Layer 2 Network Address Translation
One-to-one Layer 2 NAT (Network Address Translation) is a service that allows the assignment of a unique public IP address to an existing private IP address (end device). The assignment enables the end device to communicate on both the private and public subnets. This service is configured in a NAT-enabled device and is the public “alias” of the IP address that is physically programmed on the end device. This is typically represented by a table in the NAT device.
Layer 2 NAT uses a table to translate IPv4 addresses both public-to-private, and private-to-public at line rate. Layer 2 NAT is a hardware-based implementation that provides the same high level of (bump-on-the-wire) wire-speed performance. This implementation also supports multiple VLANs through the NAT boundary for enhanced network segmentation.
In the following example, Layer 2 NAT translates addresses between sensors on a 192.168.1.x network and a line controller on a 10.1.1.x network.
-
The 192.168.1.x network is the inside/internal IP address space and the 10.1.1.x network is the outside or external IP address space.
-
The sensor at 192.168.1.1 sends a ping request to the line controller by using an “inside” address, 192.168.1.100.
-
Before the packet leaves the internal network, Layer 2 NAT translates the source address (SA) to 10.1.1.1 and the destination address (DA) to 10.1.1.100.
-
The line controller sends a ping reply to 10.1.1.1.
-
When the packet is received on the internal network, Layer 2 NAT translates the source address to 192.168.1.100 and the destination address to 192.168.1.1.

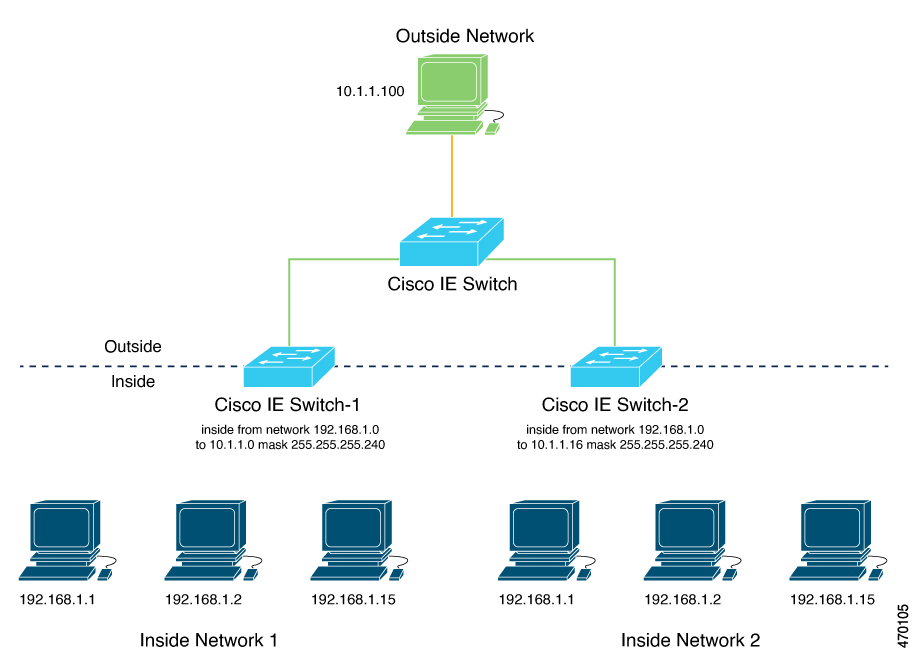
For large numbers of nodes, you can quickly enable translations for all devices in a subnet. In the scenario shown in the following figure, addresses from Inside Network 1 can be translated to outside addresses in the 10.1.1.0/28 subnet, and addresses from Inside Network 2 can be translated to outside addresses in the 10.1.1.16/28 subnet. All addresses in each subnet can be translated with one command. The benefit of using subnet-based translations saves in Layer L2 NAT rules. The switch has limits on the number of Layer 2 NAT rules. A rule with a subnet allows for multiple end devices to be translated with a single rule.
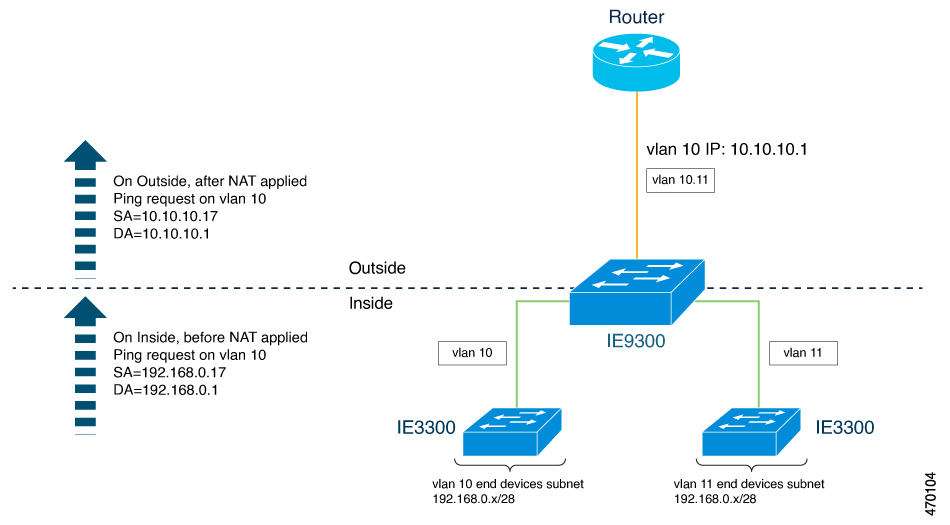
The following figure shows a switch at the aggregation layer forwarding Ethernet packets based on Layer 2 MAC Addresses. In this example, the router is the Layer 3 gateway for all subnets and VLANs.
The L2NAT instance definitions use the network command to define a translated row for multiple devices in the same subnet. In this the case, it’s a /28 subnet with last byte in the IP address starting with 16 and ending with 31. The gateway for the VLAN is the router with last byte of the IP address ending with .1. An outside host translation is provided for the router. The network command in the Layer 2NAT definition translates a subnet’s worth of host with a single command, saving on Layer 2 NAT translation records.
The Gi1/1 uplink interface has Layer 2NAT translation instances for vlan10 and vlan 11 subnets. Interfaces can support multiple Layer 2 NAT instance definitions.
The downstream switches are examples of access layer switches which do not perform L2NAT and rely on the upstream aggregation layer switch to do it.
The following example shows the NAT configuration for the preceding diagram:
!
l2nat instance Subnet10-NAT
instance-id 1
permit all
fixup all
outside from host 10.10.10.1 to 192.168.0.1
inside from network 192.168.0.0 to 10.10.10.16 mask 255.255.255.240
!
l2nat instance Subnet11-NAT
instance-id 1
permit all
fixup all
outside from host 10.10.11.1 to 192.168.0.1
inside from network 192.168.0.0 to 10.10.11.16 mask 255.255.255.240
!
interface GigabitEthernet1/1
switchport mode trunk
l2nat Subnet10-NAT 10
l2nat Subnet11-NAT 11
!
Interface vlan 1
ip address 10.10.1.2



 Feedback
Feedback