The Ingestion Configuration page allows you to configure flow and variable traffic storage. You can choose whether to store flows and variables. Flows
and variables storage is disabled by default.
To access the Ingestion Configuration, choose Admin > Data Management > Ingestion Configurationfrom the main menu.
Messages can appear in Cisco Cyber Vision's user interface to indicate to the user that features may be limited due to absence
of flows in the database. For example, in the activity technical sheet, at the top of the flows table:
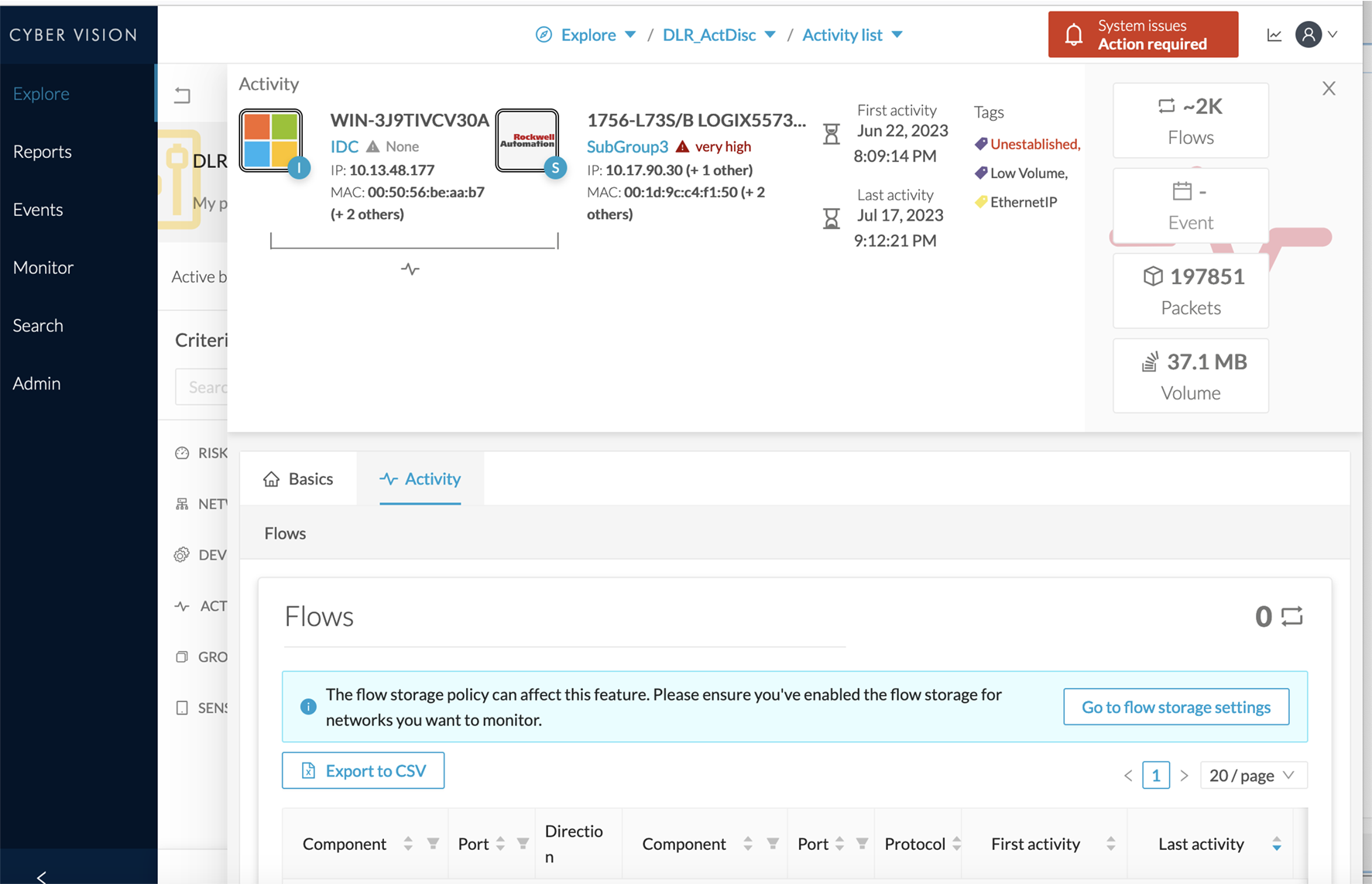
In this case, you can click Go to flow storage settings and enable Flow Storage.
If Flow Storage is enabled, it is possible to choose from which subnetworks flows should be stored. These subnetworks can be set on the Network organization page. The option "others" includes flows that are not part of the industrial private network.
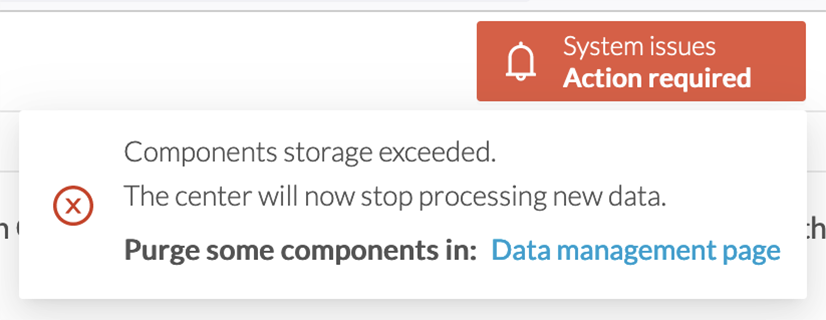
An automatic purge will occur on selected flows when a period of inactivity exceeds 7 days.
You can click the Flows Aggregation and port scan detection toggle buttons to enable them.


 Feedback
Feedback