Configuring Google Cloud Site Connectivity Workflow
The following sections describe how to configure Google Cloud sites infra, intersite connectivity, and a simple deployment use case. The workflow includes:
-
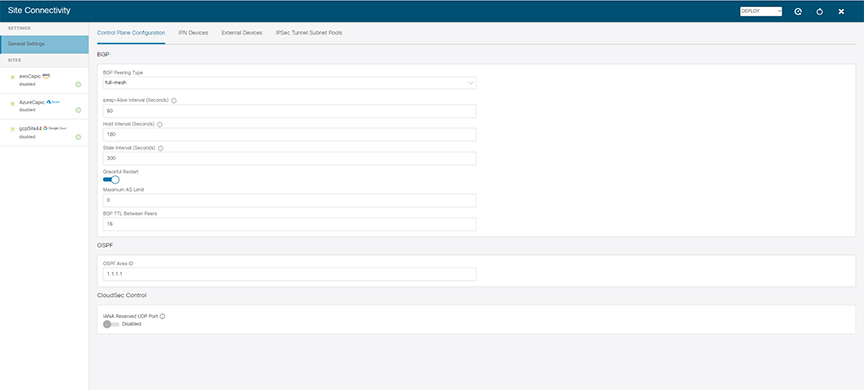
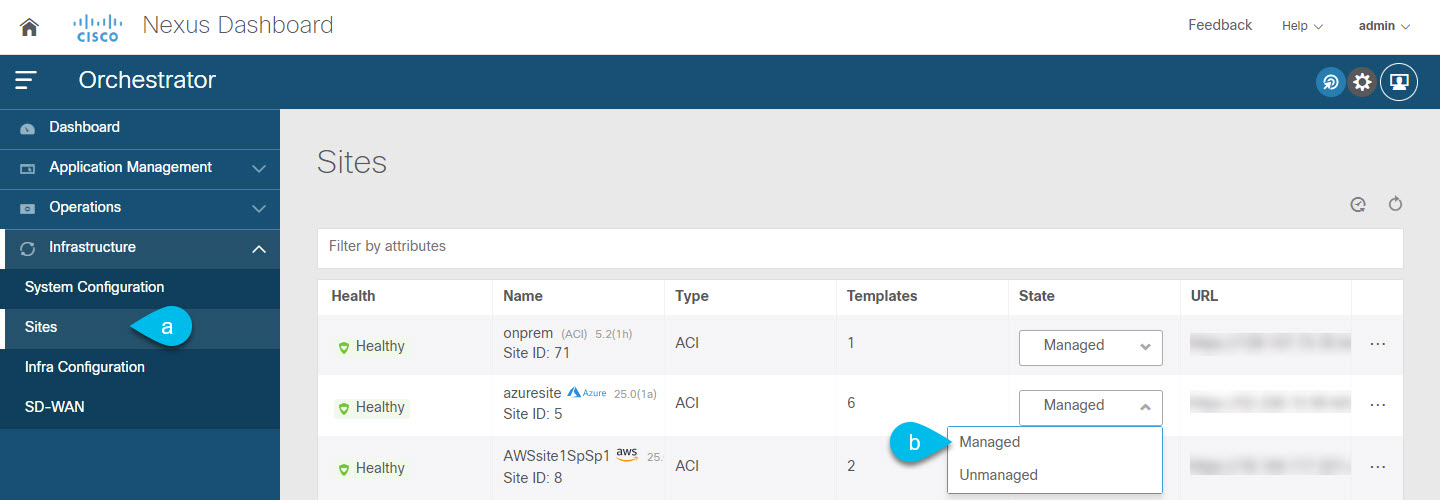
Configuring general infra settings, such as adding the on-premises IPN devices as external devices in Nexus Dashboard Orchestrator and establishing external connectivity from google cloud site to those devices
-
Configuring and deploying external VRFs in the Google Cloud site's Infra tenant
-
Configuring intersite connectivity from your Google Cloud site to an on-premises site and manually configuring any on-premises sites connectivity to the Google Cloud site
-
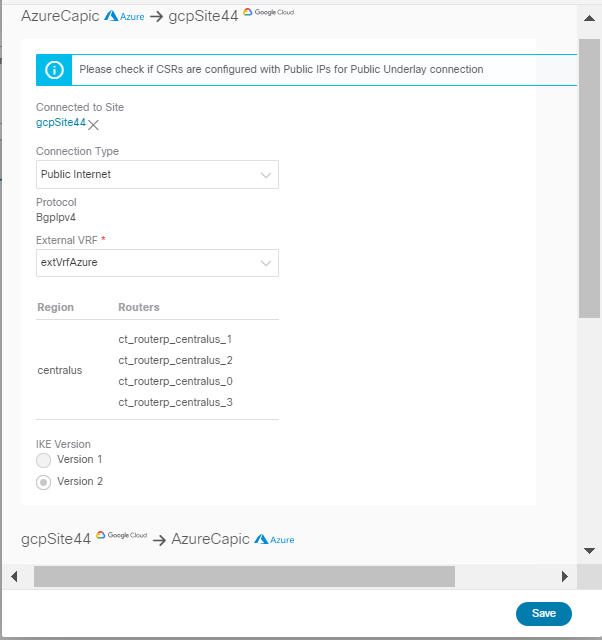
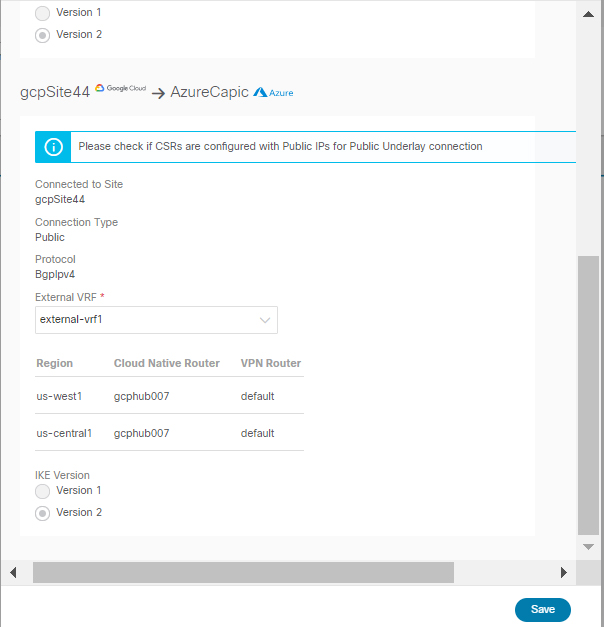
Configuring intersite connectivity between your Google Cloud site and other cloud sites like AWS/Azure
-
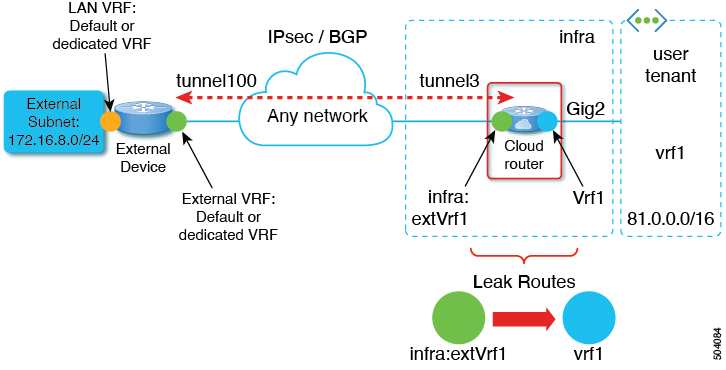
Configuring route leaking in the external VRFs to enable routing between sites
-
Creating or importing a user tenant and EPGs and applying contracts to enable communication between sites








 Feedback
Feedback