Upgrade Prerequisites and Guidelines
The following sections describe the various requirements for upgrading an existing Nexus Dashboard Fabric Controller (NDFC) or the earlier DCNM software to this release.
-
Ensure that your current Nexus Dashboard cluster is healthy.
You can check the system status on the Overview page of the Nexus Dashboard's Admin Console or by logging in to one of the nodes as
rescue-userand ensuring that theacs healthcommand returnsAll components are healthy. -
If you are upgrading a virtual Nexus Dashboard cluster deployed in VMware ESX, ensure that the ESX version is still supported by the target release.

Note
If you need to upgrade the ESX server, you must do that before upgrading your Nexus Dashboard to the target release:
-
Upgrade one of the ESX hosts as you typically would with your existing Nexus Dashboard node VM running.
-
After the host is upgraded, ensure that the Nexus Dashboard cluster is still operational and healthy.
-
Repeat the upgrade on the other ESX hosts one at a time.
-
After all ESX hosts are upgraded and the existing Nexus Dashboard cluster is healthy, proceed with upgrading your Nexus Dashboard to the target release as described in the following section.
-
-
If you are upgrading from release 12.1.1, ensure that the VRF is correctly set on all existing switches.
For additional information and context, see the Discovery VRF on Existing Switches section below.
-
If you take a backup of the NDFC configuration when upgrading from DCNM release 11.5.4, and then you restore on another release of NDFC (such as NDFC 12.1.3), in some situations during the initial setup, you might see an error message such as
Failed to allocate VLAN or Loopback ID/IP due to range exhausted. This might happen if multiple networks or VRFs, or a combination of networks and VRFs, have the same default VLAN specified and are attached to the same switch, which will result in the default VLAN being set to -1 for the second attached entity. To fix this issue, you must specify an override VLAN to be used on that switch. -
You must perform configuration backups of your Nexus Dashboard and Nexus Dashboard Fabric Controller before the upgrade to safeguard data and minimize any potential risk before proceeding with the upgrade.
-
If you are upgrading from DCNM release 11.5.4, the
trap-ipused in DCNM must not be the Nexus Dashboard management or data IP address. Instead, the IP must be configured in the Nexus Dashboard persistent IP address pool.For more information about configuring persistent IPs, see the "Persistent IP addresses" section of the Cisco Nexus Dashboard Infrastructure Management article.
-
You must disable all preview/beta features and delete the associated data.
In the page, disable all
BETAfeatures.In the page, ensure that Enable Preview Features is disabled.

Note
Disabling a beta feature does not remove any created configurations. For example, if you had enabled the ECL preview feature and created/discovered an ECL fabric, disabling the feature does not remove the existing configuration. In this case, in addition to disabling the feature, you must also delete the configuration before the upgrade.
-
Ensure that you have deleted all NDFC versions except the currently enabled one from your Nexus Dashboard.
You must not have multiple NDFC release images coexisting in the same cluster during the upgrade. Before you upgrade to the next release, navigate to the Nexus Dashboard's Services page, click the ... menu in the NDFC service tile, choose Versions and remove all non-active versions:
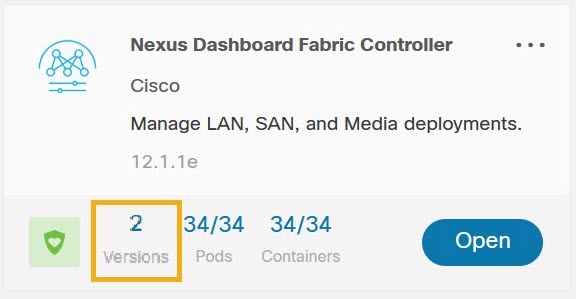
-
Ensure that you have enough external IP addresses configured in your Nexus Dashboard for the Fabric Controller service.
If there are not enough IPs available, such if the IPs are consumed by another service, the NDFC service would not be able to start.
-
You must be running Nexus Dashboard release 2.2(1) or later to upgrade directly to release 3.0(1).

Note
If you are upgrading from NDFC release 12.0.2 or earlier, direct upgrades are not supported. You must first upgrade to release 12.1.1 and then to release 12.1.3. See the upgrade workflows table below for additional information.
-
You must disable all services running in the cluster before upgrading to release 3.0(1) or later.

Note
After you have upgraded your Nexus Dashboard to release 3.0(1), you must not re-enable the existing NDFC versions that you had disabled prior to the Nexus Dashboard upgrade.
You must also not delete the existing versions of the service, which may now display an
App Version not compatible. Upgrade required.error: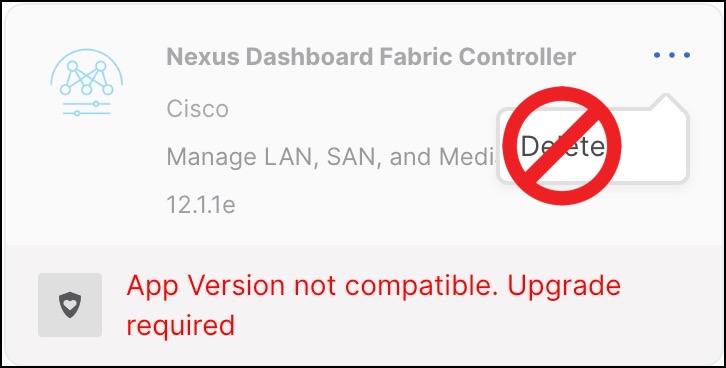
-
Ensure that no configuration changes are made to the cluster, such as adding worker or standby nodes, while the upgrade is in progress.
-
Nexus Dashboard and Nexus Dashboard Fabric Controller do not support software downgrades.
If you want to downgrade to an earlier release, you will need to deploy a new cluster and reinstall the services.
-
We recommend that you do not upgrade any underlying third-party software separately. All the necessary software components will be updated during the inline upgrade procedure. Upgrading the components outside of Nexus Dashboard Fabric Controller upgrade may cause functionality issues.
Discovery VRF on Existing Switches
 Note |
The following information applies to NDFC upgrades from release 12.1.1; if you are upgrading from release 12.1.2, you can skip this subsection. |
Reachability from NDFC to the switches is controlled by the routes configuration in the Nexus Dashboard cluster. By default, all NDFC pods have their default gateway set to the Nexus Dashboard's data interface gateway. However, for pods with persistent IPs (External Service IPs), the default gateway is set based on the specific management or data interface associated with the persistent IP pool:
-
If a pod is using an external service IP from the management subnet, its default gateway is set to the Nexus Dashboard's management interface gateway.
-
If a pod is using an external service IP from the data subnet pool, its default gateway is set to the Nexus Dashboard's data interface gateway.
NDFC's discovery pod requires IP reachability to the switches and does not have a persistent IP, so the pod's reachability to the switches depends on how routing is configured from the switches to the Nexus Dashboard cluster that is hosting the NDFC service. However, some of the pod's operations require reverse reachability from the switches to NDFC. For example, when NDFC is set as a trap-host destination for a switch, you must specify the VRF over which this IP is reachable in addition to the NDFC syslog-trap External Service IP configuration on that switch. Similarly, when a switch executes an SCP copy command to copy images for Image Management purposes, the VRF must be specified for the switch to reach the SCP destination IP (External Service IP associated with NDFC's poap-scp pod). As a result, for every switch, you must associate a VRF that can be used for connectivity from the switch to NDFC.
When NDFC's LAN Device Management Connectivity is set to Management (default setting), the POAP-SCP and SNMP-Trap pods get persistent IPs from the Management External Service IP pool. In this
case, switches must be imported into NDFC using the switches' mgmt0 IP address, which must be reachable from NDFC over the Nexus Dashboard's management interface. For switches that are reachable
via Layer 3, this requires static routes to be configured in the Nexus Dashboard's (previously, ). For these switches, the VRF associated with the switch gets set to management.
On the other hand, when NDFC's LAN Device Management Connectivity is set to Data, the POAP-SCP and SNMP-Trap pods get persistent IPs from the Data External Service IP pool and are reachable over the Nexus
Dashboard data interface. In this case, you must also enable the When LAN Device Management Connectivity is set to Data, rely on LAN discovery to always populate VRF for all Nexus Switches option for the VRF to be properly populated for the switch.
In NDFC release 12.1.1, the above option was disabled by default, which means that any switch imported into NDFC had its VRF
set to “default”. In this case, you had to enable reachability from the switch to NDFC via the front-panel interface or update the discovery
VRF for the switch for the persistent IPs associated with the POAP-SCP and SNMP-Trap pods to be reachable. However, if you
did not use Image Management or trap-related functionality and did not enable reachability from the switch to NDFC, you would
not notice that the reverse communication from the switch to NDFC was not working because NDFC-to-switch communication would
continue to function via either Nexus Dashboard's management or data interface.
Beginning with release 12.1.2, the When LAN Device Management Connectivity is set to Data, rely on LAN discovery to always populate VRF for all Nexus Switches option is enabled by default. So NDFC would properly populate the discovery VRF from the switch configuration during switch discovery.
As a result of the default setting change, if you are upgrading from release 12.1.1, you may run into an issue where the VRF is not set on the switch and you must manually update it using the GUI or API to establish proper reachability from your existing switches to NDFC. Note that if you had already explicitly configured the VRF for your existing switches, it is preserved during the upgrade but any switch whose VRF is currently set to "default" is not updated regardless of the change in default value of the When LAN Device Management Connectivity is set to Data, rely on LAN discovery to always populate VRF for all Nexus Switches setting unless the switch is removed and re-added.
Upgrade Workflow Overview
The following table summarizes the upgrade workflows required to upgrade from your current NDFC release to release 12.1.3.
| Current Release | Nexus Dashboard Version for the Current Release | Upgrade workflow when upgrading to release 12.1.3 |
|---|---|---|
|
12.1.2 |
2.3.x |
For detailed instructions, see Upgrading From NDFC Release 12.1.x. |
|
12.1.1e |
2.2.x |
For detailed instructions, see Upgrading From NDFC Release 12.1.x. |
|
12.0.2f |
2.1.2d |
Direct upgrade is not supported. We recommend upgrading your NDFC to release 12.1.2 as described in the Nexus Dashboard Fabric Controller Installation and Upgrade Guide, Release 12.1.2e before returning to this document to upgrade to release 12.1.3. |
|
12.0.1a |
2.1.1e |
Direct upgrade is not supported. We recommend upgrading your NDFC to release 12.1.2 as described in the Nexus Dashboard Fabric Controller Installation and Upgrade Guide, Release 12.1.2e before returning to this document to upgrade to release 12.1.3. |
|
11.5(4) |
Not Applicable |
For detailed instructions, see Upgrading from DCNM (Data Center Network Manager). |
 Feedback
Feedback