This section shows two examples of policing data packets.
The first example illustrates how to configure a policer to rate limit traffic received on an interface. After you configure
the policer, include it in an access list. Here "policer p1" is configured to have a maximum traffic rate of 1,000,000 bits
per second and a maximum burst-size limit of 15000 bytes. Traffic exceeding these rate limits is dropped. The policer is then
included in the access list "acl1," which is configured to accept all TCP or UDP traffic originating from the host at source
2.2.0.0 and going to the destination host at 10.1.1.0 on port 20 or 100.1.1.0 on port 30. You can use "access-list acl1" on
the input or output of the interface to do flow-based policing.
policy
policer p1
rate 1000000
burst 15000
exceed drop
!
access-list acl1
sequence 1
match
source-ip 2.2.0.0/16
destination-ip 10.1.1.0/24 100.1.1.0/24
destination-port 20 30
protocol 6 17 23
!
action accept
policer p1
!
!
default-action drop
!
!
vpn 1
interface ge0/4
ip address 10.20.24.15/24
no shutdown
access-list acl1 in
!
!
You can also apply a policer directly on an inbound or an outbound interface when you want to police all traffic ingressing
or egressing this interface:
policy
policer p1
rate 1000000
burst 15000
exceed drop
!
!
vpn 1
interface ge0/4
ip address 10.20.24.15/24
no shutdown
policer p1 in
!
!
vpn 2
interface ge0/0
ip address 10.1.15.15/24
no shutdown
policer p1 out
!
!
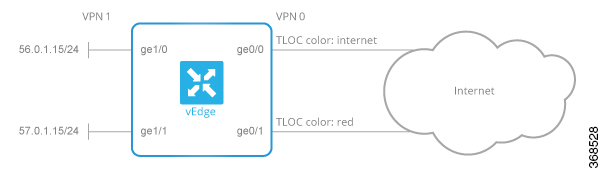
In the second example, we have a Cisco vEdge device with two WAN interfaces in VPN 0. The ge0/0 interface connects to a 30-MB link, and we want to always have 10 MB available
for very high priority traffic. When lower-priority traffic bursts exceed 20 MB, we want to redirect that traffic to the second
WAN interface, ge0/1.
Implementing this traffic redirection requires two policies:
-
You apply an access list to the service-side interface that polices the incoming data traffic.
-
You apply a data policy to the ge0/0 WAN interface that directs bursty traffic to the second WAN interface, ge0/1.
For the access list, the configuration snippet below is for interface ge1/0, in VPN 1. The policer monitors incoming traffic
on the interface. When traffic exceeds 20 MB (configured in the policer burst command), we change the PLP from low to high (configured by the policer exceed remark command). You configure the following on the Cisco vEdge device:
policy
policer bursty-traffic
rate 1000000
burst 20000
exceed remark
access-list policer-bursty-traffic
sequence 10
match
source-ip 56.0.1.0/24
action accept
policer bursty-traffic
default-action accept
vpn 1
interface ge1/0
ip address 56.0.1.14/24
no shutdown
access-list policer-bursty-traffic in
To display a count of the packets that have been remarked, issue the show interface detail or the show system statistics command on the Cisco vEdge device. The count is reported in the rx-policer-remark field.
The centralized data policy directs burst traffic away from the ge0/0 interface (color: internet) to interface ge0/1 (color:
red). You apply this data policy to all the routers at a particular site, specifying the direction from-service so that the policy is applied only to traffic originating from the service side of the router. You configure the following
on the vSmart controller:
policy
lists
site-list highest-priority-routers
site-id 100
vpn-list wan-vpn
vpn 0
data-policy highest-priority
vpn-list wan-vpn
sequence 10
match
plp high
source-ip 56.0.1.0/24
action accept
count bursty-counter
set local-tloc color red
default-action accept
apply-policy
site-list highest-priority-routers
data-policy highest-priority from-service


 Feedback
Feedback