疑難排解 COS AP
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
目錄
簡介
本文檔介紹運行COS作業系統的AP(Cheetah OS、Click OS、simply Cisco AP OS)可用的部分故障排除工具。
必要條件
需求
本文件沒有特定需求。
採用元件
本文檔重點介紹COS AP,如系列2800、3800、1560和4800的AP型號,以及新的11ax AP Catalyst 91xx。
本文檔重點介紹AireOS 8.8及更高版本中的許多功能。以及Cisco IOS® XE 16.12.2s及更高版本。
在以前的版本中,可能會出現有關某些功能可用性的註釋。
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
擷取封包追蹤(監聽器追蹤)
AP埠上的有線PCAP
可以對AP乙太網埠使用pcap。您可以在CLI上即時顯示結果(僅包含彙總的資料包詳細資訊),也可以將其儲存為AP快閃記憶體中的完整pcap。
有線pcap會擷取乙太網路端的所有內容(包括Rx/Tx),且存取點內的分流點會在封包上線之前立即執行。
但是,它僅捕獲AP CPU平面流量,這意味著進出該AP的流量(AP DHCP、AP capwap控制隧道……)並且不顯示客戶端流量。
請注意,大小非常有限(最大大小限製為5MB),因此可能需要配置過濾器以僅捕獲您感興趣的流量。
嘗試複製流量之前,請務必使用「no debug traffic wired ip capture」或「undebug all」來停止流量擷取(否則複製不會因為封包仍在寫入而結束)。
程式
步驟1.啟動pcap;使用「debug traffic wired ip capture」選擇流量型別:
AP70DB.98E1.3DEC#debug traffic wired ip capture
% Writing packets to "/tmp/pcap/AP70DB.98E1.3DEC_capture.pcap0"
AP70DB.98E1.3DEC#reading from file /dev/click_wired_log, link-type EN10MB (Ethernet)
步驟2.等待流量通過,然後使用命令「no debug traffic wired ip capture」或簡單的「undebug all」停止捕獲:
AP70DB.98E1.3DEC#no debug traffic wired ip capture
步驟3.將檔案複製到tftp/scp伺服器:
AP70DB.98E1.3DEC#copy pcap AP70DB.98E1.3DEC_capture.pcap0 tftp 192.168.1.100
###################################################################################################################################################################### 100.0%
AP70DB.98E1.3DEC#
步驟4.現在您可以在wireshark中開啟該檔案。該檔案為pcap0。請更改為pcap,以便它自動與wireshark關聯。
命令選項
debug traffic wired命令有幾個選項可以幫助您捕獲特定流量:
APC4F7.D54C.E77C#debug traffic wired
<0-3> wired debug interface number
filter filter packets with tcpdump filter string
ip Enable wired ip traffic dump
tcp Enable wired tcp traffic dump
udp Enable wired udp traffic dum
您可以在debug指令的結尾新增「verbose」來檢視封包的十六進位制轉儲。請注意,如果過濾條件不夠嚴格,CLI會話可能會很快被淹沒。
使用過濾器實現有線PCAP
過濾器格式與tcpdump捕獲過濾器格式相對應。
| 過濾器示例 |
說明 |
|
| 主機 |
"主機192.168.2.5" |
此指令會過濾封包擷取,以便只收集前往或來自主機192.168.2.5的封包。 |
| "src host 192.168.2.5" |
這樣會過濾封包擷取,只收集來自192.168.2.5的封包。 |
|
| "dst host 192.168.2.5" |
此指令會過濾封包擷取,以便只收集前往192.168.2.5的封包。 |
|
| 連接埠 |
"埠443" |
此指令會過濾封包擷取,以僅收集具有連線埠443來源或目的地的封包。 |
| "src埠1055" |
這會擷取源自連線埠1055的流量。 |
|
| "dst埠443" |
這會擷取目的地為連線埠443的流量。 |
以下示例中的輸出顯示在控制檯上,但也經過過濾以僅檢視CAPWAP資料包:
APC4F7.D54C.E77C#debug traffic wired filter "port 5246"
APC4F7.D54C.E77C#reading from file /dev/click_wired_log, link-type EN10MB (Ethernet)
12:20:50.483125 IP APC4F7-D54C-E77C.lan.5264 > 192.168.1.15.5246: UDP, length 81
12:20:50.484361 IP 192.168.1.15.5246 > APC4F7-D54C-E77C.lan.5264: UDP, length 97
APC4F7.D54C.E77C#no debug traffic wired filter "port 5246"
APC4F7.D54C.E77C#Killed
APC4F7.D54C.E77C#
檔案輸出示例:
APC4F7.D54C.E77C#debug traffic wired filter "port 5246" capture
% Writing packets to "/tmp/pcap/APC4F7.D54C.E77C_capture.pcap0"
APC4F7.D54C.E77C#reading from file /dev/click_wired_log, link-type EN10MB (Ethernet)
APC4F7.D54C.E77C#no debug traffic wired filter "port 5246" capture
APC4F7.D54C.E77C#copy pcap APC4F7.D54C.E77C_capture.pcap0 tftp 192.168.1.100
###################################################################################################################################################################### 100.0%
APC4F7.D54C.E77C#
要在wireshark上開啟捕獲,請執行以下操作:
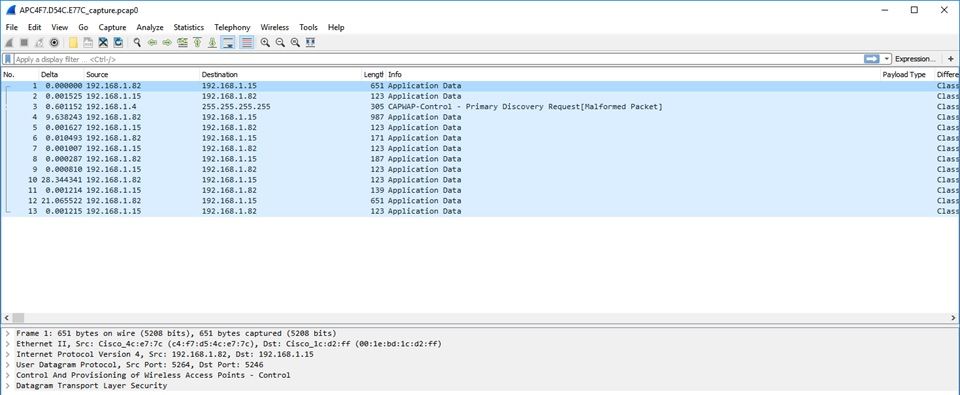
無線電捕獲
可以在無線電的控制平面上啟用資料包捕獲。由於效能影響,無法在無線電資料平面上捕獲。
這意味著客戶端關聯流(探測、身份驗證、關聯、eap、arp、dhcp資料包以及ipv6控制資料包、icmp和ndp)可見,但客戶端在移動到連線狀態後傳送的資料不可見。
程式
步驟1.新增跟蹤的客戶端mac地址。可以新增多個mac地址。也可以對所有客戶端運行該命令,但不建議這樣做。
config ap client-trace address add < client-mac> --- Per client debugging. Allows multiple macs.
config ap client-trace all-clients <enable | disable> -- All clients debugging. Not recommended.
步驟2.將過濾器設定為僅記錄特定協定或所有支援的協定:
config ap client-trace filter <all|arp|assoc|auth|dhcp|eap|icmp|ipv6|ndp|probe> <enable|disable>
步驟3.選擇在控制檯上顯示輸出(非同步):
configure ap client-trace output console-log enable
步驟4.啟動跟蹤。
config ap client-trace start
範例:
AP0CD0.F894.46E4#show dot11 clients
Total dot11 clients: 1
Client MAC Slot ID WLAN ID AID WLAN Name RSSI Maxrate WGB
A8:DB:03:08:4C:4A 0 1 1 testewlcwlan -41 MCS92SS No
AP0CD0.F894.46E4#config ap client-trace address add A8:DB:03:08:4C:4A
AP0CD0.F894.46E4#config ap client-trace filter
all Trace ALL filters
arp Trace arp Packets
assoc Trace assoc Packets
auth Trace auth Packets
dhcp Trace dhcp Packets
eap Trace eap Packets
icmp Trace icmp Packets
ipv6 Trace IPv6 Packets
ndp Trace ndp Packets
probe Trace probe Packets
AP0CD0.F894.46E4#config ap client-trace filter all enable
AP0CD0.F894.46E4#configure ap client-trace output console-log enable
AP0CD0.F894.46E4#configure ap client-trace start
AP0CD0.F894.46E4#term mon
要停止捕獲,請執行以下操作:
configure ap client-trace stop
configure ap client-trace clear
configure ap client-trace address clear
驗證
驗證客戶端跟蹤:
AP70DB.98E1.3DEC#show ap client-trace status
Client Trace Status : Started
Client Trace ALL Clients : disable
Client Trace Address : a8:db:03:08:4c:4a
Remote/Dump Client Trace Address : a8:db:03:08:4c:4a
Client Trace Filter : probe
Client Trace Filter : auth
Client Trace Filter : assoc
Client Trace Filter : eap
Client Trace Filter : dhcp
Client Trace Filter : dhcpv6
Client Trace Filter : icmp
Client Trace Filter : icmpv6
Client Trace Filter : ndp
Client Trace Filter : arp
Client Trace Output : eventbuf
Client Trace Output : console-log
Client Trace Output : dump
Client Trace Output : remote
Remote trace IP : 192.168.1.100
Remote trace dest port : 5688
NOTE - Only VIP packets are seen on remote if VIP is enabled
Dump packet length : 10
Client Trace Inline Monitor : disable
Client Trace Inline Monitor pkt-attach : disable
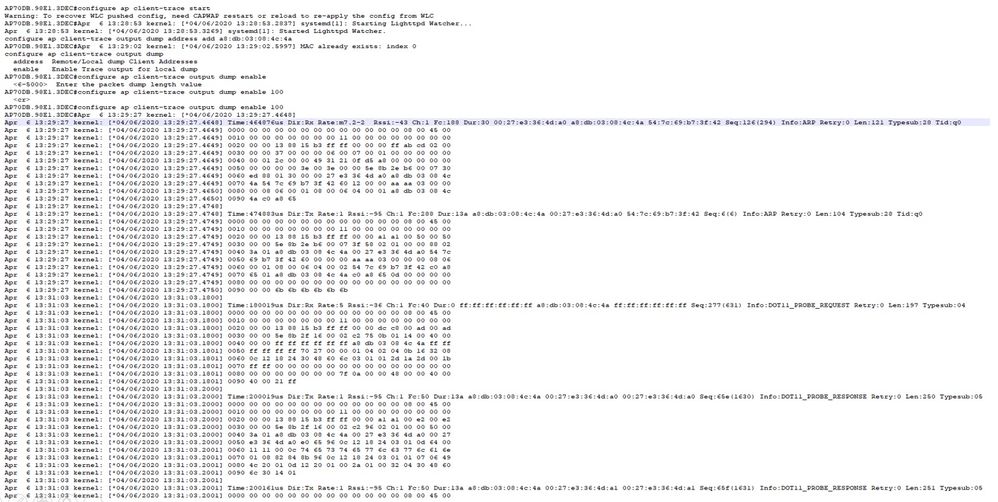
成功的客戶端連線示例:
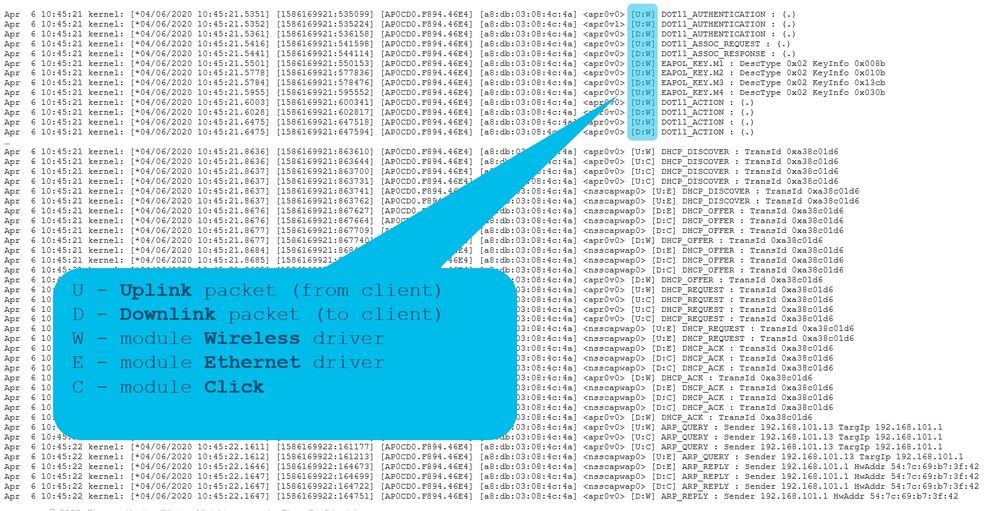
括弧中的字母可幫助您瞭解該幀出現在何處(E表示乙太網,W表示無線,C表示在AP內部的Click模組),以及在哪個方向(上傳或下載)。
下面是一張小表,上面列出了這些字母的含義:
U — 上行鏈路資料包(來自客戶端)
D — 下行鏈路資料包(按一下)
W — 模組無線驅動程式
E — 模組乙太網驅動程式
C — 模組按一下
附註: 從17.12.1開始,新增了一個附加的字母A,以幫助驗證資料包是否通過空中傳送:
[D:W]部分,用於讓aptrace知道有關通過kclick成功傳遞給驅動程式的管理/資料資料包
[D:A]部分,用於在通過空中傳送資料包時讓aptrace知道相應的管理/資料資料包pkts tx完成狀態
其他選項
非同步檢視日誌:
然後可使用以下命令檢視日誌:「show ap client-trace events mac xx:xx:xx:xx:xx:xx:xx」(或將mac替換為「all」)
AP0CD0.F894.46E4#show ap client-trace events mac a8:db:03:08:4c:4a
[*04/06/2020 10:11:54.287675] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v1> [U:W] DOT11_AUTHENTICATION : (.)
[*04/06/2020 10:11:54.288144] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] DOT11_AUTHENTICATION : (.)
[*04/06/2020 10:11:54.289870] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [U:W] DOT11_ASSOC_REQUEST : (.)
[*04/06/2020 10:11:54.317341] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] DOT11_ASSOC_RESPONSE : (.)
[*04/06/2020 10:11:54.341370] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] EAPOL_KEY.M1 : DescType 0x02 KeyInfo 0x008b
[*04/06/2020 10:11:54.374500] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [U:W] EAPOL_KEY.M2 : DescType 0x02 KeyInfo 0x010b
[*04/06/2020 10:11:54.377237] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] EAPOL_KEY.M3 : DescType 0x02 KeyInfo 0x13cb
[*04/06/2020 10:11:54.390255] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [U:W] EAPOL_KEY.M4 : DescType 0x02 KeyInfo 0x030b
[*04/06/2020 10:11:54.396855] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [U:W] DOT11_ACTION : (.)
[*04/06/2020 10:11:54.416650] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] DOT11_ACTION : (.)
[*04/06/2020 10:11:54.469089] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [U:W] DOT11_ACTION : (.)
[*04/06/2020 10:11:54.469157] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] DOT11_ACTION : (.)
[*04/06/2020 10:11:57.921877] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [U:W] DOT11_ACTION : (.)
[*04/06/2020 10:11:57.921942] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] DOT11_ACTION : (.)
[*04/06/2020 10:15:36.123119] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] DOT11_DEAUTHENTICATION : (.)
[*04/06/2020 10:15:36.127731] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr1v0> [D:W] DOT11_DISASSOC : (.)
[*04/06/2020 10:17:24.128751] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [U:W] DOT11_AUTHENTICATION : (.)
[*04/06/2020 10:17:24.128870] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v1> [U:W] DOT11_AUTHENTICATION : (.)
[*04/06/2020 10:17:24.129303] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [D:W] DOT11_AUTHENTICATION : (.)
[*04/06/2020 10:17:24.133026] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [U:W] DOT11_ASSOC_REQUEST : (.)
[*04/06/2020 10:17:24.136095] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [D:W] DOT11_ASSOC_RESPONSE : (.)
[*04/06/2020 10:17:24.138732] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [D:W] EAPOL_KEY.M1 : DescType 0x02 KeyInfo 0x008b
[*04/06/2020 10:17:24.257295] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [U:W] EAPOL_KEY.M2 : DescType 0x02 KeyInfo 0x010b
[*04/06/2020 10:17:24.258105] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [D:W] EAPOL_KEY.M3 : DescType 0x02 KeyInfo 0x13cb
[*04/06/2020 10:17:24.278937] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [U:W] EAPOL_KEY.M4 : DescType 0x02 KeyInfo 0x030b
[*04/06/2020 10:17:24.287459] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [U:W] DOT11_ACTION : (.)
[*04/06/2020 10:17:24.301344] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [D:W] DOT11_ACTION : (.)
[*04/06/2020 10:17:24.327482] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [U:W] DOT11_ACTION : (.)
[*04/06/2020 10:17:24.327517] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [D:W] DOT11_ACTION : (.)
[*04/06/2020 10:17:24.430136] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [U:W] DOT11_ACTION : (.)
[*04/06/2020 10:17:24.430202] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [D:W] DOT11_ACTION : (.)
[*04/06/2020 10:19:08.075326] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [U:W] DOT11_PROBE_REQUEST : (.)
[*04/06/2020 10:19:08.075392] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v0> [D:W] DOT11_PROBE_RESPONSE : (.)
[*04/06/2020 10:19:08.075437] [AP0CD0.F894.46E4] [a8:db:03:08:4c:4a] <apr0v1> [U:W] DOT11_PROBE_REQUEST : (.)
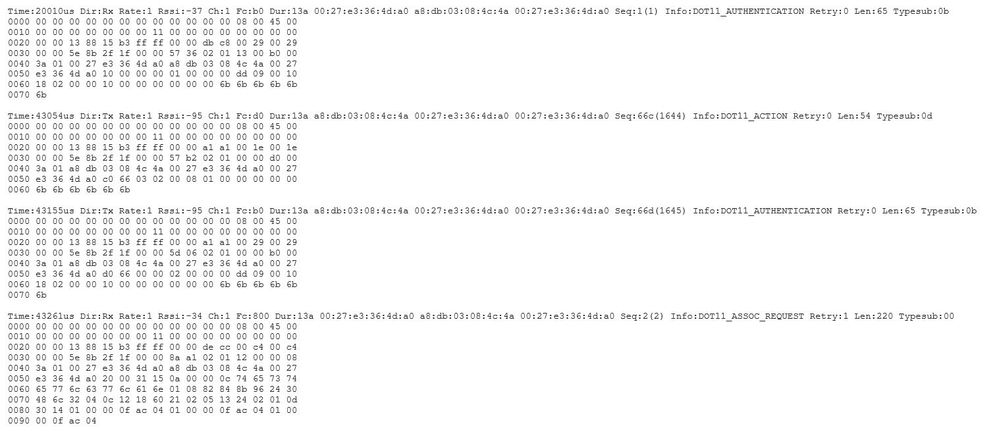
以十六進位制格式轉儲資料包
您可以在CLI中轉儲十六進位制格式的資料包:
configure ap client-trace output dump address add xx:xx:xx:xx:xx:xx
configure ap client-trace output dump enable x -> Enter the packet dump length value
然後,您可以清除十六進位制轉儲並以txt格式儲存並匯入到wireshark中:
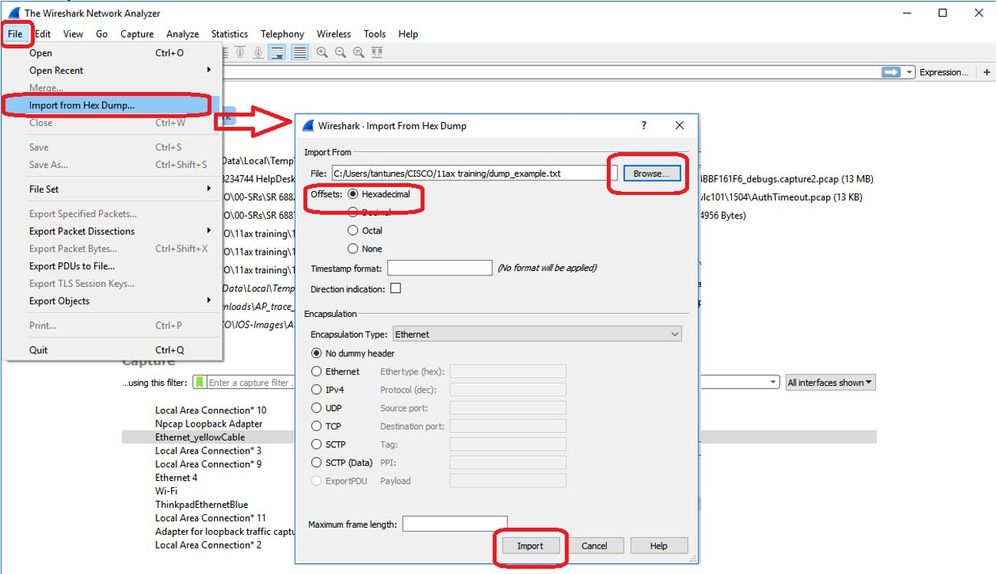
由於輸出可能非常大,並且要考慮到輸出只提到可見的幀型別,而不提到任何內部細節,因此將資料包捕獲重定向到運行捕獲應用程式(如wireshark)的筆記型電腦可能更有效。
啟用遠端捕獲功能,以便使用wireshark將資料包傳送到外部裝置:
config ap client-trace output remote enable
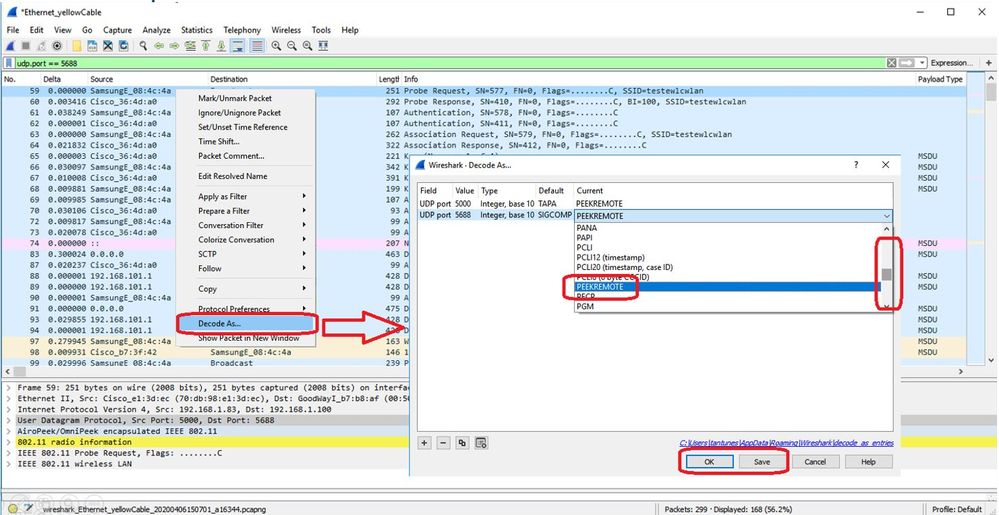
此命令表示AP將client-trace filter捕獲的每個幀轉發到地址為192.168.68.68的膝上型電腦,並在埠5000上使用PEEKREMOTE封裝(與監聽器模式中的AP一樣)。
一個限制是,目標筆記型電腦必須與您在其上運行此命令的AP位於同一個子網中。您可以更改埠號以容納網路中的所有安全策略。
在運行Wireshark的筆記型電腦上收到所有資料包後,您可以右擊udp 5000報頭,選擇decode as並選擇PEEKREMOTE,如下圖所示:
有關此功能的錯誤和增強功能的清單:
思科錯誤ID CSCvm09020 8.8上的客戶端跟蹤不再顯示DNS
8.8上的客戶端跟蹤不再顯示DNS
思科錯誤ID CSCvm09015 客戶端跟蹤顯示許多ICMP_other,序列號為null
客戶端跟蹤顯示許多ICMP_other,序列號為null
思科錯誤ID CSCvm02676 AP COS客戶端跟蹤不會捕獲webauth資料包
AP COS客戶端跟蹤不會捕獲webauth資料包
思科錯誤ID CSCvm02613  AP COS客戶端跟蹤遠端輸出無法正常工作
AP COS客戶端跟蹤遠端輸出無法正常工作
思科錯誤ID CSCvm00855  客戶端跟蹤SEQ號不一致
客戶端跟蹤SEQ號不一致
從9800 WLC控制AP客戶端跟蹤
可以配置多個AP以執行無線客戶端跟蹤並從
步驟1.配置定義要捕獲的流量的AP跟蹤配置檔案
config term
wireless profile ap trace
filter all no filter probe output console-log
步驟 2. 將AP跟蹤配置檔案新增到目標的AP使用的AP加入配置檔案中。
ap profile < ap join profile name>
trace
確保將此AP加入配置檔案應用於目標AP使用的站點標籤
第4步觸發啟動/停止
ap trace client start ap
client all/
ap trace client stop ap
client all/
ap trace client start site
client all/
ap trace client stop site
client all/
驗證命令:
show wireless profile ap trace summary
show wireless profile ap trace detailed PROF_NAME detail
sh ap trace client summary
show ap trace unsupported-ap summaryAP上的客戶端調試捆綁包
如果您正在調試一個或多個特定客戶端,使用客戶端調試捆綁功能可能比收集無線電調試/捕獲更容易。
步驟1.確定您要排除的客戶端。
9164#show dot11 clients
Total dot11 clients: 6
Client MAC Slot ID WLAN ID AID WLAN Name RSSI Maxrate is_wgb_wired is_
mld_sta
52:1E:34:C9:D6:F3 1 2 35 MySSID -62 M7 No
No
80:A9:97:2C:DC:6E 1 2 34 MySSID -47 MCS112SS No
No
E8:D8:D1:1F:71:F3 0 2 35 MySSID -62 M7 No
No
6A:E4:06:E7:AB:E1 1 2 33 MySSID -44 MCS112SS No
No
00:1D:63:70:AC:23 0 2 33 MySSID -56 M7 No
No
68:72:C3:FD:17:F5 0 2 34 MySSID -53 M15 No
No
步驟2.啟動一個或多個客戶端MAC地址的調試
9164#debug client-bundle start debug 80:A9:97:2C:DC:6E
WORD
預設情況下,螢幕上不列印任何內容。您可以啟用terminal monitor並即時檢視正在列印的調試,但請注意,這將使終端很難使用。收集套件組合時,無需在終端機上列印偵錯。
步驟3.您必須停止偵錯套件組合,才能上傳其輸出:
debug client-bundle start debug 80:A9:97:2C:DC:6E步驟4.將套件組合上傳到FTP或SCP伺服器(以提醒WLC可以充當SCP伺服器)
9164#debug client-bundle upload tftp 192.168.129.29 80:a9:97:2c:dc:6e
2024-09-04 11:58:48 Creating client bundle, please wait...
2024-09-04 11:59:01 Client bundle file 9164-_client_bundle.17.15.1.6.20240904.115848.tgz created.
2024-09-04 11:59:01 TFTP uploading...
Successful file transfer:
9164_client_bundle.17.15.1.6.20240904.115848.tgz
9164#TGZ捆綁包包含4個檔案:
- 2個包含與無線電和客戶端相關的show命令
- 1關於實際調試(如果執行term mon,則會在終端上顯示)
- 1個包含syslog
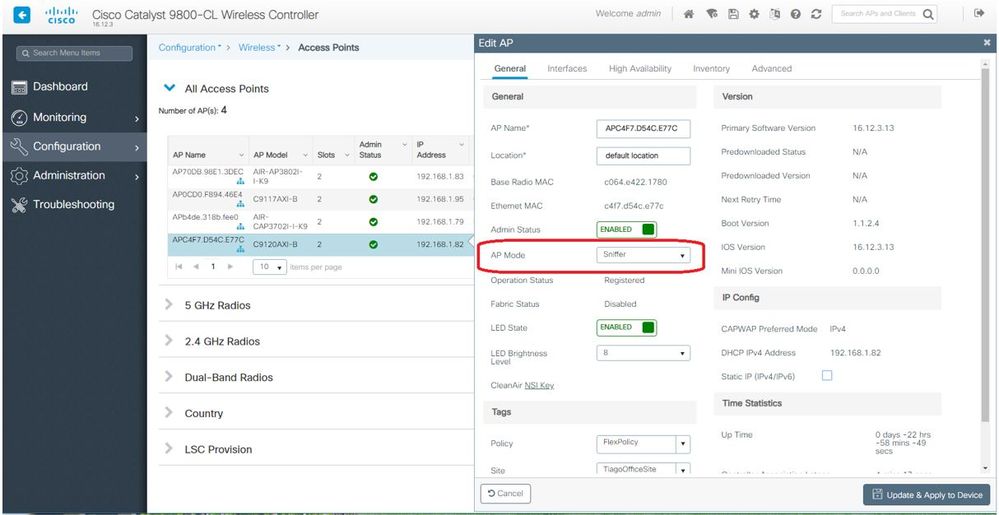
處於監聽器模式的 Catalyst 91xx AP
新的Catalyst 9115、9117、9120和9130可以在監聽器模式下設定。此過程與以前的AP模型類似。
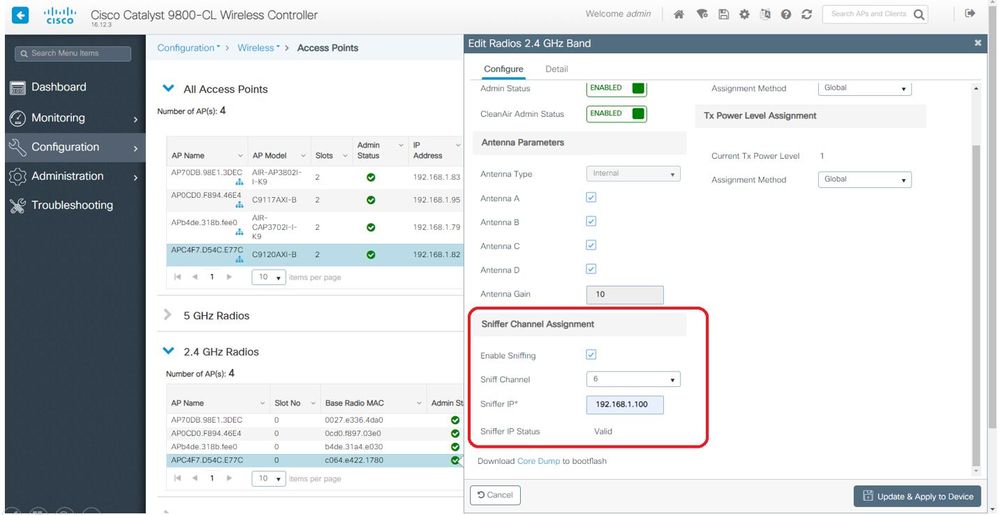
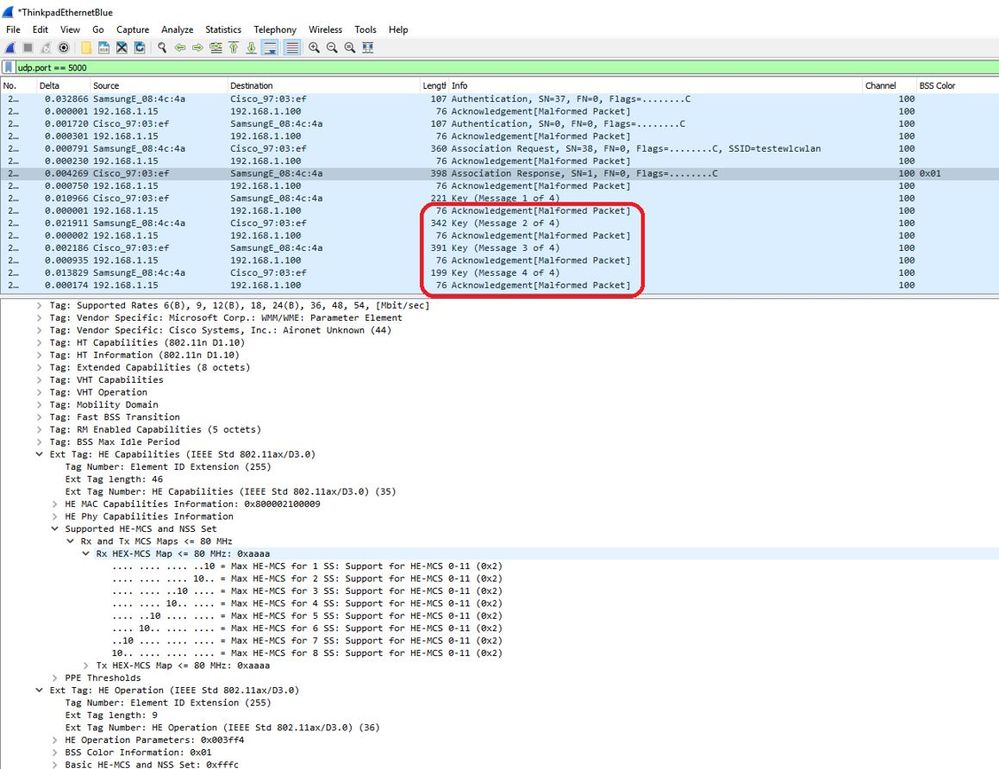
附註:捕獲以WIFI 6資料速率傳送的資料幀,但由於peekremote在Wireshark上不是最新的,因此它們現在顯示為802.11ax phy型別。修復在Wireshark 3.2.4中,其中Wireshark顯示正確的WiFi6物理速率。
附註:Cisco AP此時無法捕獲MU-OFDMA幀,但可以捕獲通告MU-OFDMA視窗的觸發幀(以管理資料速率傳送)。您已經可以推斷MU-OFDMA已發生(或未發生)以及客戶端與哪個發生。
疑難排解提示
路徑MTU
雖然路徑MTU發現可找到AP的最佳MTU,但可以手動覆蓋此設定。
在AireOS 8.10.130 WLC上,命令config ap pmtu disable <ap/all>可為一個或所有AP設定靜態MTU,而不是依賴動態探索機制。
要在引導時啟用調試,請執行以下操作
您可以在下次引導時運行config boot debug capwap以啟用capwap、DTLS和DHCP調試,即使在作業系統已引導且顯示提示之前也是如此。
您還有幾個記憶體調試的「config boot debug memory xxxx」。
您可以使用「show boot」檢視下次重新啟動時是否啟用了引導調試。
您可以通過在結尾處新增disable關鍵字(例如「config boot debug capwap disable」)來禁用它們。
省電機制
可以通過運行以下命令來診斷給定客戶端的節能問題
debug client trace <mac address>
客戶端QoS
若要驗證是否應用了QoS標籤,可以運行「debug capwap client qos」。
它顯示無線客戶端的資料包的UP值。
自8.8起,它不能進行MAC過濾; 增強請求Cisco錯誤IDCSCvm08899  )。
)。
labAP#debug capwap client qos [*08/20/2018 09:43:36.3171] chatter: set_qos_up :: SetQosPriority: bridged packet dst: 00:AE:FA:78:36:89 UP: 0 [*08/20/2018 09:43:45.0051] chatter: set_qos_up :: SetQosPriority: bridged packet dst: 00:AE:FA:78:36:89 UP: 0 [*08/20/2018 09:43:45.5463] chatter: set_qos_up :: SetQosPriority: bridged packet dst: 00:AE:FA:78:36:89 UP: 0 [*08/20/2018 09:43:46.5687] chatter: set_qos_up :: SetQosPriority: bridged packet dst: AC:81:12:C7:CD:35 UP: 5 [*08/20/2018 09:43:47.0982] chatter: set_qos_up :: SetQosPriority: bridged packet dst: AC:81:12:C7:CD:35 UP: 5
您還可以驗證AP上的Qos UP到DSCP表以及Qos標籤、整形和丟棄的資料包總數:
LabAP#show dot11 qos Qos Policy Maps (UPSTREAM) no policymap Qos Stats (UPSTREAM) total packets: 0 dropped packets: 0 marked packets: 0 shaped packets: 0 policed packets: 0 copied packets: 0 DSCP TO DOT1P (UPSTREAM) Default dscp2dot1p Table Value: [0]->0 [1]->2 [2]->10 [3]->18 [4]->26 [5]->34 [6]->46 [7]->48 Active dscp2dot1p Table Value: [0]->0 [1]->2 [2]->10 [3]->18 [4]->26 [5]->34 [6]->46 [7]->48 Qos Policy Maps (DOWNSTREAM) no policymap Qos Stats (DOWNSTREAM) total packets: 0 dropped packets: 0 marked packets: 0 shaped packets: 0 policed packets: 0 copied packets: 0 DSCP TO DOT1P (DOWNSTREAM) Default dscp2dot1p Table Value: [0]->0 [1]->-1 [2]->1 [3]->-1 [4]->1 [5]->-1 [6]->1 [7]->-1 [8]->-1 [9]->-1 [10]->2 [11]->-1 [12]->2 [13]->-1 [14]->2 [15]->-1 [16]->-1 [17]->-1 [18]->3 [19]->-1 [20]->3 [21]->-1 [22]->3 [23]->-1 [24]->-1 [25]->-1 [26]->4 [27]->-1 [28]->-1 [29]->-1 [30]->-1 [31]->-1 [32]->-1 [33]->-1 [34]->5 [35]->-1 [36]->-1 [37]->-1 [38]->-1 [39]->-1 [40]->-1 [41]->-1 [42]->-1 [43]->-1 [44]->-1 [45]->-1 [46]->6 [47]->-1 [48]->7 [49]->-1 [50]->-1 [51]->-1 [52]->-1 [53]->-1 [54]->-1 [55]->-1 [56]->7 [57]->-1 [58]->-1 [59]->-1 [60]->-1 [61]->-1 [62]->-1 [63]->-1 Active dscp2dot1p Table Value: [0]->0 [1]->-1 [2]->1 [3]->-1 [4]->1 [5]->-1 [6]->1 [7]->-1 [8]->-1 [9]->-1 [10]->2 [11]->-1 [12]->2 [13]->-1 [14]->2 [15]->-1 [16]->-1 [17]->-1 [18]->3 [19]->-1 [20]->3 [21]->-1 [22]->3 [23]->-1 [24]->-1 [25]->-1 [26]->4 [27]->-1 [28]->-1 [29]->-1 [30]->-1 [31]->-1 [32]->-1 [33]->-1 [34]->5 [35]->-1 [36]->-1 [37]->-1 [38]->-1 [39]->-1 [40]->-1 [41]->-1 [42]->-1 [43]->-1 [44]->-1 [45]->-1 [46]->6 [47]->-1 [48]->7 [49]->-1 [50]->-1 [51]->-1 [52]->-1 [53]->-1 [54]->-1 [55]->-1 [56]->7 [57]->-1 [58]->-1 [59]->-1 [60]->-1 [61]->-1 [62]->-1 [63]->-1 LabAP#
在WLC上定義Qos策略並在Flexconnect AP上下載時,可以使用進行驗證:
AP780C-F085-49E6#show policy-map
2 policymaps
Policy Map BWLimitAAAClients type:qos client:default
Class BWLimitAAAClients_AVC_UI_CLASS
drop
Class BWLimitAAAClients_ADV_UI_CLASS
set dscp af41 (34)
Class class-default
police rate 5000000 bps (625000Bytes/s)
conform-action
exceed-action
Policy Map platinum-up type:qos client:default
Class cm-dscp-set1-for-up-4
set dscp af41 (34)
Class cm-dscp-set2-for-up-4
set dscp af41 (34)
Class cm-dscp-for-up-5
set dscp af41 (34)
Class cm-dscp-for-up-6
set dscp ef (46)
Class cm-dscp-for-up-7
set dscp ef (46)
Class class-default
no actions
在Qos速率限制的情況下:
AP780C-F085-49E6#show rate-limit client
Config:
mac vap rt_rate_out rt_rate_in rt_burst_out rt_burst_in nrt_rate_out nrt_rate_in nrt_burst_out nrt_burst_in
A8:DB:03:6F:7A:46 2 0 0 0 0 0 0 0 0
Statistics:
name up down
Unshaped 0 0
Client RT pass 0 0
Client NRT pass 0 0
Client RT drops 0 0
Client NRT drops 0 38621
9 54922 0
非通道掃描
在排查欺詐檢測故障時(驗證AP是否和何時進入要掃描的特定通道),調試AP的通道外掃描非常有用,但在未使用「通道外掃描延遲」功能時,在敏感即時流不斷中斷的影片故障排除中,調試也非常有用。
debug rrm off-channel defer
debug rrm off-chanel dbg (starting 17.8.1) debug rrm off-channel schedule
debug rrm off-channel voice (starting 17.8.1)
debug rrm schedule (starting 17.8.1, debug NDP packet tx) show trace dot_11 channel enable
[*06/11/2020 09:45:38.9530] wcp/rrm_userspace_0/rrm_schedule :: RRMSchedule process_int_duration_timer_local rrm_is_msmt_schedule_local passive scan on channel 5 bandwidth 20MHz
[*06/11/2020 09:45:39.0550] noise measurement channel 5 noise 89
[*06/11/2020 09:45:43.5490] wcp/rrm_userspace_1/rrm_schedule :: RRMSchedule process_int_duration_timer_local rrm_is_msmt_schedule_local passive scan on channel 140 bandwidth 20MHz
[*06/11/2020 09:45:43.6570] noise measurement channel 140 noise 97
用戶端連線
可以使用最後一個事件時間戳列出已經由接入點取消驗證的客戶端:
LabAP#show dot11 clients deauth
timestamp mac vap reason_code
Mon Aug 20 09:50:59 2018 AC:BC:32:A4:2C:D3 9 4
Mon Aug 20 09:52:14 2018 00:AE:FA:78:36:89 9 4
Mon Aug 20 10:31:54 2018 00:AE:FA:78:36:89 9 4
在上一個輸出中,原因代碼是取消驗證原因代碼,如以下連結所詳述:
Vap是指AP中WLAN的識別碼(與WLC路由器上的WLAN ID不!!!)。
您可以將其與隨後詳細描述的其他輸出交叉關聯起來,這些輸出總是提到關聯客戶端的vap。
您可以看到具有「show controllers Dot11Radio 0/1 wlan」的VAP ID清單。
當客戶端仍然關聯時,您可以獲得有關其連線的詳細資訊:
LabAP#show dot11 clients
Total dot11 clients: 1
Client MAC Slot ID WLAN ID AID WLAN Name RSSI Maxrate WGB
00:AE:FA:78:36:89 1 10 1 TestSSID -25 MCS82SS No
有關客戶端條目的更多詳細資訊,可執行以下操作:
LabAP#show client summ
Radio Driver client Summary:
==============================
wifi0
[*08/20/2018 11:54:59.5340]
[*08/20/2018 11:54:59.5340] Total STA List Count 0
[*08/20/2018 11:54:59.5340] | NO| MAC|STATE|
[*08/20/2018 11:54:59.5340] -----------------------------
wifi1
[*08/20/2018 11:54:59.5357]
[*08/20/2018 11:54:59.5357] Total STA List Count 1
[*08/20/2018 11:54:59.5357] | NO| MAC|STATE|
[*08/20/2018 11:54:59.5357] -----------------------------
[*08/20/2018 11:54:59.5357] | 1| 0:ffffffae:fffffffa:78:36:ffffff89| 8|
Radio Driver Client AID List:
==============================
wifi0
[*08/20/2018 11:54:59.5415]
[*08/20/2018 11:54:59.5415] Total STA-ID List Count 0
[*08/20/2018 11:54:59.5415] | NO| MAC|STA-ID|
[*08/20/2018 11:54:59.5415] ------------------------------
wifi1
[*08/20/2018 11:54:59.5431]
[*08/20/2018 11:54:59.5431] Total STA-ID List Count 1
[*08/20/2018 11:54:59.5431] | NO| MAC|STA-ID|
[*08/20/2018 11:54:59.5432] ------------------------------
[*08/20/2018 11:54:59.5432] | 1| 0:ffffffae:fffffffa:78:36:ffffff89| 6|
WCP client Summary:
=====================
mac radio vap aid state encr Maxrate is_wgb_wired wgb_mac_addr
00:AE:FA:78:36:89 1 9 1 FWD AES_CCM128 MCS82SS false 00:00:00:00:00:00
NSS client Summary:
=====================
Current Count: 3
| MAC | OPAQUE |PRI POL|VLAN|BR|TN|QCF|BSS|RADID|MYMAC|
|F8:0B:CB:E4:7F:41|00000000| 3| 0| 1| 1| 0| 2| 3| 1|
|F8:0B:CB:E4:7F:40|00000000| 3| 0| 1| 1| 0| 2| 3| 1|
|00:AE:FA:78:36:89|00000003| 1| 0| 1| 1| 0| 9| 1| 0|
Datapath IPv4 client Summary:
===============================
id vap port node tunnel mac seen_ip hashed_ip sniff_ago confirm_ago
00:AE:FA:78:36:89 9 apr1v9 192.0.2.13 - 00:AE:FA:78:36:89 192.168.68.209 10.228.153.45 5.990000 5.980000
Datapath IPv6 client Summary:
===============================
client mac seen_ip6 age scope port
1 00:AE:FA:78:36:89 fe80::2ae:faff:fe78:3689 61 link-local apr1v9
Wired client Summary:
=======================
mac port state local_client detect_ago associated_ago tx_pkts tx_bytes rx_pkts rx_bytes
可以使用強制斷開特定客戶端的連線:
test dot11 client deauthenticate 可以使用以下命令為每個客戶端獲取流量計數器:
LabAP#show client statistics wireless 00:AE:FA:78:36:89 Client MAC address: 00:AE:FA:78:36:89 Tx Packets : 621 Tx Management Packets : 6 Tx Control Packets : 153 Tx Data Packets : 462 Tx Data Bytes : 145899 Tx Unicast Data Packets : 600 Rx Packets : 2910 Rx Management Packets : 13 Rx Control Packets : 943 Rx Data Packets : 1954 Rx Data Bytes : 145699 LabAP#
在無線電層面,很多資訊都可以在「show controllers」中獲得。 新增客戶端mac地址時,將顯示支援的資料速率、當前資料建立量、PHY功能以及重試次數和失敗次數:
LabAP#show controllers dot11Radio 0 client 00:AE:FA:78:36:89
mac radio vap aid state encr Maxrate is_wgb_wired wgb_mac_addr
00:AE:FA:78:36:89 0 9 1 FWD AES_CCM128 M15 false 00:00:00:00:00:00
Configured rates for client 00:AE:FA:78:36:89
Legacy Rates(Mbps): 11
HT Rates(MCS):M0 M1 M2 M3 M4 M5 M6 M7 M8 M9 M10 M11 M12 M13 M14 M15
VHT Rates: 1SS:M0-7 2SS:M0-7
HT:yes VHT:yes HE:no 40MHz:no 80MHz:no 80+80MHz:no 160MHz:no
11w:no MFP:no 11h:no encrypt_polocy: 4
_wmm_enabled:yes qos_capable:yes WME(11e):no WMM_MIXED_MODE:no
short_preamble:yes short_slot_time:no short_hdr:yes SM_dyn:yes
short_GI_20M:yes short_GI_40M:no short_GI_80M:yes LDPC:yes AMSDU:yes AMSDU_long:no
su_mimo_capable:yes mu_mimo_capable:no is_wgb_wired:no is_wgb:no
Additional info for client 00:AE:FA:78:36:89
RSSI: -90
PS : Legacy (Sleeping)
Tx Rate: 0 Kbps
Rx Rate: 117000 Kbps
VHT_TXMAP: 0
CCX Ver: 4
Statistics for client 00:AE:FA:78:36:89
mac intf TxData TxMgmt TxUC TxBytes TxFail TxDcrd TxCumRetries RxData RxMgmt RxBytes RxErr TxRt RxRt idle_counter stats_ago expiration
00:AE:FA:78:36:89 apr0v9 8 1 6 1038 1 0 0 31 1 1599 0 0 117000 290 13.952000 0
Per TID packet statistics for client 00:AE:FA:78:36:89
Priority Rx Pkts Tx Pkts Rx(last 5 s) Tx (last 5 s) QID Tx Drops Tx Cur Qlimit
0 899 460 1 1 144 0 0 1024
1 0 0 0 0 145 0 0 1024
2 0 0 0 0 146 0 0 1024
3 59 0 0 0 147 0 0 1024
4 0 0 0 0 148 0 0 1024
5 0 0 0 0 149 0 0 1024
6 0 0 0 0 150 0 0 1024
7 0 0 0 0 151 0 0 1024
Legacy Rate Statistics:
(Mbps : Rx, Tx, Tx-Retries)
11 Mbps : 2, 0, 0
6 Mbps : 0, 9, 0
HT/VHT Rate Statistics:
(Rate/SS/Width : Rx, Rx-Ampdu, Tx, Tx-Ampdu, Tx-Retries)
0/1/20 : 4, 4, 0, 0, 0
6/2/20 : 4, 4, 0, 0, 0
7/2/20 : 5, 5, 0, 0, 0
webauth done:
false
為了持續追蹤使用者端資料速率和/或RSSI值,您可以執行「debug dot11 client rate address <mac>」,此指令會每秒記錄一次此資訊:
LabAP#debug dot11 client rate address 00:AE:FA:78:36:89 [*08/20/2018 14:17:28.0928] MAC Tx-Pkts Rx-Pkts Tx-Rate Rx-Rate RSSI SNR Tx-Retries [*08/20/2018 14:17:28.0928] 00:AE:FA:78:36:89 0 0 12 a8.2-2s -45 53 0 [*08/20/2018 14:17:29.0931] 00:AE:FA:78:36:89 7 18 12 a8.2-2s -45 53 0 [*08/20/2018 14:17:30.0934] 00:AE:FA:78:36:89 3 18 12 a8.2-2s -45 53 0 [*08/20/2018 14:17:31.0937] 00:AE:FA:78:36:89 2 20 12 a8.2-2s -45 53 0 [*08/20/2018 14:17:32.0939] 00:AE:FA:78:36:89 2 20 12 a8.2-2s -45 53 0 [*08/20/2018 14:17:33.0942] 00:AE:FA:78:36:89 2 21 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:34.0988] 00:AE:FA:78:36:89 1 4 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:35.0990] 00:AE:FA:78:36:89 9 23 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:36.0993] 00:AE:FA:78:36:89 3 7 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:37.0996] 00:AE:FA:78:36:89 2 6 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:38.0999] 00:AE:FA:78:36:89 2 14 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:39.1002] 00:AE:FA:78:36:89 2 10 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:40.1004] 00:AE:FA:78:36:89 1 6 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:41.1007] 00:AE:FA:78:36:89 9 20 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:42.1010] 00:AE:FA:78:36:89 0 0 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:43.1013] 00:AE:FA:78:36:89 2 8 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:44.1015] 00:AE:FA:78:36:89 0 0 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:45.1018] 00:AE:FA:78:36:89 0 0 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:46.1021] 00:AE:FA:78:36:89 0 0 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:47.1024] 00:AE:FA:78:36:89 0 0 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:48.1026] 00:AE:FA:78:36:89 7 15 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:49.1029] 00:AE:FA:78:36:89 0 6 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:50.1032] 00:AE:FA:78:36:89 0 0 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:51.1035] 00:AE:FA:78:36:89 1 7 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:52.1037] 00:AE:FA:78:36:89 0 17 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:53.1040] 00:AE:FA:78:36:89 1 19 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:54.1043] 00:AE:FA:78:36:89 2 17 12 a8.2-2s -46 52 0 [*08/20/2018 14:17:55.1046] 00:AE:FA:78:36:89 2 22 12 a8.2-2s -45 53 0 [*08/20/2018 14:17:56.1048] 00:AE:FA:78:36:89 1 18 12 a8.2-2s -45 53 0 [*08/20/2018 14:17:57.1053] 00:AE:FA:78:36:89 2 18 12 a8.2-2s -45 53 0 [*08/20/2018 14:17:58.1055] 00:AE:FA:78:36:89 12 37 12 a8.2-2s -45 53 0
在此輸出中,Tx和Rx封包計數器是自上次列印後第二個間隔內傳輸之封包,與Tx重試相同。但是,RSSI、SNR和資料速率是該間隔的最後一個資料包的值(而不是該間隔中所有資料包的平均值)。
Flexconnect方案
在身份驗證前(例如CWA)或身份驗證後情況下,您可以驗證當前應用於客戶端的ACL:
AP#show client access-lists pre-auth all f48c.507a.b9ad Pre-Auth URL ACLs for Client: F4:8C:50:7A:B9:AD IPv4 ACL: IPv6 ACL: ACTION URL-LIST Resolved IPs for Client: F4:8C:50:7A:B9:AD HIT-COUNT URL ACTION IP-LIST REDIRECT rule 0: allow true and ip proto 17 and src port 53 rule 1: allow true and ip proto 17 and dst port 53 rule 2: allow true and src 10.48.39.161mask 255.255.255.255 rule 3: allow true and dst 10.48.39.161mask 255.255.255.255 rule 4: deny true No IPv6 ACL found AP#show client access-lists post-auth all f48c.507a.b9ad Post-Auth URL ACLs for Client: F4:8C:50:7A:B9:AD IPv4 ACL: IPv6 ACL: ACTION URL-LIST Resolved IPs for Client: F4:8C:50:7A:B9:AD HIT-COUNT URL ACTION IP-LIST post-auth rule 0: deny true and dst 192.0.0.0mask 255.0.0.0 rule 1: deny true and src 192.0.0.0mask 255.0.0.0 rule 2: allow true No IPv6 ACL found
您可以通過啟用debug flexconnect access-list counter client <client MAC>
後續執行show client access-list pre-auth/post-auth all <MAC>,然後為每個ACL專案新增命中計數器。這適用於自Cisco IOS® XE 17.13起的所有型別的flex ACL。在早期版本中,存在相同的命令,但只有VLAN ACL的命中計數器已更新。
您可以使用clear counters access-list client <mac>
AP檔案系統
COS AP不允許在unix平台上列出檔案系統的所有內容。
命令「show filesystems」提供當前分割槽上空間使用情況和分佈的詳細資訊:
2802#show filesystems Filesystem Size Used Available Use% Mounted on /dev/ubivol/storage 57.5M 364.0K 54.1M 1% /storage 2802#
命令「show flash」列出AP快閃記憶體上的主檔案。您還可以附加syslog或core關鍵字以列出這些特定資料夾。
ap_2802#show flash Directory of /storage/ total 84 -rw-r--r-- 1 root root 0 May 21 2018 1111 -rw-r--r-- 1 root root 6 Apr 15 11:09 BOOT_COUNT -rw-r--r-- 1 root root 6 Apr 15 11:09 BOOT_COUNT.reserve -rw-r--r-- 1 root root 29 Apr 15 11:09 RELOADED_AT_UTC drwxr-xr-x 2 root root 160 Mar 27 13:53 ap-images drwxr-xr-x 4 5 root 2016 Apr 15 11:10 application -rw-r--r-- 1 root root 6383 Apr 26 09:32 base_capwap_cfg_info -rw-r--r-- 1 root root 20 Apr 26 10:31 bigacl -rw-r--r-- 1 root root 1230 Mar 27 13:53 bootloader.log -rw-r--r-- 1 root root 5 Apr 26 09:29 bootloader_verify.shadow -rw-r--r-- 1 root root 18 Jun 30 2017 config -rw-r--r-- 1 root root 8116 Apr 26 09:32 config.flex -rw-r--r-- 1 root root 21 Apr 26 09:32 config.flex.mgroup -rw-r--r-- 1 root root 0 Apr 15 11:09 config.local -rw-r--r-- 1 root root 0 Jul 26 2018 config.mesh.dhcp -rw-r--r-- 1 root root 180 Apr 15 11:10 config.mobexp -rw-r--r-- 1 root root 0 Jun 5 2018 config.oeap -rw-r--r-- 1 root root 2253 Apr 26 09:43 config.wireless drwxr-xr-x 2 root root 160 Jun 30 2017 cores drwxr-xr-x 2 root root 320 Jun 30 2017 dropbear drwxr-xr-x 2 root root 160 Jun 30 2017 images -rw-r--r-- 1 root root 222 Jan 2 2000 last_good_uplink_config drwxr-xr-x 2 root root 160 Jun 30 2017 lists -rw-r--r-- 1 root root 215 Apr 16 11:01 part1_info.ver -rw-r--r-- 1 root root 215 Apr 26 09:29 part2_info.ver -rw-r--r-- 1 root root 4096 Apr 26 09:36 random_seed -rw-r--r-- 1 root root 3 Jun 30 2017 rxtx_mode -rw-r--r-- 1 root root 64 Apr 15 11:11 sensord_CSPRNG0 -rw-r--r-- 1 root root 64 Apr 15 11:11 sensord_CSPRNG1 drwxr-xr-x 3 support root 224 Jun 30 2017 support drwxr-xr-x 2 root root 2176 Apr 15 11:10 syslogs --------------------------------------------------------------------------- Filesystem Size Used Available Use% Mounted on flash 57.5M 372.0K 54.1M 1% /storage
儲存和傳送系統日誌
syslog資料夾儲存先前重新啟動的syslog輸出。命令「show log」只會顯示自上次重新啟動以來的系統日誌。
在每次重新啟動時,系統日誌都會寫入增量檔案。
artaki# show flash syslogs Directory of /storage/syslogs/ total 128 -rw-r--r-- 1 root root 11963 Jul 6 15:23 1 -rw-r--r-- 1 root root 20406 Jan 1 2000 1.0 -rw-r--r-- 1 root root 313 Jul 6 15:23 1.last_write -rw-r--r-- 1 root root 20364 Jan 1 2000 1.start -rw-r--r-- 1 root root 33 Jul 6 15:23 1.watchdog_status -rw-r--r-- 1 root root 19788 Jul 6 16:46 2 -rw-r--r-- 1 root root 20481 Jul 6 15:23 2.0 -rw-r--r-- 1 root root 313 Jul 6 16:46 2.last_write -rw-r--r-- 1 root root 20422 Jul 6 15:23 2.start --------------------------------------------------------------------------- Filesystem Size Used Available Use% Mounted on flash 57.6M 88.0K 54.5M 0% /storage artaki# show flash cores Directory of /storage/cores/ total 0 --------------------------------------------------------------------------- Filesystem Size Used Available Use% Mounted on flash 57.6M 88.0K 54.5M 0% /storage
初始引導後的第一個輸出是檔案1.0,如果1.0過長,則會建立檔案1.1。重新開機後,系統會建立一個新檔案2.0,以此類推。
如果您希望AP將其系統日誌消息單播傳送到特定伺服器,可以從WLC配置系統日誌目標。
預設情況下,AP將其syslog傳送到可能導致相當多的廣播風暴的廣播地址,因此請確保配置syslog伺服器。
預設情況下,AP通過系統日誌傳送其控制檯輸出上的任何列印內容。
在9800控制器上,您可以在「管理」下的「配置 — > AP加入」配置檔案中更改這些引數。
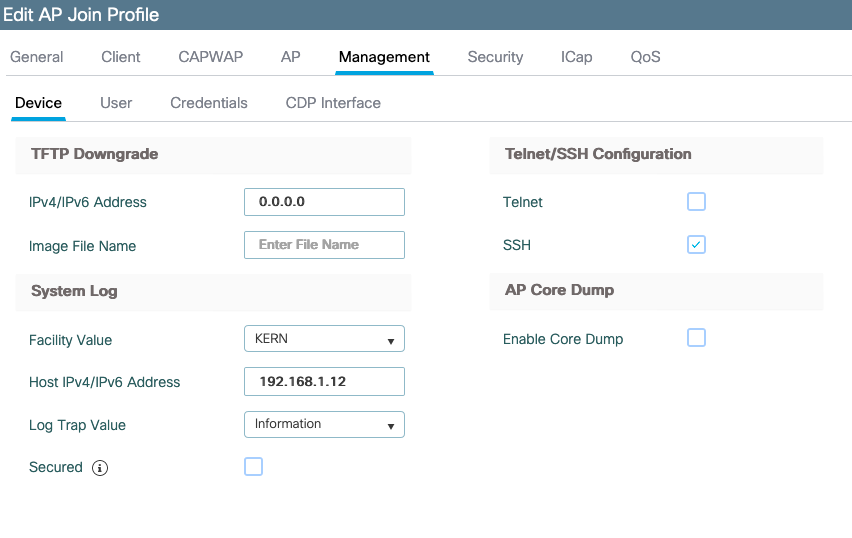
您可以將Log Trap Value 更改為也通過系統日誌傳送調試。然後,您可以在AP CLI上啟用調試,這些調試的輸出通過系統日誌消息傳送到已配置的伺服器。
由於Cisco錯誤ID CSCvu75017  ,只有當您將syslog設施設定為KERN(預設值)時,AP才會傳送系統日誌消息。
,只有當您將syslog設施設定為KERN(預設值)時,AP才會傳送系統日誌消息。
如果您正在排除AP可能失去網路連線(例如,在WGB上)的問題,則系統日誌不如在AP失去上行鏈路連線時傳送消息那麼可靠。
因此,依靠快閃記憶體中儲存的系統日誌檔案是調試和將輸出儲存在AP本身上,然後在以後定期上載的絕佳方法。
AP支援套件
可從接入點上傳的單個捆綁包中提供一些通常收集的各種型別的診斷資訊。
可以包括在捆綁包中的診斷資訊包括:
- AP show tech
- AP系統日誌
- AP Capwapd大腦日誌
- AP啟動和消息日誌
- AP核心轉儲檔案
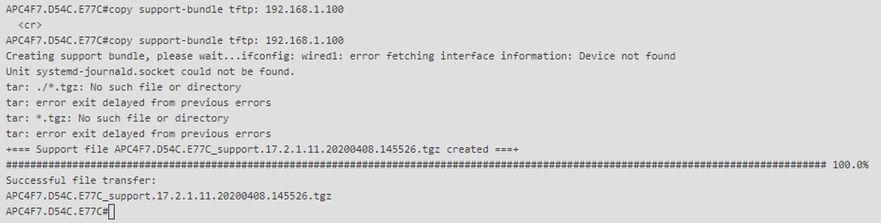
要獲取AP支援捆綁包,您可以進入AP CLI並輸入命令「copy support-bundle tftp:x.x.x.x」。
在此之後,您可以檢查名為AP名稱且附加了support.apversion.date.time.tgz的檔案,如下所示:
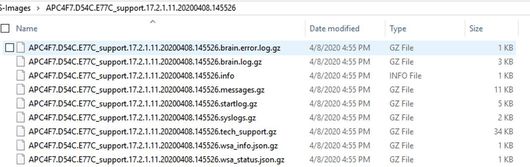
當您「解壓縮」檔案時,可以檢視收集的各種檔案:
遠端收集AP核心檔案
要遠端收集AP核心檔案,請啟用要包括在支援捆綁包中的核心轉儲,然後從AP上傳支援捆綁包,或直接傳送到tftp伺服器。後續示例使用tftp server 192.168.1.100。
AireOS CLI
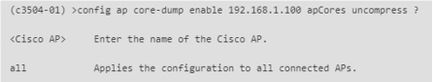
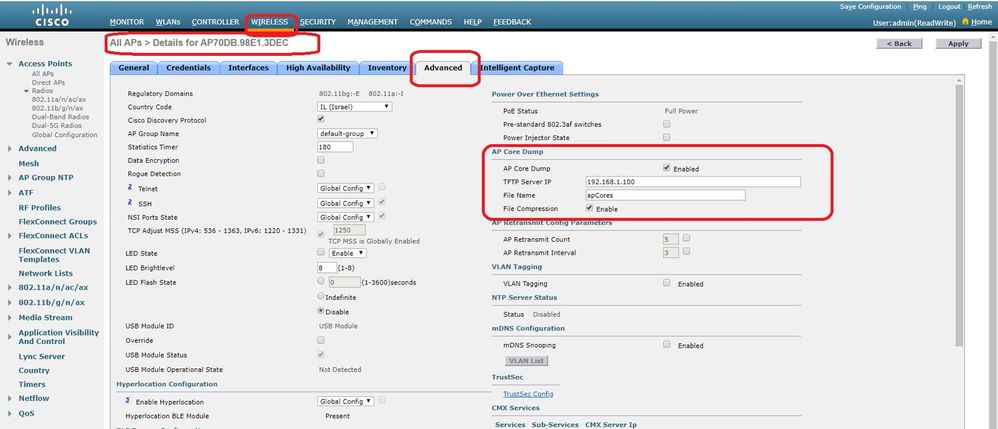
AireOS GUI
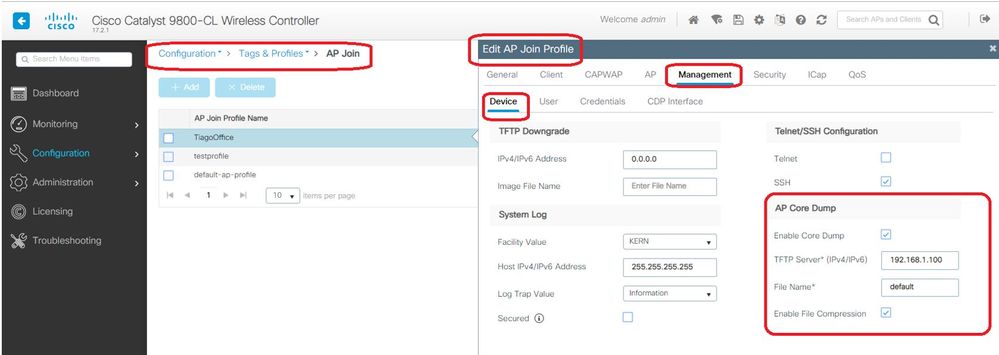
Cisco IOS® CLI
eWLC-9800-01(config)#ap profile TiagoOffice
eWLC-9800-01(config-ap-profile)#core-dump tftp-server 192.168.1.100 file apCores uncompress
Cisco IOS® GUI
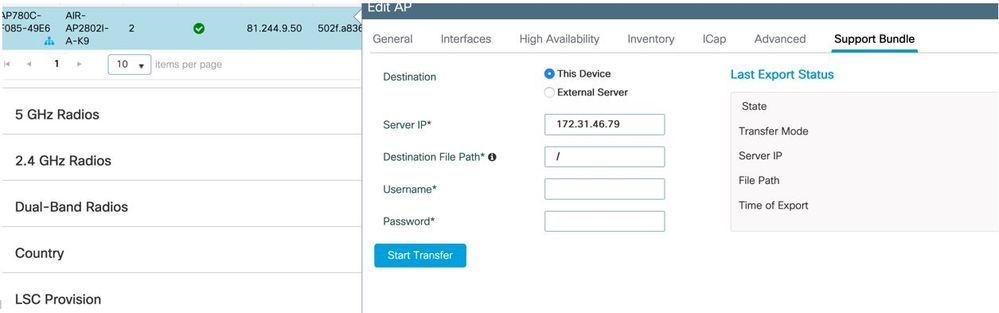
從Cisco IOS® XE 17.3.1開始,您就有一個「支援捆綁包」頁籤,可以從WLC GUI下載AP SB。
它所做的只是在AP上執行「copy support-bundle」命令,並透過SCP傳送到WLC(因為WLC可以是SCP伺服器)。
然後,您可以從瀏覽器下載:
這表示您可以在17.3.1之前的eWLC版本中手動執行相同的方法:
如果您沒有可連線到AP的TFTP伺服器,請透過SCP將支援套件組合從AP複製到eWLC IP。
eWLC通常可以從AP通過SSH訪問,因此對於17.3之前版本來說這是一個很好的技巧。
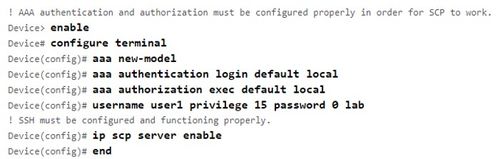
步驟2. 在Cisco IOS® XE v17.2.1上啟用SCP
此示例說明如何配置SCP的伺服器端功能。此示例使用本地定義的使用者名稱和密碼:
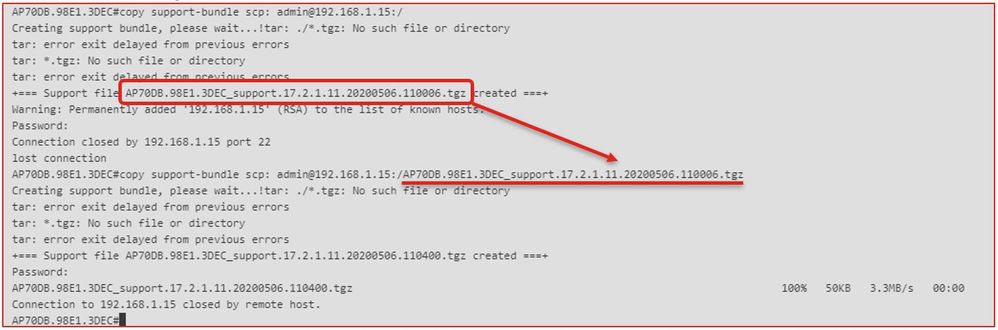
步驟3.使用命令「copy support-bundle」,我們需要指定在SCP伺服器中建立的檔名。
提示:您可以運行一次命令來獲得一個有意義的檔名,然後在命令中複製/貼上該檔名:
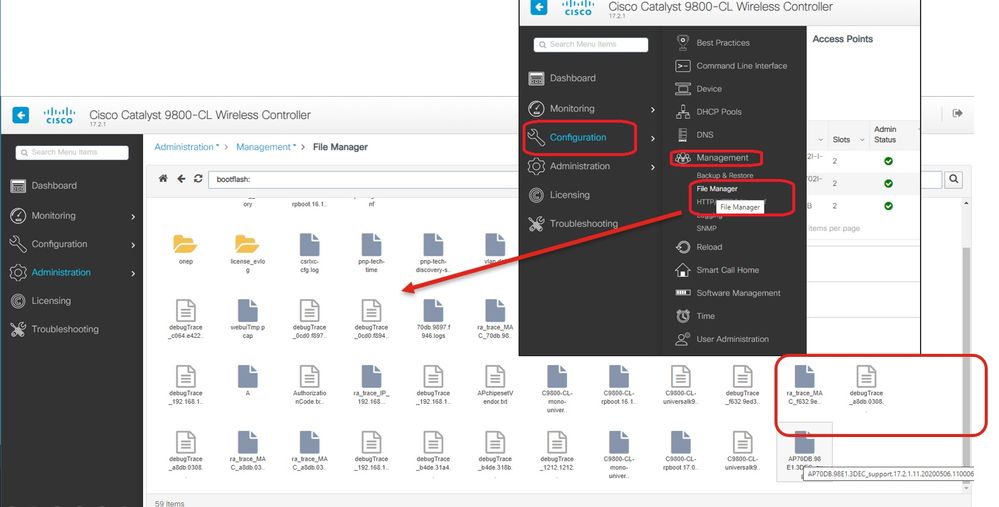
步驟4.然後您可以進入eWLC GUI並在以下位置取得檔案:管理>管理>檔案管理器:
物聯網和藍芽
可以在AP上使用檢查gRPC伺服器日誌:
AP# show grpc server log
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] spaces conn url 10.22.243.33:8000"
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] entering stopDNAspacesTmpTokenRoutine"
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] exiting stopDNAspacesTmpTokenRoutine"
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] entering startDNAspacesTmpTokenRoutine"
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] launching token request cycle"
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] exiting startDNAspacesTmpTokenRoutine"
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] spaces token expiration time 2020-04-02 01:36:52 +0000 UTC"
time="2020-04-01T01:36:52Z" level=info msg=" Calling startDNASpacesConn routine "
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] Receive Success status"
time="2020-04-01T01:36:52Z" level=info msg="[DNAS] Connection not in ready state sleeping for 10 seconds"
time="2020-04-01T01:37:02Z" level=info msg="[DNAS] Setup Stream for the gRPC connection"
time="2020-04-01T01:37:02Z" level=info msg="[DNAS] Connect RPC Succeeded."
time="2020-04-01T01:37:02Z" level=info msg="[DNAS] RX routine got enabled "
time="2020-04-01T01:37:02Z" level=info msg="[DNAS] TX routine got enabled "
可以使用驗證與Cisco DNA Spaces聯結器的連線:
AP# show cloud connector key access
Token Valid : Yes
Token Stats :
Number of Attempts : 44
Number of Failures : 27
Last Failure on : 2020-03-28 02:02:15.649556818 +0000 UTC m=+5753.097022576
Last Failure reason : curl: SSL connect error
Last Success on : 2020-04-01 00:48:37.313511596 +0000 UTC m=+346934.760976625
Expiration time : 2020-04-02 00:48:37 +0000 UTC
Connection Retry Interval : 30
AP# show cloud connector connection detail
Connection State : READY
Connection Url : 10.22.243.33:8000
Certificate Available : true
Controller Ip : 10.22.243.31
Stream Setup Interval : 30
Keepalive Interval : 30
Last Keepalive Rcvd On : 2020-04-01 00:32:47.891433113 +0000 UTC m=+345985.338898246
Number of Dials : 2
Number of Tx Pkts : 2788175
Number of Rx Pkts : 11341
Number of Dropped Pkts : 0
Number of Rx Keepalive : 11341
Number of Tx Keepalive : 11341
Number of Rx Cfg Request : 0
Number of Tx AP Cfg Resp : 0
Number of Tx APP Cfg Resp : 0
Number of Tx APP state pkts : 5
Number of Tx APP data pkts : 2776829
要檢視AP的當前BLE廣播配置:
AP# show controllers ioTRadio ble 0 broadcast
BLE Profile Config
-------------------
Active profile : v-iBeacon
Profile 0 (iBeacon)
UUID : 00001000000000000000000000000000
Interval (ms) : 100
Power (dBm) : -21
Advertised Power (dBm) : -65
Minor : 0
Major : 0
TxPower byte : bfbfbfbfbfbfbfbfbfbfbfbfbf
Profile 1 (Eddystone UID)
Namespace (hex) : 0000000000005446089c
Instance-ID (hex) : 7f0000001f00
Profile 2 (Eddystone URL)
URL : http://www.
要檢視掃描結果,請執行以下操作:
AP# show controllers ioTRadio ble 0 scan brief
Profile MAC RSSI(-dBm) RSSI@1meter(-dBm) Last-heard
Unknown 3C:1D:AF:62:EC:EC 88 0 0000D:00H:00M:01S
iBeacon 18:04:ED:04:1C:5F 86 65 0000D:00H:00M:01S
Unknown 18:04:ED:04:1C:5F 78 65 0000D:00H:00M:01S
Unknown 04:45:E5:28:8E:E7 85 65 0000D:00H:00M:01S
Unknown 2D:97:FA:0F:92:9A 91 65 0000D:00H:00M:01S
iBeacon E0:7D:EA:16:35:35 68 65 0000D:00H:00M:01S
Unknown E0:7D:EA:16:35:35 68 65 0000D:00H:00M:01S
iBeacon 04:EE:03:53:74:22 45 256 0000D:00H:00M:01S
Unknown 04:EE:03:53:74:22 45 256 0000D:00H:00M:01S
04:EE:03:53:6A:3A 72 N/A 0000D:00H:00M:01S
Unknown 04:EE:03:53:6A:3A 72 65 0000D:00H:00M:01S
iBeacon E0:7D:EA:16:35:35 68 65 0000D:00H:00M:01S
Unknown E0:7D:EA:16:35:35 67 65 0000D:00H:00M:01S
iBeacon 04:EE:03:53:74:22 60 256 0000D:00H:00M:01S
Unknown 04:EE:03:53:74:22 60 256 0000D:00H:00M:01S
Eddystone URL 04:EE:03:53:6A:3A 72 N/A 0000D:00H:00M:01S
當AP在部署應用的「高級BLE網關」模式下工作時,您可以使用檢查IoX應用的狀態:
AP#show iox applications
Total Number of Apps : 1
--------------------------
App Name : cisco_dnas_ble_iox_app
App Ip : 192.168.11.2
App State : RUNNING
App Token : 02fb3e98-ac02-4356-95ba-c43e8a1f4217
App Protocol : ble
App Grpc Connection : Up
Rx Pkts From App : 3878345
Tx Pkts To App : 6460
Tx Pkts To Wlc : 0
Tx Data Pkts To DNASpaces : 3866864
Tx Cfg Resp To DNASpaces : 1
Rx KeepAlive from App : 11480
Dropped Pkts : 0
App keepAlive Received On : Mar 24 05:56:49
您可以使用這些命令連線到IOX應用程式,然後在樓層信標配置期間監控日誌:
AP#connect iox application
/ #
/# tail -F /tmp/dnas_ble.log
Tue Mar 24 06:55:21 2020 [INFO]: Starting DNA Spaces BLE IOx Application
Tue Mar 24 06:55:21 2020 [INFO]: Auth token file contents: db26a8ab-e800-4fe9-a128-80683ea17b12
Tue Mar 24 06:55:21 2020 [INFO]: Setting gRPC endpoint to: 1.1.7.101:57777
Tue Mar 24 06:55:21 2020 [INFO]: Auth with token: db26a8ab-e800-4fe9-a128-80683ea17b12
Tue Mar 24 06:55:21 2020 [INFO]: Attempt to connect to DNAS Channel
Tue Mar 24 06:55:21 2020 [INFO]: Starting to run metrics
Tue Mar 24 06:55:21 2020 [INFO]: Starting to run Channel Keepalive
Tue Mar 24 06:55:21 2020 [INFO]: Initialize DNAS Reader Channel
Tue Mar 24 06:55:21 2020 [INFO]: Start listener for messages
Tue Mar 24 06:55:21 2020 [INFO]: Running BLE scan thread
結論
有許多故障排除工具可以幫助我們解決與COS AP相關的問題。
本文列出最常用的專案並定期更新。
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
6.0 |
04-Sep-2024 |
已新增客戶端調試捆綁包 |
5.0 |
19-Aug-2024 |
重新認證 |
3.0 |
17-Nov-2021 |
已新增IoT部分 |
2.0 |
12-Nov-2021 |
新增了引導時間調試部分 |
1.0 |
21-Jun-2019 |
初始版本 |
由思科工程師貢獻
- Nicolas DarchisCisco TAC Engineer
- Tiago AntunesCisco TAC Engineer
 意見
意見