This section lists a selected few examples of Cisco MDS NX-OS commands that are displayed as XML, JSON and JSON Native output
formats.
To check if a particular show command is NX-API-aware, enter the command along with | xml on the switch:
command | xml
If a command is NX-API-aware (supports structured output), the resulting output is in XML format:
switch# show device-alias merge status | xml
<?xml version="1.0" encoding="ISO-8859-1"?>
<nf:rpc-reply xmlns="http://www.cisco.com/nxos:8.4.1.SK.0.:ddas" xmlns:nf="urn:ietf:params:xml:ns:netconf:base:1.0">
<nf:data>
<show>
<device-alias>
<merge>
<status>
<__readonly__>
<result>Success</result>
<reason>None</reason>
</__readonly__>
</status>
</merge>
</device-alias>
</show>
</nf:data>
</nf:rpc-reply>
]]>]]>
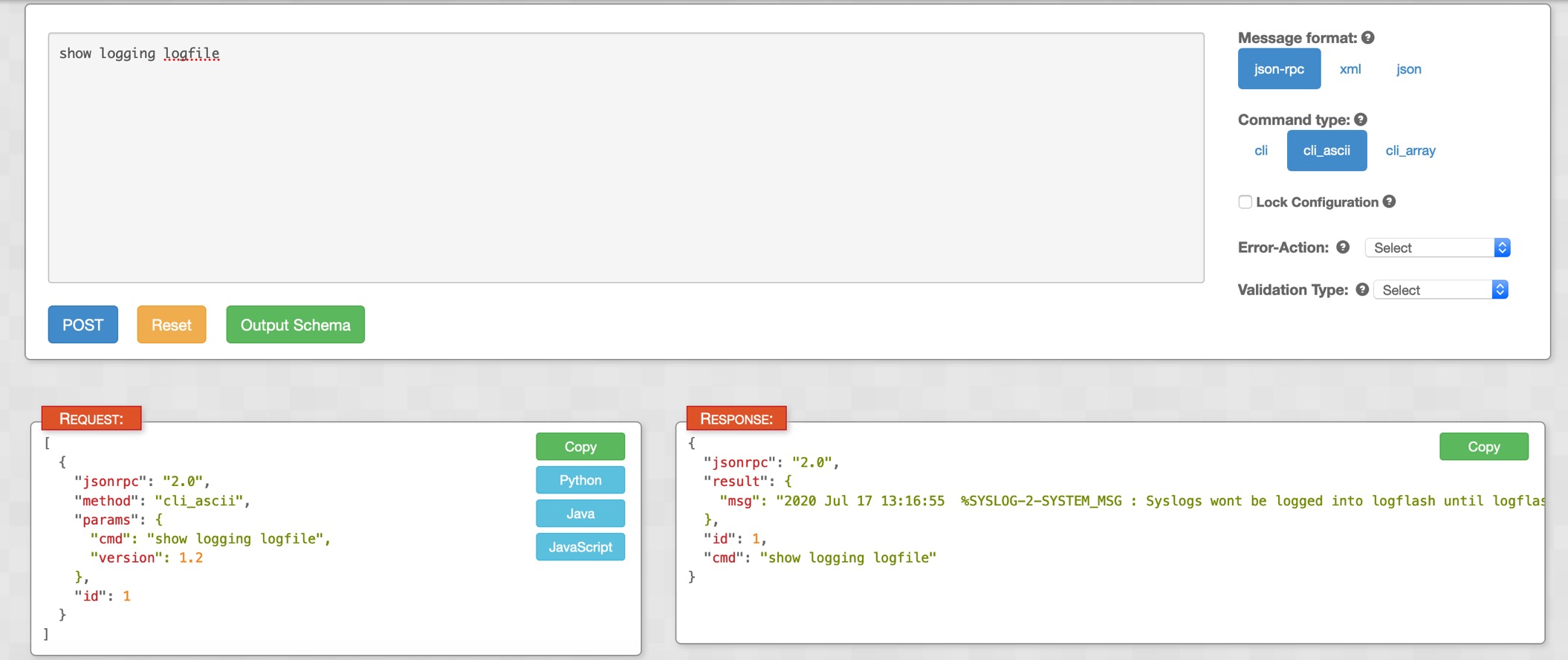
If a command is not NX-API-aware, the resulting output has the following error:
switch# show logging logfile | xml
Error: This command does not support XML output.
This example shows how to display the show version command in the XML format:
switch(config)# show version | xml
<?xml version="1.0" encoding="ISO-8859-1"?>
<nf:rpc-reply xmlns="http://www.cisco.com/nxos:8.4.2.:sysmgrcli" xmlns:nf="urn:ietf:params:xml:ns:netconf:base:1.0">
<nf:data>
<show>
<version>
<__readonly__>
<header_str>Cisco Nexus Operating System (NX-OS) Software
TAC support: http://www.cisco.com/tac
Documents: http://www.cisco.com/en/US/products/ps9372/tsd_products_support_series_home.html
Copyright (c) 2002-2020, Cisco Systems, Inc. All rights reserved.
The copyrights to certain works contained in this software are
owned by other third parties and used and distributed under
license. Certain components of this software are licensed under
the GNU General Public License (GPL) version 2.0 or the GNU
Lesser General Public License (LGPL) Version 2.1. A copy of each
such license is available at
http://www.opensource.org/licenses/gpl-2.0.php and
http://www.opensource.org/licenses/lgpl-2.1.php
</header_str>
<bios_ver_str>3.7.0</bios_ver_str>
<kickstart_ver_str>8.4(2) [build 8.4(2.191)] [gdb]</kickstart_ver_str>
<sys_ver_str>8.4(2) [build 8.4(2.191)] [gdb]</sys_ver_str>
<bios_cmpl_time>04/01/2019</bios_cmpl_time>
<kick_file_name>bootflash:///m9700-sf3ek9-kickstart-mzg.8.4.2.191.bin</kick_file_name>
<kick_cmpl_time> 2/5/2020 12:00:00</kick_cmpl_time>
<kick_tmstmp>01/08/2020 18:27:03</kick_tmstmp>
<isan_file_name>bootflash:///m9700-sf3ek9-mzg.8.4.2.191.bin</isan_file_name>
<isan_cmpl_time> 2/5/2020 12:00:00</isan_cmpl_time>
<isan_tmstmp>01/14/2020 05:36:15</isan_tmstmp>
<chassis_id>MDS 9706 (6 Slot) Chassis</chassis_id>
<module_id>Supervisor Module-3</module_id>
<cpu_name>Intel(R) Xeon(R) CPU C5528 @ 2.13GHz</cpu_name>
<memory>8167228</memory>
<mem_type>kB</mem_type>
<proc_board_id>JAE19220AQJ</proc_board_id>
<host_name>abc</host_name>
<bootflash_size>3915776</bootflash_size>
<slot0_size>0</slot0_size>
<kern_uptm_days>19</kern_uptm_days>
<kern_uptm_hrs>23</kern_uptm_hrs>
<kern_uptm_mins>16</kern_uptm_mins>
<kern_uptm_secs>11</kern_uptm_secs>
<rr_usecs>768558</rr_usecs>
<rr_ctime>Tue Jan 14 05:58:26 2020</rr_ctime>
<rr_reason>Reset Requested by CLI command reload</rr_reason>
<rr_sys_ver>8.4(2.171)</rr_sys_ver>
<rr_service></rr_service>
<manufacturer>Cisco Systems, Inc.</manufacturer>
</__readonly__>
</version>
</show>
</nf:data>
</nf:rpc-reply>
]]>]]>
This example shows how to display the show version in the JSON format:
switch(config)# show version | json
{
"header_str": "Cisco Nexus Operating System (NX-OS) Software\nTAC support: http://www.cisco.com/tac\nDocuments: http://www.cisco.c
om/en/US/products/ps9372/tsd_products_support_series_home.html\nCopyright (c) 2002-2020, Cisco Systems, Inc. All rights reserved.\nT
he copyrights to certain works contained in this software are\nowned by other third parties and used and distributed under\nlicense.
Certain components of this software are licensed under\nthe GNU General Public License (GPL) version 2.0 or the GNU\nLesser General
Public License (LGPL) Version 2.1. A copy of each\nsuch license is available at\nhttp://www.opensource.org/licenses/gpl-2.0.php and
\nhttp://www.opensource.org/licenses/lgpl-2.1.php",
"bios_ver_str": "3.7.0",
"kickstart_ver_str": "8.4(2) [build 8.4(2.191)] [gdb]",
"sys_ver_str": "8.4(2) [build 8.4(2.191)] [gdb]",
"bios_cmpl_time": "04/01/2019",
"kick_file_name": "bootflash:///m9700-sf3ek9-kickstart-mzg.8.4.2.191.bin",
"kick_cmpl_time": "2/5/2020 12:00:00",
"kick_tmstmp": "01/08/2020 18:27:03",
"isan_file_name": "bootflash:///m9700-sf3ek9-mzg.8.4.2.191.bin",
"isan_cmpl_time": "2/5/2020 12:00:00",
"isan_tmstmp": "01/14/2020 05:36:15",
"chassis_id": "MDS 9706 (6 Slot) Chassis",
"module_id": "Supervisor Module-3",
"cpu_name": "Intel(R) Xeon(R) CPU C5528 @ 2.13GHz",
"memory": 8167228,
"mem_type": "kB",
"proc_board_id": "JAE19220AQJ",
"host_name": "abc",
"bootflash_size": 3915776,
"slot0_size": 0,
"kern_uptm_days": 19,
"kern_uptm_hrs": 23,
"kern_uptm_mins": 16,
"kern_uptm_secs": 22,
"rr_usecs": 768558,
"rr_ctime": "Tue Jan 14 05:58:26 2020",
"rr_reason": "Reset Requested by CLI command reload",
"rr_sys_ver": "8.4(2.171)",
"rr_service": null,
"manufacturer": "Cisco Systems, Inc."
}
This example shows how to display the show version in the JSON Native format:
switch(config)# show version | json native
{
"header_str": "Cisco Nexus Operating System (NX-OS) Software\nTAC supp
ort: http://www.cisco.com/tac\nDocuments: http://www.cisco.com/en/US/products/ps
9372/tsd_products_support_series_home.html\nCopyright (c) 2002-2020, Cisco Syste
ms, Inc. All rights reserved.\nThe copyrights to certain works contained herein
are owned by\nother third parties and are used and distributed under license.\nS
ome parts of this software are covered under the GNU Public\nLicense. A copy of
the license is available at\nhttp://www.gnu.org/licenses/gpl.html.\n",
"bios_ver_str": "2.1.18",
"loader_ver_str": "N/A",
"kickstart_ver_str": "8.4(2a)",
"sys_ver_str": "8.4(2a)",
"bios_cmpl_time": "04/06/20",
"kick_file_name": "bootflash:///m9100-s5ek9-kickstart-mz.8.4.2a.bi
n",
"kick_cmpl_time": " 7/11/2020 12:00:00",
"kick_tmstmp": "06/20/2020 20:50:09",
"isan_file_name": "bootflash:///m9100-s5ek9-mz.8.4.2a.bin",
"isan_cmpl_time": " 7/11/2020 12:00:00",
"isan_tmstmp": "06/20/2020 22:05:47",
"chassis_id": "MDS 9148S 16G 48 FC (1 Slot) Chassis",
"module_id": "2/4/8/16 Gbps FC/Supervisor",
"cpu_name": "Motorola, e500v2",
"memory": 4088620,
"mem_type": "kB",
"proc_board_id": "JAF1751BGPS",
"host_name": "sw109-Mini",
"bootflash_size": 4001760,
"kern_uptm_days": 7,
"kern_uptm_hrs": 1,
"kern_uptm_mins": 13,
"kern_uptm_secs": 0,
"rr_usecs": 362070,
"rr_ctime": "Mon Sep 28 07:43:36 2020",
"rr_reason": "Reset due to upgrade",
"rr_sys_ver": "8.4(2b)",
"rr_service": "",
"manufacturer": "Cisco Systems, Inc."
}



 Feedback
Feedback