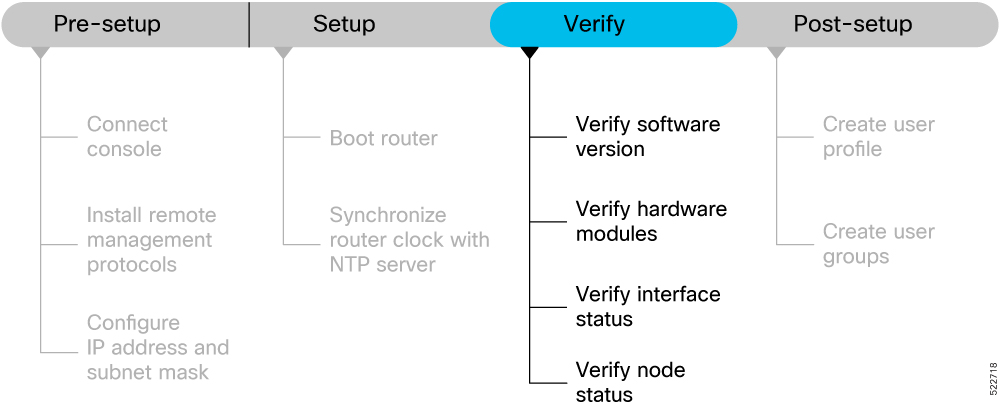
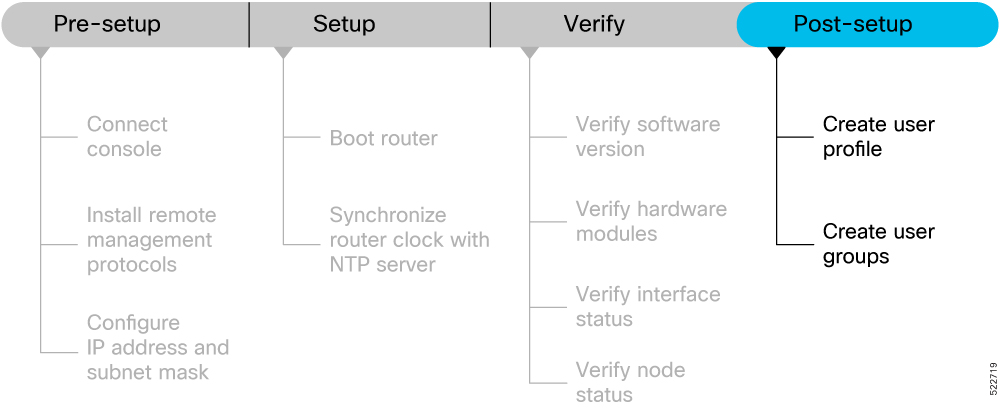
Prerequisites to Setup Router
Complete the following prerequisite tasks to prepare the router for seamless setup.
This section contains the following topics:
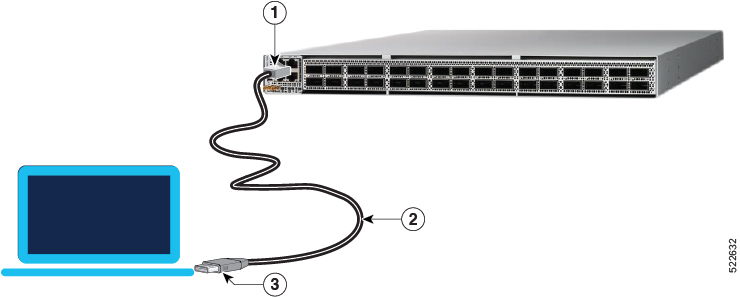
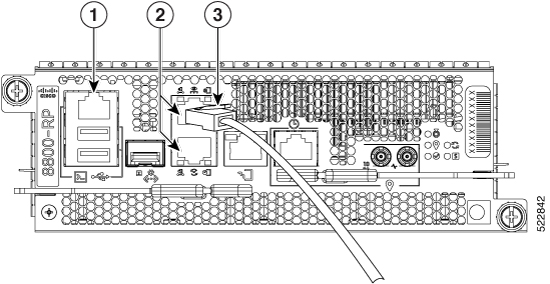
Connect Console Port to Terminal
The console port on the router is used to log into a router directly without a network connection using a terminal emulation program like HyperTerminal.
Procedure
|
Step 1 |
Connect the router to a terminal. |
|
Step 2 |
Configure the console port to match the following default port characteristics. |
|
Step 3 |
Click OK. You should see a blinking cursor in the HyperTerminal window indicating successful connection to the console port. |
Install Remote Management Protocols
The router can be accessed using remote management protocols, such as SSH, SCP, FTP, and Telnet. The SSH, SCP, and FTP management protocols are included in the ISO image by default. Telnet is an optional package.
Procedure
|
Install the remote management protocols. To install Telnet, you can use either of the following options:
|

 Feedback
Feedback