在Nexus 9000交換機上配置和驗證BFD
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本文檔介紹如何在基於Cisco Nexus NXOS®的交換機上配置和驗證雙向轉發檢測(BFD)會話。
必要條件
需求
思科建議您瞭解以下主題:
- 雙向轉送偵測(BFD)
- Nexus NX-OS軟體。
- 路由協定:開放最短路徑優先(OSPF)、邊界網關協定(BGP)、增強型內部網關路由協定(EIGRP)。
採用元件
本文檔中的資訊基於Cisco Nexus 9000(NXOS版本10.3(4a)。M)。
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
設定
網路圖表
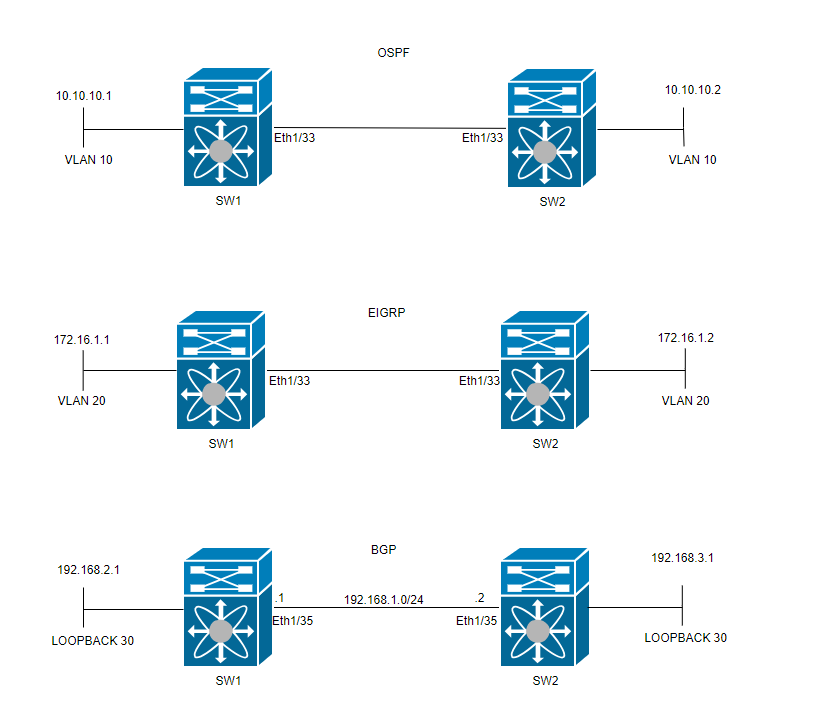
設定
配置BFD的目的是檢測並瞭解各種路由協定配置之間的差異。
第1步:在介面和協定上配置BFD之前,必須啟用BFD功能。
| 交換機1 | 交換機2 |
|
|
第2步:配置全局BFD
| 交換機1 | 交換機2 |
|
|

注意: min_tx和msec範圍從50到999毫秒,預設值為50。倍數範圍是從1到50。預設乘數為3。
第3步:在介面上配置BFD

注意:可以為介面上的所有BFD會話配置BFD會話引數。

警告:確保在啟用BFD的介面上停用網際網路控制消息協定(ICMP)重定向消息。在介面上使用no ip redirects或no ipv6 redirects命令。
| 交換機1 | 交換機2 |
|
|
BFD非同步模式類似於兩台裝置之間的握手,以保持其連線的強度。您可以在兩台裝置上設定它,當它打開時,它們會在設定的時間開始互相傳送特殊消息。這些訊息有一些重要的設定,例如傳送頻率,以及一台裝置回應另一台裝置的速度。還有一個設定會決定一台裝置需要多少則遺漏訊息,才能意識到連線可能發生問題。
BFD回送功能會將測試封包傳送給鄰居,然後讓它們傳回以檢查問題,而不需要讓鄰居參與封包轉送。它可以使用較慢的計時器來減少控制資料包流量,並在鄰居系統上測試轉發路徑,而不會影響鄰居,從而加快檢測速度。如果兩個鄰居都使用回聲功能,則不存在不對稱。
系統日誌BFD關閉原因
系統日誌BFD關閉原因 - Path Down:這表示兩個BFD鄰居之間的轉發路徑不再運行,這可能是由於網路擁塞、硬體故障或其他問題。
2024 Apr 11 22:07:07 SW2 %BFD-5-SESSION_STATE_DOWN: BFD session 1090519062 to neighbor 172.16.1.1 on interface Vlan20 has gone down. Reason: Path Down. - Echo函式失敗:Echo函式失敗,這是BFD的一個功能,用於傳送和接收回應資料包以驗證連線。如果這些資料包未能成功傳輸或接收,則表明存在問題。
2024 Apr 11 22:17:45 SW2 %BFD-5-SESSION_STATE_DOWN: BFD session 1090519174 to neighbor 10.10.10.1 on interface Vlan10 has gone down. Reason: Echo Function Failed. - 鄰居發訊號會話關閉:鄰居裝置發出BFD會話關閉的訊號,通常是因為檢測到連線結束時出現問題。
2024 Apr 11 22:03:48 SW2 %BFD-5-SESSION_STATE_DOWN: BFD session 1090519058 to neighbor 172.16.1.1 on interface Vlan20 has gone down. Reason: Neighbor Signaled Session Down. - Control Detection Time Expired:當控制檢測計時器在收到來自鄰居的預期響應(表示連線存在潛在問題)之前超時時會發生這種情況。
2024 Apr 11 22:19:31 SW2 %BFD-5-SESSION_STATE_DOWN: BFD session 1090519061 to neighbor 192.168.2.1 on interface Lo30 has gone down. Reason: Control Detection Time Expired. - 管理性關閉:BFD會話由管理員故意關閉,可能出於維護目的或由於配置更改而關閉。
2024 Apr 11 22:13:15 SW2 %BFD-5-SESSION_STATE_DOWN: BFD session 1090519064 to neighbor 10.10.10.1 on interface Vlan10 has gone down. Reason: Administratively Down.
在路由協定上配置BFD
在路由協定上配置BFD
在OSPF上配置BFD
在OSPF上配置BFD
提示:當在OSPF下啟用BFD時,它對於使用OSPF的所有介面都變為活動狀態。介面採用全局配置值。如果需要對這些值進行調整,請參閱步驟3「介面上的BFD配置」。
| 交換機1 | 交換機2 |
|
|
它還可以使用命令在OSPF介面下啟用BFDip ospf bfd
| 交換機1 | 交換機2 |
|
|
OSPF上的BFD配置示例
OSPF上的BFD配置示例SW1# show running-config ospf !Command: show running-config ospf !Running configuration last done at: Wed Apr 10 21:06:31 2024 !Time: Wed Apr 10 21:09:45 2024 version 10.3(4a) Bios:version 01.07 feature ospf router ospf 1 bfd interface Vlan10 ip router ospf 1 area 0.0.0.0 ip ospf bfd在EIGRP上配置BFD
在EIGRP上配置BFDSW1(config)# interface vlan 20 SW1(config-if)# ip eigrp 2 bfd
提示:當在EIGRP下啟用BFD時,它對於使用EIGRP的所有介面都變為活動狀態。介面採用全局配置值。如果需要對這些值進行調整,請參閱步驟3「介面上的BFD配置」。
| 交換機1 | 交換機2 |
|
|
它還可以使用命令在EIGRP介面下啟用BFDip eigrp instance-tag bfd
| 交換機1 | 交換機2 |
|
|
EIGRP上的BFD配置示例
EIGRP上的BFD配置示例SW1# show running-config eigrp !Command: show running-config eigrp !Running configuration last done at: Wed Apr 10 21:24:29 2024 !Time: Wed Apr 10 21:53:08 2024 version 10.3(4a) Bios:version 01.07 feature eigrp router eigrp 2 address-family ipv4 unicast bfd interface Vlan20 ip router eigrp 2 ip eigrp 2 bfd在BGP上配置BFD
在BGP上配置BFD
注意:在與鄰居建立BGP會話期間,更新源功能有助於BGP會話利用指定介面的主IP地址作為本地地址。此外,它使BGP能夠註冊為BFD的客戶端。

注意:在裝置上配置BFD會話時,指定「multihop」或「singlehop」將確定會話型別。如果未提供關鍵字,則當對等體直接連線時,會話型別預設為「singlehop」。如果對等體未連線,則會話型別預設為「multihop」。
| 交換機1 | 交換機2 |
|
|
BGP上的BFD配置示例
BGP上的BFD配置示例SW1# show running-config bgp !Command: show running-config bgp !Running configuration last done at: Thu Apr 11 04:47:53 2024 !Time: Thu Apr 11 06:48:43 2024 version 10.3(4a) Bios:version 01.07 feature bgp router bgp 65001 address-family ipv4 unicast neighbor 192.168.3.1 bfd multihop remote-as 65002 update-source loopback30 ebgp-multihop 5 address-family ipv4 unicast
驗證
驗證配置BFD並將其與協定(如OSPF、EIGRP或BGP)關聯後,必須自動辨識BFD鄰居。要確認這一點,請使用以下命令:
show bfd neighbors在交換機1上
SW1# show bfd neighbors OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int Vrf Type BSID 172.16.1.1 172.16.1.2 1090519059/1090519058 Up 5219(3) Up Vlan20 default SH N/A 10.10.10.1 10.10.10.2 1090519060/1090519059 Up 5219(3) Up Vlan10 default SH N/A 192.168.2.1 192.168.3.1 1090519062/1090519061 Up 728(3) Up Lo30 default MH N/A SW1# 在交換機2上
SW2# show bfd neighbors OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int Vrf Type BSID 172.16.1.2 172.16.1.1 1090519058/1090519059 Up 5053(3) Up Vlan20 default SH N/A 10.10.10.2 10.10.10.1 1090519059/1090519060 Up 5053(3) Up Vlan10 default SH N/A 192.168.3.1 192.168.2.1 1090519061/1090519062 Up 745(3) Up Lo30 default MH N/A 要確認此情況並獲取詳細輸出,請使用命令:
SW1# show bfd neighbors interface lo30 details OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int Vrf Type BSID 192.168.2.1 192.168.3.1 1090519062/1090519061 Up 676(3) Up Lo30 default MH N/A Session state is Up and not using echo function Session type: Multihop Local Diag: 0, Demand mode: 0, Poll bit: 0, Authentication: None MinTxInt: 250000 us, MinRxInt: 250000 us, Multiplier: 3 Received MinRxInt: 250000 us, Received Multiplier: 3 Holdown (hits): 750 ms (0), Hello (hits): 250 ms (82590) Rx Count: 82588, Rx Interval (ms) min/max/avg: 207/1764/219 last: 73 ms ago Tx Count: 82590, Tx Interval (ms) min/max/avg: 219/219/219 last: 67 ms ago Registered protocols: bgp Uptime: 0 days 5 hrs 2 mins 2 secs, Upcount: 1 Last packet: Version: 1 - Diagnostic: 0 State bit: Up - Demand bit: 0 Poll bit: 0 - Final bit: 0 Multiplier: 3 - Length: 24 My Discr.: 1090519061 - Your Discr.: 1090519062 Min tx interval: 250000 - Min rx interval: 250000 Min Echo interval: 0 - Authentication bit: 0 Hosting LC: 1, Down reason: None, Reason not-hosted: NoneSW2# show bfd neighbors interface vlan 20 details OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int Vrf Type BSID 172.16.1.2 172.16.1.1 1090519058/1090519059 Up 4979(3) Up Vlan20 default SH N/A Session state is Up and using echo function with 500 ms interval Session type: Singlehop Local Diag: 0, Demand mode: 0, Poll bit: 0, Authentication: None MinTxInt: 500000 us, MinRxInt: 2000000 us, Multiplier: 3 Received MinRxInt: 2000000 us, Received Multiplier: 3 Holdown (hits): 6000 ms (0), Hello (hits): 2000 ms (12454) Rx Count: 12444, Rx Interval (ms) min/max/avg: 109/1919/1908 last: 1020 ms ago Tx Count: 12454, Tx Interval (ms) min/max/avg: 1906/1906/1906 last: 856 ms ago Registered protocols: eigrp Uptime: 0 days 6 hrs 35 mins 10 secs, Upcount: 2 Last packet: Version: 1 - Diagnostic: 0 State bit: Up - Demand bit: 0 Poll bit: 0 - Final bit: 0 Multiplier: 3 - Length: 24 My Discr.: 1090519059 - Your Discr.: 1090519058 Min tx interval: 500000 - Min rx interval: 2000000 Min Echo interval: 500000 - Authentication bit: 0 Hosting LC: 1, Down reason: None, Reason not-hosted: None使用會話詳細資訊進行驗證
使用會話詳細資訊進行驗證SW1# sh bfd clients Client : Number of sessions bgp : 1 ospf : 1 eigrp : 1 SW1# show system internal bfd sess-store interface vlan 10 No of sessions: 1 >>>>> Check Number of sessions 0x4100001b - 0x41000019 Hosting LC: 1 10.10.10.1 -> 10.10.10.2 bsid 0 >>>>> Check IP addresses BFD_SESS_ST_SESSION_UP for 0 days 0:6:22 594 >>>>> Check uptime Vlan10 [2 0x901000a:0x43 0:10 0x1000c 0x1000c] SMAC: 4464.3c81.ddd7 DMAC: 4464.3c81.cdb7 Local TX/RX/ST(ms): 500/500/2000000 Mult: 3 EchoRx: 50000 Ver:1 Flags(0x0): Echo Auth Interop (Disabled) Auth(0 0 0) Group id 0x0 Active TX/RX/ST(ms): 2000/2000/2000000 Mult: 3 State: 3 Diag: 0x0 Flags: 0xc 0000 Auth(0 0 0) Spray DIs: 0 Port-Lcs: Module 1 has 2 links - ACL not programmed Applications: (1) ospf [0x1:0x41000119 flags 0x0] App Data : [c0a80301000] Description: 10.10.10.2 MTS Dest 0xfe000001:0x140 No-Host reason: 0x0(SUCCESS) Counters: >>>>>>>> Check the counters below Retries: LC remove(0), ACL Inst/Rem(0/0), Redisc(0) No. of ACLs Added(1) Flap counters: Ctrl Detect timer expired(0), Echo failed(0), Neigh Signaled down(0), Admin d own(0), Forwarding plane reset(0), Path down(0), Concat path down(0), Rev Concat path down(0) Last ACL added time: 58781 usecs after Thu Apr 11 22:18:19 2024 Last ACL response time: 81830 usecs after Thu Apr 11 22:18:19 2024 Last session install time: 58285 usecs after Thu Apr 11 22:18:19 2024 Last session install response time: 58717 usecs after Thu Apr 11 22:18:19 2024 使用訪問清單進行驗證
使用訪問清單進行驗證SW2# show system internal access-list vlan 10 input statistics slot 1 ======= INSTANCE 0x0 --------------- Tcam 12 resource usage: ---------------------- LBL M = 0x1 Bank 0 ------ IPv4 Class Policies: BFD() [Merged] Netflow profile: 0 Netflow deny profile: 0 Entries: [Index] Entry [Stats] --------------------- [0x0000:0x0003:0x0c0d] permit udp 0.0.0.0/0 0.0.0.0/0 range 3784 3785 encap 0x0 [205340] >>>>> This counter needs to increase SW2# show system internal access-list sup-redirect-stats | i i bfd 3085 BFD 12217 >>>>> This counter need to increase 3121 BFDC TCLASS PACKET 0 3146 BFDC v4 PACKET 15 3148 BFDC TCLASS V6 PACKET 0 3156 BFDC v6 PACKET 0 3158 BFDC v6 LL Ucast PACKET 0 3209 BFDC v4 multihop PACKET 383697 >>>>> This counter need to increase in multihop case 3121 BFDC TCLASS PACKET 0 3146 BFDC v4 PACKET 0 3148 BFDC TCLASS V6 PACKET 0 3156 BFDC v6 PACKET 0 3158 BFDC v6 LL Ucast PACKET 0 3209 BFDC v4 multihop PACKET 0使用Ethanalyzer驗證
使用Ethanalyzer驗證
另一種方法是執行資料包捕獲,特別是針對UDP埠3785進行過濾。
SW1# ethanalyzer local interface inband display-filter "udp.port==3785" limit-captured-frames 0 Capturing on 'ps-inb' 5 2024-04-11 05:26:37.294596186 10.10.10.1 → 10.10.10.1 BFD Echo 70 Originator specific content 6 2024-04-11 05:26:37.294623155 10.10.10.1 → 10.10.10.1 BFD Echo 70 Originator specific content 7 2024-04-11 05:26:37.294635837 172.16.1.1 → 172.16.1.1 BFD Echo 70 Originator specific content 8 2024-04-11 05:26:37.294653159 172.16.1.1 → 172.16.1.1 BFD Echo 70 Originator specific content 4 18 2024-04-11 05:26:37.780441619 10.10.10.1 → 10.10.10.1 BFD Echo 70 Originator specific content 19 2024-04-11 05:26:37.780461351 172.16.1.1 → 172.16.1.1 BFD Echo 70 Originator specific content 20 2024-04-11 05:26:37.780467533 10.10.10.1 → 10.10.10.1 BFD Echo 70 Originator specific content 21 2024-04-11 05:26:37.780481315 172.16.1.1 → 172.16.1.1 BFD Echo 70 Originator specific content 30 2024-04-11 05:26:38.266365493 10.10.10.1 → 10.10.10.1 BFD Echo 70 Originator specific content 31 2024-04-11 05:26:38.266392766 10.10.10.1 → 10.10.10.1 BFD Echo 70 Originator specific content在從BFD回聲協定捕獲的資料包中,預期存在相同的源IP地址和目的IP地址,因為這些回聲資料包源自本地交換機本身。

注意:如果介面下沒有「no bfd echo」語句,捕獲將同時顯示具有本地源IP地址和相鄰目標IP地址的資料包,並觀察BFD控制
SW2# ethanalyzer local interface inband display-filter "ip.addr==192.168.2.1" limit-captured-frames 0 Capturing on 'ps-inb' 1 2024-04-11 05:38:21.155483591 192.168.2.1 → 192.168.3.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 2 2024-04-11 05:38:21.182606602 192.168.3.1 → 192.168.2.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 11 2024-04-11 05:38:21.375187034 192.168.2.1 → 192.168.3.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 12 2024-04-11 05:38:21.402295701 192.168.3.1 → 192.168.2.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 4 14 2024-04-11 05:38:21.594612491 192.168.2.1 → 192.168.3.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 15 2024-04-11 05:38:21.621742431 192.168.3.1 → 192.168.2.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 20 2024-04-11 05:38:21.813971234 192.168.2.1 → 192.168.3.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 8 21 2024-04-11 05:38:21.841086554 192.168.3.1 → 192.168.2.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 22 2024-04-11 05:38:22.033395440 192.168.2.1 → 192.168.3.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 23 2024-04-11 05:38:22.060526055 192.168.3.1 → 192.168.2.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 28 2024-04-11 05:38:22.252709432 192.168.2.1 → 192.168.3.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 29 2024-04-11 05:38:22.279810427 192.168.3.1 → 192.168.2.1 BFD Control 66 Diag: No Diagnostic, State: Up, Flags: 0x00 修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
25-Apr-2024 |
初始版本 |
由思科工程師貢獻
- Cesar Alejandro Antonio Martinez
 意見
意見