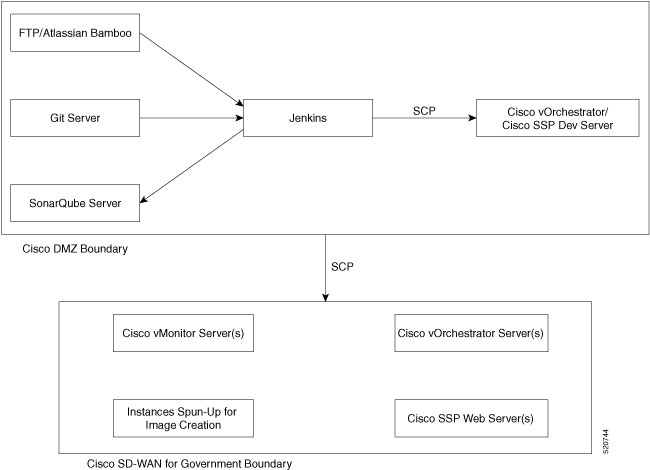
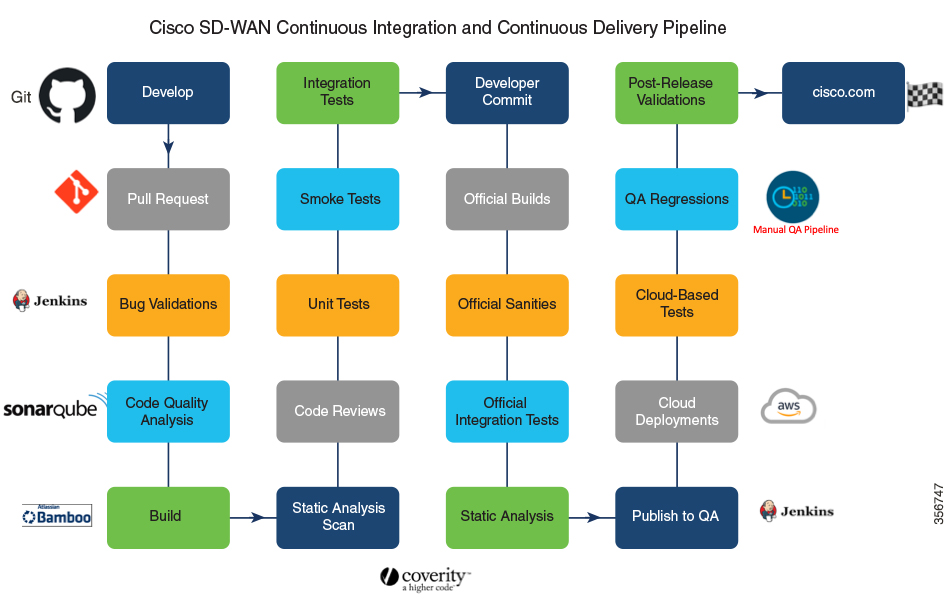
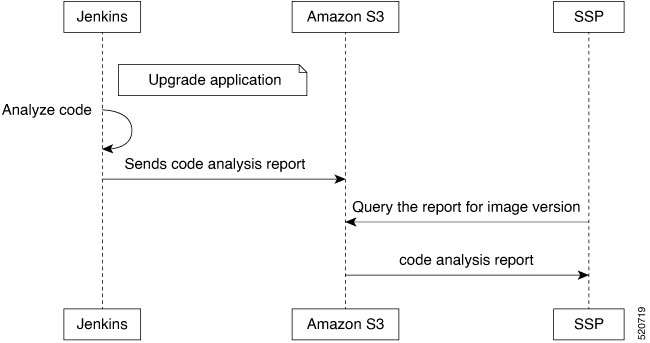
Architecture of Software Development Life Cycle Pipelines
There are two Cisco Catalyst SD-WAN for government Software Development Life Cycle (SDLC) pipelines:
-
Cisco vOrchestrator and Cisco vMonitor SDLC pipeline: The SDLC pipeline used to develop and deploy control components in the Amazon management VPC.
-
Cisco Catalyst SD-WAN controllers and Cisco SD-WAN Manager SDLC pipeline: The SDLC pipeline used to develop and deploy control components in the Amazon customer VPC.

 Feedback
Feedback