Overview of Plan of Actions and Milestones
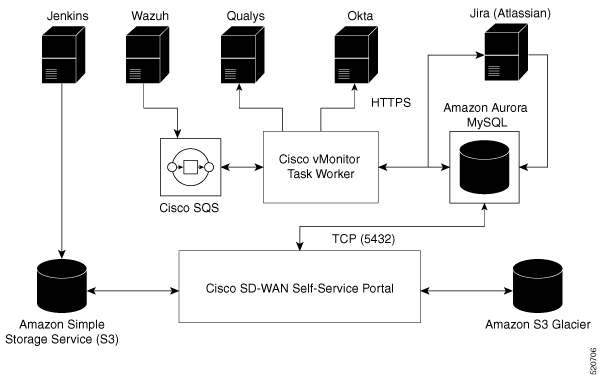
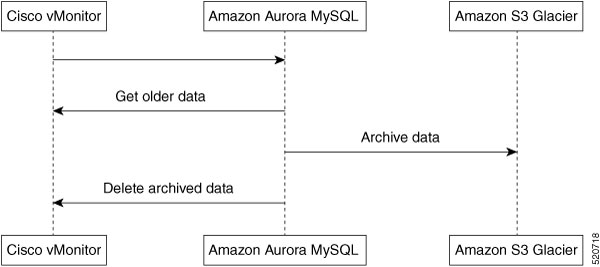
Cisco vMonitor constantly scans Cisco Catalyst SD-WAN for government for potential issues. Cisco vMonitor processes the collected data and creates a Plan of Actions & Milestones (POA&M) alert for potential vulnerabilities. Each POA&M alert generates a JIRA ticket.
Cisco FedOps users can view and download the POA&M report in the Cisco Catalyst SD-WAN Portal. This is enabled by checking if the user is logged in through a federal IdP. Cisco FedOps regardless of their role can access the POA&M reports. These reports can be used to monitor your Cisco Catalyst SD-WAN for government environment, and to identify potential risks and issues.
Cisco Catalyst SD-WAN for government uses a decentralized model to collect data from the following sources:
-
Okta: Okta log events
-
Wazuh: Standard Wazuh scans
-
Tenable: Vulnerability and compliance alerts


 Feedback
Feedback