These statistics are available for the cloud router:
-
Ingress packets
-
Egress packets
-
Ingress bytes
-
Egress bytes
The Cisco Cloud Application Policy
Infrastructure Controller (APIC) collects and stores the cloud router statistics by the following granularities:
-
15-minutes
-
1-hour
-
1-month
-
1-year
Collection Mechanism
Each cloud router instance captures and stores the previously mentioned 4-stat values for each physical and tunnel interface.
The Cisco Cloud Application Policy
Infrastructure Controller (APIC) queries the cloud routers for these statistics and maps the response to cloud router statistics on the Cisco Cloud APIC. The statistics query repeats every 5 minutes for as long as the tunnel is up and operational.
Raw Statistics
The raw statistics are stored under 2 Dns:
-
uni/tn-<infraTenant>/ctx-<infraCtx>/region-<infraRegion>/router-<csrname>/to-<ip or user-region>/tunn-<tunnel-id>
-
uni/tn-<userTenant>/ctx-<userCtx>/region-<userRegion>/region-<infraRegion>/router-<csrname>/tunn-<tunnel-id>

Note |
-
The second Dn holder is the statistics as seen from the user endpoints connected to the cloud router. These statistics are
hence flipped (Ingress on the CCR becomes egress on the user region)
-
Not all tunnels have a corresponding user dn. This is only applicable to internal tunnels. External tunnels statistics are
only available on the 1st Dn.
|
In the following figure, internal tunnels are between the user VPC and infra VPC. The infra VPC contains the CCR router. The
user VPC can contain the CCR or VGW router. Cisco Cloud APIC creates these tunnels. As a result, statistics are available for both the infra side and the user side. External tunnels
are between infra VPC and an external IP address. Statistics are only available on the infra side (Dn-1).
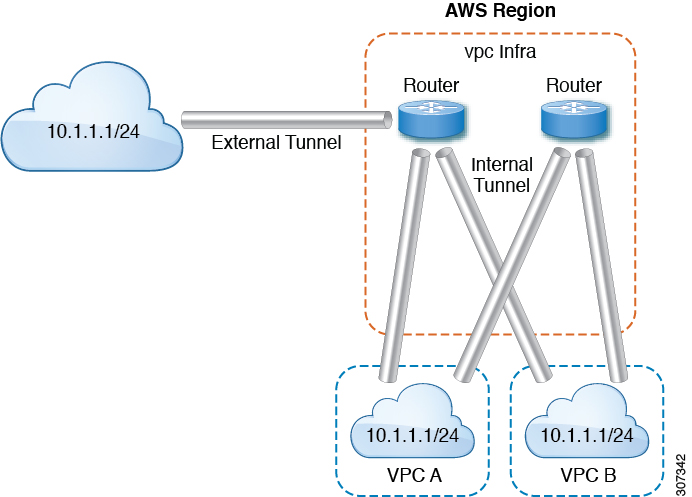
In the logical model diagram, a tenant can be infra or a user tenant. You configure a VRF (or fvCtx) to be inside a tenant (per tenant). A VRF can be within one region or span across multiple regions.

Aggregated Statistics
Statistics are aggregated at each parent level of the DN. For the preceding case, statistics on tunnel, statistics are aggregated
on to the destination IP, cloud router, region, vrf (ctx), and tenant.
For example, if you want to find the egress packets from the infra cloud router to a user region, it is available under uni/tn-<infraTenant>/ctx-<infraCtx>/region-<infraRegion>/router-<csrname>/to-<ip or user-region>/
If you want to get all the packets between user region1 and infra region2, it is available under uni/tn-<userTenant>/ctx-<userCtx>/region-<userRegion>/region-<infraRegion>/
Also, if you want to find statistics per cloudCtxProfile, it is available under uni/tn-<userTenant>/ctx-<userCtx>/region-<userRegion>/ or uni/tn-<infraTenant>/ctx-<infraCtx>/region-<infraRegion>/.
Cloud Router GUI Statistics
In the Cisco Cloud APIC GUI, statistics are visible available under the tenant, VRF, infra region, and cloud context profile.
For Amazon Web Services (AWS) Transit Gateway stats, in the Cloud Context Profile work pane, click AWS Transit Gateway For all other stats, in the Cloud Context Profile work pane, click Endpoints.



 Feedback
Feedback