Overview
This release of Multi-Site Orchestrator must be deployed as an application in Cisco Nexus Dashboard. The previously supported VMware ESX virtual appliance and Cisco Application Services Engine form factors are now deprecated.
The following sections describe how to migrate an existing Cisco Multi-Site Orchestrator to Release 3.3(1) on Nexus Dashboard platform.
If your MSO cluster is already deployed in Nexus Dashboard, follow the steps described in Upgrading or Downgrading MSO Application instead.
Migration Workflow
The following list provides a high level overview of the migration process and the order of tasks you will need to perform.
A video demonstrating the MSO-specific steps is available at Migrating from MSO 3.1 to MSO 3.3 on Nexus Dashboard. Note that the video does not replace a complete list of requirements and steps listed in this chapter, such as Nexus Dashboard deployment and Cloud APIC site upgrades.
-
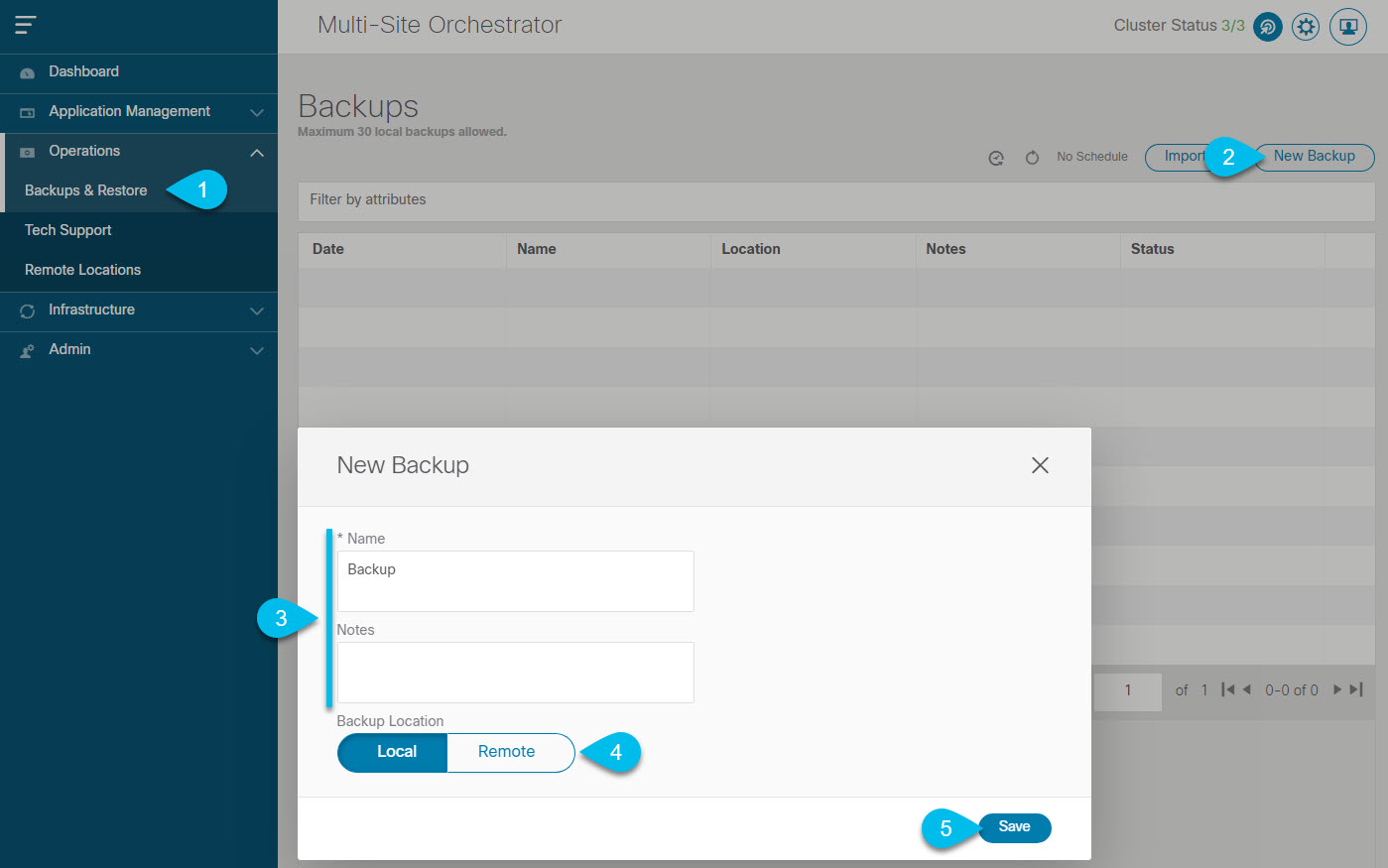
Back up existing Multi-Site Orchestrator configuration and disconnect or bring down the existing MSO cluster.
If you deploy a brand new Nexus Dashboard cluster rather than upgrade an existing cluster, we recommend preserving the existing MSO cluster until the new cluster is deployed and configuration is restored.
-
Deploy a Nexus Dashboard cluster using physical, virtual, or cloud form factor.
-
(Optional) Configure the Nexus Dashboard cluster with additional nodes if required for application co-hosting.
-
(Optional) Configure remote authentication servers in the Nexus Dashboard if required by your existing Multi-Site Orchestrator deployment.
-
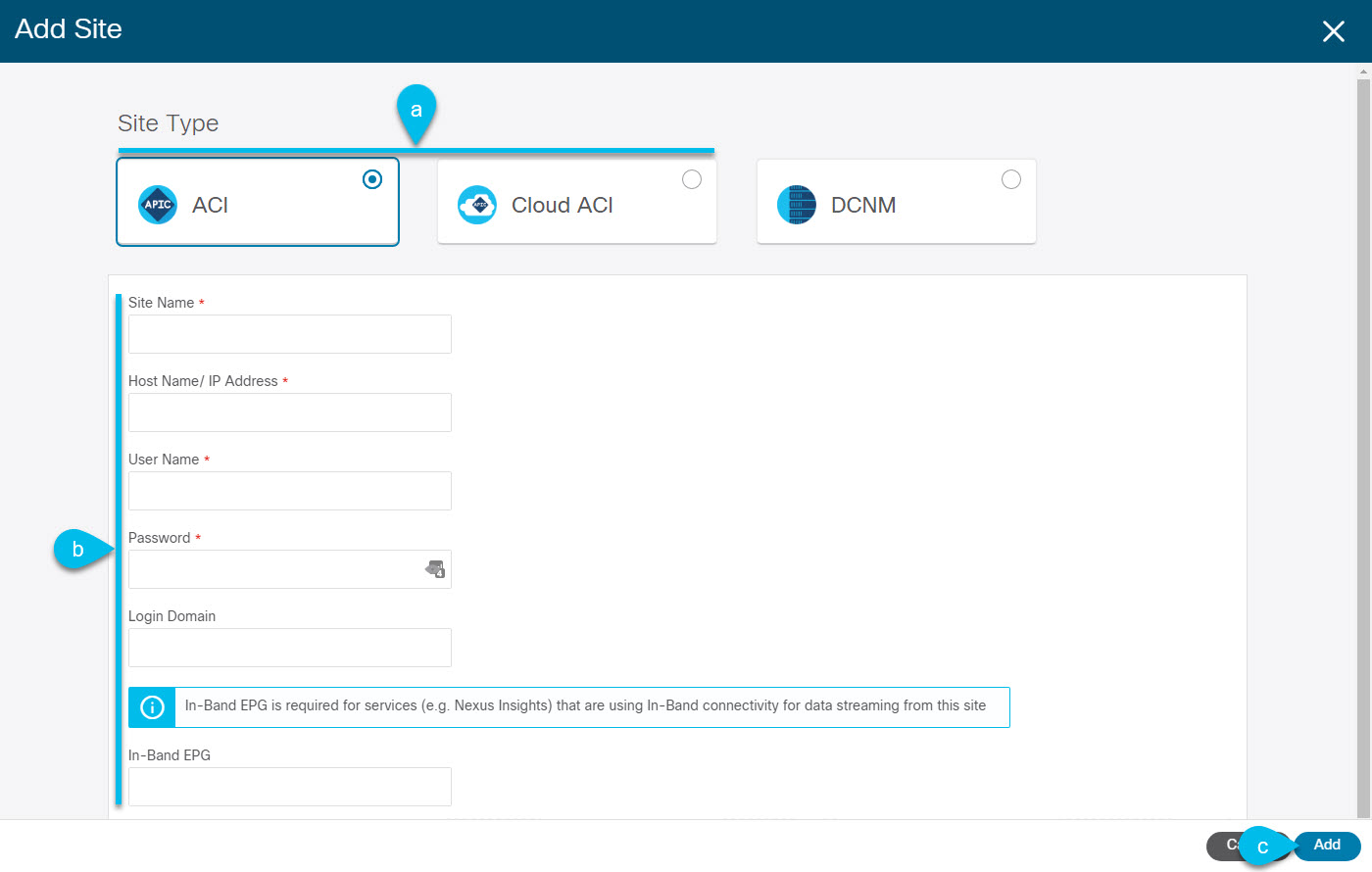
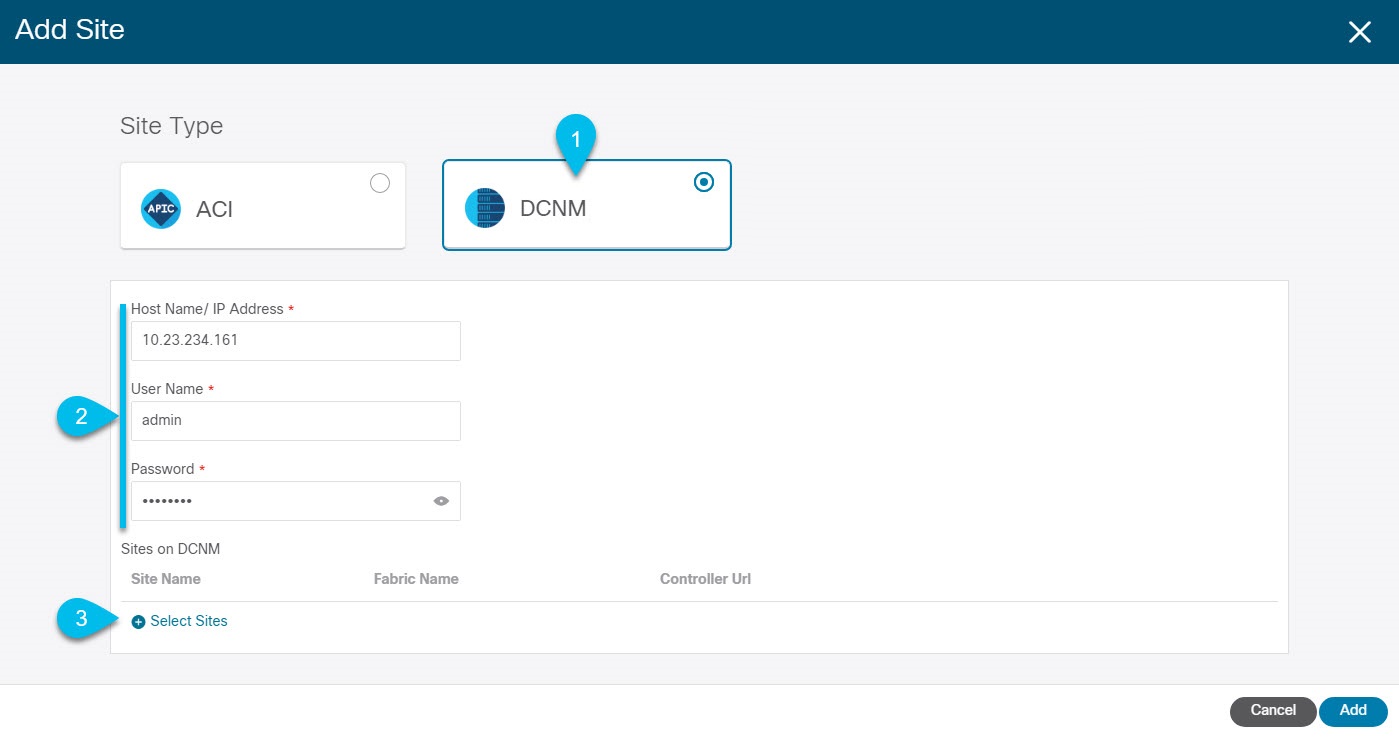
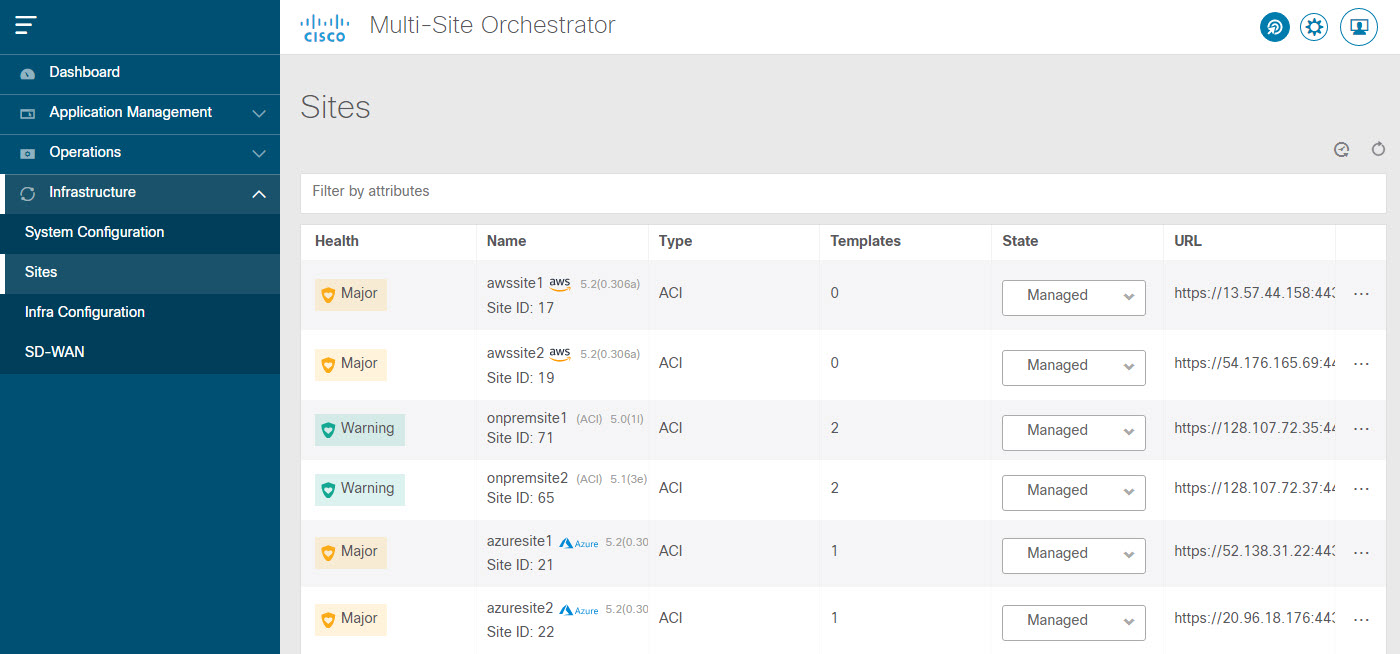
On-board the APIC, Cloud APIC, or DCNM sites that you currently manage from the Multi-Site Orchestrator to the Nexus Dashboard.
-
Install the Multi-Site Orchestrator application in the Nexus Dashboard.
-
Restore the configuration backup in the new MSO application installed in the Nexus Dashboard.
-
Upgrade cloud sites to Cloud APIC release 5.2(x) one site at a time.
You will upgrade a site's Cloud APIC, then that site's CSRs, then repeat the procedure for each additional site.
-
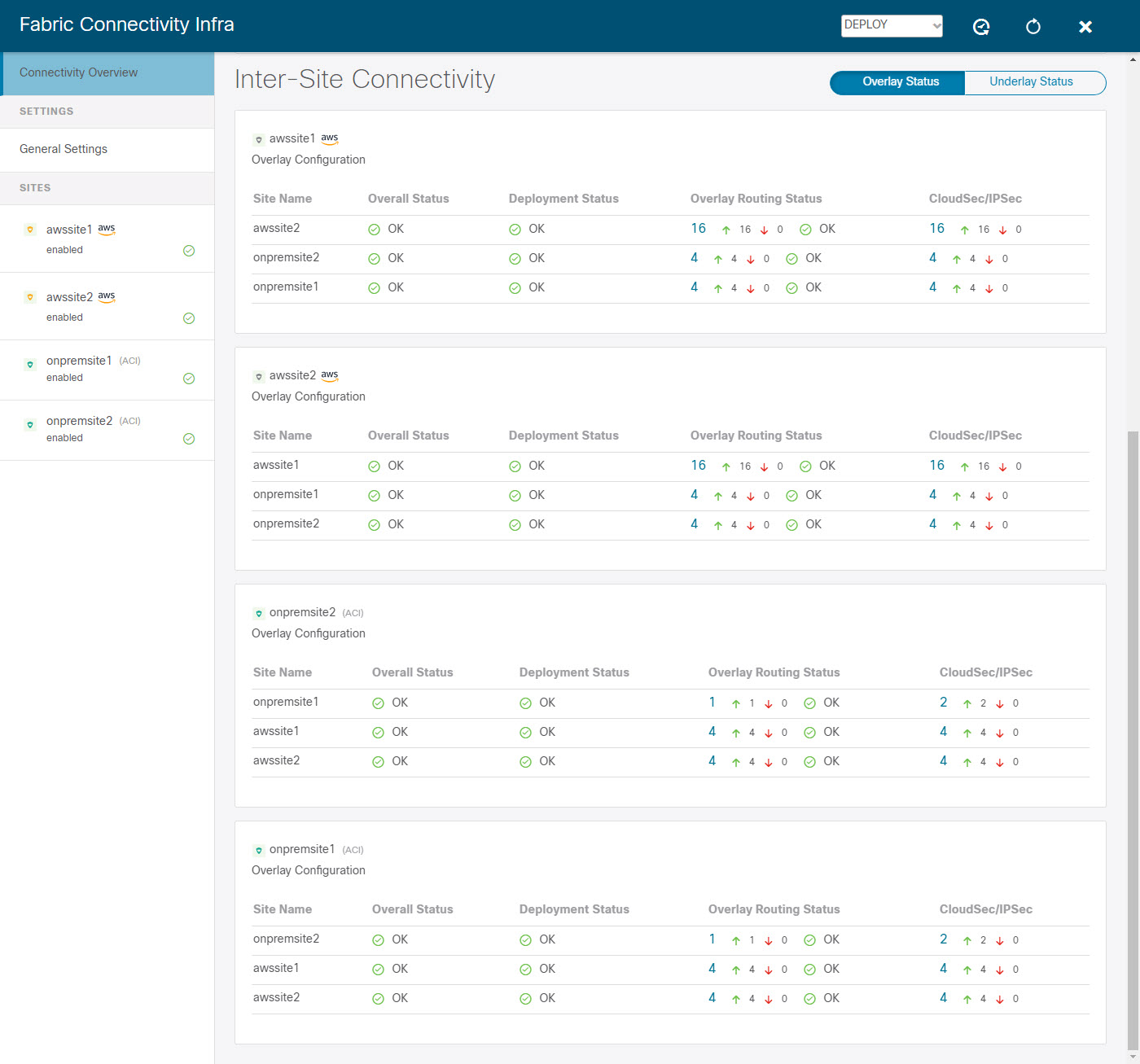
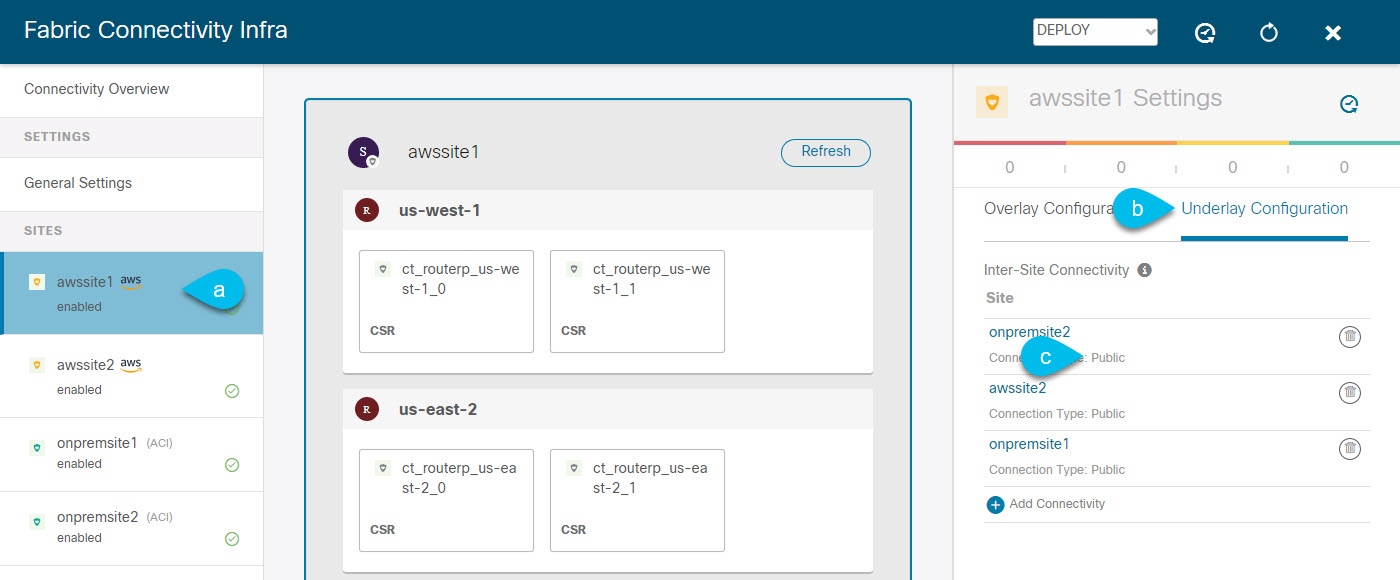
Update Infra configuration settings in Multi-Site Orchestrator.

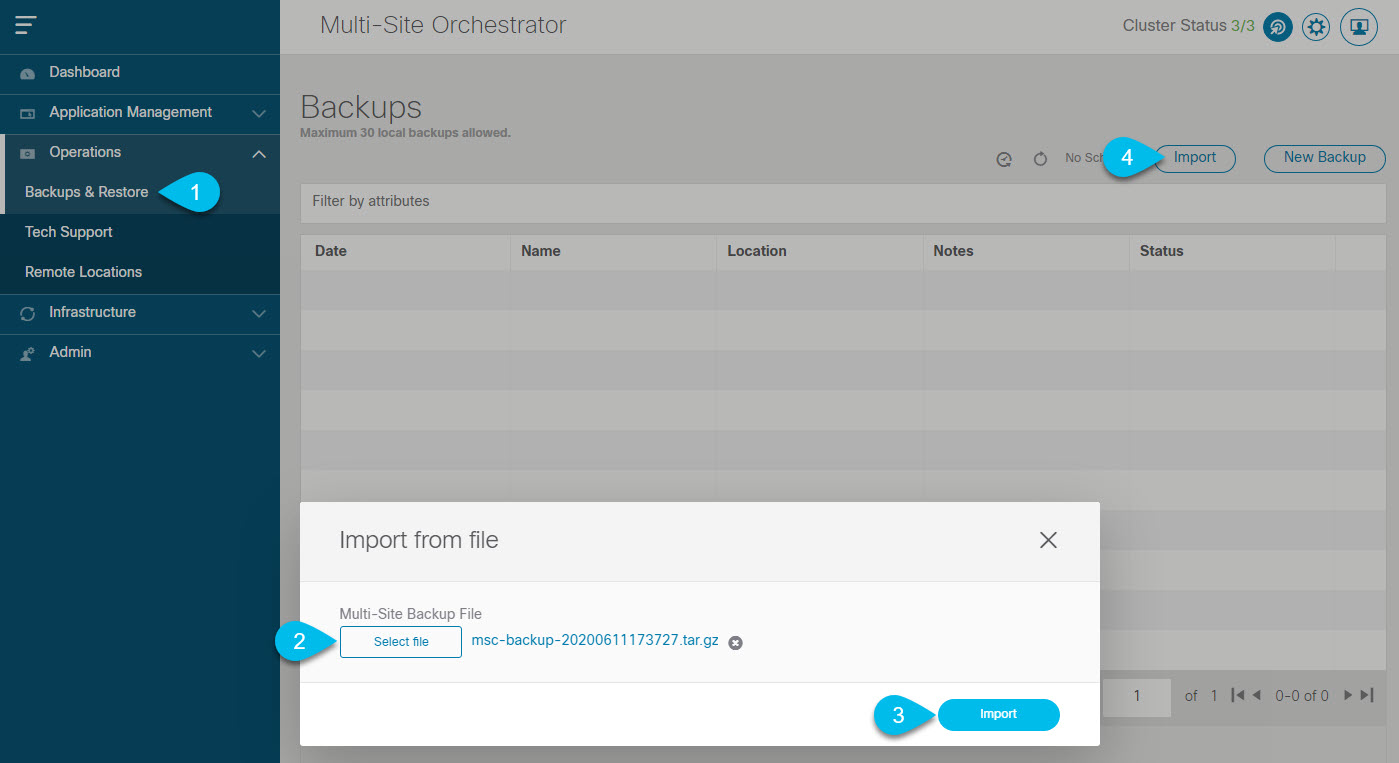
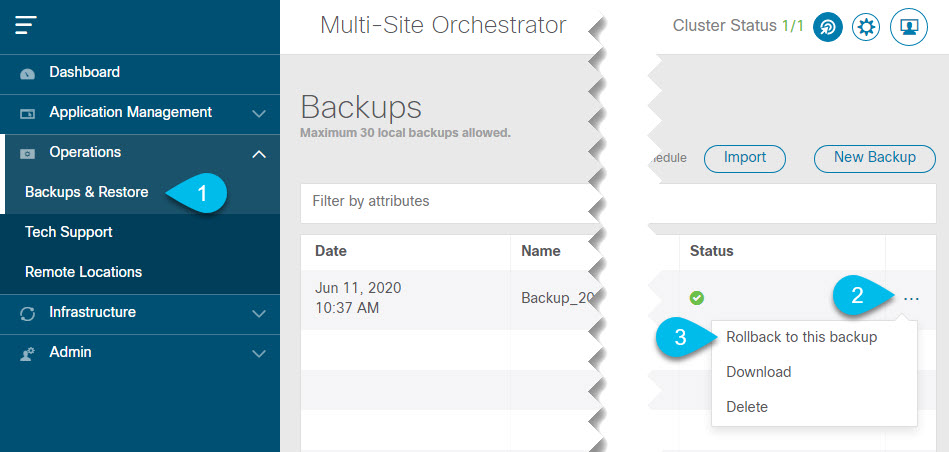
 ) icon next to the backup and select
) icon next to the backup and select 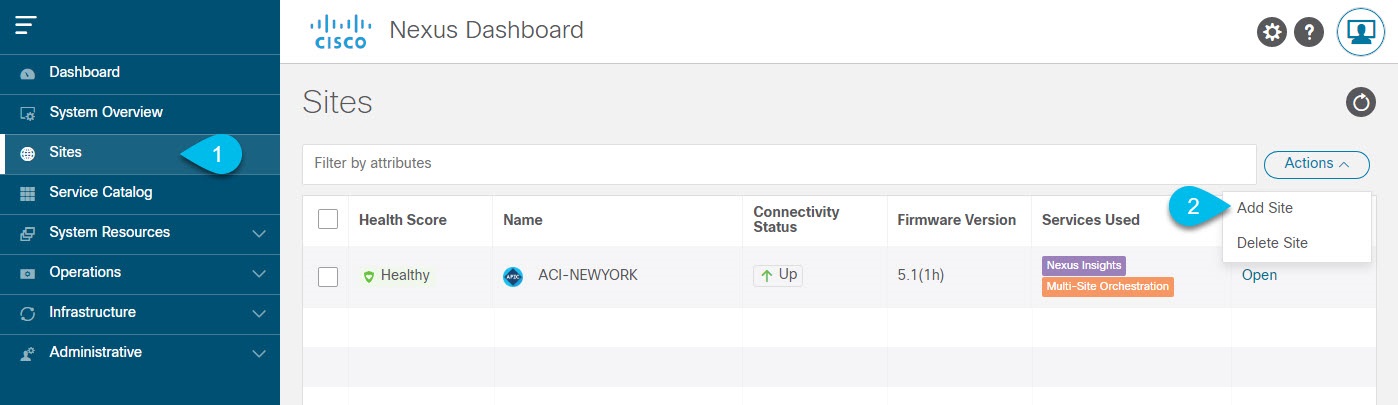

 Feedback
Feedback