Overview
CAPWAP is an IEEE standard protocol that enables a wireless LAN controller to manage multiple APs and Wireless LAN Controllers (WLCs) to exchange control and data plane information over a secure communication tunnel.
CAPWAP only operates in Layer 3 and requires IP addresses to be present on both the APs and WLC. CAPWAP establishes tunnels on the UDP ports 5246 and 5247 for IPv4 and IPv6 respectively. It adds extra security with Datagram Transport Layer Security (DTLS) encryption.
DTLS serves as a protocol ensuring security between the AP and WLC, facilitating encrypted communication to prevent eavesdropping or tampering in potential man-in-the-middle attacks.
By default, DTLS secures the control channel for CAPWAP, encrypting all CAPWAP management and control traffic between the AP and WLC.
The data channel remains disabled by default, leaving client data moving between an AP and WLC unencrypted. Enabling CAPWAP data encryption is discretionary, and it necessitates the installation of a DTLS license on the WLC before activation on an AP.
If an AP does not support DTLS data encryption, DTLS is enabled only for the control plane, and a DTLS session for the data plane is not established
If an AP supports Data DTLS, it enables data DTLS after receiving the new configuration from the controller. The AP performs a DTLS handshake on port 5247 and after successfully establishing the DTLS session. All the data traffic (from the AP to the controller and the controller to the AP) is encrypted.
CAPWAP allows administrators to manage the entire wireless network from a central location. The IW9165D use the Internet Engineering Task Force (IETF) standard CAPWAP to communicate between the controller and other AP on the network.

Certificate Provisioning on Lightweight Access Point
In order to provision a new certificate on LAP, while in CAPWAP mode, the LAP must be able to get the new signed X.509 certificate. In order to do this, it sends a certRequest to the controller, which acts as a CA proxy and helps obtain the certRequest signed by the CA for the LAP.
The certReq and the certResponses are sent to the LAP with the LWAPP payloads.
Both the LSC CA and the LAP device certificates are installed in the LAP, and the system reboots automatically. The next time when the system comes up, because it is configured to use LSCs, the AP sends the LSC device certificate to the controller as part of the JOIN Request. As part of the JOIN Response, the controller sends the new device certificate and also validates the inbound LAP certificate with the new CA root certificate.
What to Do Next
To configure, authorize, and manage certificate enrollment with the existing PKI infrastructure for controller and AP, you need to use the LSC provisioning functionality.
Understanding CAPWAP Connectivity On AP
When CAPWAP is enabled, the first function is to initiate a discovery phase. Wireless APs search for a controller by sending discovery request messages. Upon receiving a discovery request, the controller replies with a discovery response. At this point, the two devices establish a secure connection using the Datagram Transport Layer Security (DTLS) protocol to exchange CAPWAP control and data messages.
By using CAPWAP discovery mechanisms, then AP sends a CAPWAP join request to the controller. The controller sends a CAPWAP join response to the AP that allows the AP to join the controller. When the AP joins the wireless controller, the wireless controller manages its configuration, firmware, control transactions, and data transactions.
The CAPWAP has two channels, namely control and data. The AP uses the control channel to send configuration messages, download images and client keys, or receive the context. The control channel has a single window in the current implementation. The APs must acknowledge every message sent from the controller in a single window. The APs does not transmit the next control packet until it acknowledges the earlier one.
CAPWAP data channel facilitates the encapsulation and tunneling of user data traffic between APs and WLCs. This provide centralized management of user data flow, enabling the WLC to enforce policies, apply Quality of Service (QoS), and ensure security measures consistently across the wireless network. The user data is encapsulated within CAPWAP frames, allowing it to be transported between the APs and WLCs.
According to IETF, CAPWAP supports two modes of operation:
-
Split Media Access Control (MAC): A key component of CAPWAP is the concept of a split MAC, where part of the 802.11 protocol operation is managed by the CAPWAP AP, while the remaining parts are managed by the WLC.
In split MAC mode, the CAPWAP protocol encapsulates all Layer 2 wireless data and management frames, which are then exchanged between the WLC and AP.
Figure 2. Split MAC Architecture 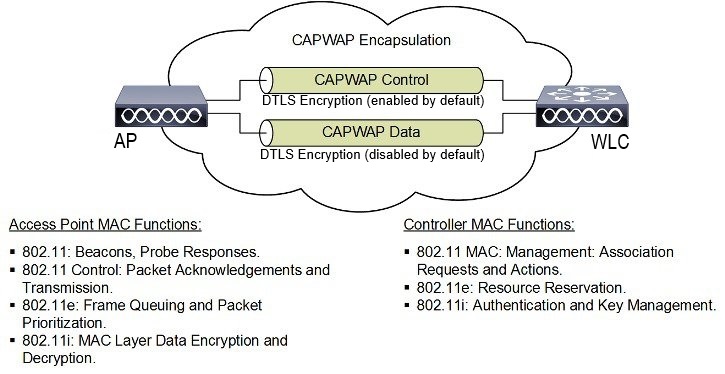
-
Local MAC: Local MAC mode enables data frames to be locally bridged or tunneled as Ethernet frames.
Local MAC where all the wireless MAC functions are performed at the AP. The complete 802.11 MAC functions, including management and control frame processing, are resident on the APs.
In either mode, the AP processes Layer 2 wireless management frames locally and then forwards them to the controller.
Reset Button Settings
The following reset actions are performed in the IW9165D when the LED turns to blinking red (after the boot loader gets the reset signal). Ensure you to press the device's reset button before the device is powering on.
-
Keep the button pressed for < 20 seconds for full reset.
-
Keep the button pressed for > 20 seconds and < 60 seconds for full factory reset (clear fips flag).
Ethernet Port Usage On CAPWAP Mode
The Catalyst IW9165D supports up to a 3.6 Gbps PHY data rate with two 2x2 multiple input and multiple output (MIMO) and two ethernet ports (2.5G mGig and 1G).
Catalyst IW9165D have below internal port mapping rules:
-
Wired0 – One mGig (2.5 Gbps) ethernet ports with 802.3af, 802.3at, 802.3bt PoE support.

Note
The wired0 port is used as CAPWAP uplink port in the AP local/Flexconnect mode.
-
Wired1 – 1Gig ethernet Lan Port.

Note
Starting from 17.14.1 release, RLAN feature is not supported in the wired1 port.
 Feedback
Feedback