瞭解AnyConnect NAM和ISE上的EAP-FAST和連結實施
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
目錄
簡介
本文檔介紹有關在Cisco AnyConnect網路訪問管理器(NAM)和身份服務引擎(ISE)上實施EAP-FAST的詳細資訊。
必要條件
需求
思科建議您瞭解以下主題:
- EAP架構和EAP-FAST方法的基本知識
- 身份服務引擎(ISE)的基本知識
- AnyConnect NAM和配置檔案編輯器基礎知識
- 適用於802.1x服務的Cisco Catalyst配置基礎知識
採用元件
本檔案中的資訊是根據以下軟體版本:
- 帶Cisco AnyConnect安全移動客戶端的Windows 7版本3.1和4.0
- Cisco Catalyst 3750X交換機,帶軟體15.2.1及更高版本
- Cisco ISE版本1.4
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
理論
階段
EAP-FAST是一種靈活的EAP方法,允許請求方和伺服器的相互身份驗證。它與EAP-PEAP類似,但通常不需要使用使用者端或甚至伺服器憑證。EAP-FAST的優點之一就是能夠鏈結多個驗證(使用多個內部方法),並以密碼方式將其繫結在一起(EAP鏈結)。思科實施將使用此功能進行使用者和電腦身份驗證。
EAP-FAST利用受保護的存取身分證明(PAC)來快速建立TLS通道(作業階段恢復)或授權使用者/機器(跳過驗證的內部方法)。
EAP-FAST有三個階段:
- 第0階段(PAC調配)
- 第1階段(建立TLS隧道)
- 第2階段(身份驗證)
EAP-FAST支援無PAC和基於PAC的通話。PAC架構包含PAC規範與PAC架構驗證。PAC規範可以基於匿名或驗證的TLS會話。
PAC
PAC是由伺服器產生並提供給使用者端的「受保護的存取身份證明」。它包括:
- PAC金鑰(隨機金鑰值,用於派生TLS主金鑰和會話金鑰)
- PAC不透明(PAC金鑰+使用者身分辨識-全部由EAP-FAST伺服器主金鑰加密)
- PAC資訊(伺服器辨識、TTL計時器)
發出PAC的伺服器會使用EAP-FAST伺服器主金鑰(即PAC不透明)加密PAC金鑰和辨識,並將整個PAC傳送給使用者端。它不會儲存/儲存任何其他資訊(除了所有PAC均使用相同的主金鑰)。
收到PAC不透明後,會使用EAP-FAST伺服器主金鑰解密並驗證。PAC金鑰用於派生縮寫TLS隧道的TLS主金鑰和會話金鑰。
新的EAP-FAST伺服器主金鑰會在上一個主金鑰過期時產生。 在某些情況下,可以撤銷主金鑰。
目前使用幾種型別的PAC:
- 通道PAC:用於TLS通道建立(不需要使用者端或伺服器憑證)。在TLS客戶端Hello中傳送
- 機器PAC:用於TLS通道建立和立即機器授權。在TLS客戶端Hello中傳送
- 使用者授權PAC:用於立即使用者身份驗證(跳過內部方法)(如果伺服器允許)。使用TLV在TLS隧道內傳送。
- 電腦授權PAC:用於立即電腦身份驗證(跳過內部方法)(如果伺服器允許)。使用TLV在TLS隧道內傳送。
- Trustsec PAC:用於執行環境或策略刷新時的授權。
所有這些PAC通常在階段0自動遞送。某些PAC(隧道、電腦、Trustsec)也可以手動傳送。
生成PAC時
- 隧道PAC:在成功進行身份驗證(內部方法)後調配(如果之前未使用)。
- 授權PAC:如果之前未使用過,則在身份驗證成功後調配(內部方法)。
- 機器PAC:在機器驗證成功後(內部方法)調配(如果以前未使用過,並且未使用授權PAC)。當隧道PAC到期時調配;但是,當授權PAC到期時不調配。當啟用或停用EAP鏈結時,會調配它。
附註:
每個PAC規範都需要成功的驗證,但使用案例除外:授權的使用者會為沒有AD帳戶的機器要求Machine PAC。
此表格總結列出啟動設定和主動式更新功能:
| PAC型別 |
通道v1/v1a/CTS |
機器 |
Authorization |
| 根據請求提供PAC |
是 |
僅在經過身份驗證的調配上 |
僅在經過身份驗證的調配上且如果也請求隧道PAC |
| 在身份驗證請求時提供PAC |
是 |
是 |
僅當此身份驗證中未使用它時 |
| 主動更新 |
是 |
否 |
否 |
| 在基於PAC的身份驗證失敗後回退到PAC調配時(例如,當PAC過期時) |
拒絕且不提供新專案 |
拒絕且不提供新專案 |
拒絕且不提供新專案 |
| 支援ACS 4.x PAC |
適用於通道PAC v1/v1a |
是 |
否 |
EAP-FAST伺服器主金鑰ACS 4.x與ACS 5x和ISE
比較ACS 4.x和ISE時,Master金鑰處理略有不同
| ACS 5.x/ISE |
||
| PAC更新是由伺服器在第一次成功驗證後傳送,驗證是在PAC到期之前的特定可設定時間週期內執行。 |
換句話說,ISE保留所有舊主金鑰,預設情況下每週生成一次新主金鑰。由於主金鑰無法過期,因此僅驗證PAC TTL。
透過管理->設定->協定-> EAP-FAST -> EAP-FAST設定配置ISE主金鑰生成期。
會話恢復
這是允許使用隧道PAC的一個重要元件。它允許TLS隧道重新協商,而不使用證書。
EAP-FAST有兩種作業階段恢復型別:以伺服器狀態為基礎和無狀態(以PAC為基礎)。
伺服器狀態
基於標準TLS的方法基於伺服器上快取的TLS SessionID。傳送TLS使用者端Hello的使用者端會附加階段作業ID,以便繼續階段作業。當使用匿名TLS隧道時,會話僅用於PAC調配:
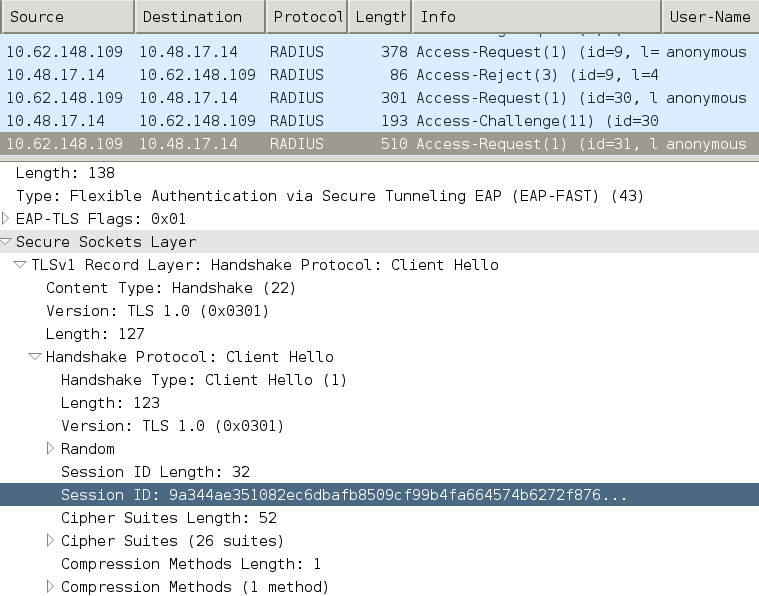
無狀態(基於PAC)
使用者/電腦授權PAC用於儲存對等體的以前身份驗證和授權狀態。
客戶端恢復基於RFC 4507。伺服器不需要快取任何資料,而是使用者端在TLS使用者端Hello SessionTicket延伸中附加PAC。反過來,伺服器會驗證PAC。 基於傳送到伺服器的隧道PAC的示例:
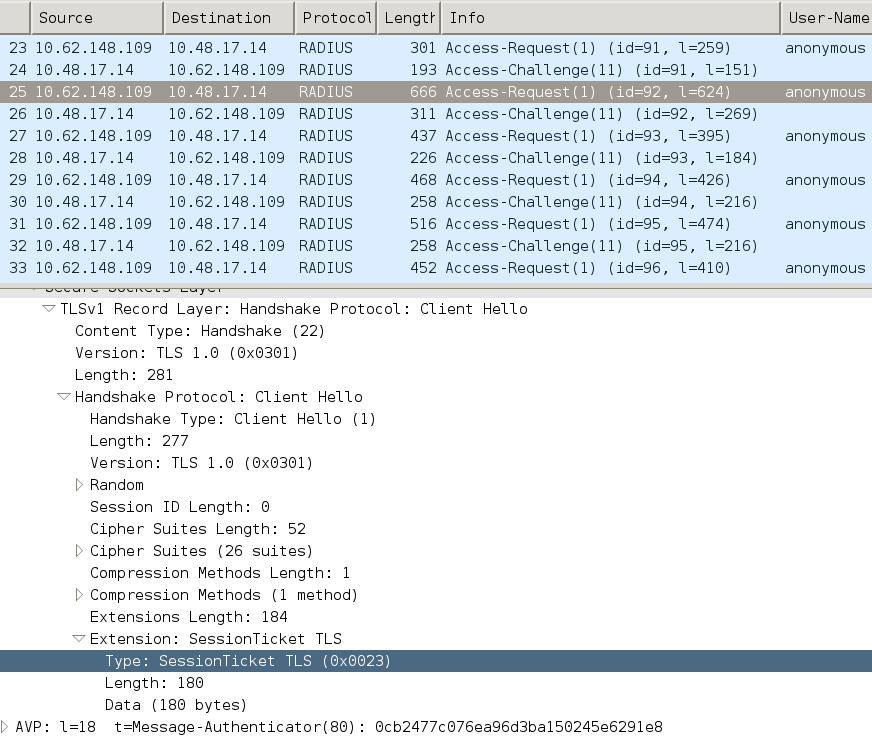
AnyConnect NAM實施
它透過快速重新連線在客戶端(AnyConnect NAM)上啟用,但僅用於控制授權PAC的使用。
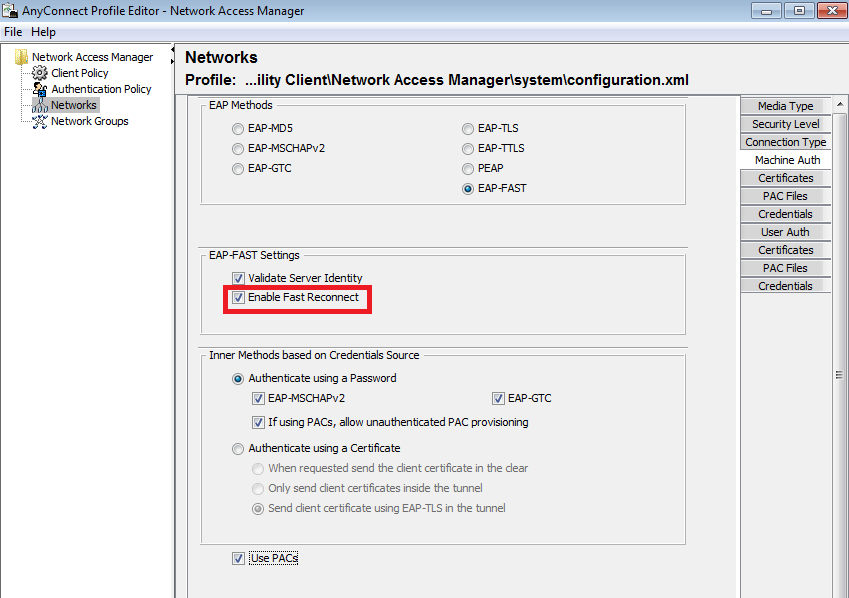
在停用設定的情況下,NAM仍使用隧道PAC來構建TLS隧道(不需要證書)。但是,這不會使用授權PAC來執行即時使用者和機器授權。因此,內部方法的階段2始終是必需的。
ISE提供啟用無狀態會話恢復的選項。與NAM一樣,它僅用於授權PAC。隧道PAC的使用由「使用PAC」選項控制。
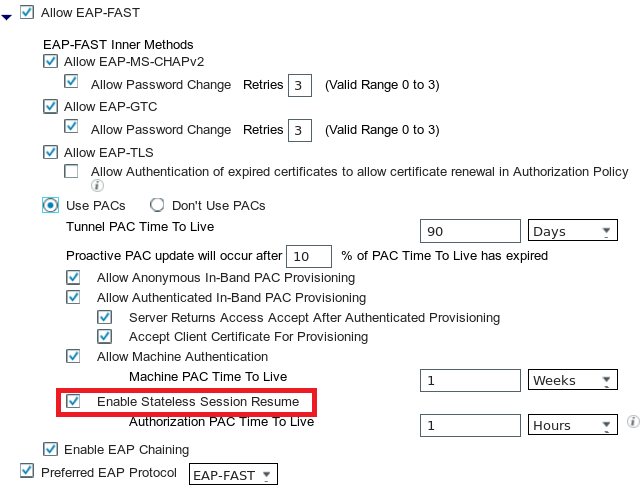
如果啟用此選項,NAM會嘗試使用PAC。如果在ISE中配置了「不使用PAC」,並且ISE在TLS擴展中收到隧道PAC,則會報告「插入此處」錯誤並返回EAP故障:
在此插入
在ISE中,還需要啟用基於TLS會話ID的會話恢復(從全局EAP-FAST設定)。預設情況下它處於停用狀態:
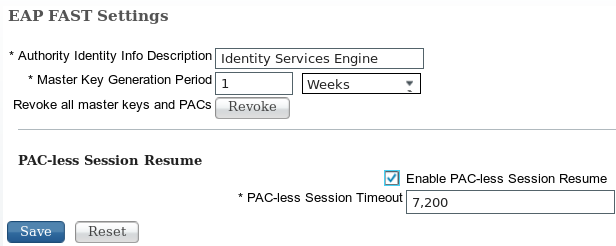
請記住,只能使用一種型別的會話恢復。基於SessionID的部署僅用於無PAC部署,基於RFC 4507的部署僅用於PAC部署。
PAC規範(第0階段)
PAC可以在階段0中自動調配。第0階段包括:
- TLS隧道建立
- 驗證(內部方法)
PAC在TLS隧道內透過PAC TLV(和PAC TLV確認)成功進行身份驗證後交付
匿名TLS隧道
對於沒有PKI基礎設施的部署,可以使用匿名TLS隧道。匿名TLS隧道使用Diffie Hellman密碼套件構建-不需要伺服器或客戶端證書。此方法容易受到「中間人」攻擊(模擬)。
要使用此選項,NAM需要此配置選項:
如果使用PAC允許未經驗證的PAC規範」(這僅適用於基於密碼的內部方法,因為沒有PKI基礎設施,無法使用基於證書的內部方法)。
此外,ISE需要在Authentication Allowed Protocols下配置「Allow Anonymous In-band PAC Provisioning」。
在TrustSec NDAC部署中使用匿名帶內PAC規範(網路裝置之間協商的EAP-FAST會話)。
驗證的TLS通道
這是最安全、最推薦的選項。TLS隧道基於請求方驗證的伺服器證書構建。這只需要伺服器端的PKI基礎設施,ISE需要該基礎設施(在NAM上,可以停用選項「驗證伺服器身份」。
對於ISE,有兩個額外的選項:

通常,在PAC調配後,會傳送Access-Reject命令,強制請求方使用PAC重新進行身份驗證。但是,由於PAC是透過身份驗證在TLS隧道中傳遞的,因此可以縮短整個過程,並在PAC調配後立即返回Access-Accept。
第二個選項基於客戶端證書構建TLS隧道(這需要在終端上部署PKI)。這允許TLS通道建立時採用相互驗證,這會略過內部方法,直接進入PAC提供階段。此處必須小心-有時請求者提供的憑證不受ISE信任(用於其他目的),而且作業階段失敗。
EAP鏈結
允許在一個RADIUS/EAP會話中進行使用者和電腦身份驗證。多個EAP方法可以連結在一起。在第一次身份驗證成功完成後(通常是電腦),伺服器會傳送一個指示成功的中間結果TLV(在TLS隧道內)。該TLV必須伴有加密繫結TLV請求。Cryptobinding用於證明伺服器和對等體都參與了特定的身份驗證序列。Cryptobinding方法使用來自階段1和階段2的金鑰材料。此外,還附加了一個TLV:EAP-Payload -正在啟動新會話(通常為使用者啟動)。一旦RADIUS伺服器(ISE)收到加密繫結TLV響應並驗證它,日誌中將顯示此消息,然後嘗試下一個EAP方法(通常用於使用者身份驗證):
12126 EAP-FAST cryptobinding verification passed
如果加密繫結驗證失敗,則整個EAP會話都將失敗。如果其中一個身份驗證失敗,則它仍然正常-因此,ISE允許管理員根據授權條件NetworkAccess:EapChainingResult配置多個連結結果:
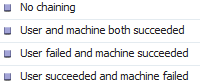
啟用EAP-FAST使用者與機器驗證時,NAM上會自動啟用EAP-Chaining。
必須在ISE中配置EAP連結。
PAC檔案的儲存位置
預設情況下,隧道和電腦PAC儲存在<credential>部分的C:\ProgramData\Cisco\Cisco AnyConnect安全移動客戶端\網路訪問管理器\system\internalConfiguration.xml中。那些以加密形式儲存。
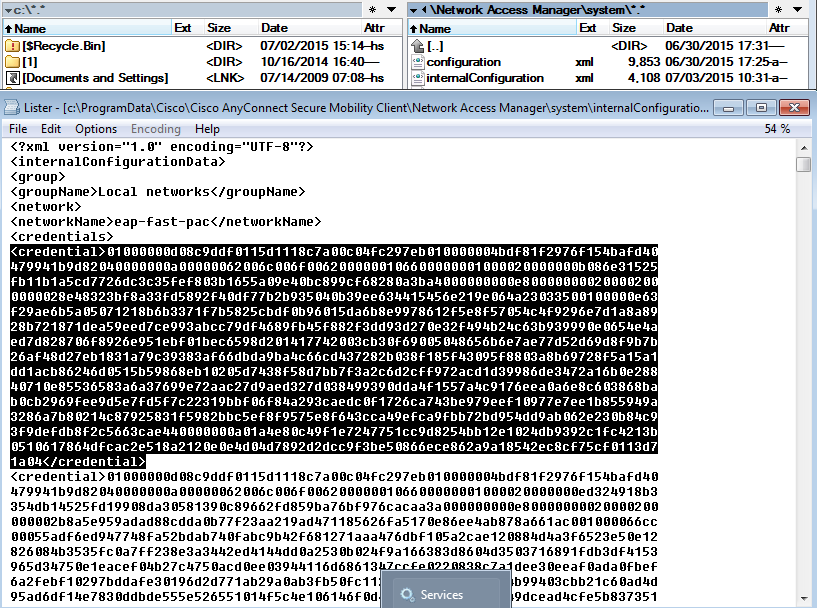
授權PAC僅儲存在記憶體中,且會在重新開機或NAM服務重新啟動後移除。
需要重新啟動服務才能刪除隧道或電腦PAC。
AnyConnect NAM 3.1與4.0
AnyConnect 3.x NAM配置檔案編輯器允許管理員手動配置PAC。此功能已從AnyConnect 4.x NAM配置檔案編輯器中刪除。
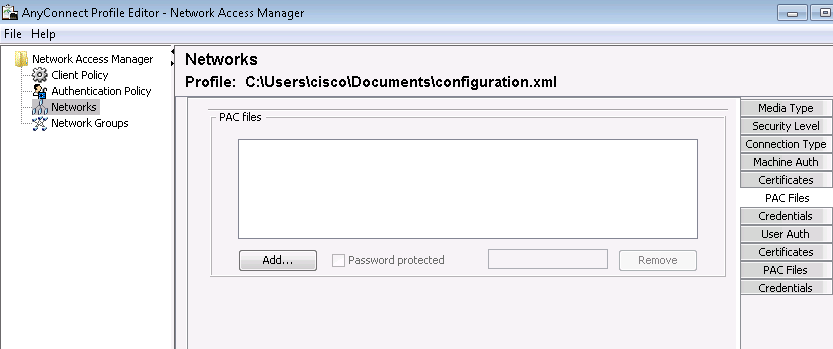
刪除此功能的決定基於思科漏洞ID CSCuf31422和思科漏洞ID CSCua13140(僅限註冊使用者)。
範例
網路圖表
所有示例都使用此網路拓撲進行了測試。使用無線時同樣適用。
EAP-Fast,不含EAP鏈結與使用者及機器PAC
預設情況下,EAP_chaining在ISE上停用。但是,所有其他選項均已啟用,包括電腦和授權PAC。請求方已具有有效的電腦和隧道PAC。在此流程中,ISE上存在兩個單獨的身份驗證-一個用於電腦,一個用於使用者-具有單獨的日誌。ISE記錄的主要步驟。第一次驗證(電腦):
- 請求方透過電腦PAC傳送TLS客戶端Hello。
- 伺服器驗證電腦PAC並構建TLS隧道(不使用證書)。
- 伺服器驗證電腦PAC,並在Active Directory中執行帳戶查詢,並跳過內部方法。
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12174 Received Machine PAC
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12801 Prepared TLS ChangeCipherSpec message
12816 TLS handshake succeeded
12132 EAP-FAST built PAC-based tunnel for purpose of authentication
24351 Account validation succeeded
24420 User's Attributes retrieval from Active Directory succeeded - example . com
22037 Authentication Passed
12124 EAP-FAST inner method skipped
11503 Prepared EAP-Success
11002 Returned RADIUS Access-Accept
第二次驗證(使用者):
- 請求方透過隧道PAC傳送TLS客戶端Hello。
- 伺服器驗證PAC並構建TLS隧道(不使用證書)。
- 由於請求方沒有任何授權PAC,因此使用內部方法(EAP-MSCHAP)進行身份驗證。
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12175 Received Tunnel PAC
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12801 Prepared TLS ChangeCipherSpec message
12816 TLS handshake succeeded
12132 EAP-FAST built PAC-based tunnel for purpose of authentication
12125 EAP-FAST inner method started
11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge
24402 User authentication against Active Directory succeeded - example . com
22037 Authentication Passed
11503 Prepared EAP-Success
11002 Returned RADIUS Access-Accept
在ISE詳細報告的「其他屬性」部分中,對使用者和機器身份驗證都進行了以下說明:
EapChainingResult: No chaining
EAP-Fast搭配EAP鏈結搭配PAC Fast重新連線
在此流程中,請求方已擁有有效的隧道PAC以及使用者和機器授權PAC:
- 請求方透過隧道PAC傳送TLS客戶端Hello。
- 伺服器驗證PAC並構建TLS隧道(不使用證書)。
- ISE啟動EAP連結,請求方使用TLS隧道中的TLV為使用者和電腦附加授權PAC。
- ISE驗證授權PAC(不需要內部方法),驗證Active Directory中是否存在帳戶(無其他身份驗證),返回成功。
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12175 Received Tunnel PAC
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12801 Prepared TLS ChangeCipherSpec message
12816 TLS handshake succeeded
12132 EAP-FAST built PAC-based tunnel for purpose of authentication
12209 Starting EAP chaining
12210 Received User Authorization PAC
12211 Received Machine Authorization PAC
24420 User's Attributes retrieval from Active Directory succeeded - example .com
22037 Authentication Passed
24439 Machine Attributes retrieval from Active Directory succeeded - example .com
22037 Authentication Passed
11503 Prepared EAP-Success
11002 Returned RADIUS Access-Accept
在ISE詳細報告的「其他屬性」部分中,將註明以下結果:
EapChainingResult: EAP Chaining
此外,使用者和機器身份證明都包含在相同的記錄中,如下所示:
Username: cisco,host/mgarcarz-PC
EAP-Fast搭配EAP鏈結(不含PAC)
在此流程中,NAM配置為不使用PAC,ISE也配置為不使用PAC(但使用EAP連結)
- 請求方在不使用隧道PAC的情況下傳送TLS客戶端Hello。
- 伺服器以TLS證書和證書請求負載做出響應。
- 請求方必須信任伺服器證書,不傳送任何客戶端證書(證書負載為零),已構建TLS隧道。
- ISE在TLS隧道內傳送客戶端證書的TLV請求,但請求方不傳送請求(沒有必要擁有該請求才能繼續)。
- 使用具有MSCHAPv2驗證的內部方法,為使用者啟動EAP鏈結。
- 繼續機器驗證,使用內部方法和MSCHAPv2驗證。
- 未規範任何PAC。
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12807 Prepared TLS Certificate message
12809 Prepared TLS CertificateRequest message
12811 Extracted TLS Certificate message containing client certificate
12812 Extracted TLS ClientKeyExchange message
12816 TLS handshake succeeded
12207 Client certificate was requested but not received during tunnel establishment. Will renegotiate and request client certificate inside the tunnel.
12226 Started renegotiated TLS handshake
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12811 Extracted TLS Certificate message containing client certificate
12812 Extracted TLS ClientKeyExchange message
12804 Extracted TLS Finished message
12801 Prepared TLS ChangeCipherSpec message
12802 Prepared TLS Finished message
12226 Started renegotiated TLS handshake
12205 Client certificate was requested but not received inside the tunnel. Will continue with inner method.
12176 EAP-FAST PAC-less full handshake finished successfully
12209 Starting EAP chaining
12218 Selected identity type 'User'
11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge
24402 User authentication against Active Directory succeeded - example .com
22037 Authentication Passed
12219 Selected identity type 'Machine'
11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge
24470 Machine authentication against Active Directory is successful - example .com
22037 Authentication Passed
11503 Prepared EAP-Success
11002 Returned RADIUS Access-Accept
具有EAP鏈結授權PAC過期的EAP-Fast
在此流程中,請求方具有有效的隧道PAC,但授權PAC已過期:
- 請求方透過隧道PAC傳送TLS客戶端Hello。
- 伺服器驗證PAC並構建TLS隧道(不使用證書)。
- ISE啟動EAP連結,請求方使用TLS隧道中的TLV為使用者和電腦附加授權PAC。
- 當PAC過期時,會啟動使用者與電腦的內部方法(EAP-MSCHAP)。
- 一旦兩個身份驗證都成功,使用者和機器授權PAC都會被調配。
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12175 Received Tunnel PAC
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12801 Prepared TLS ChangeCipherSpec message
12816 TLS handshake succeeded
12132 EAP-FAST built PAC-based tunnel for purpose of authentication
12209 Starting EAP chaining
12227 User Authorization PAC has expired - will run inner method
12228 Machine Authorization PAC has expired - will run inner method
12218 Selected identity type 'User'
11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge
24402 User authentication against Active Directory succeeded - example .com
22037 Authentication Passed
12219 Selected identity type 'Machine'
24470 Machine authentication against Active Directory is successful - example .com
22037 Authentication Passed
12171 Successfully finished EAP-FAST user authorization PAC provisioning/update
12179 Successfully finished EAP-FAST machine authorization PAC provisioning/update
11503 Prepared EAP-Success
11002 Returned RADIUS Access-Accept
EAP-Fast與EAP鏈結通道PAC過期
在此流程中,如果不存在有效的隧道PAC,則會與內部階段進行完全TLS協商。
- 請求方在不使用隧道PAC的情況下傳送TLS客戶端Hello。
- 伺服器以TLS證書和證書請求負載做出響應。
- 請求方必須信任伺服器證書,不傳送客戶端證書(證書負載為零),已構建TLS隧道。
- ISE在TLS隧道內傳送客戶端證書的TLV請求,但請求方不傳送請求(沒有必要擁有該請求才能繼續)。
- 使用具有MSCHAPv2驗證的內部方法,為使用者啟動EAP鏈結。
- 繼續機器驗證,使用內部方法和MSCHAPv2驗證。
- 已成功調配所有PAC(在ISE配置中啟用)。
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12807 Prepared TLS Certificate message
12809 Prepared TLS CertificateRequest message
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
12816 TLS handshake succeeded
12207 Client certificate was requested but not received during tunnel establishment. Will renegotiate and request client certificate inside the tunnel.
12226 Started renegotiated TLS handshake
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12811 Extracted TLS Certificate message containing client certificate
12812 Extracted TLS ClientKeyExchange message
12804 Extracted TLS Finished message
12801 Prepared TLS ChangeCipherSpec message
12802 Prepared TLS Finished message
12226 Started renegotiated TLS handshake
12205 Client certificate was requested but not received inside the tunnel. Will continue with inner method.
12149 EAP-FAST built authenticated tunnel for purpose of PAC provisioning
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12209 Starting EAP chaining
12218 Selected identity type 'User'
11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge
24402 User authentication against Active Directory succeeded - example .com
22037 Authentication Passed
12126 EAP-FAST cryptobinding verification passed
12200 Approved EAP-FAST client Tunnel PAC request
12202 Approved EAP-FAST client Authorization PAC request
12219 Selected identity type 'Machine'
11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge
24470 Machine authentication against Active Directory is successful - example .com
22037 Authentication Passed
12169 Successfully finished EAP-FAST tunnel PAC provisioning/update
12171 Successfully finished EAP-FAST user authorization PAC provisioning/update
12170 Successfully finished EAP-FAST machine PAC provisioning/update
12179 Successfully finished EAP-FAST machine authorization PAC provisioning/update
11503 Prepared EAP-Success
11002 Returned RADIUS Access-Accept
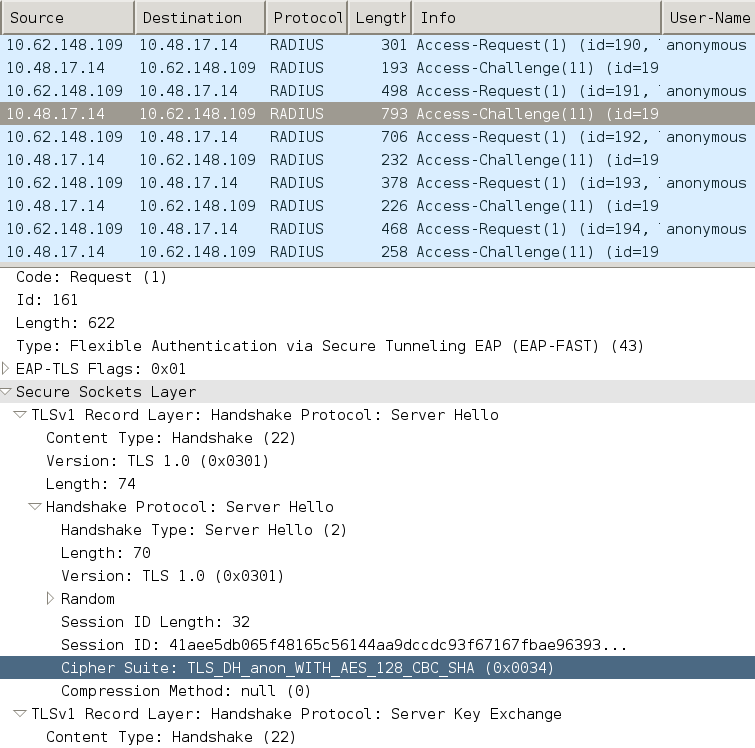
EAP-Fast搭配EAP鏈結和匿名TLS通道PAC規範
在此流程中,為PAC調配配置了ISE和NAM匿名TLS隧道(停用了PAC調配的ISE身份驗證TLS隧道) PAC調配請求看起來像:
- 請求方傳送TLS客戶端Hello而不傳送多個密碼套件。
- 伺服器會以TLS伺服器Hello和TLS匿名Diffie Hellman密碼回應(例如TLS_DH_anon_WITH_AES_128_CBC_SHA)。
- 請求方接受該協定,並構建匿名TLS隧道(不交換證書)。
- 使用具有MSCHAPv2驗證的內部方法,為使用者啟動EAP鏈結。
- 繼續機器驗證,使用內部方法和MSCHAPv2驗證。
- 由於正在構建匿名TLS隧道,因此不允許使用授權PAC。
- 返回RADIUS拒絕以強制請求方重新進行身份驗證(使用調配的PAC)。
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12808 Prepared TLS ServerKeyExchange message
12810 Prepared TLS ServerDone message
12812 Extracted TLS ClientKeyExchange message
12804 Extracted TLS Finished message
12801 Prepared TLS ChangeCipherSpec message
12802 Prepared TLS Finished message
12816 TLS handshake succeeded
12131 EAP-FAST built anonymous tunnel for purpose of PAC provisioning
12209 Starting EAP chaining
12218 Selected identity type 'User'
11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge
24402 User authentication against Active Directory succeeded - example .com
22037 Authentication Passed
12162 Cannot provision Authorization PAC on anonymous provisioning. Authorization PAC can be provisioned only on authenticated provisioning
12200 Approved EAP-FAST client Tunnel PAC request
12219 Selected identity type 'Machine'
24470 Machine authentication against Active Directory is successful - example .com
22037 Authentication Passed
12162 Cannot provision Authorization PAC on anonymous provisioning. Authorization PAC can be provisioned only on authenticated provisioning
12169 Successfully finished EAP-FAST tunnel PAC provisioning/update
12170 Successfully finished EAP-FAST machine PAC provisioning/update
11504 Prepared EAP-Failure
11003 Returned RADIUS Access-Reject
用於匿名TLS隧道協商的Wireshark資料包捕獲:
EAP-Fast僅含EAP鏈結使用者驗證
在此流程中,配置了AnyConnect NAM與EAP-FAST和使用者(EAP-TLS)和電腦身份驗證(EAP-TLS)。Windows PC已啟動,但未提供使用者憑據。交換機發起802.1x會話,NAM必須響應,但是未提供使用者憑據(尚未提供對使用者儲存和證書的訪問許可權)。因此,使用者身份驗證失敗,但電腦成功- ISE授權條件「網路訪問:EapChainingResult EQUALS User failed and machine successful」得到滿足。稍後,使用者登入並開始進行其他驗證,使用者與機器都會成功。
- 請求方透過電腦PAC傳送TLS客戶端Hello。
- 伺服器以TLS變更密碼規格回應- TLS通道會立即建立在該PAC上。
- ISE啟動EAP鏈並請求使用者身份。
- 請求方改為提供電腦標識(使用者尚未就緒),完成EAP-TLS內部方法。
- ISE再次請求使用者身份,請求方無法提供身份。
- ISE傳送TLV,中間結果=失敗(用於使用者身份驗證)。
- ISE返回最終EAP成功消息,ISE條件Network Access:EapChainingResult EQUALS User failed and machine successful已滿足。
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12174 Received Machine PAC
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12801 Prepared TLS ChangeCipherSpec message
12802 Prepared TLS Finished message
12816 TLS handshake succeeded
12132 EAP-FAST built PAC-based tunnel for purpose of authentication
12209 Starting EAP chaining
12218 Selected identity type 'User'
12213 Identity type provided by client is not equal to requested type
12215 Client suggested 'Machine' identity type instead
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12523 Extracted EAP-Response/NAK for inner method requesting to use EAP-TLS instead
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12807 Prepared TLS Certificate message
12809 Prepared TLS CertificateRequest message
12816 TLS handshake succeeded
12509 EAP-TLS full handshake finished successfully
22070 Identity name is taken from certificate attribute
15013 Selected Identity Source - Test-AD
24323 Identity resolution detected single matching account
22037 Authentication Passed
12202 Approved EAP-FAST client Authorization PAC request
12218 Selected identity type 'User'
12213 Identity type provided by client is not equal to requested type
12216 Identity type provided by client was already used for authentication
12967 Sent EAP Intermediate Result TLV indicating failure
12179 Successfully finished EAP-FAST machine authorization PAC provisioning/update
12106 EAP-FAST authentication phase finished successfully
11503 Prepared EAP-Success
11002 Returned RADIUS Access-Accept
具有EAP鏈結和不一致的匿名TLS通道設定的EAP-Fast
在此流程中,ISE僅透過匿名TLS隧道為PAC調配配置,但NAM使用已驗證的TLS隧道,ISE記錄此資訊:
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12805 Extracted TLS ClientHello message
12814 Prepared TLS Alert message
12817 TLS handshake failed
12121 Client didn't provide suitable ciphers for anonymous PAC-provisioning
11504 Prepared EAP-Failure
11003 Returned RADIUS Access-Reject
當NAM嘗試使用其特定TLS密碼構建經過身份驗證的TLS隧道,並且這些密碼不被配置為匿名TLS隧道的ISE接受(僅接受DH密碼)時會發生這種情況
疑難排解
ISE
對於詳細日誌,必須在相應的PSN節點上啟用運行時AAA調試。下面是來自prrt-server.log的一些示例日誌:
機器PAC產生:
DEBUG,0x7fd5332fe700,cntx=0001162745,sesn=mgarcarz-ise14/223983918/29245,CPMSessionID=0A3E946D00000FE5131F9D26,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Using IID from PAC request for machine,EapFastTlv.cpp:1234
DEBUG,0x7fd5332fe700,cntx=0001162745,sesn=mgarcarz-ise14/223983918/29245,CPMSessionID=0A3E946D00000FE5131F9D26,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Adding PAC of type=Machine Authorization,EapFastProtocol.cpp:3610
DEBUG,0x7fd5332fe700,cntx=0001162745,sesn=mgarcarz-ise14/223983918/29245,CPMSessionID=0A3E946D00000FE5131F9D26,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Eap-Fast: Generating Pac, Issued PAC type=Machine Authorization with expiration time: Fri Jul 3 10:38:30 2015
PAC請求核准:
INFO ,0x7fd5330fc700,cntx=0001162745,sesn=mgarcarz-ise14/223983918/29245,CPMSessionID=0A3E946D00000FE5131F9D26,user=host/mgarcarz-pc,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Eap-Fast: client PAC request approved for PAC type - Requested PAC type=Machine,EapFastProtocol.cpp:955
INFO ,0x7fd5330fc700,cntx=0001162745,sesn=mgarcarz-ise14/223983918/29245,CPMSessionID=0A3E946D00000FE5131F9D26,user=host/mgarcarz-pc,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Eap-Fast: client PAC request approved for PAC type - Requested PAC type=Machine Authorization,EapFastProtocol.cpp:955
PAC驗證:
DEBUG,0x7fd5330fc700,cntx=0001162499,sesn=mgarcarz-ise14/223983918/29243,CPMSessionID=0A3E946D00000FE5131F9D26,user=anonymous,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Authorization PAC is valid,EapFastProtocol.cpp:3403
Eap,2015-07-03 09:34:39,208,DEBUG,0x7fd5330fc700,cntx=0001162499,sesn=mgarcarz-ise14/223983918/29243,CPMSessionID=0A3E946D00000FE5131F9D26,user=anonymous,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Authorization PAC accepted,EapFastProtocol.cpp:3430
成功生成PAC的摘要示例:
DEBUG,0x7fd5331fd700,cntx=0001162749,sesn=mgarcarz-ise14/223983918/29245,CPMSessionID=0A3E946D00000FE5131F9D26,user=cisco,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Conversation summary: Provisioning. Authenticated. Inner method succeeded. Inner method succeeded. Generated PAC of type Tunnel V1A. Generated PAC of type User Authorization. Generated PAC of type Machine. Generated PAC of type Machine Authorization. Success
PAC驗證成功摘要的範例:
DEBUG,0x7fd5330fc700,cntx=0001162503,sesn=mgarcarz-ise14/223983918/29243,CPMSessionID=0A3E946D00000FE5131F9D26,user=host/mgarcarz-pc,CallingStationID=00-50-B6-11-ED-31,FramedIPAddress=10.0.13.127,Conversation summary: Authentication. PAC type Tunnel V1A. PAC is valid.Skip inner method. Skip inner method. Success
AnyConnect NAM
非EAP鏈結工作階段、沒有快速重新連線的機器驗證範例:
EAP: Identity requested
Auth[eap-fast-pac:machine-auth]: Performing full authentication
Auth[eap-fast-pac:machine-auth]: Disabling fast reauthentication
授權PAC查詢範例(非EAP鏈結工作階段的機器驗證):
Looking for matching pac with iid: host/ADMIN-PC2
Requested machine pac was sen
內部方法(對於MSCHAP)的所有狀態都可從以下日誌中驗證:
EAP (0) EAP-MSCHAP-V2: State: 0 (eap_auth_mschapv2_c.c 731
EAP (0) EAP-MSCHAP-V2: State: 2 (eap_auth_mschapv2_c.c 731
EAP (0) EAP-MSCHAP-V2: State: 1 (eap_auth_mschapv2_c.c 731
EAP (0) EAP-MSCHAP-V2: State: 4 (eap_auth_mschapv2_c.c 73
NAM允許配置擴展日誌記錄功能,該功能捕獲所有EAP資料包並將其儲存在pcap檔案中。這對於登入前啟動功能特別有用(即使是在使用者登入前進行的身份驗證,也會捕獲EAP資料包)。要啟用功能,請諮詢您的TAC工程師。
參考資料
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
15-Mar-2016 |
初始版本 |
由思科工程師貢獻
- Michal Garcarz
- Thomas Wall
 意見
意見