Before You Start
Deploy and perform initial configuration of the management center. See the Cisco Firepower Management Center 1600, 2600, and 4600 Hardware Installation Guide or Cisco Secure Firewall Management Center Virtual Getting Started Guide.
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Is This Chapter for You?
This chapter explains how to complete the initial configuration of your threat defense and how to register the device to a management center. In a typical deployment on a large network, multiple managed devices are installed on network segments, monitor traffic for analysis, and report to a managing management center, which provides a centralized management console with web interface that you can use to perform administrative, management, analysis, and reporting tasks.
For networks that include only a single device or just a few, where you do not need to use a high-powered multiple-device manager like the management center, you can use the integrated device manager. Use the device manager web-based device setup wizard to configure the basic features of the software that are most commonly used for small network deployments.
The Cisco ISA 3000 can run either the threat defense software or ASA software. Switching between threat defense and ASA requires you to reimage the device. See Reimage the Cisco ASA or Firepower Threat Defense Device.
Privacy Collection Statement—The ISA 3000 does not require or actively collect personally-identifiable information. However, you can use personally-identifiable information in the configuration, for example for usernames. In this case, an administrator might be able to see this information when working with the configuration or when using SNMP.
Deploy and perform initial configuration of the management center. See the Cisco Firepower Management Center 1600, 2600, and 4600 Hardware Installation Guide or Cisco Secure Firewall Management Center Virtual Getting Started Guide.
See the following tasks to deploy the threat defense with management center on your chassis.

|
|
Pre-Configuration |
|
|
|
Pre-Configuration |
|
|
|
Pre-Configuration |
|
|
|
Threat Defense CLI |
Complete the Threat Defense Initial Configuration Using the CLI. |
|
|
Management Center |
|
|
|
Smart Software Manager |
Obtain Licenses for the Management Center: Generate a license token for the management center. |
|
|
Management Center |
Obtain Licenses for the Management Center: Register the management center with the Smart Licensing server. |
|
|
Management Center |
|
|
|
Management Center |
You can manage the threat defense using management center from the Management 1/1 interface, or in 6.7 and later, a data interface. By default, the Management 1/1 interface is enabled and configured with an IP address (192.168.45.45). This interface also runs a DHCP server initially; after you select the management center as the manager during initial setup, the DHCP server is disabled. You can configure the Management interface and an management center access data interface during initial setup at the console port. You can configure other data interfaces after you connect the threat defense to the management center.
 Note |
Management Center access from a data interface has the following limitations:
|
See the following sample network deployments for ideas on how to place your threat defense device in your network.
Both the management center and the threat defense require internet access from management for licensing and updates.
The following figure shows a possible network deployment for the ISA 3000 where the management center and management computer connect to the management network. The management network has a path to the internet for licensing and updates.

 Note |
For a remote branch setup, we recommend that you use the standalone document specific to that deployment. |
The following figure shows the recommended network deployment for the ISA 3000 using the outside interface for management. This scenario is ideal for managing branch offices from a central headquarters. You can perform initial setup of the threat defense at headquarters and then send a pre-configured device to a branch location.
Either the threat defense or management center needs a public IP address or hostname. If the threat defense receives a public IP address using DHCP, then you can optionally configure Dynamic DNS (DDNS) for the outside interface. DDNS ensures the management center can reach the threat defense at its Fully-Qualified Domain Name (FQDN) if the threat defense's IP address changes. If the threat defense receives a private IP address, then the management center needs to have a public IP address or hostname.

The following figure shows the recommended network deployment for the ISA 3000 using the inside interface for management.
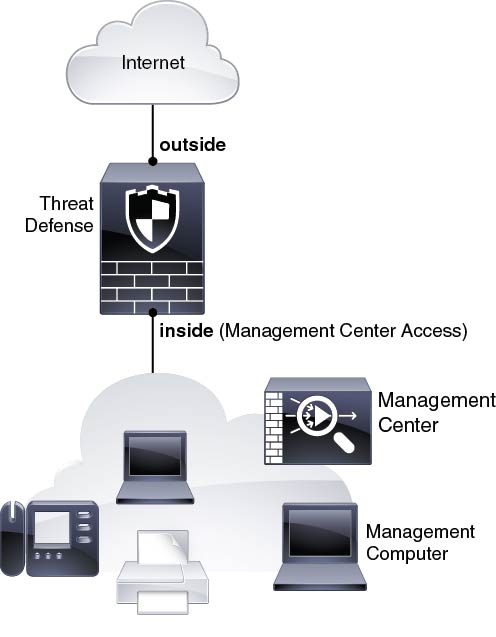
The management center can only communicate with the threat defense on the management interface in 6.6 and earlier. Moreover, both the management center and threat defense require internet access from management for licensing and updates.
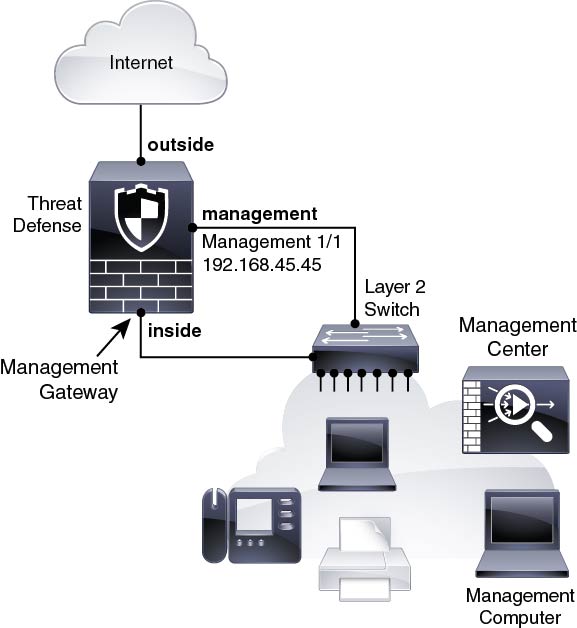
The following figure shows a possible network deployment for the ISA 3000 where the ISA 3000 acts as the internet gateway for the management center and threat defense management.You can also use this scenario in 6.7 and later for a High Availability deployment, for example.
In the following diagram, the ISA 3000 acts as the internet gateway for the management interface and the management center by connecting Management 1/1 to an inside interface through a Layer 2 switch, and by connecting the management center and management computer to the switch. (This direct connection is allowed because the management interface is separate from the other interfaces on the threat defense.)
To cable one of the recommended scenarios on the ISA 3000, see the following steps.
 Note |
The ISA 3000 and the management center both have the same default management IP address: 192.168.45.45. This guide assumes that you will set different IP addresses for your devices during initial setup. Note that the management center on 6.5 and later defaults to a DHCP client for the management interface; however, if there is no DHCP server, it will default to 192.168.45.45. |
 Note |
Other topologies can be used, and your deployment will vary depending on your basic logical network connectivity, ports, addressing, and configuration requirements. |
| Step 1 |
Cable for a separate management network. 
|
| Step 2 |
(6.7 and later) Cable for a remote management deployment: 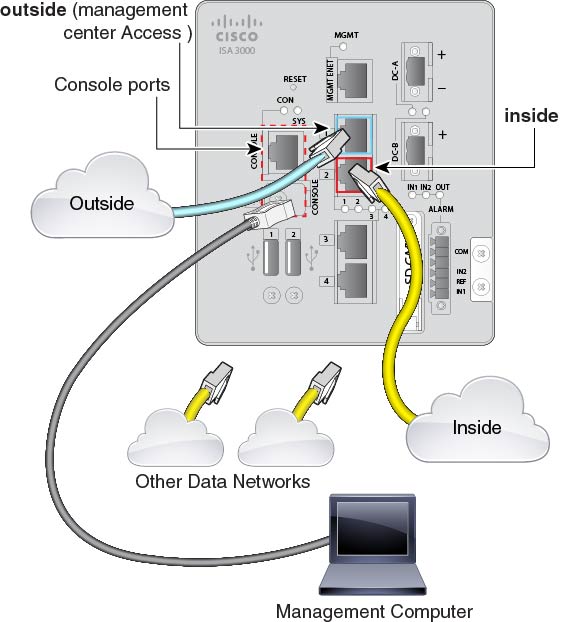
The management center and your management computer reside at a remote headquarters, and can reach the threat defense over the internet. |
| Step 3 |
(6.7 and later) Cable for an inside management deployment: 
The management center and your management computer reside on the inside network with your other inside end points. |
| Step 4 |
(6.6 and earlier) Cable for an edge deployment. 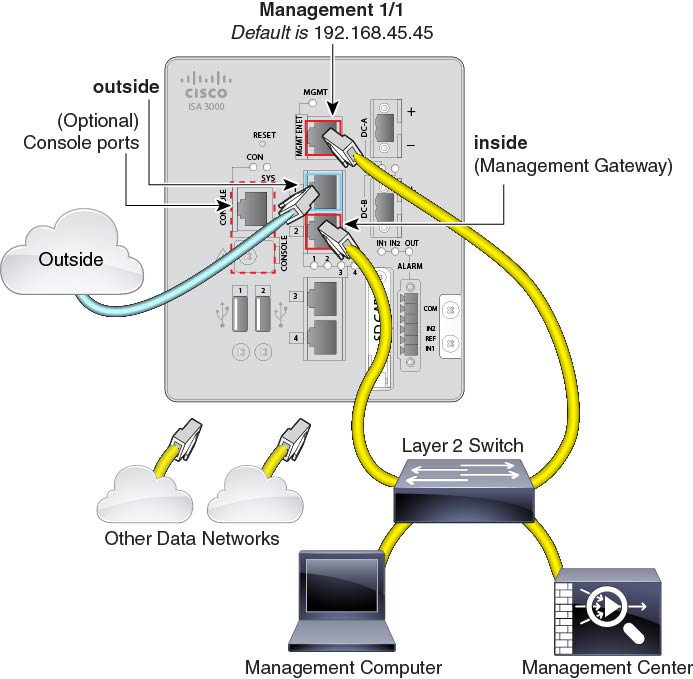
|
System power is controlled by DC power; there is no power button.
It's important that you provide reliable power for your device (for example, using an uninterruptable power supply (UPS)). Loss of power without first shutting down can cause serious file system damage. There are many processes running in the background all the time, and losing power does not allow the graceful shutdown of your system.
| Step 1 |
Attach the power plug to the ISA 3000 after wiring it to the DC power source. Refer to “Connecting to DC Power” in the hardware installation guide for instructions on proper wiring of the power plug. |
| Step 2 |
Check the System LED on the front panel of the ISA 3000 device; if it is steady green, the device is powered on. If it is flashing green, the device is in Boot up phase and POST. Refer to “Verifying Connections” in the hardware installation guide to verify that all devices are properly connected to the ISA 3000. |
Connect to the threat defense CLI to perform initial setup, including setting the Management IP address, gateway, and other basic networking settings using the setup wizard. The dedicated Management interface is a special interface with its own network settings. In 6.7 and later: If you do not want to use the Management interface for the management center access, you can use the CLI to configure a data interface instead. You will also configure management center communication settings.
| Step 1 |
Connect to the threat defense CLI, either from the console port or using SSH to the Management interface, which obtains an IP address from a DHCP server by default. If you intend to change the network settings, we recommend using the console port so you do not get disconnected. |
||||
| Step 2 |
Log in with the username admin and the password Admin123.
|
||||
| Step 3 |
The first time you log in to the threat defense, you are prompted to accept the End User License Agreement (EULA) and to change the admin password. You are then presented with the CLI setup script.
Defaults or previously entered values appear in brackets. To accept previously entered values, press Enter.
See the following guidelines:
Example: |
||||
| Step 4 |
Identify the management center that will manage this threat defense. configure manager add {hostname | IPv4_address | IPv6_address | DONTRESOLVE} reg_key [nat_id]
Example:If the management center is behind a NAT device, enter a unique NAT ID along with the registration key, and specify DONTRESOLVE instead of the hostname, for example: Example:If the threat defense is behind a NAT device, enter a unique NAT ID along with the management center IP address or hostname, for example: Example: |
||||
| Step 5 |
(Optional) (6.7 and Later) Configure a data interface for the management center access. configure network management-data-interface You are then prompted to configure basic network settings for the data interface.
See the following details for using this command:
Example:Example: |
||||
| Step 6 |
(Optional) (6.7 and Later) Limit data interface access to an management center on a specific network. configure network management-data-interface client ip_address netmask By default, all networks are allowed. |
Register your device to a management center.
Use the management center to configure and monitor the threat defense.
For information on supported browsers, refer to the release notes for the version you are using (see https://www.cisco.com/go/firepower-notes).
| Step 1 |
Using a supported browser, enter the following URL. https://fmc_ip_address |
| Step 2 |
Enter your username and password. |
| Step 3 |
Click Log In. |
All licenses are supplied to the threat defense by the management center. You can purchase the following licenses:
Threat—Security Intelligence and Next-Generation IPS
Malware—Malware defense
URL—URL Filtering
RA VPN—AnyConnect Plus, AnyConnect Apex, or AnyConnect VPN Only
For a more detailed overview on Cisco Licensing, go to cisco.com/go/licensingguide
Have a master account on the Smart Software Manager.
If you do not yet have an account, click the link to set up a new account. The Smart Software Manager lets you create a master account for your organization.
Your Smart Software Licensing account must qualify for the Strong Encryption (3DES/AES) license to use some features (enabled using the export-compliance flag).
| Step 1 |
Make sure your Smart Licensing account contains the available licenses you need. When you bought your device from Cisco or a reseller, your licenses should have been linked to your Smart Software License account. However, if you need to add licenses yourself, use the Find Products and Solutions search field on the Cisco Commerce Workspace. Search for the following license PIDs: 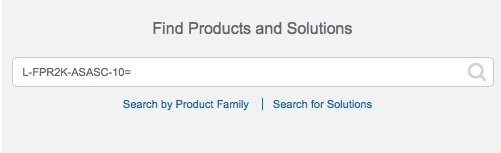
|
||
| Step 2 |
If you have not already done so, register the management center with the Smart Licensing server. Registering requires you to generate a registration token in the Smart Software Manager. See the Cisco Secure Firewall Management Center Administration Guide for detailed instructions. |
Register the threat defense to the management center manually using the device IP address or hostname.
Gather the following information that you set in the threat defense initial configuration:
The threat defense management IP address or hostname, and NAT ID
The management center registration key
| Step 1 |
In the management center, choose . |
||
| Step 2 |
From the Add drop-down list, choose Add Device. 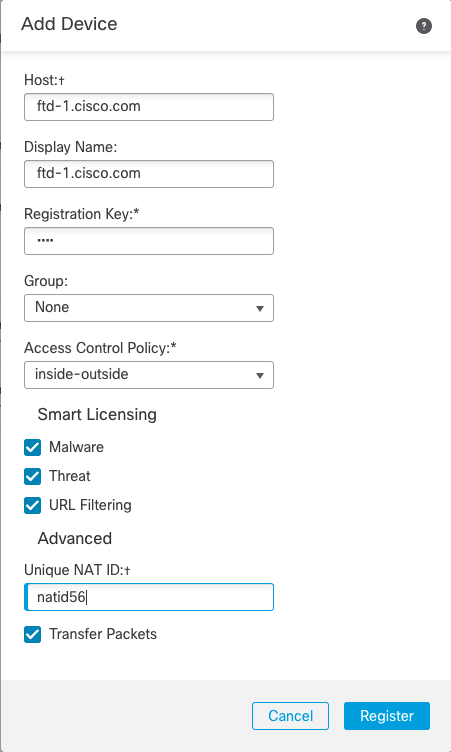 Set the following parameters:
|
||
| Step 3 |
Click Register, or if you want to add another device, click Register and Add Another and confirm a successful registration. If the registration succeeds, the device is added to the list. If it fails, you will see an error message. If the threat defense fails to register, check the following items:
For more troubleshooting information, see https://cisco.com/go/fmc-reg-error. |
This section describes how to configure a basic security policy with the following settings:
Inside and outside interfaces—Assign a static IP address to the inside interface, and use DHCP for the outside interface.
DHCP server—Use a DHCP server on the inside interface for clients.
Default route—Add a default route through the outside interface.
NAT—Use interface PAT on the outside interface.
Access control—Allow traffic from inside to outside.
To configure a basic security policy, complete the following tasks.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Enable the threat defense interfaces, assign them to security zones, and set the IP addresses. Typically, you must configure at least a minimum of two interfaces to have a system that passes meaningful traffic. Normally, you would have an outside interface that faces the upstream router or internet, and one or more inside interfaces for your organization’s networks. Some of these interfaces might be “demilitarized zones” (DMZs), where you place publically-accessible assets such as your web server.
A typical edge-routing situation is to obtain the outside interface address through DHCP from your ISP, while you define static addresses on the inside interfaces.
The following example configures a routed mode inside interface with a static address and a routed mode outside interface using DHCP.
| Step 1 |
Choose , and click the Edit ( |
||
| Step 2 |
Click Interfaces.  |
||
| Step 3 |
Click Edit ( The General tab appears.  |
||
| Step 4 |
Click the Edit ( The General tab appears. 
|
||
| Step 5 |
Click Save. |
Enable the DHCP server if you want clients to use DHCP to obtain IP addresses from the threat defense.
| Step 1 |
Choose , and click the Edit ( |
| Step 2 |
Choose . |
| Step 3 |
On the Server page, click Add, and configure the following options: 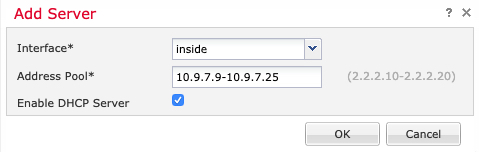
|
| Step 4 |
Click OK. |
| Step 5 |
Click Save. |
The default route normally points to the upstream router reachable from the outside interface. If you use DHCP for the outside interface, your device might have already received a default route. If you need to manually add the route, complete this procedure. If you received a default route from the DHCP server, it will show in the IPv4 Routes or IPv6 Routes table on the page.
| Step 1 |
Choose , and click the Edit ( |
| Step 2 |
Choose , click Add Route, and set the following: 
|
| Step 3 |
Click OK. The route is added to the static route table.  |
| Step 4 |
Click Save. |
A typical NAT rule converts internal addresses to a port on the outside interface IP address. This type of NAT rule is called interface Port Address Translation (PAT).
| Step 1 |
Choose , and click . |
||
| Step 2 |
Name the policy, select the device(s) that you want to use the policy, and click Save.  The policy is added the management center. You still have to add rules to the policy. |
||
| Step 3 |
Click Add Rule. The Add NAT Rule dialog box appears. |
||
| Step 4 |
Configure the basic rule options: 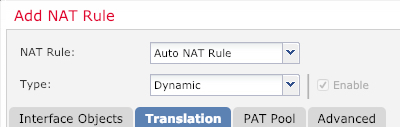
|
||
| Step 5 |
On the Interface Objects page, add the outside zone from the Available Interface Objects area to the Destination Interface Objects area. 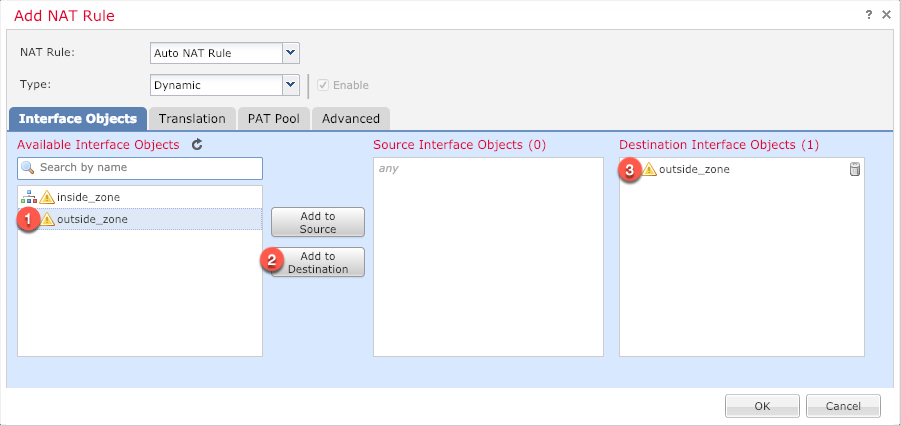 |
||
| Step 6 |
On the Translation page, configure the following options: 
|
||
| Step 7 |
Click Save to add the rule. The rule is saved to the Rules table.  |
||
| Step 8 |
Click Save on the NAT page to save your changes. |
If you created a basic Block all traffic access control policy when you registered the threat defense, then you need to add rules to the policy to allow traffic through the device. The following procedure adds a rule to allow traffic from the inside zone to the outside zone. If you have other zones, be sure to add rules allowing traffic to the appropriate networks.
| Step 1 |
Choose , and click the Edit ( |
| Step 2 |
Click Add Rule, and set the following parameters: 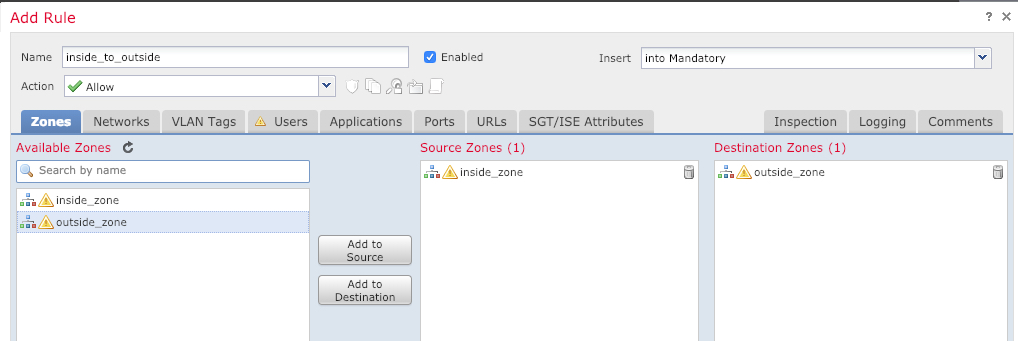
Leave the other settings as is. |
| Step 3 |
Click Add. The rule is added to the Rules table.  |
| Step 4 |
Click Save. |
Deploy the configuration changes to the threat defense; none of your changes are active on the device until you deploy them.
| Step 1 |
Click Deploy in the upper right. 
|
| Step 2 |
Either click Deploy All to deploy to all devices or click Advanced Deploy to deploy to selected devices. 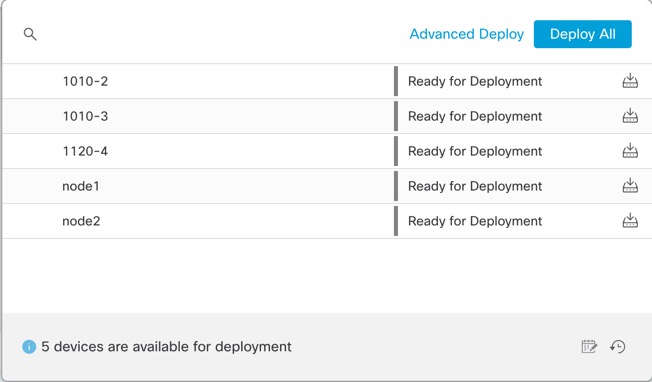
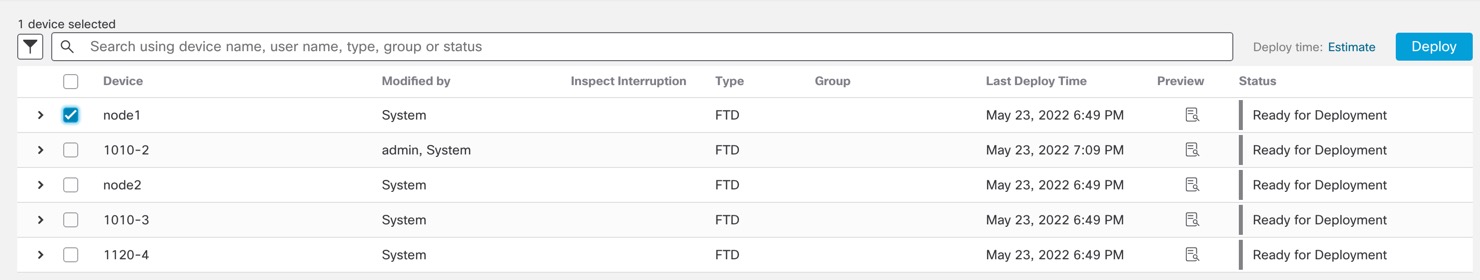
|
| Step 3 |
Ensure that the deployment succeeds. Click the icon to the right of the Deploy button in the menu bar to see status for deployments. 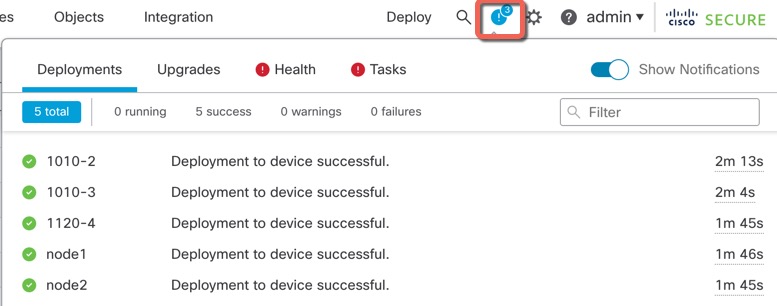
|
Use the command-line interface (CLI) to set up the system and do basic system troubleshooting. You cannot configure policies through a CLI session. You can access the CLI by connecting to the console port.
You can SSH to the management interface of the threat defense device. You can also connect to the address on a data interface if you open the interface for SSH connections. SSH access to data interfaces is disabled by default.
| Step 1 |
To log into the CLI, connect your management computer to the console port., either the RJ-45 port or the mini-USB port.Be sure to install any necessary USB serial drivers for your operating system. Use the following serial settings:
|
| Step 2 |
Log in to the threat defense CLI using the admin username and the password you set at initial setup (the default is Admin123). After logging in, for information on the commands available in the CLI, enter help or ? . For usage information, see the Cisco Firepower Threat Defense Command Reference. |
It's important that you shut down your system properly. Simply unplugging the power can cause serious file system damage. Remember that there are many processes running in the background all the time, and unplugging or shutting off the power does not allow the graceful shutdown of your firewall system.
The ISA 3000 chassis does not have an external power switch.You can power off the device using the management center device management page, or you can use the CLI.
It's important that you shut down your system properly. Simply unplugging the power or pressing the power switch can cause serious file system damage. Remember that there are many processes running in the background all the time, and unplugging or shutting off the power does not allow the graceful shutdown of your firewall.
 Note |
Shutting down is supported in 7.0.2+/7.2+. |
You can shut down your system properly using the management center.
| Step 1 |
Choose . |
| Step 2 |
Next to the device that you want to restart, click the edit icon ( |
| Step 3 |
Click the Device tab. |
| Step 4 |
Click the shut down device icon ( |
| Step 5 |
When prompted, confirm that you want to shut down the device. |
| Step 6 |
Monitor the shutdown process. If you cannot monitor the device, wait approximately 3 minutes to ensure the system has shut down.
|
| Step 7 |
You can now unplug the power to physically remove power from the chassis if necessary. |
It's important that you shut down your system properly. Simply unplugging the power can cause serious file system damage. Remember that there are many processes running in the background all the time, and unplugging or shutting off the power does not allow the graceful shutdown of your system. The ISA 3000 chassis does not have an external power switch.
 Note |
Shutting down is supported in 7.0.2+/7.2+. |
| Step 1 |
Connect to the console port to access the threat defense CLI, and then shut down the threat defense. shutdown Example: |
| Step 2 |
After the threat defense shuts down, and the console shows that "It is safe to power off now", you can then unplug the power to physically remove power from the chassis if necessary. |
To continue configuring your threat defense, see the documents available for your software version at Navigating the Cisco Firepower Documentation.
For information related to using the management center, see the Firepower Management Center Configuration Guide.