MAC Authentication Bypass
|
Feature Name |
Release Information |
Feature Description |
|---|---|---|
|
MAC Authentication Bypass |
Release 24.3.1 |
Introduced in this release on: NCS 5500 fixed port routers; NCS 5700 fixed port routers; NCS 5500 modular routers (NCS 5500 line cards; NCS 5700 line cards [Mode: Compatibility; Native]) Based on the MAC address of the end device or the client connected to the router port, this feature enables port control functionality for your router. This functionality provides controlled access to network services for end devices that do not support other authentication methods such as IEEE 802.1X port-based authentication. The feature introduces these changes: CLI:
|
MAC authentication bypass (MAB) is a port control feature in which the router (authenticator) uses the MAC address of the end device or the client (also called as supplicant) as an authenticating parameter to provide network access.
802.1X (Dot1x) is one of the most widely used port-based authentication method to allow controlled access to the end devices connected to the port. However, not all clients support 802.1X. We would still need to allow them into the network even without 802.1X authentication. The MAB feature intends to provide this controlled access to such devices based on their MAC addresses.
Restrictions for MAC Authentication Bypass
These restrictions apply to the MAB feature:
-
With MAB, you can perform user authentication using a remote AAA server only; not using the local AAA server on the router.
-
MAB feature works only as a standalone feature; not as a fallback mechanism for any other type of authentication failures.
-
MAB supports only a single end device on each port.
Hence, you must configure the authenticator (the router) to be in single-host mode.
Authentication Failure Scenarios of MAB
This table lists the various authentication failure scenarios and the expected behavior of MAB feature.
|
If... |
And... |
Then… |
|---|---|---|
|
the RADIUS server rejects the authentication request |
— |
the router
|
|
the client is unauthenticated |
authentication does not happen after the retries |
the router
|
|
the RADIUS server is not reachable during authentication process |
server dead action auth-retry command is configured |
the router
To clear the client session and its programming on the router, use the clear mab session command. |
|
the RADIUS server is not reachable during authentication process |
server dead action auth-retry command is not configured |
the router
|
How MAC Authentication Bypass Works
Summary
These are the key components of MAC authentication bypass:
-
Supplicant: The client or end device without dot1x support.
-
Authenticator: The router that tries to authenticate the host device running the supplicant with the authentication server.
-
Authentication Server: The server that provides the authenticator the RADIUS reply (Access-Accept or Access-Reject message), which allows or denies network access to the end device.
Workflow
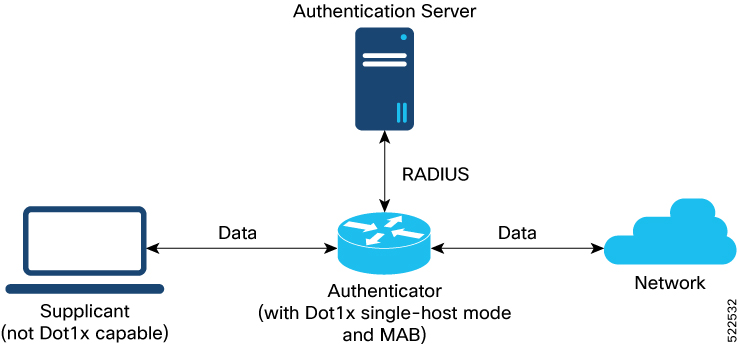
These stages describe how MAC authentication bypass process works.
-
The router receives an incoming data packet from the client that is connected to the router port.
-
The router
-
learns the source MAC address, and
-
sends it to the external RADIUS server (authentication server) for authentication.
The RADIUS authentication server maintains a database of MAC addresses for devices that require access to the network.
-
-
Based on the authentication result, the router allows or drops the data packets from that client.
If the RADIUS server… Then… And… returns a success (Access-Accept ) message -
it indicates that the MAC address is authenticated
-
the client is authorized to send traffic through that port
the router allows the traffic from the client to be forwarded to the network.
returns a failure (Access-Reject ) message it indicates that the MAC address is unauthenticated
the router drops further data packets from that client.
-
Result
Thus, the MAB feature brings in port control functionality for Cisco IOS XR routers and provides end devices a controlled access to network services.
Configure MAC Authentication Bypass
Before you begin
-
Configure the remote RADIUS server using the radius-server command, and authentication method with the RADIUS server using the aaa authentication dot1x command in .
-
Configure the 802.1X profile (using the dot1x profile command in XR Config mode)
-
Configure the authenticator (using the authenticator command in dot1x profile configuration sub mode) by specifying these parameters:
-
Re-authentication time—using reauth-time option
-
Host mode—using single-host option
-
Retry action for server-unreachable scenarios—using auth-retry or auth-fail option
-
See the MACSec Using EAP-TLS Authentication chapter for these configuration details.
See Running Configuration section for examples.
Follow these steps to configure MAC authentication bypass feature.
Procedure
|
Step 1 |
Enable MAB on the dot1x profile. Example: |
|
Step 2 |
Configure the authenticator retry time for MAB clients. Example: |
|
Step 3 |
Attach the dot1x profile to the corresponding interface or port on the router. Example: |
|
Step 4 |
Verify the running configuration on the router. Example: |
Verify MAC Authentication Bypass
Follow these steps to verify MAC authentication bypass feature.
Procedure
|
Step 1 |
Check the MAB summary. Example:The Status field shows as Authorized . |
|
Step 2 |
Verify the detailed status of MAB. Example:The PortControl field shows as Enabled . |
|
Step 3 |
Verify the MAB interface summary. Example:The Status field shows as Authorized . |
|
Step 4 |
Verify the MAB interface details. Example:The PortControl field shows as Enabled . |
|
Step 5 |
Verify the MAB interface statistics. Example:The EnableSuccess field under Port Control shows as 1 . |
System Logs for MAC Authentication Bypass
The router displays these system logs on the console in various MAB scenarios:
-
When you apply dot1x profile on the port, with MAB feature enabled
Success case:
%L2-DOT1X-5-PORT_CONTROL_ENABLE_SUCCESS : Hu0/0/1/0 : Port Control Enabled with Single-Host modeFailure case:
%L2-DOT1X-5-PORT_CONTROL_ENABLE_FAILURE : Hu0/0/1/0 : Failed to enable port-control -
When you remove dot1x profile from the interface
Success case:
%L2-DOT1X-5-PORT_CONTROL_DISABLE_SUCCESS : Hu0/0/1/0 : Port Control DisabledFailure case:
%L2-DOT1X-5-PORT_CONTROL_DISABLE_FAILURE : Hu0/0/1/0 : Failed to disable port-control -
As part of MAB client authentication process
Success case:
%L2-DOT1X-5-MAB_AUTH_SUCCESS : Hu0/0/1/0 : Authentication successful for client <mac-address> %L2-DOT1X-5-PORT_CONTROL_ADD_CLIENT_SUCCESS : Hu0/0/1/0 : Port Access Enabled For Client <mac-address>Failure case:
%L2-DOT1X-5-MAB_AUTH_FAIL : Hu0/0/1/0 : Authentication failed for client <mac-address> %L2-DOT1X-5-PORT_CONTROL_REMOVE_CLIENT_SUCCESS : Hu0/0/1/0 : Port Access Disabled For Client <mac-address> -
When the authentication server is unreachable
%L2-DOT1X-5-MAB_AAA_UNREACHABLE : Hu0/0/1/0 : AAA server unreachable for client 027E.15F2.CAE7, Retrying Authentication
 Feedback
Feedback