Overview
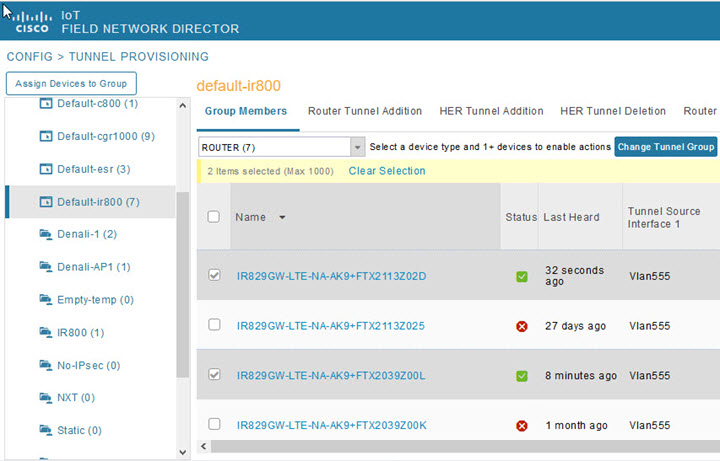
IoT FND sends the commands generated from processing the tunnel provisioning templates to FARs and HERs to provision secure tunnels between them. The default IoT FND templates contain CLI commands to set up and configure GRE and IPsec tunnels. One HER can serve up to 500 FARs, which may include multiple tunnels with the same HER EID and name.

To provision tunnels between HERs and FARs, IoT FND executes CLI tunnel configuration commands on these devices. By default, IoT FND provides basic tunnel configuration templates containing the CLI tunnel configuration commands. You can also use your own templates. Although the tunnel provisioning process is automatic, you must first complete the configuration steps outlined in Tunnel Provisioning Configuration Process. After that, whenever a FAR comes online, IoT FND automatically provisions it with a tunnel. Before you configure IoT FND for tunnel provisioning, ensure that the IoT FND TPS Proxy is installed and running.
ZTD without IPSec
Beginning with IoT FND Release 3.1.x, you have the option to initiate ZTD with no IPSec configured by ensuring that the Tunnel Provisioning Template is empty of any CLI. This initial approach of bringing up your network without a factory configuration does not preclude subsequent use of IPSec in your network
Tunnel Provisioning Configuration Process
To configure IoT FND for tunnel provisioning:
|
1 |
Configure the DHCP servers. Configure DHCP servers to provide unique IP addresses to IoT FND. The default IoT FND tunnel provisioning templates configure a loopback interface and the IP addresses required to create the tunnels. Cisco IOS CGRs/FARs use FlexVPN. Ensures that the template only contains addresses for the loopback interface. |
Configuring the DHCP Server for Tunnel Provisioning
|
||
|
2 |
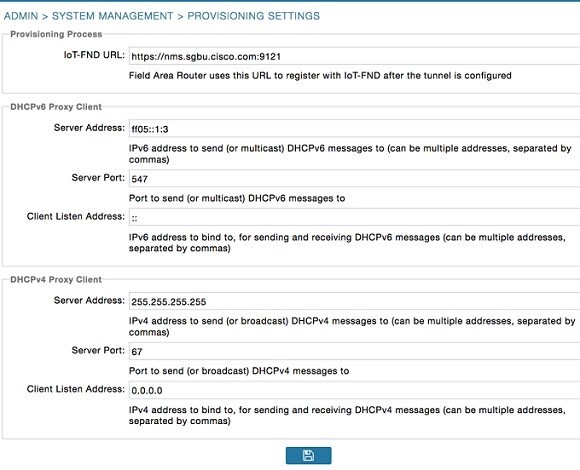
Configure the tunnel settings. Configure the NMS URL and the DHCP proxy client settings on the Provisioning Settings page in IoT FND (). |
See the Configuring Provisioning in Managing System Settings chapter. |
||
|
3 |
Cisco IOS CGRs use the CGNA service |
See Managing Devices chapter. | ||
|
4 |
Configure HER management. Configure HERs to allow management by IoT FND using NETCONF over SSH. |
Configuring HERs before adding them to IoT FND. |
||
|
5 |
Add HERs to IoT FND. |
Adding HERs to IoT FND. See Adding HER to IoT FND in Managing Devices chapter. |
||
|
6 |
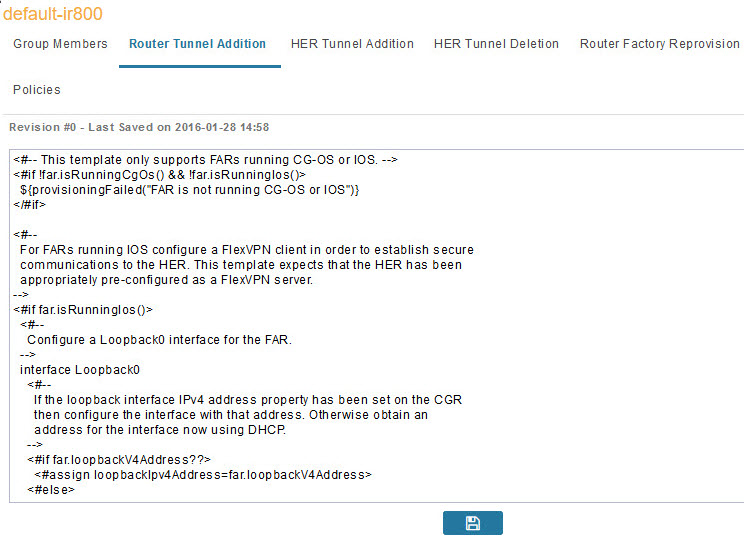
Review the IoT FND tunnel provisioning templates to ensure that they create the correct type of tunnel. |
See Tunnel Provisioning Templates in Managing Tunnel Provisioning chapter. | ||
|
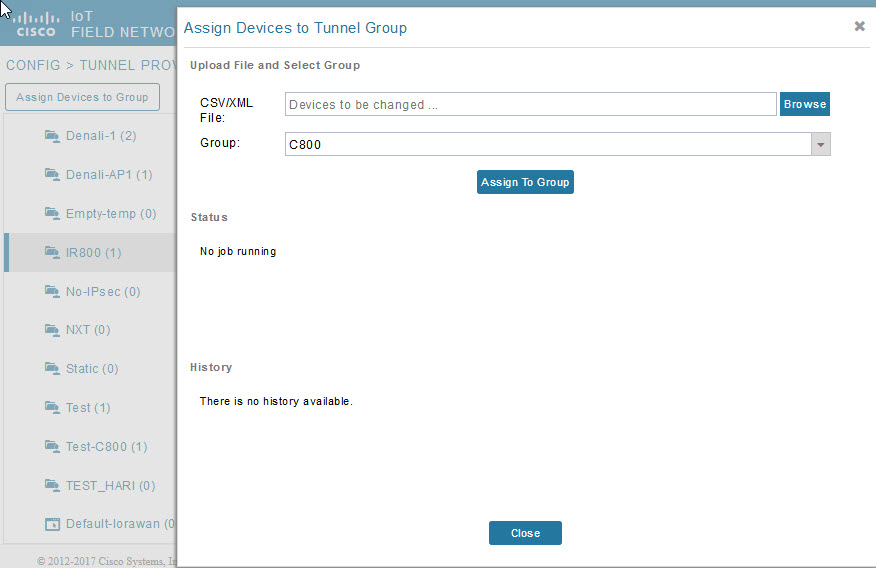
7 |
(Optional) If you plan to use your own templates for tunnel provisioning, create one or more tunnel provisioning groups and modify the default tunnel provisioning templates. |
|||
|
8 |
Configure FARs to contact IoT FND over HTTPS through the IoT FND TPS proxy. |
This step is typically performed at the factory where the FARs are configured to contact the TPS Proxy. |
||
|
9 |
Add FARs to IoT FND. Import the FARs into IoT FND using the Notice-of-Shipment XML file. |
See Adding FARs to IoT FND in the Managing Devices chapter. | ||
|
10 |
Map FARs to their corresponding HER. |
After completing the previous steps, deploy the FARs and power them on. Tunnel provisioning happens automatically.
This is the sequence of events after a FAR is turned on:
Before you begin
You must generate the keystore files on the IoT FND and TPS Proxy before configuring tunnel provisioning. Then, you configure
IoT FND and the TPS Proxy to talk to one another (refer to Setting Up TPS Proxy, Configuring IoT FND to Use the TPS Proxy, and Starting the IoT FND TPS Proxy). Use the systemctl command for TPS proxy if the OS version is RHEL 8.x or greater.
| RHEL Version | Command |
|---|---|
|
8.x |
systemctl <start/stop/status/restart> tpsproxy |
|
7.x |
|
Procedure
|
Step 1 |
Upon joining the uplink network after being turned on, the FAR sends a request for certificate enrollment. |
|
Step 2 |
The FAR then requests tunnel provisioning to IoT FND through the IoT FND TPS Proxy. |
|
Step 3 |
IoT FND looks up the FAR record in the IoT FND database and determines which tunnel provisioning templates to use. IoT FND also looks up which HERs to which to establish a tunnel. |
|
Step 4 |
For Cisco IOS CGRs, the default templates configure the CGR to use FlexVPN. The FlexVPN client is configured on the CGR that will contact the HER and ask for a FlexVPN tunnel to be dynamically constructed. This is how the HER dynamically adds a new tunnel endpoint interface for the CGR. |
|
Step 5 |
Before processing FAR templates, IoT FND processes the HER Tunnel Deletion template and sends the resulting commands to the HERs. This is done for each HER to remove existing tunnel configuration that may be associated with the FAR. |
|
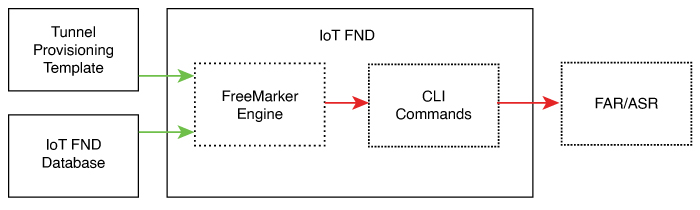
Step 6 |
IoT FND uses the FreeMarker template engine to process the FAR Tunnel Addition template. The engine converts the templates to text, which IoT FND assumes to be CLI configuration commands (Cisco IOS per the CGR). IoT FND uses these commands to configure and bring up one end of the tunnel on the FAR. |
|
Step 7 |
IoT FND uses the FreeMarker template engine to process the HER Tunnel Addition template. The engine converts the templates to text, which IoT FND assumes to be commands for configuring the tunnel on the HERs. |
|
Step 8 |
For Cisco IOS CGRs, if no errors occurred applying the commands generated by the templates to the FAR and HERs, IoT FND configures a new active CGNA profile “cg-nms-register,” and deactivates the cg-nms-tunnel profile. That cg-nms-register profile uses the IoT FND URL.  The specified URL uses the IoT FND registration port (default 9121) instead of the tunnel provisioning port. The Fully Qualified Domain Name (FQDN) in that URL is different and resolves to an IP address that is only reachable through the tunnels. |






 Feedback
Feedback