|
Platform Features
|
|
Support ends for the ASA 5525-X, 5545-X, and 5555-X. The last
supported release is FTD 6.6.
|
You cannot install FTD 6.7 on an ASA 5525-X, 5545-X, or 5555-X. The last supported
release for these models is FTD 6.6.
|
|
Firewall and IPS Features
|
|
TLS server identity discovery for access control rule matching.
|
TLS 1.3 certificates are encrypted. For traffic encrypted with TLS
1.3 to match access rules that use application or URL filtering, the
system must decrypt the TLS 1.3 certificate. We recommend that you
enable TLS Server Identity Discovery to
ensure encrypted connections are matched to the right access control
rule. The setting decrypts the certificate only; the connection
remains encrypted.
We added the Access Control Settings ( ) button and dialog box to the page. ) button and dialog box to the page.
|
|
External trusted CA certificate groups.
|
You can now customize the list of trusted CA certificates used by the
SSL decryption policy. By default, the policy uses all
system-defined trusted CA certificates, but you can create a custom
group to add more certificates, or replace the default group with
your own, more limited, group.
We added certificate groups to the page, and modified the SSL decryption policy settings
to allow the selection of certificate groups.
|
|
Active Directory realm sequences for passive identity rules.
|
You can create a realm sequence, which is an ordered list of Active
Directory (AD) servers and their domains, and use them in a passive
authentication identity rule. Realm sequences are useful if you
support more than one AD domain and you want to do user-based access
control. Instead of writing separate rules for each AD domain, you
can write a single rule that covers all of your domains. The
ordering of the AD realms within the sequence is used to resolve
identity conflicts if any arise.
We added the AD realm sequence object on the page, and the ability to select the object as a realm in a passive authentication identity rule. In the FTD API, we added the RealmSequence resource, and in the IdentityRule resource, we added the ability to select a realm sequence object as the realm for a rule that uses passive authentication
as the action.
|
|
FDM support for Trustsec security group tag (SGT) group objects and
their use in access control rules.
|
In FTD 6.5, support was added to the FTD API to configure SGT group objects and use them as matching criteria in access control rules. In addition, you could modify
the ISE identity object to listen to the SXP topic published by ISE. Now, you can configure these features directly in FDM.
We added a new object, SGT groups, and updated the access control
policy to allow their selection and display. We also modified the
ISE object to include the explicit selection of topics to subscribe
to.
|
|
Snort 3.0 support.
|
For new systems, Snort 3.0 is the default inspection engine. If you
upgrade to 6.7 from an older release, Snort 2.0 remains the active
inspection engine, but you can switch to Snort 3.0. For this
release, Snort 3.0 does not support virtual routers, time-based
access control rules, or the decryption of TLS 1.1 or lower
connections. Enable Snort 3.0 only if you do not need these
features. You can freely switch back and forth between Snort 2.0 and
3.0, so you can revert your change if needed. Traffic will be
interrupted whenever you switch versions.
We added the ability to switch Snort versions to the page, in the Intrusion Rules
group. In the FTD API, we added the IntrusionPolicy resource
action/toggleinspectionengine.
In addition, there is a new audit event, Rules Update Event, that
shows which intrusion rules were added, deleted, or changed in a
Snort 3 rule package update.
|
|
Custom intrusion policies for Snort 3.
|
You can create custom intrusion policies when you are using Snort 3
as the inspection engine. In comparison, you could use the
pre-defined policies only if you use Snort 2. With custom intrusion
policies, you can add or remove groups of rules, and change the
security level at the group level to efficiently change the default
action (disabled, alert or drop) of the rules in the group. Snort 3
intrusion policies give you more control over the behavior of your
IPS/IDS system without the need to edit the base Cisco
Talos-provided policies.
We changed the page to list intrusion policies. You can create new
ones, and view or edit existing policies, including adding/removing
groups, assigning security levels, and changing the action for
rules. You can also select multiple rules and change their actions.
In addition, you can select custom intrusion policies in access
control rules.
|
|
Multiple syslog servers for intrusion events.
|
You can configure multiple syslog servers for intrusion policies.
Intrusion events are sent to each syslog server.
We added the ability to select multiple syslog server objects to the
intrusion policy settings dialog box.
|
|
URL reputation matching can include sites with unknown
reputations.
|
When you configure URL category traffic-matching criteria, and select
a reputation range, you can include URLs with unknown reputation in
the reputation match.
We added the Include Sites with Unknown
Reputation check box to the URL reputation criteria
in access control and SSL decyption rules.
|
|
VPN Features
|
|
Virtual Tunnel Interface (VTI) and route-based site-to-site VPN.
|
You can now create route-based site-to-site VPNs by using a Virtual
Tunnel Interface as the local interface for the VPN connection
profile. With route-based site-to-site VPN, you manage the protected
networks in a given VPN connection by simply changing the routing
table, without altering the VPN connection profile at all. You do
not need to keep track of remote networks and update the VPN
connection profile to account for these changes. This simplifies VPN
management for cloud service providers and large enterprises.
We added the Virtual Tunnel Interfaces tab to
the Interface listing page, and updated the site-to-site VPN wizard
so that you can use a VTI as the local interface.
|
|
FTD API support for Hostscan and Dynamic Access Policy (DAP) for
remote access VPN connections.
|
You can upload Hostscan packages and the Dynamic Access Policy (DAP)
rule XML file, and configure DAP rules to create the XML file, to
control how group policies are assigned to remote users based on
attributes related to the status of the connecting endpoint. You can
use these features to perform Change of Authorization if you do not
have Cisco Identity Services Engine (ISE). You can upload Hostscan
and configure DAP using the FTD API only; you cannot configure them using FDM. See the AnyConnect
documentation for information about Hostscan and DAP usage.
We added or modified the following FTD API object models: dapxml, hostscanpackagefiles,
hostscanxmlconfigs, ravpns.
|
|
Enabling certificate revocation checking for external CA
certificates
|
You can use the FTD API to enable certificate revocation checking on a particular external CA certificate. Revocation checking is particularly
useful for certificates used in remote access VPN. You cannot configure revocation checking on a certificate using FDM, you
must use the FTD API.
We added the following attributes to the ExternalCACertificate
resource: revocationCheck, crlCacheTime, oscpDisableNonce.
|
|
Support removed for less secure Diffie-Hellman groups, and encryption
and hash algorithms.
|
The following features were deprecated in 6.6 and they are now
removed. If you are still using them in IKE proposals or IPsec
policies, you must replace them after upgrade before you can deploy
any configuration changes. We recommend that you change your VPN
configuration prior to upgrade to supported DH and encryption
algorithms to ensure the VPN works correctly.
-
Diffie-Hellman groups: 2, 5, and 24.
-
Encryption algorithms for users who satisfy export controls
for strong encryption: DES, 3DES, AES-GMAC, AES-GMAC-192,
AES-GMAC-256. DES continues to be supported (and is the only
option) for users who do not satisfy export controls.
-
Hash algorithms: MD5.
|
|
Custom port for remote access VPN.
|
You can configure the port used for remote access VPN (RA VPN)
connections. If you need to connect to FDM on the same interface
used for RA VPN, you can change the port number for RA VPN
connections. FDM uses port 443, which is also the default RA VPN
port.
We updated the global settings step of the RA VPN wizard to include
port configuration.
|
|
SAML Server support for authenticating remote access VPN.
|
You can configure a SAML 2.0 server as the authentication source for
a remote access VPN. Following are the supported SAML servers:
Duo.
We added SAML server as an identity source on the page, and updated remote access VPN connection
profiles to allow its use.
|
|
FTD API Support for AnyConnect module profiles.
|
You can use the FTD API to upload module profiles used with AnyConnect, such as AMP Enabler, ISE Posture, or Umbrella. You must create these
profiles using the offline profile editors that you can install from the AnyConnect profile editor package.
We added the anyConnectModuleType attribute to the
AnyConnectClientProfile model. Although you can initially create
AnyConnect Client Profile objects that use module profiles, you will
still need to use the API to modify the objects created in FDM to
specify the correct module type.
|
|
Routing Features
|
|
EIGRP support using Smart CLI.
|
In previous releases, you configured EIGRP in the Advanced
Configuration pages using FlexConfig. Now, you configure EIGRP using
Smart CLI directly on the Routing page.
If you configured EIGRP using FlexConfig, when you upgrade to release
6.7, you must remove the FlexConfig object from the FlexConfig
policy, and then recreate your configuration in the Smart CLI
object. You can retain your EIGRP FlexConfig object for reference
until you have completed the Smart CLI updates. Your configuration
is not automatically converted.
We added the EIGRP Smart CLI object to the Routing pages.
|
|
Interface Features
|
|
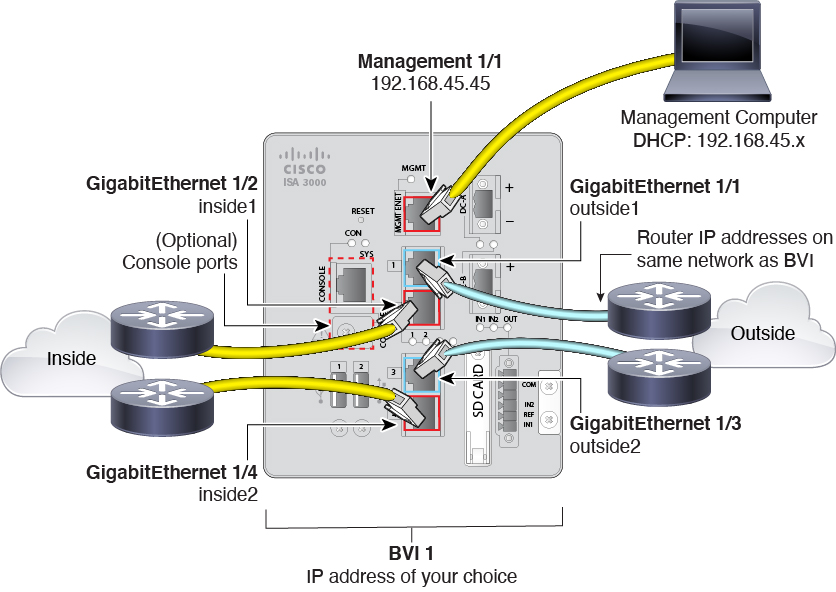
ISA 3000 hardware bypass persistence
|
You can now enable hardware bypass for ISA 3000 interface pairs with
the persistence option: after power is restored, hardware bypass
remains enabled until you manually disable it. If you enable
hardware bypass without persistence, hardware bypass is
automatically disabled after power is restored. There may be a brief
traffic interruption when hardware bypass is disabled. The
persistence option lets you control when the brief interruption in
traffic occurs.
New/Modified screen:
|
|
Synchronization between the FTD operational link state and the physical link state for the Firepower 4100/9300
|
The Firepower 4100/9300 chassis can now synchronize the FTD operational link state with the physical link state for data interfaces. Currently, interfaces will be in an Up state as
long as the FXOS admin state is up and the physical link state is up. The FTD application interface admin state is not considered. Without synchronization from FTD, data interfaces can be in an Up state physically before the FTD application has completely come online, for example, or can stay Up for a period of time after you initiate an FTD shutdown. This feature is disabled by default, and can be enabled per logical device in FXOS.
| Note
|
This feature is not supported for an FTD with a Radware vDP decorator.
|
New/Modified Firepower Chassis Manager screens: Logical Devices > Enable Link State
New/Modified FXOS commands: set link-state-sync enabled,
show interface expand detail
Supported platforms: Firepower 4100/9300
|
|
Firepower 1100 and 2100 SFP interfaces now support disabling
auto-negotiation
|
You can now configure a Firepower 1100 and 2100 SFP interface to
disable auto-negotiation. For 10GB interfaces, you can configure the
speed down to 1GB without auto-negotiation; you cannot disable
auto-negotiation for an interface with the speed set to
10GB.
New/Modified screen: Device > Interfaces > Edit Interface >
Advanced Options > SpeedSupported platforms: Firepower 1100
and 2100
|
|
Administrative and Troubleshooting Features
|
|
Ability to cancel a failed FTD software upgrade and to revert to the previous release.
|
If an FTD major software upgrade fails or is otherwise not functioning correctly, you can revert to the state of the device as it was
when you installed the upgrade.
We added the ability to revert the upgrade to the System Upgrade panel in FDM. During an upgrade, the FDM login screen shows
the upgrade status and gives you the option to cancel or revert in case of upgrade failure. In the FTD API, we added the CancelUpgrade, RevertUpgrade, RetryUpgrade, and UpgradeRevertInfo resources.
In the FTD CLI, we added the following commands: show last-upgrade status , show upgrade status , show upgrade revert-info , upgrade cancel , upgrade revert , upgrade cleanup-revert , upgrade retry .
|
|
Custom HTTPS port for FDM/FTD API access on data interfaces.
|
You can change the HTTPS port used for FDM or FTD API access on data interfaces. By changing the port from the default 443, you can avoid conflict between management access
and other features, such as remote access VPN, configured on the same data interface. Note that you cannot change the management
access HTTPS port on the management interface.
We added the ability to change the port to the page.
|
|
Low-touch provisioning for Cisco Defense Orchestrator on Firepower
1000 and 2100 series devices.
|
If you plan on managing a new FTD device using Cisco Defense Orchestrator (CDO), you can now add the device without completing the device setup wizard or even
logging into FDM.
New Firepower 1000 and 2100 series devices are initially registered
in the Cisco cloud, where you can easily claim them in CDO. Once in
CDO, you can immediately manage the devices from CDO. This low-touch
provisioning minimizes the need to interact directly with the
physical device, and is ideal for remote offices or other locations
where your employees are less experienced working with networking
devices.
We changed how Firepower 1000 and 2100 series devices are initially
provisioned. We also added auto-enrollment to the page, so that you can manually start the process for
upgraded devices or other devices that you have previously managed
using FDM.
|
|
FTD API support for SNMP configuration.
|
You can use the FTD API to configure SNMP version 2c or 3 on an FDM or CDO managed FTD device.
We added the following API resources: SNMPAuthentication, SNMPHost,
SNMPSecurityConfiguration, SNMPServer, SNMPUser, SNMPUserGroup,
SNMPv2cSecurityConfiguration, SNMPv3SecurityConfiguration.
| Note
|
If you used FlexConfig to configure SNMP, you must redo your configuration using the FTD API SNMP resources. The commands for configuring SNMP are no longer allowed in FlexConfig. Simply removing the SNMP FlexConfig
object from the FlexConfig policy will allow you to deploy changes; you can then use the object as reference while you use
the API to reconfigure the feature.
|
|
|
Maximum backup files retained on the system is reduced from 10 to
3.
|
The system will retain a maximum of 3 backup files on the system
rather than 10. As new backups are created, the oldest backup file
is deleted. Please ensure that you download backup files to a
different system so that you have the versions required to recover
the system in case you need to.
|
|
FTD API Version backward compatibility.
|
Starting with FTD Version 6.7, if an API resource model for a feature does not change between releases, then the FTD API can accept calls that are based on the older API version. Even if the feature model did change, if there is a logical
way to convert the old model to the new model, the older call can work. For example, a v4 call can be accepted on a v5 system.
If you use “latest” as the version number in your calls, these “older” calls are interpreted as a v5 call in this scenario,
so whether you are taking advantage of backward compatibility depends on how you are structuring your API calls.
|
|
FTD REST API version 6 (v6).
|
The FTD REST API for software version 6.7 is version 6. You can use v6 in
the API URLs, or preferentially, use /latest/ to signify you are
using the most recent API version that is supported on the device.
Please re-evaluate all existing calls, as changes might have been
mode to the resource models you are using. To open the API Explorer,
where you can view the resources, log into FDM, then click the more
options button ( ) and choose API Explorer. ) and choose API Explorer.
|







 Feedback
Feedback