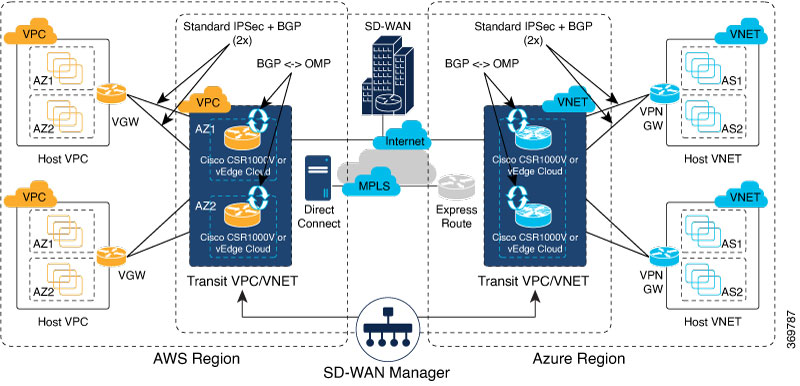
This section describes how to troubleshoot common problems with Cisco SD-WAN Cloud OnRamp for IaaS.
Two Cisco Cloud vEdge Routers are Not Available
From the Cisco vManage menu, choose . After you click Add New Cloud instance, you see an error message indicating that two Cisco vEdge Cloud Routers aren’t available.
Resolve the Problem
The Cisco vManage server doesn’t have two Cisco Cloud vEdge Cloud Routers that are running licensed Cisco SD-WAN software. Contact your operations team so that they can create the necessary Cisco vEdge Cloud Routers.
If the Cisco vEdge Cloud Routers are present and the error message persists, the two routers aren’t attached to configuration
templates. Attach these templates in the Cisco vManage
window. For the desired device template, click … and choose Attach Devices.

Note |
In Cisco vManage Release 20.7.x and earlier releases, Device Templates is titled Device.
|
Required API Permissions are Unavailable
When you enter your API keys, you get an error message indicating that this user doesn’t have the required permissions.
Resolve the Problem
Ensure that the Cisco vManage server can reach the internet and has a DNS server configured so that it can reach AWS or Microsoft Azure. To configure a
DNS server, in the Cisco vManage VPN feature configuration template, enter the IP address of a DNS server, and then reattach the configuration template to
the Cisco vManage server.
For AWS, check the API keys belonging to your AWS account. If you think you have the wrong keys, generate another pair of
keys.
For AWS, if you’re entering the correct keys and the error message persists, the keys don’t have the required permissions.
Check the user permissions associated with the key. Give necessary permissions to the user to create and edit VPCs and EC2
instances.
If the error message persists, check the time of the Cisco vManage server to ensure that it’s set to the current time. If it’s not, configure the Cisco vManage server time to point to the Google NTP server. To configure the server time, in the Cisco vManage NTP feature configuration template, enter the hostname of an NTP server. Next, reattach the configuration template to the
NTP feature using Cisco vManage. The Google NTP servers are time.google.com, time2.google.com,time3.google.com, and time4.google.com, and so on.
WAN Edge Router Software Versions don’t Appear in the Drop-Down List When Configuring for AWS
Problem Statement
When you’re trying to configure transit VPC parameters for the transit VPC, Cisco vEdge Cloud Routers software versions aren’t
listed in the drop-down list.
Resolve the Problem
Ensure that you subscribe to the Cisco vEdge Cloud Router Amazon machine image (AMI) in your account within the AWS Marketplace.
Ensure that the Cisco vEdge Cloud Router is running software Release 19.2.1 or later.
VPNs aren’t Listed During Configuration
Problem Statement
After you select the host VPCs or VNets to map, VPNs aren’t listed in the drop-down list.
Resolve the Problem
The problem occurs when the device configuration template attached to the Cisco SD-WAN cloud devices doesn’t include service-side VPNs. You require the service-side VPNs (VPNs other than VPN 0 and VPN 512) to
configure the IPsec connection between the two Cisco SD-WAN cloud devices that you select for the transit and host VPCs or VNets.
This problem can also occur if the two Cisco SD-WAN cloud devices that you select for the transit VPC or VNet have no overlapping service-side VPNs. Because the two Cisco vEdge
Cloud routers form an active–active pair, configure the same service-side VPNs on both of them.
To configure service-side VPNs, in the Cisco vManage VPN feature configuration template, configure at least one service-side VPN. Ensure that at least one of the service-side
VPNs is the same on both routers. Then reattach the configuration template to the routers.
Cisco SD-WAN Cloud OnRamp for IaaS Task Fails
Problem Statement
After you have completed mapping the host VPCs to the transit VPCs, or host VNets to transit VNets, the configuration of Cisco SD-WAN Cloud OnRamp for IaaS fails.
Resolve the Problem
Review the displayed task information that appears on the screen to determine why the task failed. If the errors are related
to AWS or Azure resources, ensure that all required resources are in place.
Cisco SD-WAN Cloud OnRamp for IaaS Task Succeeds, but Cisco SD-WAN Cloud Devices Are Down
Problem Statement
The Cisco SD-WAN Cloud OnRamp for IaaS task was successful, but the Cisco SD-WAN cloud devices are still in the down state.
Resolve the Problem
Check the configuration templates:
-
Check that all portions of the Cisco SD-WAN cloud devices configuration, including policies, are valid and correct. If the configurations are invalid, they aren’t applied
to the router, and the router never comes up.
-
Check that the configuration for the Cisco vBond Orchestrator is correct. If the DNS name or IP address configured in the Cisco vBond Orchestrator is wrong, the Cisco vEdge Cloud Router are unable to reach the Cisco vBond Orchestrator, and hence they are unable to join the overlay network.
After you have determined what the configuration issues are:
-
Delete the Cisco SD-WAN Cloud OnRamp for IaaS components:
-
Unmap the host VPCs or VNets and the transit VPCs or VNets.
-
Delete the transit VPC for the Cisco vEdge Cloud Routers.
-
Edit the configuration templates and reattach them to the Cisco SD-WAN cloud devices.
-
Repeat the Cisco SD-WAN Cloud OnRamp for IaaS configuration process.
Desired Routes are Not Exchanged
Problem Statement
The Cisco SD-WAN Cloud OnRamp for IaaS configuration workflow is successful, the Cisco vEdge Cloud Routers are available and running, but the desired routes aren’t getting exchanged.
Resolve the Problem
In Cisco vManage, check the BGP configuration on the transit cloud routers. During the mapping process, when you configureCisco SD-WAN Cloud OnRamp for IaaS service, BGP is configured to advertise the network address, 0.0.0.0/0. Make sure that the service-side VPN contains an IP
route that points to 0.0.0.0/0. If necessary, add a static route in the VPN feature configuration template, and then reattach
the configuration to the two cloud routers that you selected for the transit VPC or VNet.
On AWS, go to the host VPC and check the route table. In the route table, click Enable route propagation to ensure that the VPC receives the routes.
End-to-End Ping Is Unsuccessful
Problem Statement
Routing is working properly, but an end-to-end ping isn’t working.
Resolve the Problem
On AWS, check the security group rules of the host VPC. On Azure, check the network security group rules of the host VNet.
The security group rules must allow the source IP address range subnets of the on-premises or branch-side devices to allow
traffic from the branch to reach AWS.

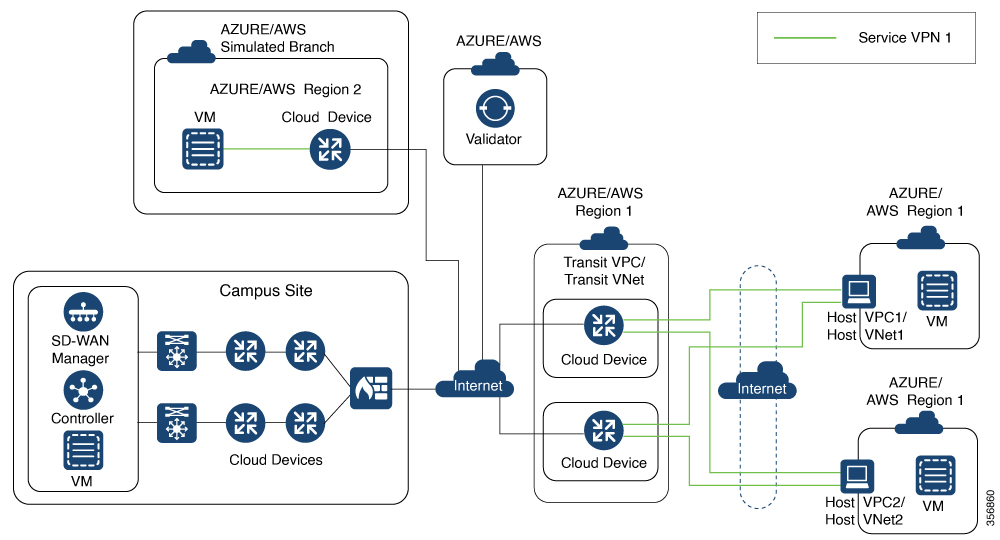
 .
.
 .
.
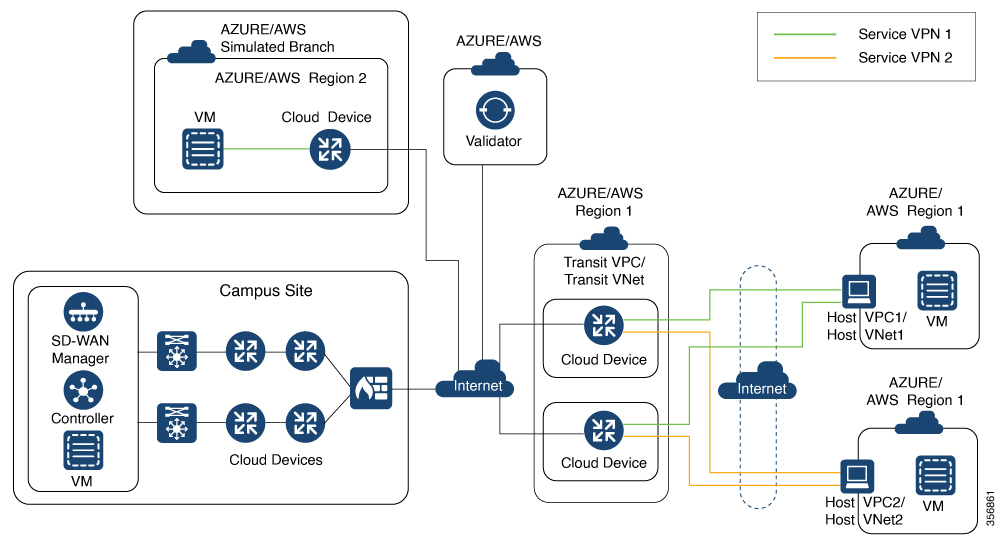
 Feedback
Feedback