Information About Lawful Intercept 2.0
Cisco Catalyst SD-WAN’s Lawful Intercept feature allows an LEA to get a copy of network traffic for analysis or evidence. This is also referred as traffic mirroring. See the chapter Lawful Intercept in the Cisco Catalyst SD-WAN Policies Configuration Guide.
From Cisco vManage Release 20.9.1, Cisco Catalyst SD-WAN implements a new architecture for Lawful Intercept , as shown in the following figure.
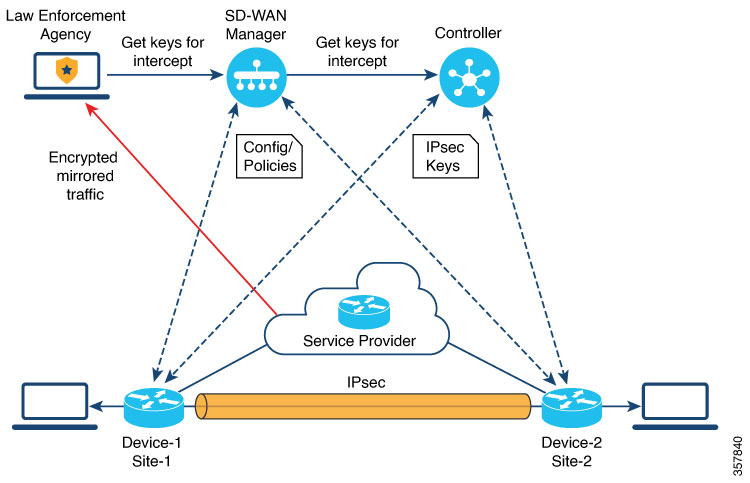
The following are the characteristics of the new architecture:
-
Traffic mirroring is outside the scope of Cisco Catalyst SD-WAN. The LEA works with the corresponding service provider to capture network traffic for mirroring.

Note
In the illustration above, the service provider is an underlay connection and the IPsec tunnel is an overlay connection.
-
Because the captured network traffic is encrypted, Cisco SD-WAN Manager and Cisco SD-WAN Controller provide key information to the LEA.
-
The LEA retrieves the keys from Cisco SD-WAN Manager to decrypt Cisco Catalyst SD-WAN IPsec traffic. The LEA ensures that they retrieve key information is retrieved during each rekey period. The rekey period is provided by the service provider. For more information about retrieving keys, see Retrieve an Intercept. For information on rekey period, see Configure Data Plane Security Parameters.
A Lawful Intercept administrator is solely responsible for configuring intercepts and creating Lawful Intercept API users who perform Lawful Intercepts. A Cisco SD-WAN Manager administrator can create an account for the Lawful Intercept administrator; the administrator must be a member of the li-admin group. For more information about creating an account for a Lawful Intercept administrator, see Create Lawful Intercept Administrator.
 Feedback
Feedback