Redundant Tunnel Creation between Firewalls using PDM
Available Languages
Contents
Introduction
This document describes the procedure you use to configure tunnels between two PIX firewalls using Cisco PIX Device Manager (PDM). PIX firewalls are placed at two different sites. In case of a failure to reach the primary path, it is desirable to kick off the tunnel through a redundant link. IPsec is a combination of open standards that provide data confidentiality, data integrity, and data origin authentication between IPsec peers.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco Secure PIX 515E Firewalls with 6.x and PDM version 3.0
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
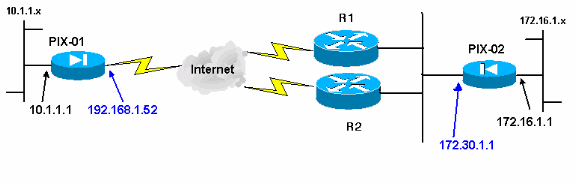
Network Diagram
This document uses this network setup:
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
Background Information
IPsec negotiation can be broken down into five steps, and includes two Internet Key Exchange (IKE) phases.
An IPsec tunnel is initiated by interesting traffic. Traffic is considered interesting when it travels between the IPsec peers.
In IKE Phase 1, the IPsec peers negotiate the established IKE Security Association (SA) policy. Once the peers are authenticated, a secure tunnel is created using Internet Security Association and Key Management Protocol (ISAKMP).
In IKE Phase 2, the IPsec peers use the authenticated and secure tunnel to negotiate IPsec SA transforms. The negotiation of the shared policy determines how the IPsec tunnel is established.
The IPsec tunnel is created and data is transferred between the IPsec peers based on the IPsec parameters configured in the IPsec transform sets.
The IPsec tunnel terminates when the IPsec SAs are deleted or when their lifetime expires.
Note: IPsec negotiation between the two PIXes fails if the SAs on both of the IKE phases do not match on the peers.
Configuration
This procedure guides you through the configuration of one of the PIX firewalls to trigger the tunnel when interesting traffic exists. This configuration also helps you establish the tunnel through the backup link through router 2 (R2), when there is no connectivity between the PIX-01 and PIX-02 through router 1 (R1). This document shows the configuration of PIX-01 using PDM. You can configure PIX-02 on similar lines.
This document assumes that you have already configured the routing.
For only one link to be up at a time, make R2 advertize a worse metric for the 192.168.1.0 network as well as for the 172.30.0.0 network. For example, if you use RIP for the routing, R2 has this configuration apart from other network advertisements:
R2(config)#router rip R2(config-router)#offset-list 1 out 2 s1 R2(config-router)#offset-list 2 out 2 e0 R2(config-router)#exit R2(config)#access-list 1 permit 172.30.0.0 0.0.255.255 R2(config)#access-list 2 permit 192.168.1.0 0.0.0.255
Configuration Procedure
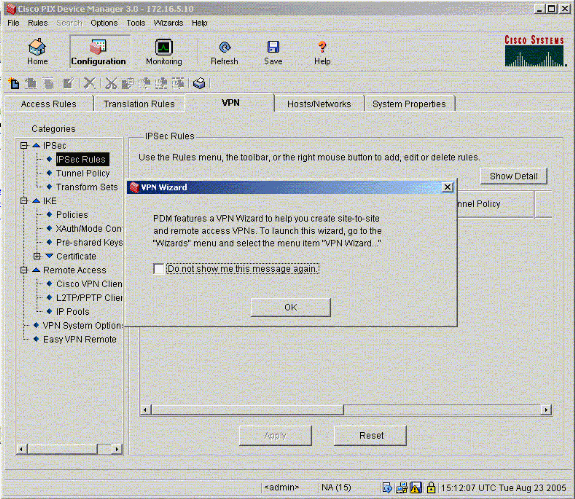
When you type https://<Inside_IP_Address_on_PIX> in order to launch PDM and click the VPN tab for the first time, information about the automatic VPN Wizard displays.
-
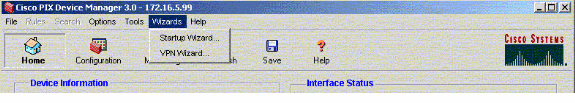
Select Wizards > VPN Wizard.
-
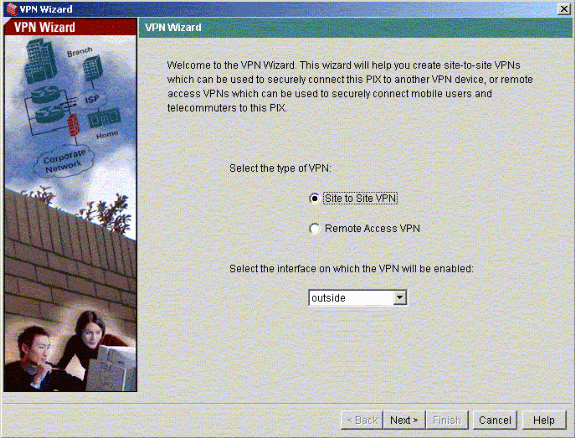
The VPN wizard starts and prompts you for the type of VPN you want to configure. Choose Site-to-Site VPN, select the outside interface as the interface on which the VPN will be enabled, and click Next.
-
Enter the Peer IP address, where the IPsec tunnel should end. In this example, the tunnel ends on the outside interface of PIX-02. Click Next.
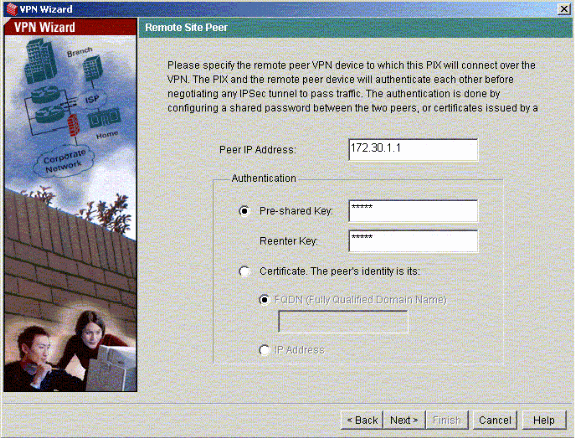
-
Enter the IKE Policy parameters that you choose to use and click Next.
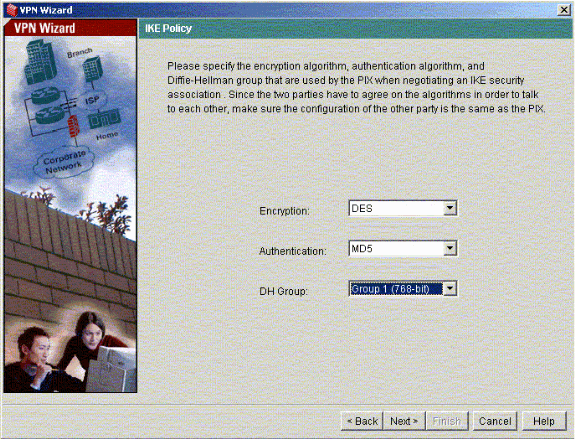
-
Provide the Encryption and Authentication parameters for the Transform Set and click Next.
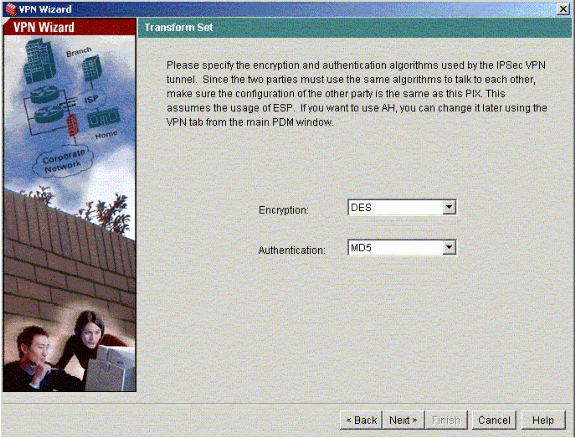
-
Select the local network and the remote networks you need to protect using IPsec in order to select the interesting traffic that you need to protect.
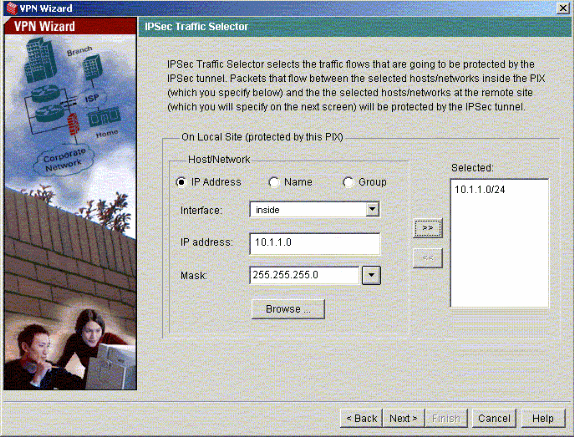
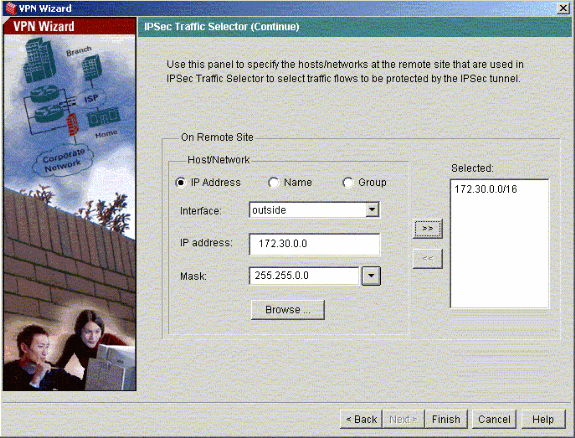
Verify
If there is interesting traffic to the peer, the tunnel is established between PIX-01 and PIX-02.
In order to verify this, shut down the R1 serial interface for which the tunnel is established between PIX-01 and PIX-02 via R2 when the interesting traffic exists.
View the VPN Status under Home in the PDM (highlighted in red) in order to verify the formation of the tunnel.
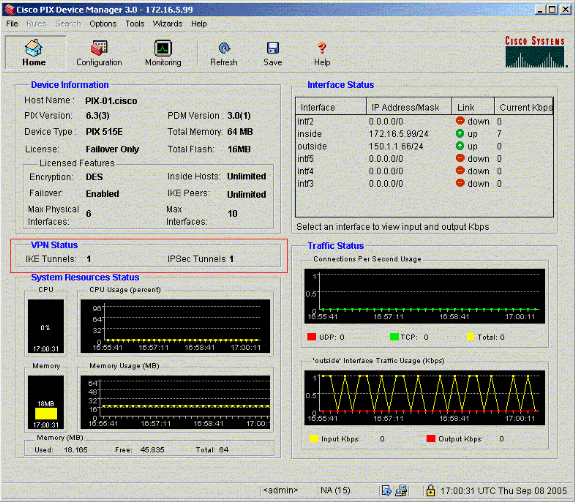
You can also verify the formation of tunnels using CLI under Tools in the PDM. Issue the show crypto isakmp sa command to check the formation of tunnels and issue the show crypto ipsec sa command to observe the number of packets encapsulated, encrypted, and so forth.
The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output.
Refer to Cisco PIX Device Manager 3.0 for more information on the configuration of the PIX Firewall using PDM.
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
02-Feb-2006 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)







 Feedback
Feedback