RUM Reporting and Acknowledgment Requirement for Cisco Catalyst 9800-CL Wireless Controller
About This Requirement
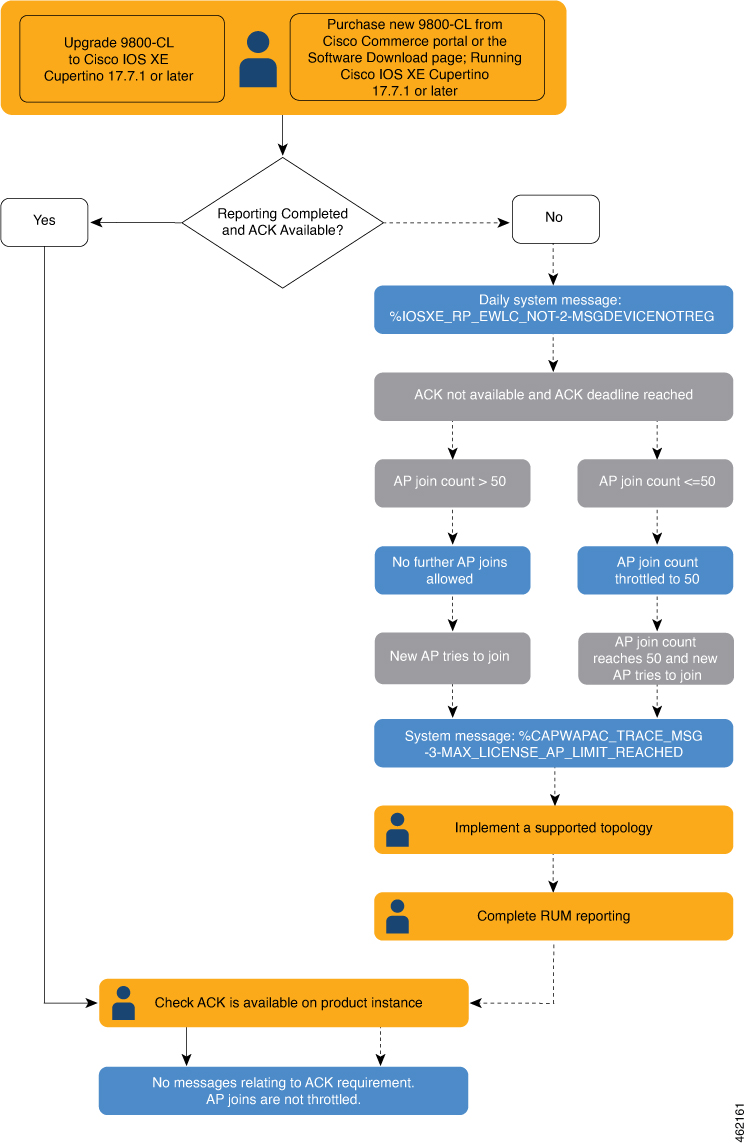
Beginning with Cisco IOS XE Cupertino 17.7.1, if you are using a Cisco Catalyst 9800-CL Wireless Controller, you must complete RUM (Resource Utilization Measurement) reporting and ensure that the Acknowledgment (ACK) is made available on the product instance - at least once. This is to ensure that correct and up-to-date usage information is reflected in CSSM.
Prior to Cisco IOS XE Cupertino 17.7.1, RUM reporting and ACK installation was not mandatory for a Cisco Catalyst 9800-CL Wireless Controller (unlike other Cisco Catalyst Wireless Controllers).
This requirement is applicable to:
-
A new Cisco Catalyst 9800-CL Wireless Controller purchased through the Cisco Commerce portal or downloaded from the Software Download page, and where the software version running on the product instance is Cisco IOS XE Cupertino 17.7.1 or a later release.
-
An existing Cisco Catalyst 9800-CL Wireless Controller that is upgraded to Cisco IOS XE Cupertino 17.7.1 or later release.
Required Action to Meet This Requirement
The following procedure provides information about what you have to do to ensure compliance with this requirement and avoid any throttling restrictions on new and upgraded product instances. This procedure is followed by a flow chart which depicts the same information.
-
Check when the ACK is expected. Note system behavior if you don't meet the ACK deadline.
Enter the show license air entities summary command in privileged EXEC mode and check field
License Ack expected within.....................: [n] days.System behavior if you do not meet the ACK deadline:

Note
If the number of AP joins is greater than 10, the system displays this system message once-a-day until an ACK is installed: %IOSXE_RP_EWLC_NOT-2-MSGDEVICENOTREG.
-
If an ACK is not installed by the ACK deadline, and the count of currently active APs is lesser than or equal to 50, the system throttles the AP join count to 50.
-
If an ACK is not installed by the ACK deadline and the count of currently active APs is greater than 50, these currently active APs are not disconnected, but no new AP joins are allowed.
-
If there is a reload after the throttled state has come into effect, the system throttles the number of currently active APs to 50 when the system comes up after reload.
-
If there is a stateful switchover (SSO) after the throttled state has come into effect, all connected APs remain joined.
-
The following system message is displayed when the throttling restriction is effective and a new AP tries to join: %CAPWAPAC_TRACE_MSG-3-MAX_LICENSE_AP_LIMIT_REACHED.
The AP join restriction and the display of the system messages continues until the first ACK is made available on the product instance.
-
-
Implement a supported topology.
If you have not already done so, implement one of the supported topologies and complete usage reporting. The method you use to send the RUM report to CSSM and ACK installation depends on the topology you implement.
For more information, see: Connecting to Cisco SSM and Implementing Smart Licensing Using Policy.
-
Ensure that the ACK is available on the product instance.
In the output of the show license status command in privileged EXEC mode check for an updated timestamp in the Last ACK received:.Device# show license status <output truncated> Usage Reporting: Last ACK received: <none> Next ACK deadline: <none> Reporting push interval: 0 (no reporting) Next ACK push check: <none> Next report push: <none> Last report push: <none> Last report file write: <none>In the output of the show license air entities summary command in privileged EXEC mode, the License Ack expected within.....................: [n] daysfield is no longer displayed.Device# show license air entities summary Upcoming license report time....................: 21:05:16.092 UTC Mon Oct 25 2021 No. of APs active at last report................: 57 No. of APs newly added with last report.........: 57 No. of APs deleted with last report.............: 0Once the first ACK is installed, the system messages ( %IOSXE_RP_EWLC_NOT-2-MSGDEVICENOTREG and %CAPWAPAC_TRACE_MSG-3-MAX_LICENSE_AP_LIMIT_REACHED) are not displayed any longer and AP join throttling restrictions are lifted.
Figure 1. Flow Chart of System Events, User Actions, and System Actions on a Cisco Catalyst 9800-CL Wireless Controller 
 Feedback
Feedback