Overview of the API Client Authentication Process
Following is the end-to-end view of how to authenticate your API client with the threat defense device.
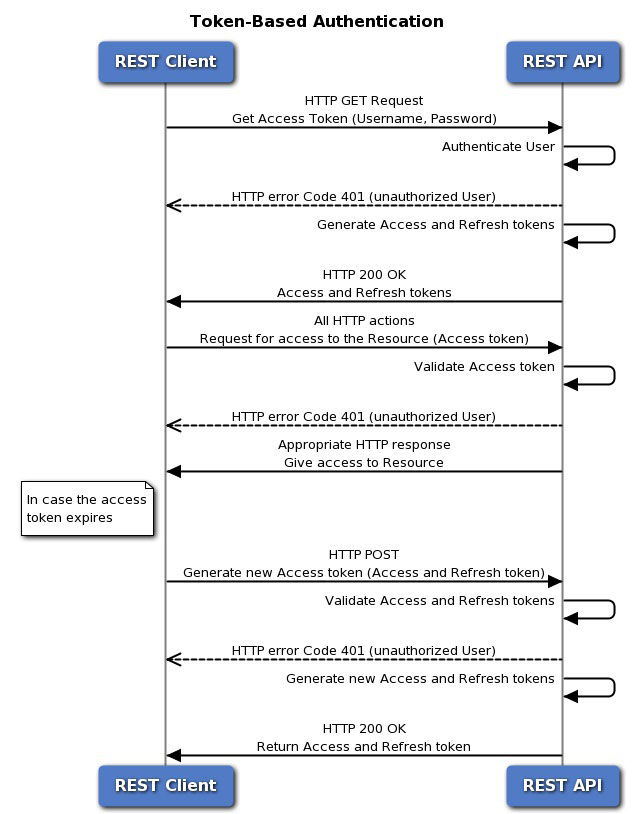
Before you begin
Each token represents an HTTPS login session, which counts for API sessions and device manager sessions. There can be a maximum of 5 active HTTPS sessions. If you exceed this limit, the oldest session, either the device manager login or API token, is expired to allow the new session. Thus, it is important that you get only those tokens you need, and you reuse each token until it is expired, then renew them. Getting a new token for each API call will result in severe session churn and could lock users out of the device manager. These limits do not apply to SSH sessions.
Procedure
|
Step 1 |
Authenticate the API client user using whatever method you require. Your client is obligated to authenticate users and ensure they have the authority to access and modify the threat defense device. If you want to provide differential abilities based on authorization rights, you need to build that into your client. For example, if you want to allow read-only access, you must set up the required authentication server, user accounts, and so forth. Then, when a user with read-only rights logs into your client, you must ensure that you issue GET calls only. In API v1, this type of variable access cannot be controlled by the threat defense device itself. Starting with API v2, if you are using external users and you do not groom calls based on user authorization, you will get errors if there is a mismatch between user authorization and the calls you attempt. For v1, when communicating with the device, you must use the admin user account on the threat defense device. The admin account has full read/write authorization for all user-configurable objects. |
|
Step 2 |
Request a password-granted access token based on username/password using the admin account. |
|
Step 3 |
Optionally, request a custom access token for your client. With a custom token, you can explicitly request a validity period, and assign a subject name for the token. See Requesting a Custom Access Token. |
|
Step 4 |
Use the access token on API calls in the Authorization: Bearer header. |
|
Step 5 |
Before the access token expires, refresh the token. |
|
Step 6 |
When you are finished, revoke the token if it has not yet expired. |

 Feedback
Feedback