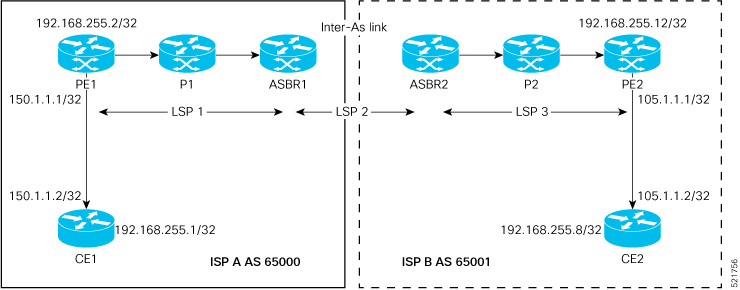
Perform the following task on PE1, P1, ASBR1, ASBR2, P2, and PE2 to configure Inter-AS Option B for L3VPN.
Verification
Verification on PE1.
L3VPN route 202.1.0.0/24 is learned through iBGP from ASBR1 on PE1 over address family VPNv4 unicast.
Router:PE1# show route vrf vrf1
Sun Jun 6 23:08:38.433 UTC
Codes: C - connected, S - static, R - RIP, B - BGP, (>) - Diversion path
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - ISIS, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, su - IS-IS summary null, * - candidate default
U - per-user static route, o - ODR, L - local, G - DAGR, l - LISP
A - access/subscriber, a - Application route
M - mobile route, r - RPL, t - Traffic Engineering, (!) - FRR Backup path
Gateway of last resort is not set
B 105.1.1.0/24 [200/0] via 10.10.10.10 (nexthop in vrf default), 00:04:43
C 150.1.1.0/24 is directly connected, 01:14:27, TenGigE0/0/0/22/0.1
L 150.1.1.1/32 is directly connected, 01:14:27, TenGigE0/0/0/22/0.1
B 202.1.0.0/24 [200/0] via 10.10.10.10 (nexthop in vrf default), 00:00:08
B 202.1.1.0/24 [200/0] via 10.10.10.10 (nexthop in vrf default), 00:00:08
The following output shows that you can reach 202.1.0.0/24 using a VPN label of 24521. The next hop for the VPNv4 prefix decides
the transport label as well as the label switched path.
Router:PE1# show bgp vpnv4 unicast rd 100:1 202.1.0.0/24
Sun Jun 6 23:12:12.140 UTC
BGP routing table entry for 202.1.0.0/24, Route Distinguisher: 100:1
Versions:
Process bRIB/RIB SendTblVer
Speaker 2844 2844
Last Modified: Jun 6 23:08:30.194 for 00:03:42
Paths: (1 available, best #1)
Not advertised to any peer
Path #1: Received by speaker 0
Not advertised to any peer
200 501
10.10.10.10 (metric 30) from 10.10.10.10 (10.10.10.10)
Received Label 24521
Origin IGP, localpref 100, valid, internal, best, group-best, import-candidate, imported
Received Path ID 0, Local Path ID 1, version 2844
Extended community: RT:100:1
Source AFI: VPNv4 Unicast, Source VRF: vrf1, Source Route Distinguisher: 100:1
Router:PE1# show cef vrf vrf1 202.1.0.0
Mon Jun 7 02:07:39.841 UTC
202.1.0.0/24, version 513583, internal 0x5000001 0x30 (ptr 0xa3f8bac8) [1], 0x0 (0x0), 0x208 (0x8f505928)
Updated Jun 7 01:50:33.710
Prefix Len 24, traffic index 0, precedence n/a, priority 3
gateway array (0x8f2d20e8) reference count 252, flags 0x2038, source rib (7), 0 backups
[1 type 1 flags 0x48441 (0x8ad86708) ext 0x0 (0x0)]
LW-LDI[type=0, refc=0, ptr=0x0, sh-ldi=0x0]
gateway array update type-time 1 Jun 6 23:20:45.951
LDI Update time Jun 6 23:20:45.951
via 10.10.10.10/32, 5 dependencies, recursive [flags 0x6000]
path-idx 0 NHID 0x0 [0xa25ff9d8 0x0]
recursion-via-/32
next hop VRF - 'default', table - 0xe0000000
next hop 10.10.10.10/32 via 24003/0/21
next hop 20.50.1.1/32 BE25 labels imposed {24004 24521}
Load distribution: 0 (refcount 1)
Hash OK Interface Address
0 Y recursive 24003/0
The following output shows the transport label information to reach 202.1.0.0/24.
Router:PE1# show mpls forwarding prefix 10.10.10.10/32
Mon Jun 7 02:06:40.845 UTC
Local Outgoing Prefix Outgoing Next Hop Bytes
Label Label or ID Interface Switched
------ ----------- ------------------ ------------ --------------- ------------
24003 24004 10.10.10.10/32 BE25 20.50.1.1 141107
-------------------------------------------------------------------------------
Router:PE1# show cef vrf vrf1 202.1.0.0
Mon Jun 7 02:07:39.841 UTC
202.1.0.0/24, version 513583, internal 0x5000001 0x30 (ptr 0xa3f8bac8) [1], 0x0 (0x0), 0x208 (0x8f505928)
Updated Jun 7 01:50:33.710
Prefix Len 24, traffic index 0, precedence n/a, priority 3
gateway array (0x8f2d20e8) reference count 252, flags 0x2038, source rib (7), 0 backups
[1 type 1 flags 0x48441 (0x8ad86708) ext 0x0 (0x0)]
LW-LDI[type=0, refc=0, ptr=0x0, sh-ldi=0x0]
gateway array update type-time 1 Jun 6 23:20:45.951
LDI Update time Jun 6 23:20:45.951
via 10.10.10.10/32, 5 dependencies, recursive [flags 0x6000]
path-idx 0 NHID 0x0 [0xa25ff9d8 0x0]
recursion-via-/32
next hop VRF - 'default', table - 0xe0000000
next hop 10.10.10.10/32 via 24003/0/21
next hop 20.50.1.1/32 BE25 labels imposed {24004 24521}
Load distribution: 0 (refcount 1)
Hash OK Interface Address
0 Y recursive 24003/0
Verification on P1.
P1 performs a PHP operation for transport label and exposes the VPN label before forwarding the traffic to next-hop 10.10.10.10.
Router:P1#d show mpls forwarding prefix 10.10.10.10/32
Mon Jun 7 02:34:55.293 UTC
Local Outgoing Prefix Outgoing Next Hop Bytes
Label Label or ID Interface Switched
------ ----------- ------------------ ------------ --------------- ------------
24004 Pop 10.10.10.10/32 BE12 10.20.1.1 28804
-------------------------------------------------------------------------------
Verification on ASBR1.
ASBR1 learns the remote route 202.1.0.0/24 from ASBR2 through address-family VPNv4 unicast. The next hop is the ASBR2 loopback0.
After receiving this update, it is advertised to the local PE1 through iBGP address-family VPNv4 unicast. The next-hop-self
configuration is used on ASBR1 since it is reachable through IGP from PE1, so the next hop is changed to itself. The traffic
arrives from PE1 with a label 24521 and is swapped with label 25516 before forwarding it to ASBR2.
Router:ASBR1# show bgp vpnv4 unicast rd 100:1 202.1.0.0
Sun Jun 6 19:28:09.018 EDT
BGP routing table entry for 202.1.0.0/24, Route Distinguisher: 100:1
Versions:
Process bRIB/RIB SendTblVer
Speaker 1002022 1002022
Local Label: 24521
Paths: (1 available, best #1)
Advertised to update-groups (with more than one peer):
0.3
Path #1: Received by speaker 0
Advertised to update-groups (with more than one peer):
0.3
200 501
10.0.0.1 from 10.0.0.1 (10.0.0.1)
Received Label 25516
Origin IGP, localpref 100, valid, external, best, group-best, import-candidate, not-in-vrf
Received Path ID 0, Local Path ID 1, version 1002022
Extended community: RT:100:1
Router:ASBR1# show bgp vpnv4 unicast rd 100:1 advertised neighbor 192.168.255.2 summary
Network Next Hop From AS Path
Route Distinguisher: 100:1
105.1.1.0/24 10.10.10.10 10.0.0.1 200?
202.1.0.0/24 10.10.10.10 10.0.0.1 200 501i
202.1.1.0/24 10.10.10.10 10.0.0.1 200 501i
Processed 3 prefixes, 3 paths
Router:ASBR1# show mpls forwarding labels 24521
Sun Jun 6 23:05:49.323 EDT
Local Outgoing Prefix Outgoing Next Hop Bytes
Label Label or ID Interface Switched
------ ----------- ------------------ ------------ --------------- ------------
24521 25516 100:1:202.1.0.0/24 10.0.0.1 0
-------------------------------------------------------------------------------
Verification on ASBR2.
The prefix 202.1.0.0/24 is received through iBGP address-family VPNv4 unicast from PE2 with a label of 24002. ASBR2 assigns
it a local label of 25516 and advertises it to ASBR1 through eBGP vpnv4 address-family changing the next hop to itself. This
local label of 25516 is used by the ASBR1 to forward traffic to ASBR2, which in turn swaps it with a VPN label of 24002 before
forwarding it to the next hop.
Router:ASBR2# show bgp vpnv4 unicast rd 100:1 202.1.0.0
Sun Jun 6 23:06:32.812 EDT
BGP routing table entry for 202.1.0.0/24, Route Distinguisher: 100:1
Versions:
Process bRIB/RIB SendTblVer
Speaker 16194881 16194881
Local Label: 25516
Gateway Array ID: 21940, Resilient per-PE nexthop set ID: 19598
Paths: (1 available, best #1)
Advertised to update-groups (with more than one peer):
0.3
Path #1: Received by speaker 0
Advertised to update-groups (with more than one peer):
0.3
501
5.5.5.5 (metric 30) from 5.5.5.5 (5.5.5.5)
Received Label 24002
Origin IGP, localpref 100, valid, internal, best, group-best, import-candidate, not-in-vrf
Received Path ID 0, Local Path ID 1, version 16194881
Extended community: RT:100:1
Router:ASBR2# show bgp vpnv4 unicast rd 100:1 advertised neighbor 10.10.10.10 summary
Sun Jun 6 23:07:05.617 EDT
Network Next Hop From AS Path
Route Distinguisher: 100:1
105.1.1.0/24 10.0.0.1 5.5.5.5 200?
150.1.1.0/24 10.0.0.1 10.10.10.10 200 100?
202.1.0.0/24 10.0.0.1 5.5.5.5 200 501i
202.1.1.0/24 10.0.0.1 5.5.5.5 200 501i
Processed 4 prefixes, 4 paths
Router:ASBR2# show mpls forwarding labels 25516
Sun Jun 6 23:07:32.394 EDT
Local Outgoing Prefix Outgoing Next Hop Bytes
Label Label or ID Interface Switched
------ ----------- ------------------ ------------ --------------- ------------
25516 24002 No ID 5.5.5.5 654
-------------------------------------------------------------------------------
Verification on P2.
P2 is along the transit path of the traffic. It label switches or pop the transport label. In this example, PHP operation
is performed and exposes the VPN label before forwarding the traffic.
Router:P2# show mpls forwarding prefix 5.5.5.5/32
Mon Jun 7 03:09:11.532 UTC
Local Outgoing Prefix Outgoing Next Hop Bytes
Label Label or ID Interface Switched
------ ----------- ------------------ ------------ --------------- ------------
24005 Pop 5.5.5.5/32 BE25 2.5.1.2 11921958
-------------------------------------------------------------------------------
Verification on PE2.
L3VPN route 202.1.0.0/24 is learned from eBGP neighbor 105.1.1.2 (CE2 interface towards PE2) in vrf1.
Router:PE2# show route vrf vrf1
Codes: C - connected, S - static, R - RIP, B - BGP, (>) - Diversion path
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - ISIS, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, su - IS-IS summary null, * - candidate default
U - per-user static route, o - ODR, L - local, G - DAGR, l - LISP
A - access/subscriber, a - Application route
M - mobile route, r - RPL, t - Traffic Engineering, (!) - FRR Backup path
Gateway of last resort is not set
C 105.1.1.0/24 is directly connected, 6w4d, TenGigE0/0/0/30.1
L 105.1.1.1/32 is directly connected, 6w4d, TenGigE0/0/0/30.1
B 150.1.1.0/24 [200/0] via 10.0.0.1 (nexthop in vrf default), 03:58:16
B 160.1.0.0/24 [200/0] via 10.0.0.1 (nexthop in vrf default), 04:30:07
B 202.1.0.0/24 [20/0] via 105.1.1.2, 01:30:05
B 202.1.1.0/24 [20/0] via 105.1.1.2, 01:30:05
The route 202.1.0.0/24 gets installed in VRF1 with a local label of 24002 and then advertised through iBGP address-family
VPNv4 unicast to ASBR2 changing the next hop to itself. ASBR2 adds this VPN label before forwarding it to PE2.
Router:PE2# show bgp vpnv4 unicast rd 100:1 202.1.0.0
BGP routing table entry for 202.1.0.0/24, Route Distinguisher: 100:1
Versions:
Process bRIB/RIB SendTblVer
Speaker 1070062 1070062
Local Label: 24002
Last Modified: Jun 7 01:30:56.657 for 01:31:29
Paths: (1 available, best #1)
Advertised to peers (in unique update groups):
10.0.0.1
Path #1: Received by speaker 0
Advertised to peers (in unique update groups):
10.0.0.1
501
105.1.1.2 from 105.1.1.2 (194.0.0.1)
Origin IGP, localpref 100, valid, external, best, group-best, import-candidate
Received Path ID 0, Local Path ID 1, version 1070062
Extended community: RT:100:1
The traffic that arrives from PE2 with a VPN label of 24002 is assigned an outgoing label ‘aggregate’, which means that the
lookup is to be performed in vrf1 RIB to forward it to the next hop on 150.1.1.2.
Router:PE2# show mpls forwarding labels 24002
Mon Jun 7 03:02:53.255 UTC
Local Outgoing Prefix Outgoing Next Hop Bytes
Label Label or ID Interface Switched
------ ----------- ------------------ ------------ --------------- ------------
24002 Aggregate vrf1: Per-VRF Aggr[V] \
vrf1 138
-------------------------------------------------------------------------------
Router:PE2# show cef vrf vrf1 202.1.0.0
Mon Jun 7 03:04:08.268 UTC
202.1.0.0/24, version 3477, internal 0x1000001 0x30 (ptr 0x97f75328) [1], 0x0 (0x0), 0x0 (0x0)
Updated Jun 7 01:30:57.120
Prefix Len 24, traffic index 0, precedence n/a, priority 3
gateway array (0x8c820f38) reference count 2, flags 0x2010, source rib (7), 0 backups
[1 type 3 flags 0x48441 (0x8a79cd88) ext 0x0 (0x0)]
LW-LDI[type=0, refc=0, ptr=0x0, sh-ldi=0x0]
gateway array update type-time 1 Jun 7 01:30:57.120
LDI Update time Jun 7 01:30:57.120
Level 1 - Load distribution: 0
[0] via 105.1.1.2/32, recursive
via 105.1.1.2/32, 3 dependencies, recursive, bgp-ext [flags 0x6020]
path-idx 0 NHID 0x0 [0x8d575b80 0x0]
next hop 105.1.1.2/32 via 105.1.1.2/32
Load distribution: 0 (refcount 1)
Hash OK Interface Address
0 Y TenGigE0/0/0/30.1 105.1.1.2








 Feedback
Feedback