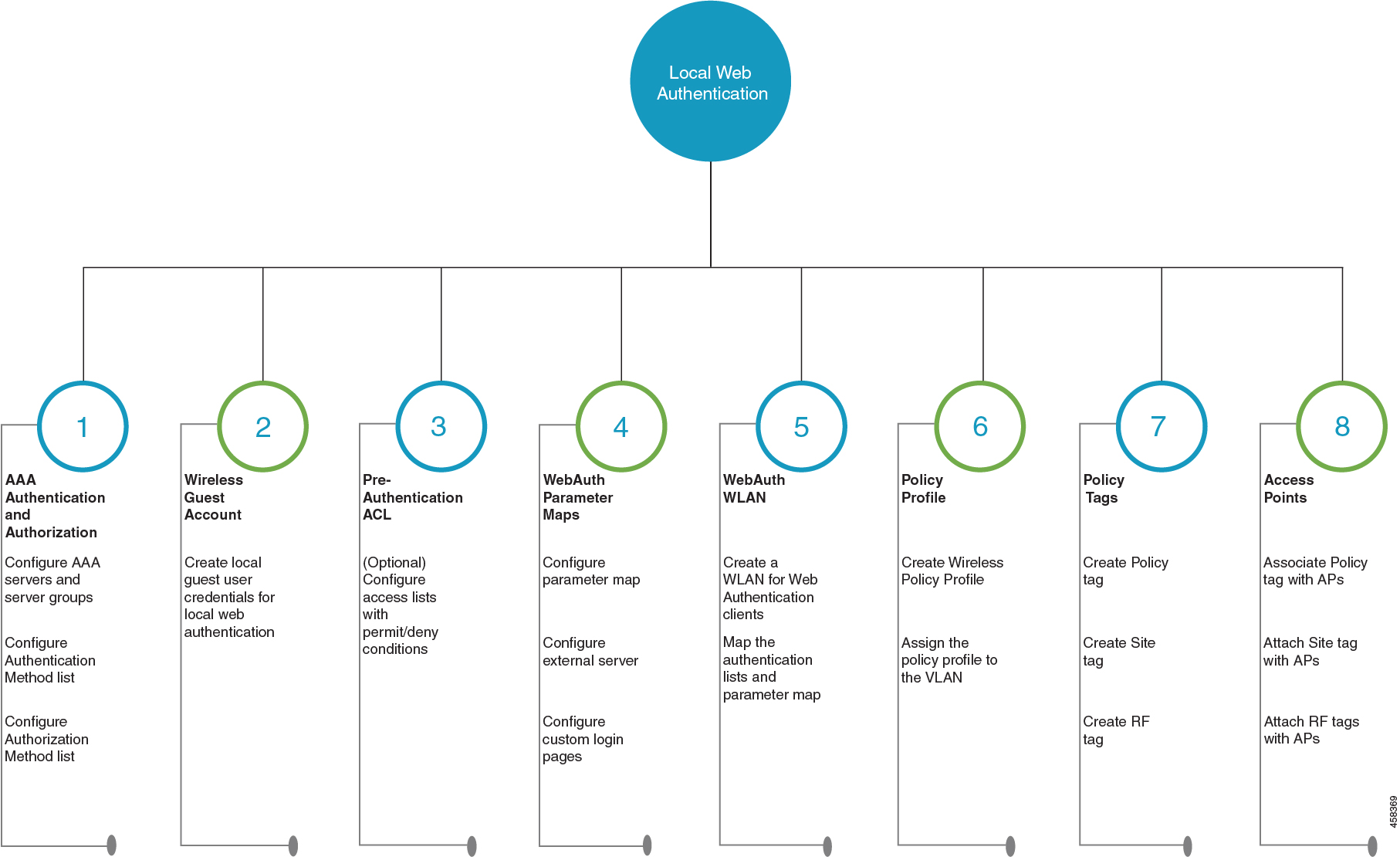
Configure Local Web Authentication using the CLI
Configure AAA Server and Server Groups
When trying to access the WLC, you will be prompted to enter a username and password in order to let you connect to the guest network. By default, these credentials are validated against the local database of users on the controller. Alternatively, you can set up a remote AAA RADIUS or LDAP server for authentication.
Procedure
| Step 1 |
enable Example:Enables privileged EXEC mode.
|
| Step 2 |
configure terminal Example:Enters global configuration mode. |
| Step 3 |
To configure LDAP server, do the following: |
| Step 4 |
To configure RADIUS server, do the following: |
| Step 5 |
To configure TACACS+ server, do the following: |
| Step 6 |
exit Example: |
| Step 7 |
aaa group server {ldap | radius | tacacs+} server-group Example:server-group refers to the server group name with a maximum length of 32 strings. |
| Step 8 |
server name server-name Example:If you have multiple LDAP/RADIUS/TACACS+ servers that can be used for authentication, it is recommended to map all these servers to the same server group. The WLC handles load balancing different authentications among the servers in the server group. |
| Step 9 |
end Example:Exits the global configuration mode and returns to privileged EXEC mode. |
Configure Local Authentication and Authorization
A method list is a sequential list describing the authentication and authorization methods to be queried to authenticate a user. Method lists enable you to designate one or more security protocols to be used for authentication and authorization, thus ensuring a backup system in case the initial method fails.
Configure the following steps to specify the local username database as the method of user authentication at login.
Procedure
| Step 1 |
enable Example:Enables privileged EXEC mode.
|
| Step 2 |
configure terminal Example:Enters global configuration mode. |
| Step 3 |
aaa new-model Example:Enables AAA functionality. |
| Step 4 |
aaa authentication login {default | list-name} local group AAA-server-group Example:The list-name is a character string used to name the list you are creating. The list-name should not exceed 255 characters. group AAA_server_group lets you specify the AAA server group that you have created for authorization. |
| Step 5 |
aaa authorization network {default | list-name} local group AAA_server_group Example:group AAA_server_group lets you specify the AAA server group that you have created for authorization. |
| Step 6 |
user-name user name Example:Creates guest user name in the local database, and establishes a username-based authentication system. For user-name , specify the user ID as one word. Spaces and quotation marks are not allowed. |
| Step 7 |
password {encryption-type | password} Example:
Configures the password for the guest user name in the local database. |
| Step 8 |
end Example:Exits the global configuration mode and returns to privileged EXEC mode. |
Configure Parameter Maps
A parameter map allows you to modify parameters that control the behavior of actions configured under a control policy. A parameter map for web-based authentication sets parameters that can be applied to subscriber sessions during authentication. If you do not create a parameter map, the policy uses default parameters.
Before you begin
-
You have already downloaded and installed a third-party certificate signed by a trusted certificate authority on the controller. Applicable only if you are opting to use third-party certificates.
Procedure
| Step 1 |
enable Example:Enables privileged EXEC mode.
|
||
| Step 2 |
configure terminal Example: |
||
| Step 3 |
Configure the global parameter map as follows: |
||
| Step 4 |
Configure the named parameter map as follows:
|
Enables you to configure the global and user-defined parameter maps which is required for external and internal Web Authentication
Configure WLAN Security Parameters
WLAN profile defines the properties of a WLAN such as Profile Name, Status, WLAN ID, L2 and L3 Security parameters, AAA Server associated with this SSID and other parameters that are specific to a particular WLAN.
Before you begin
-
Ensure that you have configured a parameter map for web authentication.
-
Ensure that you have configured a authentication method list for web authentication.
-
Run the show wlan summary command to view the configured security types.
Procedure
| Step 1 |
enable Example:Enables privileged EXEC mode.
|
||
| Step 2 |
configure terminal Example:Enters global configuration mode. |
||
| Step 3 |
wlan profile-name wlan-id ssid-name Example:Specifies the WLAN name and ID. profile-name is the WLAN name which can contain 32 alphanumeric characters. wlan-id is the wireless LAN identifier. The valid range is from 1 to 512. ssid-name is the SSID which can contain 32 alphanumeric characters. |
||
| Step 4 |
no security wpa Example:Disables the WPA security, if configured. |
||
| Step 5 |
Configure layer 2 security, as required. You can configure open authentication or a combination of any of the following supported security methods.
|
||
| Step 6 |
security web-auth Example:Enables web authentication for WLAN. |
||
| Step 7 |
security web-auth {authentication-list authentication-list-name} Example:Enables authentication list for for web authentication. authentication-list authentication-list-name : Sets the authentication list for IEEE 802.1X.
|
||
| Step 8 |
security web-auth {authorization-list authorization-list-name} Example:Enables authorization list for for web authentication. authorization-list authorization-list-name : Sets the override-authorization list for IEEE 802.1X.
|
||
| Step 9 |
security web-auth parameter-map parameter-map-name} Example:
|
||
| Step 10 |
end Example:Returns to privileged EXEC mode. |
Create Wireless Policy Profile
Policy profile contains policy to be associated with the WLAN. It specifies the settings for client VLAN, Authentication, Authorization, and Accounting (AAA), Access Control Lists (ACLs), session and idle timeout settings and so on.
Before you begin
Ensure you have created the VLANs for assigning the wireless clients.
Procedure
| Step 1 |
enable Example:Enables privileged EXEC mode.
|
| Step 2 |
configure terminal Example:Enters global configuration mode. |
| Step 3 |
wireless profile policy profile-name Example:Configures the WLAN policy profile. |
| Step 4 |
vlan vlan-name Example:Assigns the profile policy to the VLAN. |
| Step 5 |
no shutdown Example:Restarts the WLAN. |
| Step 6 |
end Example:Returns to privileged EXEC mode. |
Create a Policy Tag
A policy tag constitutes mapping of the WLAN profile to the policy profile. The WLAN profile defines the wireless characteristics of the WLAN. The policy profile defines the network policies and the switching policies for the client.
You can either create a new policy tag or use the default policy tag. The default policy tag automatically maps any SSID with a WLAN ID between 1 to 16 to the default policy profile. It cannot be modified nor deleted. If you have a WLAN with ID 17 or higher, the default policy tag cannot be used.
Before you begin
-
Ensure you have configured a WLAN for web authentication.
-
Ensure you have configured a WLAN policy profile.
Procedure
| Step 1 |
configure terminal Example:Enters global configuration mode. |
| Step 2 |
wireless tag policy policy-tag-name Example:Configures a policy tag and enters policy tag configuration mode. |
| Step 3 |
wlan wlan-name policy profile-policy-name Example:Maps the WLAN policy profile to a WLAN profile. |
| Step 4 |
end Example:Saves the configuration, exits configuration mode, and returns to privileged EXEC mode. |
Configure a Site Tag
Site tag assigns the AP join profile settings to the AP and determines if the site is a local site, in which case the APs will be in local mode.
To get the best performance from your 9800 Series wireless controller, it is recommended that you:
-
Use custom site tags and not the default site tag
-
Assign the same site tag to all the APs in the same roaming domain
-
Limit the number of APs to 500 per site tag for best performance
-
Not exceed the recommended maximum number of APs per site tag based on the controller model
Procedure
| Step 1 |
configure terminal Example:Enters global configuration mode. |
| Step 2 |
wireless tag site site-tag Example:Configures site tag and enters site tag configuration mode. The site is configured as a local site, by default. To configure the site tag as Flexconnect, run the no local-site command. |
| Step 3 |
description description Example:Adds a description for the site tag. |
| Step 4 |
end Example:Returns to privileged EXEC mode. |
Assign a Policy Tag to an AP
Access Points are tagged based on the broadcast domain, the site it belongs to, and the desired RF characteristics. Once tagged, the AP gets a list of WLANs to be broadcast along with the properties of the respective SSIDs, properties of the APs on the local/remote site, and the RF properties of the network.
Each access point is assigned three unique tags: a policy, site, and RF tag. By default, when an AP joins the Cisco Catalyst 9800 Wireless Controller, it gets default tags; the default policy tag, default site tag, and default RF tag. Users can make changes to the default tags or create custom tags. For more information about tags, see "Tags, Profiles, and SSIDs" chapter in the Cisco Catalyst 9800 Series Wireless Controller Software Configuration Guide.
Before you begin
-
Ensure you have created a policy tag that maps the WLAN profile to the policy profile.
-
Ensure you have created a site tag.
Procedure
| Step 1 |
configure terminal Example:Enters the global configuration mode. |
||
| Step 2 |
ap mac-address Example:Configures an AP and enters the ap tag configuration mode.
|
||
| Step 3 |
policy-tag policy-tag-name Example:Maps a policy tag to an AP. |
||
| Step 4 |
site-tag site-tag-name Example:Maps a site tag to an AP. |
||
| Step 5 |
end Example:Exits the configuration mode and returns to privileged EXEC mode. |
Enable the HTTP/HTTPS Server for Web Authentication
Before you begin
Procedure
| Step 1 |
configure terminal Example:Enters global configuration mode. |
||
| Step 2 |
ip http server Example:Enables the HTTP server. The local web authentication feature uses the HTTP server to communicate with the hosts for user authentication.
|
||
| Step 3 |
ip http secure-server Example:Enables secure authentication. With secure authentication enabled, the login page always uses HTTPS even if the client sends an HTTP request. You can configure custom authentication proxy web pages or specify a redirection URL for successful login.
|
||
| Step 4 |
end Example:Exits configuration mode. |
 Feedback
Feedback