Cisco Catalyst SD-WAN Validator Redundancy
The Cisco SD-WAN Validator performs two key functions in the Cisco Catalyst SD-WAN overlay network:
-
Authenticates and validates all Cisco SD-WAN Controllers and routers that attempt to join the Cisco Catalyst SD-WAN network.
-
Orchestrates the control plane connections between the Cisco SD-WAN Controllers and routers, thus enabling Cisco SD-WAN Controller and routers to connect to each other in the Cisco Catalyst SD-WAN network.
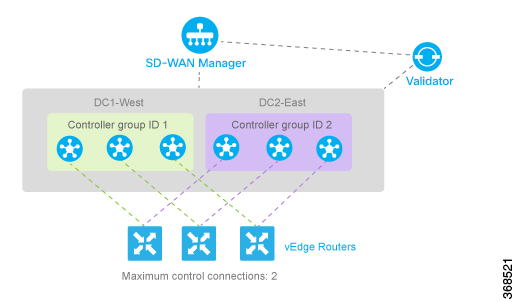
The Cisco SD-WAN Validator runs as a VM on a network server. The Cisco SD-WAN Validator can also run on a router that is configured to be a Cisco SD-WAN Validator, however this is not recommended, and it limits the number of router control connections to 50. If using running the Cisco SD-WAN Validator daemon on a router, note that only one Cisco SD-WAN Validator daemon can run at a time on a router, so to provide redundancy and high availability, the network must have two or more routers that function as Cisco SD-WAN Validator orchestrators. (Note also that it is not recommended to use a router acting as a vBond orchestrator as a regular router.)
Having multiple Cisco SD-WAN Validators ensures that one of them is always available whenever a Cisco device such as a router or a Cisco SD-WAN Controller is attempting to join the network.
Configuration of Redundant Cisco Catalyst SD-WAN Validators
A Cisco SD-WAN Controller learns that it is acting as a Cisco SD-WAN Validator from its configuration. In the system vbond configuration command, which defines the IP address (or addresses) of the Cisco SD-WAN Validator (or validators) in the Cisco Catalyst SD-WAN overlay network, you include the local option. In this command, you also include the local public IP address of the Cisco SD-WAN Validator, (Even though on Cisco vEdge device and Cisco SD-WAN Controllers you can specify an IP address of Cisco SD-WAN Validator as a DNS name, on the Cisco SD-WAN Validator itself, you must specify it as an IP address.)
On Cisco SD-WAN Controllers, and Cisco vEdge devices, when the network has only a single Cisco SD-WAN Validator, you can configure the location of the Cisco SD-WAN Validator system either as an IP address or as the name of a DNS server (such as vbond.cisco.com). (Again, you configure this in the system vbond command.) When the network has two or more Cisco SD-WAN Validators and they must all be reachable, you should use the name of a DNS server. The DNS server then resolves the name to a single IP address that the Cisco SD-WAN Validator returns to the Cisco vEdge device. If the DNS name resolves to multiple IP addresses, the Cisco SD-WAN Validator returns them all to the Cisco vEdge device, and the router tries each address sequentially until it forms a successful connection.
Note that even if your Cisco Catalyst SD-WAN network has only a single Cisco SD-WAN Validator, it is recommended as a best practice that you specify a DNS name rather than an IP address in the system vbond configuration command, because this results in a scalable configuration. Then, if you add additional Cisco SD-WAN Validators to your network, you do not need to change the configurations on any of the routers or Cisco SD-WAN Controllers in your network.
Recovering from a Cisco Catalyst SD-WAN Validator Failure
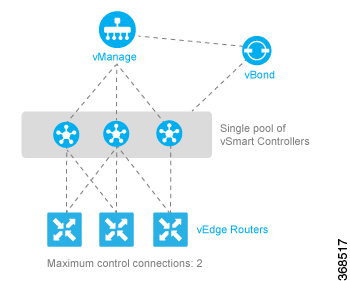
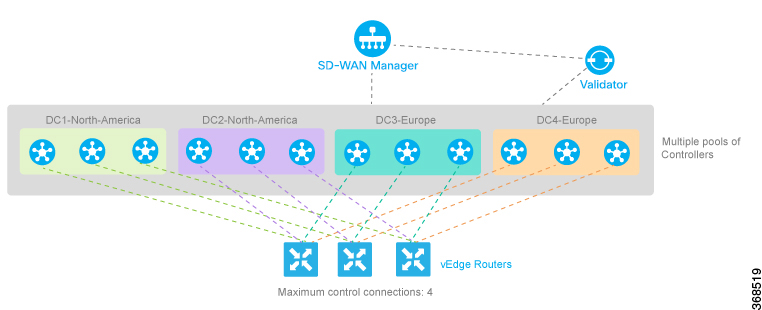
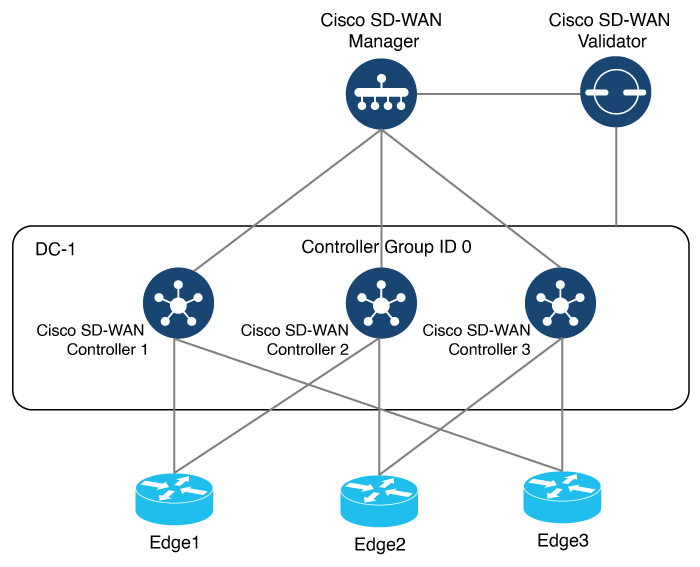
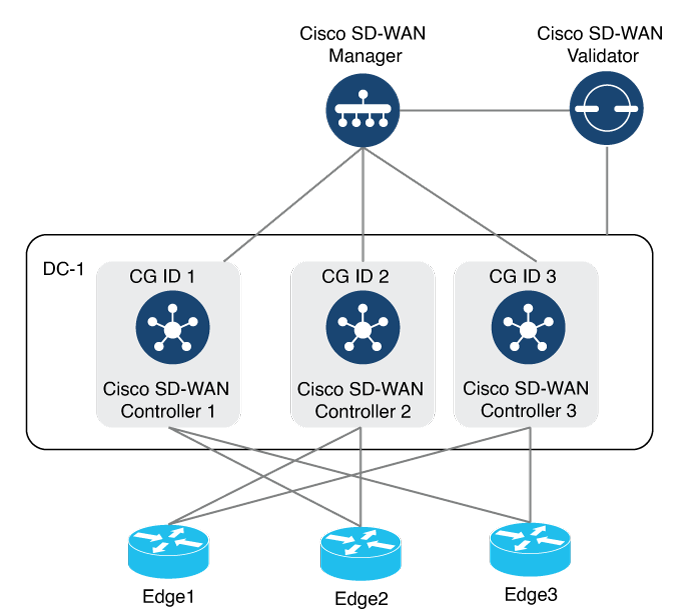
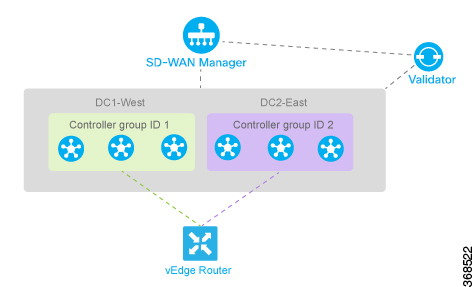
In a network with multiple Cisco SD-WAN Validators, if one of them fails, the other Cisco SD-WAN Validators simply continue operating and are able to handle all requests by Cisco devices to join the network. From a control plane point of view, each Cisco SD-WAN Validator maintains a permanent DTLS connections to each of the Cisco SD-WAN Controllers in the network. (Note however, that there are no connections between the Cisco SD-WAN Validators themselves.) As long as one Cisco SD-WAN Validator is present in the domain, the Cisco Catalyst SD-WAN network is able to continue operating without interruption, because Cisco SD-WAN Controllers and routers are still able to locate each other and join the network.
Because Cisco SD-WAN Validators never participate in the data plane of the overlay network, the failure of any Cisco SD-WAN Validator has no impact on data traffic. Cisco SD-WAN Validators communicate with routers only when the routers are first joining the network. The joining router establishes a transient DTLS connection with a Cisco SD-WAN Validator to learn the IP address of a Cisco SD-WAN Controller. When the Cisco vEdge device configuration lists the Cisco SD-WAN Validator address as a DNS name, the router tries each of the Cisco SD-WAN Validators in the list, one by one, until it is able to establish a DTLS connection. This mechanism allows a router to always be able to join the network, even after one of a group of Cisco SD-WAN Validators has failed.



 Feedback
Feedback