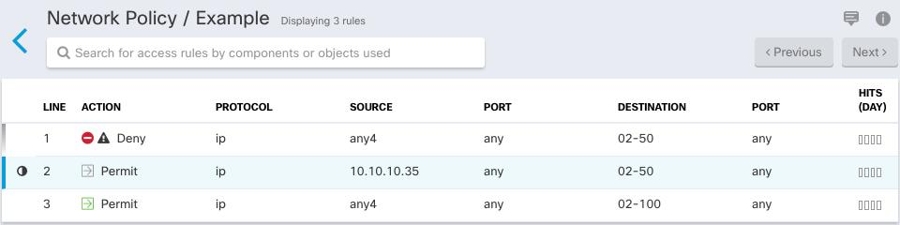
 because it's shadowing another rule in the policy. The rule on line 2 is marked as being shadowed
because it's shadowing another rule in the policy. The rule on line 2 is marked as being shadowed  by another rule in the policy. The action for the rule on line 2 is grayed-out because it's entirely shadowed by another
rule in the policy.
by another rule in the policy. The action for the rule on line 2 is grayed-out because it's entirely shadowed by another
rule in the policy. 
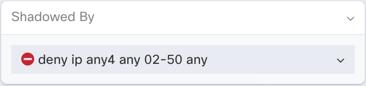

 .
.
 .
.


 to expand the history pane if it is not already expanded.
to expand the history pane if it is not already expanded.
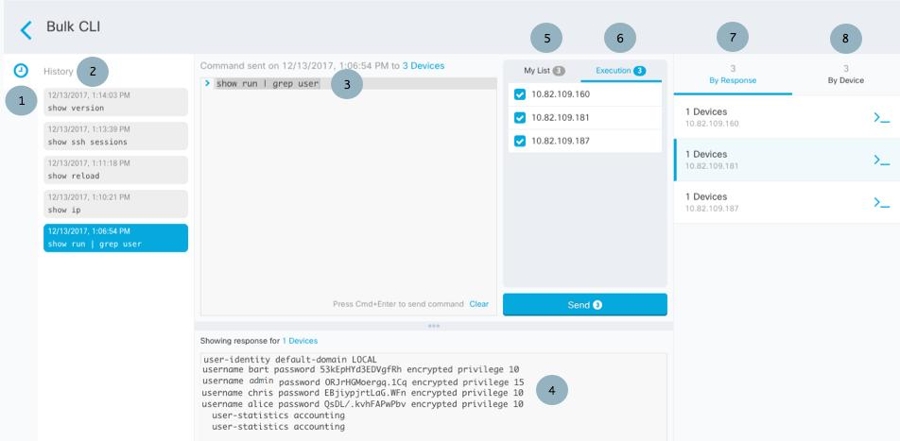
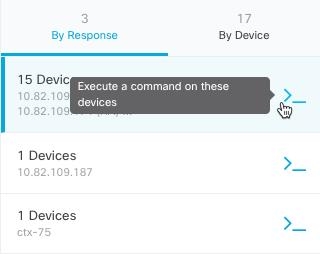


 to see what macros already exist.
to see what macros already exist.
 .
.
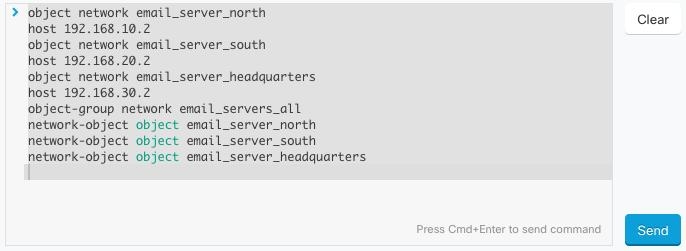
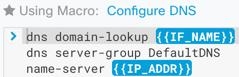
 . The command is now the basis for a new CLI macro.
. The command is now the basis for a new CLI macro.
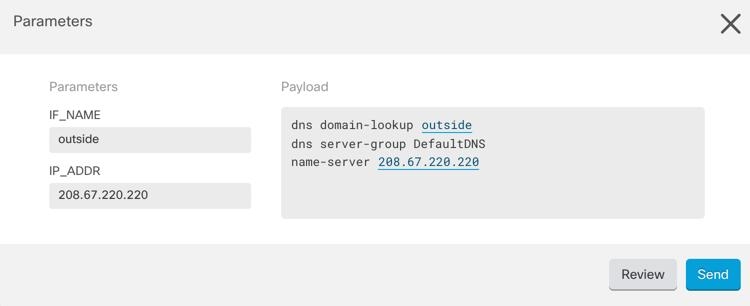

 in the CLI macro label.
in the CLI macro label.

 .
.
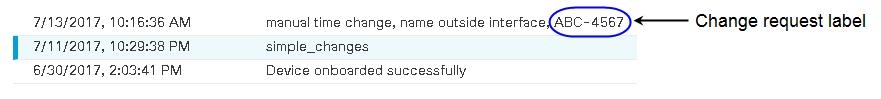
 . The devices affected by these changes show the status "Not Synced" in the Devices and
. The devices affected by these changes show the status "Not Synced" in the Devices and  on the details pane. Review any warnings and click
on the details pane. Review any warnings and click  in the navigation bar to view the results of the bulk deploy.
in the navigation bar to view the results of the bulk deploy.


 Feedback
Feedback