On board Devices Using Three-Step Validation
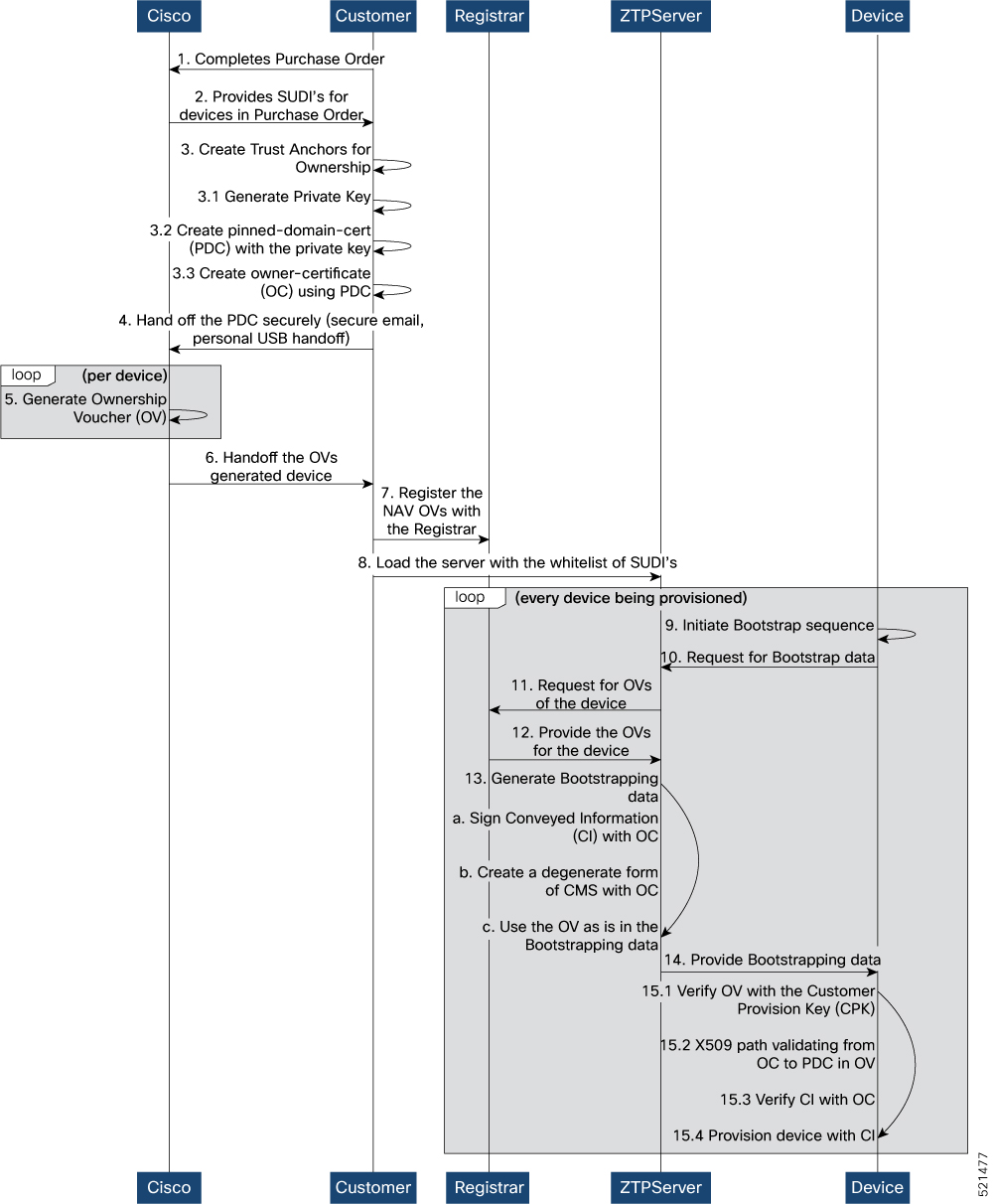
The Cisco IOS XR software implements the secure zero touch provisioning capabilities as described in RFC 8572. Secure ZTP uses a three-step validation process to on board the remote devices securely:
-
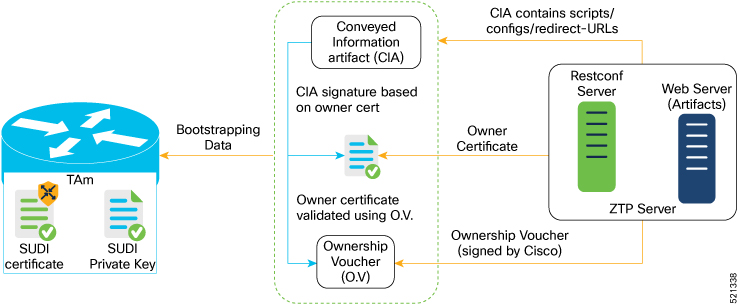
Router Validation: The ZTP server authenticates the router before providing bootstrapping data using the Trust Anchor Certificate (SUDI certificate). Ensure that you have preinstalled the CA certificate chain for Cisco, as this is a prerequisite for the Cisco CA on ZTP server to verify the client/router SUDI certificates. The required certificates are:
-
subject=O = Cisco, CN = ACT2 SUDI CA
-
subject=O = Cisco Systems, CN = Cisco Root CA 2048
-
subject=CN = High Assurance SUDI CA, O = Cisco
-
subject=O = Cisco, CN = Cisco Root CA 2099
-
-
Server Validation: The router device in turn validates the ZTP server to make sure that the on board happens to the correct network. Upon completion, the ZTP server sends the bootstrapping data (for example, a YANG data model) or artifact to the router. See Secure ZTP Components.
-
Artifact Validation: The configuration validates the bootstrapping data or artifact that is received from the ZTP server.



 Feedback
Feedback