簡介
本文檔介紹如何檢查Nexus 9K平台中智慧流量導向器(ITD)的控制平面和資料平面。
必要條件
需求
思科建議您瞭解以下主題:
- Nexus NX-OS軟體。
- 存取清單(ACL)。
- IP服務層級協定(IP SLA)。
- 原則型路由(PBR)。
- 智慧流量導向器(ITD)。
採用元件
本檔案中的資訊是根據搭載NXOS版本10.2(5)的Cisco Nexus 9000。
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
設定
ITD是一個基於硬體的智慧、多TB解決方案,允許您為第3層和第4層流量分配、負載平衡和重定向構建可擴展的架構。
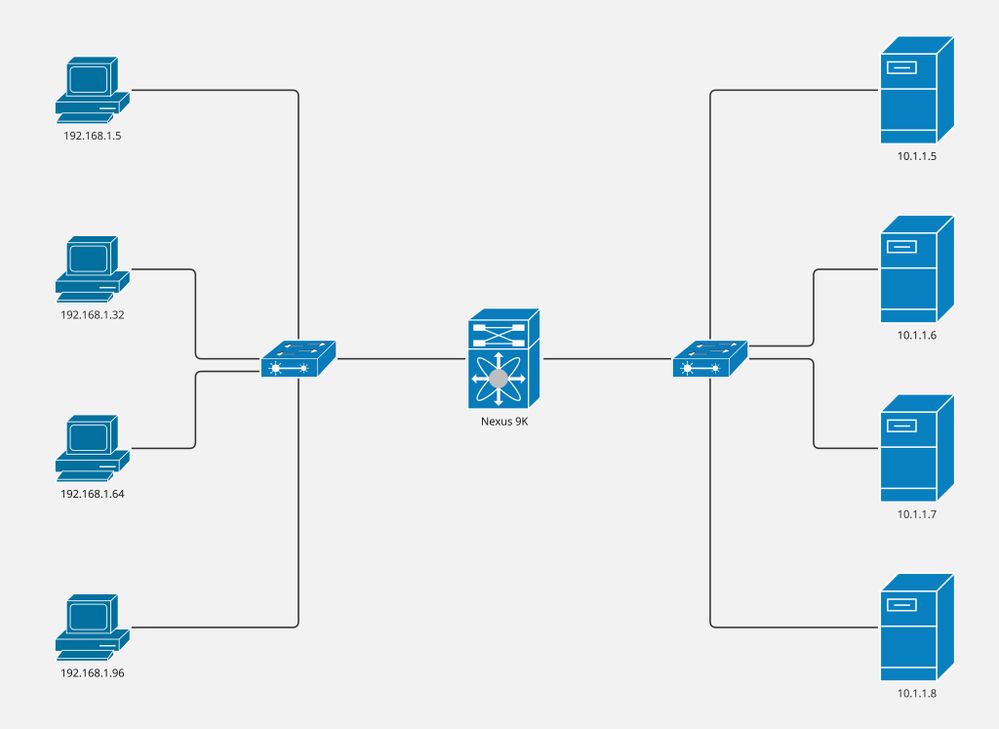
網路圖表
- 電腦:4
- 伺服器:4
- 第2層交換機:2
- Nexus 9K交換機:1

注意:第2層交換機合併伺服器/電腦與Nexus 9K交換機(ITD運行在該交換機上)之間的連線。
組態
此配置在Nexus 9K交換機上實施,僅涵蓋ITD部分。電腦是VLAN 5的一部分,伺服器是VLAN 10的一部分,而Nexus 9K是兩個VLAN的網關。
步驟 1.啟用所需功能。
feature itd
feature sla sender
feature sla responder
feature pbr
步驟 2.定義裝置組、指向節點並指示探測方法。
itd device-group CiscoGroup
probe icmp frequency 5 timeout 5 retry-down-count 2 retry-up-count 2
node ip 10.1.1.5
node ip 10.1.1.6
node ip 10.1.1.7
node ip 10.1.1.8
步驟 3.定義服務。使用者可以指示虛擬IP或包括訪問清單。

注意:NX-OS將最後一個八位元除以指定的儲存段數。例如,我們將256除以8。因此,每個儲存桶包括32台主機。
Bucket 1: From x.x.x.0 to x.x.x.31
Bucket 2: From x.x.x.32 to x.x.x.63
Bucket 3: From x.x.x.64 to x.x.x.95
Bucket 4: From x.x.x.96 to x.x.x.127
Bucket 5: From x.x.x.128 to x.x.x.159
Bucket 6: From x.x.x.160 to x.x.x.191
Bucket 7: From x.x.x.192 to x.x.x.223
Bucket 8: From x.x.x.224 to x.x.x.255
itd CiscoService
device-group CiscoGroup
virtual ip 192.168.255.1 255.255.255.255 advertise enable
ingress interface Vlan5
failaction node reassign
load-balance method src ip buckets 8
no shut
步驟 4.為定義的服務啟用統計資訊。
itd statistics CiscoService
驗證
1.確認ITD服務處於活動狀態,並且節點狀態為正常。
Nexus# show itd CiscoService brief
Legend:
C-S(Config-State): A-Active,S-Standby,F-Failed
ST(Status): ST-Standby,LF-Link Failed,PF-Probe Failed,PD-Peer Down,IA-Inactive,SH-Shut,HD-Hold-down
Name LB Scheme Status Buckets Interface
-------------- ---------- -------- --------- --------------
CiscoService src-ip ACTIVE 8 Vlan5
Source Interface
----------------
Device Group Probe Port VRF
-------------------------------------------------- ----- ------ ---------
CiscoGroup ICMP
Virtual IP Netmask/Prefix Protocol Port
------------------------------------------------------ ------------ ----------
192.168.255.1 / 255.255.255.255 IP 0
Node IP Cluster-id C-S WGT Probe Port Probe-IP STS
------------------------- ---------- -- --- ---- ----- --------------- --
1 10.1.1.5 A 1 ICMP OK
2 10.1.1.6 A 1 ICMP OK
3 10.1.1.7 A 1 ICMP OK
4 10.1.1.8 A 1 ICMP OK
2.確認已建立路由策略並與入口介面關聯。

注意:Route-policy在運行配置中應用(在輸入介面下),直到NXOS 10.1(2),從NXOS 10.2(1)開始,您可以使用show ip policy命令查詢系統中關聯的路由策略。
Nexus# show ip policy
Interface Route-map Status VRF-Name
Vlan5 CiscoService_itd_pool Active default
3.確認已正確生成與預期節點關聯的路由對映,並指示跟蹤(IP SLA)。

註:每個桶應具有一個路由對映條目。
每個節點應具有一個軌道。
Nexus# show route-map dynamic CiscoService_itd_pool
route-map CiscoService_itd_pool, permit, sequence 10
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_1
Set clauses:
ip next-hop verify-availability 10.1.1.5 track 2 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 11
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_2
Set clauses:
ip next-hop verify-availability 10.1.1.6 track 3 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 12
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_3
Set clauses:
ip next-hop verify-availability 10.1.1.7 track 4 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 13
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_4
Set clauses:
ip next-hop verify-availability 10.1.1.8 track 5 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 14
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_5
Set clauses:
ip next-hop verify-availability 10.1.1.5 track 2 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 15
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_6
Set clauses:
ip next-hop verify-availability 10.1.1.6 track 3 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 16
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_7
Set clauses:
ip next-hop verify-availability 10.1.1.7 track 4 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 17
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_8
Set clauses:
ip next-hop verify-availability 10.1.1.8 track 5 [ UP ] force-order
4.確認存取清單已正確產生,且具備預期的ip相符條件。

註意:ACL在running-config中生成,直到NXOS 9.3(2),從NXOS 9.3(3)開始,我們可以使用show ip access-list dynamic命令在系統中找到ACL。
Nexus# show ip access-lists CiscoService_itd_vip_1_bucket_1 dynamic
IP access list CiscoService_itd_vip_1_bucket_1
10 permit ip 1.1.1.0 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_2 dynamic
IP access list CiscoService_itd_vip_1_bucket_2
10 permit ip 1.1.1.32 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_3 dynamic
IP access list CiscoService_itd_vip_1_bucket_3
10 permit ip 1.1.1.64 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_4 dynamic
IP access list CiscoService_itd_vip_1_bucket_4
10 permit ip 1.1.1.96 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_5 dynamic
IP access list CiscoService_itd_vip_1_bucket_5
10 permit ip 1.1.1.128 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_6 dynamic
IP access list CiscoService_itd_vip_1_bucket_6
10 permit ip 1.1.1.160 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_7 dynamic
IP access list CiscoService_itd_vip_1_bucket_7
10 permit ip 1.1.1.192 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_8 dynamic
IP access list CiscoService_itd_vip_1_bucket_8
10 permit ip 1.1.1.224 255.255.255.31 192.168.255.1/32
5.確保在TCAM中對訪問清單進行程式設計。
Nexus# show system internal access-list input entries detail | begin "VLAN 5"
VLAN 5 :
=========
INSTANCE 0x0
---------------
Tcam 1 resource usage:
----------------------
LBL B = 0x1
Bank 1
------
IPv4 Class
Policies: PBR(CiscoService_itd_vip_1_bucket_8)
Netflow profile: 0
Netflow deny profile: 0
Entries:
[Index] Entry [Stats]
---------------------
[0x0000:0x0002:0x0002] permit ip 0.0.0.0/0 224.0.0.0/4 routeable 0x1 [0]
[0x0002:0x0004:0x0004] permit ip 0.0.0.0/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0003:0x0005:0x0005] permit ip 0.0.0.32/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0004:0x0006:0x0006] permit ip 0.0.0.64/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0005:0x0007:0x0007] permit ip 0.0.0.96/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000b:0x000d:0x000d] permit ip 0.0.0.128/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000c:0x000e:0x000e] permit ip 0.0.0.160/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000d:0x000f:0x000f] permit ip 0.0.0.192/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000e:0x0010:0x0010] permit ip 0.0.0.224/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000f:0x0011:0x0011] permit ip 0.0.0.0/0 0.0.0.0/0 routeable 0x1 [0]
L4 protocol cam entries usage: none
No mac protocol cam entries are in use
INSTANCE 0x1
---------------
Tcam 1 resource usage:
----------------------
LBL B = 0x1
Bank 1
------
IPv4 Class
Policies: PBR(CiscoService_itd_vip_1_bucket_8)
Netflow profile: 0
Netflow deny profile: 0
Entries:
[Index] Entry [Stats]
---------------------
[0x0000:0x0002:0x0002] permit ip 0.0.0.0/0 224.0.0.0/4 routeable 0x1 [0]
[0x0002:0x0004:0x0004] permit ip 0.0.0.0/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0003:0x0005:0x0005] permit ip 0.0.0.32/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0004:0x0006:0x0006] permit ip 0.0.0.64/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0005:0x0007:0x0007] permit ip 0.0.0.96/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000b:0x000d:0x000d] permit ip 0.0.0.128/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000c:0x000e:0x000e] permit ip 0.0.0.160/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000d:0x000f:0x000f] permit ip 0.0.0.192/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000e:0x0010:0x0010] permit ip 0.0.0.224/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000f:0x0011:0x0011] permit ip 0.0.0.0/0 0.0.0.0/0 routeable 0x1 [0]
L4 protocol cam entries usage: none
No mac protocol cam entries are in use
6.將流量傳送到虛擬IP地址,並確認預期節點的計數器(資料包數)增加。
Nexus# show itd CiscoService statistics
Service Device Group VIP/mask #Packets
-------------------------------------------------------------------------------------------------------------------------------------------
CiscoService CiscoGroup 192.168.255.1 / 255.255.255.255 0 (0%)
Traffic Bucket Assigned to Mode Original Node #Packets
--------------- -------------- ----- -------------- ---------
CiscoService_itd_vip_1_bucket_1 10.1.1.5 Redirect 10.1.1.5 0 (0%)
CiscoService_itd_vip_1_bucket_5 10.1.1.5 Redirect 10.1.1.5 0 (0%)
Traffic Bucket Assigned to Mode Original Node #Packets
--------------- -------------- ----- -------------- ---------
CiscoService_itd_vip_1_bucket_2 10.1.1.6 Redirect 10.1.1.6 0 (0%)
CiscoService_itd_vip_1_bucket_6 10.1.1.6 Redirect 10.1.1.6 0 (0%)
Traffic Bucket Assigned to Mode Original Node #Packets
--------------- -------------- ----- -------------- ---------
CiscoService_itd_vip_1_bucket_3 10.1.1.7 Redirect 10.1.1.7 0 (0%)
CiscoService_itd_vip_1_bucket_7 10.1.1.7 Redirect 10.1.1.7 0 (0%)
Traffic Bucket Assigned to Mode Original Node #Packets
--------------- -------------- ----- -------------- ---------
CiscoService_itd_vip_1_bucket_4 10.1.1.8 Redirect 10.1.1.8 0 (0%)
CiscoService_itd_vip_1_bucket_8 10.1.1.8 Redirect 10.1.1.8 0 (0%)