|
Platform Features
|
|
FDM support for FTDv for the Amazon Web Services (AWS) Cloud.
|
You can configure Firepower Threat Defense on FTDv for the AWS Cloud using FDM.
|
|
FDM for the Firepower 4112.
|
We introduced Firepower Threat Defense for the Firepower 4112.
|
|
e1000 Interfaces on FTDv for VMware.
|
Prevents upgrade. Version 6.6 ends support for e1000
interfaces on FTDv for VMware. You cannot upgrade until you switch
to vmxnet3 or ixgbe interfaces. Or, you can deploy a new
device.
For more information, see the Cisco Secure Firewall
Threat Defense Virtual Getting Started
Guide.
|
|
Firewall and IPS Features
|
|
Ability to enable intrusion rules that are disabled by default.
|
Each system-defined intrusion policy has a number of rules that are
disabled by default. Previously, you could not change the action for
these rules to alert or drop. You can now change the action for
rules that are disabled by default.
We changed the Intrusion Policy page to display all rules, even those
that are disabled by default, and allow you to edit the action for
these rules.
|
|
Intrusion Detection System (IDS) mode for the intrusion policy.
|
You can now configure the intrusion policy to operate in Intrusion
Detection System (IDS) mode. In IDS mode, active intrusion rules
issue alerts only, even if the rule action is Drop. Thus, you can
monitor or test how an intrusion policy works before you make it an
active prevention policy in the network.
In FDM, we added an indication of the inspection mode to each intrusion
policy on the page, and an Edit link so that
you can change the mode.
In the Firepower Threat Defense API, we added the inspectionMode attribute to the IntrusionPolicy
resource.
|
|
Support for manually uploading Vulnerability Database (VDB),
Geolocation Database, and Intrusion Rule update packages.
|
You can now manually retrieve update packages for VDB, Geolocation
Database, and Intrusion Rules, and then upload them from your
workstation to the Firepower Threat Defense device using FDM. For example, if you have an air-gapped network, where FDM cannot retrieve updates from the Cisco Cloud, you can now get the
update packages you need.
We updated the page to allow you to select and upload a file from
your workstation.
|
|
Firepower Threat Defense API support for access control rules that are limited based on
time.
|
Using the Firepower Threat Defense API, you can create time range objects, which specify one-time or
recurring time ranges, and apply these objects to access control
rules. Using time ranges, you can apply an access control rule to
traffic during certain times of day, or for certain periods of time,
to provide flexibility to network usage. You cannot use FDM to create or apply time ranges, nor does FDM show you if an access control rule has a time range applied to
it.
The TimeRangeObject, Recurrence, TimeZoneObject,
DayLightSavingDateRange, and DayLightSavingDayRecurrence resources
were added to the Firepower Threat Defense API. The timeRangeObjects attribute was added to the accessrules
resource to apply a time range to the access control rule. In
addition, there were changes to the GlobalTimeZone and TimeZone
resources.
|
|
Object group search for access control policies.
|
While operating, the Firepower Threat Defense device expands access control rules into multiple access control
list entries based on the contents of any network objects used in
the access rule. You can reduce the memory required to search access
control rules by enabling object group search. With object group
search enabled, the system does not expand network objects, but
instead searches access rules for matches based on those group
definitions. Object group search does not impact how your access
rules are defined or how they appear in FDM. It impacts only how the device interprets and processes them
while matching connections to access control rules. Object group
search is disabled by default.
In FDM, you must use FlexConfig to enable the
object-group-search access-control
command.
|
|
VPN Features
|
|
Backup peer for site-to-site VPN. (Firepower Threat Defense API only.)
|
You can use the Firepower Threat Defense API to add a backup peer to a site-to-site VPN connection. For
example, if you have two ISPs, you can configure the VPN connection
to fail over to the backup ISP if the connection to the first ISP
becomes unavailable.
Another main use of a backup peer is when you have two different
devices on the other end of the tunnel, such as a primary-hub and a
backup-hub. The system would normally establish the tunnel to the
primary hub. If the VPN connection fails, the system automatically
can re-establish the connection with the backup hub.
We updated the Firepower Threat Defense API so that you can specify more than one interface for
outsideInterface in the SToSConnectionProfile resource. We also
added the BackupPeer resource, and the remoteBackupPeers attribute
to the SToSConnectionProfile resource.
You cannot configure a backup peer using FDM, nor will the existence of a backup peer be visible in FDM.
|
|
Support for Datagram Transport Layer Security (DTLS) 1.2 in remote
access VPN.
|
You can now use DTLS 1.2 in remote access VPN. This can be configured
using the Firepower Threat Defense API only, you cannot configure it using FDM. However, DTLS 1.2 is now part of the default SSL cipher group,
and you can enable the general use of DTLS using FDM in the AnyConnect attributes of the group policy. Note that DTLS
1.2 is not supported on the ASA 5508-X or 5516-X models.
We updated the protocolVersion attribute of the sslcipher resource to
accept DTLSV1_2 as an enum value.
|
|
Deprecated support for less secure Diffie-Hellman groups, and
encryption and hash algorithms.
|
The following features are deprecated and will be removed in a future
release. You should avoid configuring these features in IKE
proposals or IPSec policies for use in VPNs. Please transition away
from these features and use stronger options as soon as is
practical.
-
Diffie-Hellman groups: 2, 5, and 24.
-
Encryption algorithms for users who satisfy export controls
for strong encryption: DES, 3DES, AES-GMAC, AES-GMAC-192,
AES-GMAC-256. DES continues to be supported (and is the only
option) for users who do not satisfy export controls.
-
Hash algorithms: MD5.
|
|
Routing Features
|
|
Virtual routers and Virtual Routing and Forwarding (VRF)-Lite.
|
You can create multiple virtual routers to maintain separate routing
tables for groups of interfaces. Because each virtual router has its
own routing table, you can provide clean separation in the traffic
flowing through the device.
Virtual routers implement the “light” version of Virtual Routing and
Forwarding, or VRF-Lite, which does not support Multiprotocol
Extensions for BGP (MBGP).
We changed the Routing page so you can enable
virtual routers. When enabled, the Routing
page shows a list of virtual routers. You can configure separate
static routes and routing processes for each virtual router.
We also added the [ vrf
name | all]
keyword set to the following CLI commands, and changed the output to
indicate virtual router information where applicable:
clear ospf , clear
route , ping ,
show asp table routing ,
show bgp , show ipv6
route , show ospf ,
show route , show snort
counters .
We added the following command: show vrf .
|
|
OSPF and BGP configuration moved to the Routing pages.
|
In previous releases, you configured OSPF and BGP in the Advanced
Configuration pages using Smart CLI. Although you still configure
these routing processes using Smart CLI, the objects are now
available directly on the Routing pages. This makes it easier for
you to configure processes per virtual router.
The OSPF and BGP Smart CLI objects are no longer available on the
Advanced Configuration page. If you configured these objects before
upgrading to 6.6, you can find them on the Routing page after
upgrade.
|
|
High Availability Features
|
|
The restriction for externally authenticated users logging into the
standby unit of a high availability (HA) pair has been removed.
|
Previously, an externally-authenticated user could not directly log
into the standby unit of an HA pair. The user first needed to log
into the active unit, then deploy the configuration, before login to
the standby unit was possible.
This restriction has been removed. Externally-authenticated users can
log into the standby unit even if they never logged into the active
unit, so long as they provide a valid username/password.
|
|
Change to how interfaces are handled by the BreakHAStatus resource in
the Firepower Threat Defense API.
|
Previously, you could include the clearIntfs
query parameter to control the operational status of the interfaces
on the device where you break the high availability (HA)
configuration.
Starting with version 6.6, there is a new attribute,
interfaceOption, which you should use
instead of the clearIntfs query parameter. This attribute is
optional when used on the active node, but required when used on a
non-active node. You can choose from one of two options:
-
DISABLE_INTERFACES (the default)—All data interfaces on the
standby device (or this device) are disabled.
-
ENABLE_WITH_STANDBY_IP—If you configured a standby IP address
for an interface, the interface on the standby device (or
this device) is reconfigured to use the standby address. Any
interface that lacks a standby address is disabled.
If you use break HA on the active node when the devices are in a
healthy active/standby state, this attribute applies to the
interfaces on the standby node. In any other state, such as
active/active or suspended, the attribute applies to the node on
which you initiate the break.
If you do use the clearIntfs query parameter, clearIntfs=true will
act like interfaceOption = DISABLE_INTERFACES. This means that
breaking an active/standby pair with clearIntfs=true will no longer
disable both devices; only the standby device will be disabled.
When you break HA using FDM, the interface option is always set to DISABLE_INTERFACES. You
cannot enable the interfaces with the standby IP address. Use the
API call from the API Explorer if you want a different result.
|
|
The last failure reason for High Availability problems is now
displayed on the High Availability page.
|
If High Availability (HA) fails for some reason, such as the active
device becoming unavailable and failing over to the standby device,
the last reason for failure is now shown below the status
information for the primary and secondary device. The information
includes the UTC time of the event.
|
|
Interface Features
|
|
PPPoE support.
|
You can now configure PPPoE for routed interfaces. PPPoE is not
supported on High Availability units.
New/Modified screens:
New/Modified commands: show vpdn group, show vpdn username, show
vpdn session pppoe state
|
|
Management interface acts as a DHCP client by default.
|
The Management interface now defaults to obtaining an IP address from
DHCP instead of using the 192.168.45.45 IP address. This change
makes it easier for you to deploy an Firepower Threat Defense in your existing network. This feature applies to all platforms
except for the Firepower 4100/9300 (where you set the IP address when you deploy the logical
device), and the FTDv and ISA 3000 (which still use the 192.168.45.45 IP address). The
DHCP server on the Management interface is also no longer
enabled.
You can still connect to the default inside IP address by default
(192.168.1.1).
|
|
HTTP proxy support for FDM management connections.
|
You can now configure an HTTP proxy for the management interface for
use with FDM connections. All management connections, including manual and
scheduled database updates, go through the proxy.
We added the page to configure the setting. In addition, we added
the HTTPProxy resource to the Firepower Threat Defense API.
|
|
Set the MTU for the Management interface.
|
You can now set the MTU for the Management interface up to 1500
bytes. The default is 1500 bytes.
New/Modified commands: configure network mtu, configure network
management-interface mtu-management-channel
No modified screens.
|
|
Licensing Features
|
|
Smart Licensing and Cloud Services enrollment are now separate, and
you can manage your enrollments separately.
|
You can now enroll for cloud services using your security account
rather than your Smart Licensing account. Enrolling using the
security account is the recommended approach if you intend to manage
the device using Cisco Defense Orchestrator. You can also unregister
from cloud services without unregistering from Smart Licensing.
We changed how the page behaves, and added the ability to unregister
from cloud services. In addition, the Web Analytics feature was
removed from the page and you can now find it at . In the Firepower Threat Defense API, the CloudServices resources were modified to reflect the new
behavior.
|
|
Support for Permanent License Reservation.
|
If you have an air-gapped network, where there is no path to the
internet, you cannot register directly with the Cisco Smart Software
Manager (CSSM) for Smart Licensing. In this situation, you can now
get authorization to use Universal Permanent License Reservation
(PLR) mode, where you can apply a license that does not need direct
communication with CSSM. If you have an air-gapped network, please
contact your account representative and ask for authorization to use
Universal PLR mode in your CSSM account, and to obtain the necessary
licenses. ISA 3000 does not support Universal PLR.
We added the ability to switch to PLR mode, and to cancel and
unregister a Universal PLR license, to the page. In the Firepower Threat Defense API, there are new resources for PLRAuthorizationCode, PLRCode,
PLRReleaseCode, PLRRequestCode, and actions for PLRRequestCode,
InstallPLRCode, and CancelReservation.
|
|
Administrative and Troubleshooting Features
|
|
FDM direct support for Precision Time Protocol (PTP) configuration
for ISA 3000 devices.
|
You can use FDM to configure the Precision Time Protocol (PTP) on ISA 3000
devices. PTP is a time-synchronization protocol developed to
synchronize the clocks of various devices in a packet-based network.
The protocol is designed specifically for industrial, networked
measurement and control systems. In previous releases, you had to
use FlexConfig to configure PTP.
We grouped PTP with NTP on the same System Settings page, and renamed
the page to Time Services. We also
added the PTP resource to the Firepower Threat Defense API.
|
|
Trust chain validation for the FDM management web server certificate.
|
When you configure a non-self-signed certificate for the FDM web server, you now need to include all intermediate
certificates, and the root certificate, in the trust chain. The
system validates the entire chain.
We added the ability to select the certificates in the chain on the
Management Web Server tab on the page.
|
|
Support for encrypting backup files.
|
You can now encrypt backup files using a password. To restore an
encrypted backup, you must supply the correct password.
We added the ability to choose whether to encrypt backup files for
recurring, scheduled, and manual jobs, and to supply the password on
restore, to the page. We also added the encryptArchive and
encryptionKey attributes to the BackupImmediate and BackupSchedule
resources, and encryptionKey to the RestoreImmediate resource in the
Firepower Threat Defense API.
|
|
Support for selecting which events to send to the Cisco cloud for use
by cloud services.
|
When you configure the device to send events to the Cisco cloud, you
can now select which types of events to send: intrusion,
file/malware, and connection. For connection events, you can send
all events or just the high-priority events, which are those related
to connections that trigger intrusion, file, or malware events, or
that match Security Intelligence blocking policies.
We changed how the Send Events to the Cisco Cloud Enable button
works. The feature is on the page.
|
|
Firepower Threat Defense REST API version 5 (v5).
|
The Firepower Threat Defense REST API for software version 6.6 has been incremented to version
5. You must replace v1/v2/v3/v4 in the API URLs with v5, or
preferentially, use /latest/ to signify you are using the most
recent API version that is supported on the device.
The v5 API includes many new resources that cover all features added
in software version 6.6. Please re-evaluate all existing calls, as
changes might have been mode to the resource models you are using.
To open the API Explorer, where you can view the resources, log into
FDM, then click the more options button (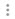 ) and choose API Explorer. ) and choose API Explorer.
|
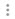







 Feedback
Feedback