在檢查點NG和路由器之間配置IPSec隧道
簡介
本文檔演示如何使用預共用金鑰形成IPSec隧道以加入兩個專用網路:
-
路由器內部的172.16.15.x專用網路。
-
CheckpointTM Next Generation(NG)內部的192.168.10.x專用網路。
必要條件
需求
本文檔中概述的程式基於這些假設。
-
CheckpointTM NG基本策略已設定。
-
所有訪問、網路地址轉換(NAT)和路由設定均已配置。
-
從路由器內部和CheckpointTM NG內部到Internet的流量。
採用元件
本文中的資訊係根據以下軟體和硬體版本:
-
思科1751路由器
-
Cisco IOS®軟體(C1700-K9O3SY7-M),版本12.2(8)T4,版本軟體(fc1)
-
CheckpointTM NG內部版50027
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路正在作用,請確保您已瞭解任何指令可能造成的影響。
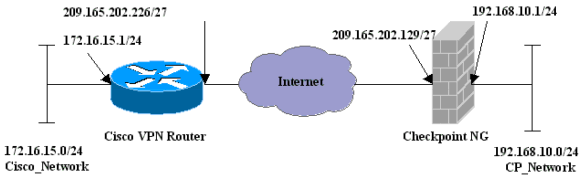
網路圖表
本檔案會使用以下網路設定:
慣例
如需文件慣例的詳細資訊,請參閱思科技術提示慣例。
配置Cisco 1751 VPN路由器
| Cisco VPN 1751路由器 |
|---|
version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption hostname sv1-6 memory-size iomem 15 mmi polling-interval 60 no mmi auto-configure no mmi pvc mmi snmp-timeout 180 ip subnet-zero no ip domain-lookup ip audit notify log ip audit po max-events 100 !--- Internet Key Exchange (IKE) configuration. crypto isakmp policy 1 encr 3des hash md5 authentication pre-share group 2 lifetime 1800 !--- IPSec configuration. crypto isakmp key aptrules address 209.165.202.129 ! crypto ipsec transform-set aptset esp-3des esp-md5-hmac ! crypto map aptmap 1 ipsec-isakmp set peer 209.165.202.129 set transform-set aptset match address 110 ! interface Ethernet0/0 ip address 209.165.202.226 255.255.255.224 ip nat outside half-duplex crypto map aptmap ! interface FastEthernet0/0 ip address 172.16.15.1 255.255.255.0 ip nat inside speed auto !--- NAT configuration. ip nat inside source route-map nonat interface Ethernet0/0 overload ip classless ip route 0.0.0.0 0.0.0.0 209.165.202.225 no ip http server ip pim bidir-enable !--- Encryption match address access list. access-list 110 permit ip 172.16.15.0 0.0.0.255 192.168.10.0 0.0.0.255 !--- NAT access list. access-list 120 deny ip 172.16.15.0 0.0.0.255 192.168.10.0 0.0.0.255 access-list 120 permit ip 172.16.15.0 0.0.0.255 any route-map nonat permit 10 match ip address 120 line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 password cisco login end |
配置檢查點NG
CheckpointTM NG是物件導向的配置。定義網路對象和規則以組成與要設定的VPN配置相關的策略。然後使用CheckpointTM NG策略編輯器安裝此策略,以完成VPN配置的CheckpointTM NG端。
-
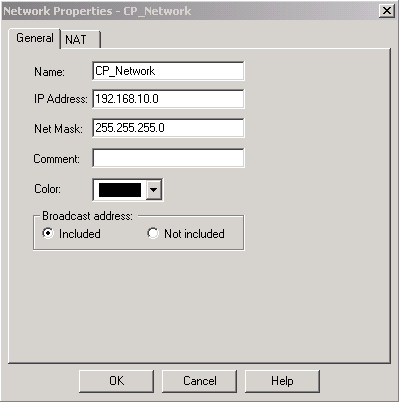
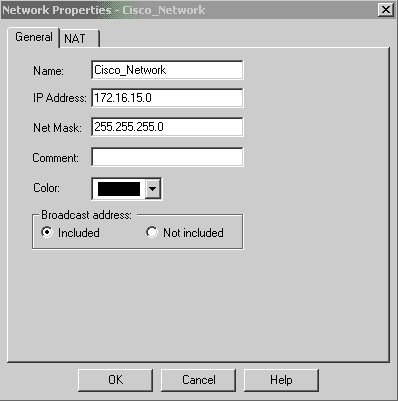
建立Cisco網路子網和CheckpointTM NG網路子網作為網路對象。這是加密的。要建立對象,請選擇管理>網路對象,然後選擇新建>網路。輸入相應的網路資訊,然後按一下OK。
這些示例顯示一組名為CP_Network和Cisco_Network的對象。
-
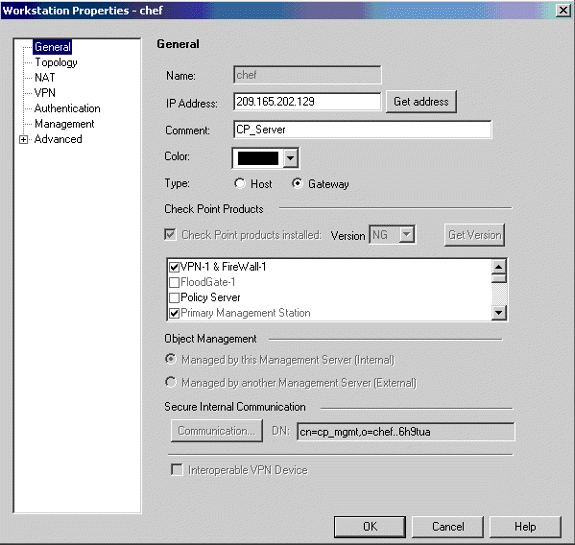
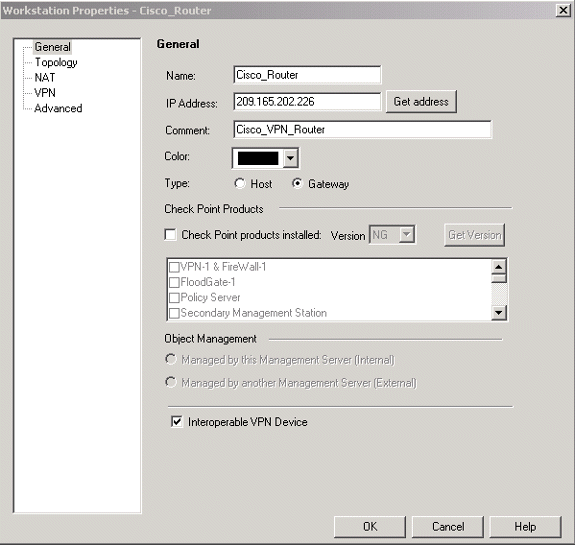
將Cisco_Router和Checkpoint_NG對象建立為工作站對象。這些是VPN裝置。要建立對象,請選擇管理>網路對象,然後選擇新建>工作站。
請注意,您可以使用初始CheckpointTM NG設定期間建立的CheckpointTM NG工作站對象。選擇選項將工作站設定為Gateway和Interoperational VPN Device。
以下示例顯示一組名為chef和Cisco_Router的對象。
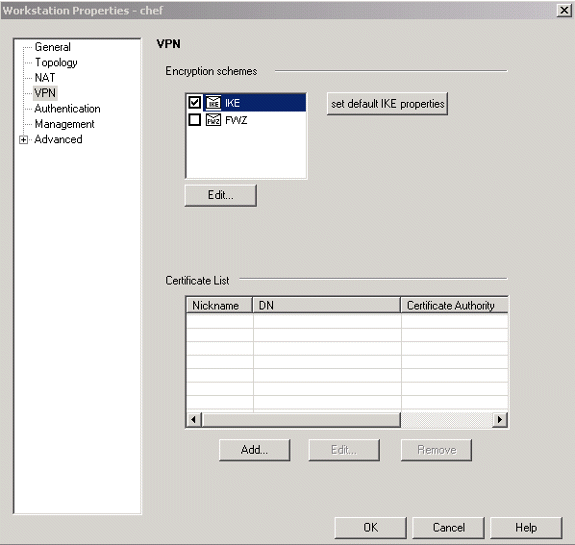
-
在VPN頁籤上配置IKE,然後按一下Edit。
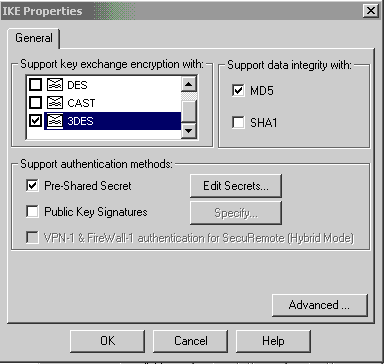
-
配置金鑰交換策略,然後按一下Edit Secrets。
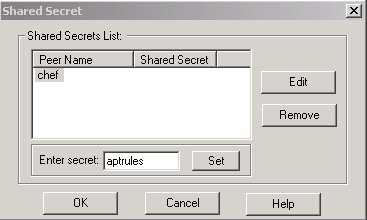
-
設定要使用的預共用金鑰,然後多次按一下OK,直到配置視窗消失。
-
選擇Rules > Add Rules > Top為策略配置加密規則。
頂部的規則是第一個在可以繞過加密的任何其他規則之前執行的規則。配置Source和Destination以包括CP_Network和Cisco_Network,如下所示。新增規則的Encrypt Action部分後,按一下右鍵Action並選擇Edit Properties。
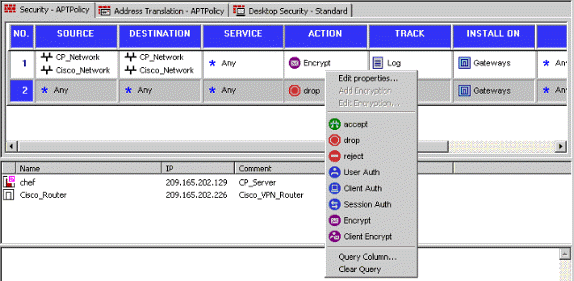
-
選中並突出顯示IKE後,按一下Edit。
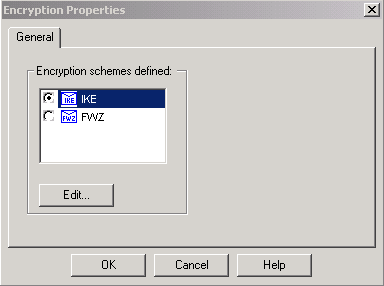
-
確認IKE配置。
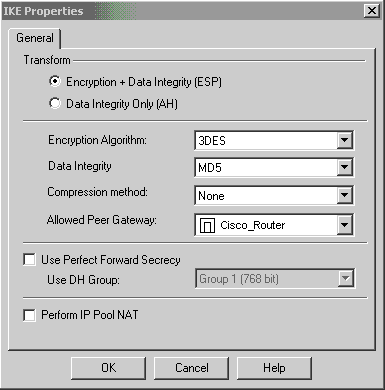
-
在Cisco裝置與其他IPSec裝置之間運行VPN的主要問題之一是金鑰交換重新協商。確保Cisco路由器上IKE交換的設定與CheckpointTM NG上配置的IKE交換設定完全相同。
注意:此引數的實際值取決於特定的公司安全策略。
在本示例中,路由器上的IKE配置已使用lifetime 1800命令設定為30分鐘。必須在CheckpointTM NG上設定相同的值。
要在CheckpointTM NG上設定此值,請選擇Manage Network Object,然後選擇CheckpointTM NG對象,然後按一下Edit。然後選擇VPN,編輯IKE。選擇Advanced並配置重新鍵入引數。為CheckpointTM NG網路對象配置金鑰交換後,請為Cisco_Router網路對象執行相同的金鑰交換重新協商配置。
注意:請確保選擇了正確的Diffie-Hellman組,以匹配路由器上配置的組。
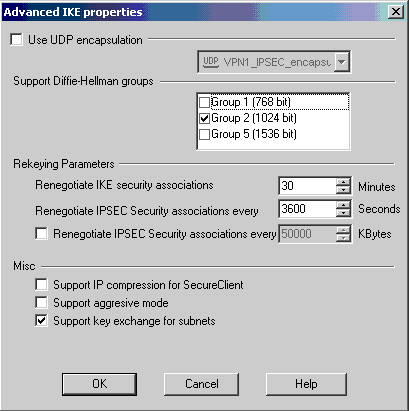
-
策略配置已完成。儲存策略並選擇Policy > Install以啟用它。
編譯策略時,安裝視窗將顯示進度註釋。
當安裝視窗指示策略安裝完成時,按一下Close完成該過程。
驗證
本節提供的資訊可用於確認您的組態是否正常運作。
驗證思科路由器
輸出直譯器工具(僅供註冊客戶使用)支援某些show命令,此工具可讓您檢視show命令輸出的分析。
-
show crypto isakmp sa — 顯示對等體上的所有當前IKE安全關聯(SA)。
-
show crypto ipsec sa — 顯示當前SA使用的設定。
驗證檢查點NG
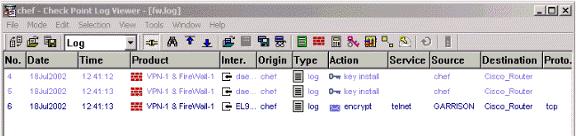
要檢視日誌,請選擇視窗>日誌檢視器。
要檢視系統狀態,請選擇「視窗」>「系統狀態」。
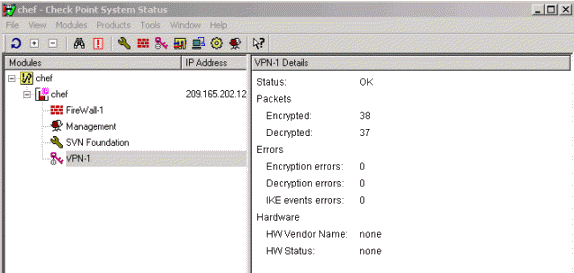
疑難排解
思科路由器
本節提供的資訊可用於對組態進行疑難排解。
如需更多疑難排解資訊,請參閱IP安全性疑難排解 — 瞭解和使用debug命令。
注意:發出debug命令之前,請參閱有關Debug命令的重要資訊。
-
debug crypto engine — 顯示有關執行加密和解密的加密引擎的調試消息。
-
debug crypto isakmp — 顯示有關IKE事件的消息。
-
debug crypto ipsec — 顯示IPSec事件。
-
clear crypto isakmp — 清除所有活動的IKE連線。
-
clear crypto sa — 清除所有IPSec SA。
成功的debug Log輸出
18:05:32: ISAKMP (0:0): received packet from
209.165.202.129 (N) NEW SA
18:05:32: ISAKMP: local port 500, remote port 500
18:05:32: ISAKMP (0:1): Input = IKE_MESG_FROM_PEER,
IKE_MM_EXCH
Old State = IKE_READY New State = IKE_R_MM1
18:05:32: ISAKMP (0:1): processing SA payload. message ID = 0
18:05:32: ISAKMP (0:1): processing vendor id payload
18:05:32: ISAKMP (0:1): vendor ID seems Unity/DPD
but bad major
18:05:32: ISAKMP (0:1): found peer pre-shared key
matching 209.165.202.129
18:05:32: ISAKMP (0:1): Checking ISAKMP transform 1
against priority 1 policy
18:05:32: ISAKMP: encryption 3DES-CBC
18:05:32: ISAKMP: hash MD5
18:05:32: ISAKMP: auth pre-share
18:05:32: ISAKMP: default group 2
18:05:32: ISAKMP: life type in seconds
18:05:32: ISAKMP: life duration (VPI) of 0x0 0x0 0x7 0x8
18:05:32: ISAKMP (0:1): atts are acceptable. Next payload is 0
18:05:33: ISAKMP (0:1): processing vendor id payload
18:05:33: ISAKMP (0:1): vendor ID seems Unity/DPD but bad major
18:05:33: ISAKMP (0:1): Input = IKE_MESG_INTERNAL,
IKE_PROCESS_MAIN_MODE
Old State = IKE_R_MM1 New State = IKE_R_MM1
18:05:33: ISAKMP (0:1): sending packet to 209.165.202.129 (R)
MM_SA_SETUP
18:05:33: ISAKMP (0:1): Input = IKE_MESG_INTERNAL,
IKE_PROCESS_COMPLETE
Old State = IKE_R_MM1 New State = IKE_R_MM2
18:05:33: ISAKMP (0:1): received packet from 209.165.202.129 (R)
MM_SA_SETUP
18:05:33: ISAKMP (0:1): Input = IKE_MESG_FROM_PEER,
IKE_MM_EXCH
Old State = IKE_R_MM2 New State = IKE_R_MM3
18:05:33: ISAKMP (0:1): processing KE payload.
message ID = 0
18:05:33: ISAKMP (0:1): processing NONCE payload.
message ID = 0
18:05:33: ISAKMP (0:1): found peer pre-shared key
matching 209.165.202.129
18:05:33: ISAKMP (0:1): SKEYID state generated
18:05:33: ISAKMP (0:1): Input = IKE_MESG_INTERNAL,
IKE_PROCESS_MAIN_MODE
Old State = IKE_R_MM3 New State = IKE_R_MM3
18:05:33: ISAKMP (0:1): sending packet to 209.165.202.129 (R)
MM_KEY_EXCH
18:05:33: ISAKMP (0:1): Input = IKE_MESG_INTERNAL,
IKE_PROCESS_COMPLETE
Old State = IKE_R_MM3 New State = IKE_R_MM4
18:05:33: ISAKMP (0:1): received packet from 209.165.202.129 (R)
MM_KEY_EXCH
18:05:33: ISAKMP (0:1): Input = IKE_MESG_FROM_PEER,
IKE_MM_EXCH
Old State = IKE_R_MM4 New State = IKE_R_MM5
18:05:33: ISAKMP (0:1): processing ID payload.
message ID = 0
18:05:33: ISAKMP (0:1): processing HASH payload.
message ID = 0
18:05:33: ISAKMP (0:1): SA has been authenticated
with 209.165.202.129
18:05:33: ISAKMP (0:1): Input = IKE_MESG_INTERNAL,
IKE_PROCESS_MAIN_MODE
Old State = IKE_R_MM5 New State = IKE_R_MM5
18:05:33: ISAKMP (0:1): SA is doing pre-shared key authentication
using id type ID_IPV4_ADDR
18:05:33: ISAKMP (1): ID payload
next-payload : 8
type : 1
protocol : 17
port : 500
length : 8
18:05:33: ISAKMP (1): Total payload length: 12
18:05:33: ISAKMP (0:1): sending packet to 209.165.202.129
(R) QM_IDLE
18:05:33: ISAKMP (0:1): Input = IKE_MESG_INTERNAL,
IKE_PROCESS_COMPLETE
Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
18:05:33: ISAKMP (0:1): Input = IKE_MESG_INTERNAL,
IKE_PHASE1_COMPLETE
Old State = IKE_P1_COMPLETE
New State = IKE_P1_COMPLETE
18:05:33: ISAKMP (0:1): received packet from 209.165.202.129 (R)
QM_IDLE
18:05:33: ISAKMP (0:1): processing HASH payload.
message ID = -1335371103
18:05:33: ISAKMP (0:1): processing SA payload.
message ID = -1335371103
18:05:33: ISAKMP (0:1): Checking IPSec proposal 1
18:05:33: ISAKMP: transform 1, ESP_3DES
18:05:33: ISAKMP: attributes in transform:
18:05:33: ISAKMP: SA life type in seconds
18:05:33: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
18:05:33: ISAKMP: authenticator is HMAC-MD5
18:05:33: ISAKMP: encaps is 1
18:05:33: ISAKMP (0:1): atts are acceptable.
18:05:33: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 209.165.202.226, remote= 209.165.202.129,
local_proxy= 172.16.15.0/255.255.255.0/0/0 (type=4),
remote_proxy= 192.168.10.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x4
18:05:33: ISAKMP (0:1): processing NONCE payload.
message ID = -1335371103
18:05:33: ISAKMP (0:1): processing ID payload.
message ID = -1335371103
18:05:33: ISAKMP (0:1): processing ID payload.
message ID = -1335371103
18:05:33: ISAKMP (0:1): asking for 1 spis from ipsec
18:05:33: ISAKMP (0:1): Node -1335371103,
Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
18:05:33: IPSEC(key_engine): got a queue event...
18:05:33: IPSEC(spi_response): getting spi 2147492563 for SA
from 209.165.202.226 to 209.165.202.129 for prot 3
18:05:33: ISAKMP: received ke message (2/1)
18:05:33: ISAKMP (0:1): sending packet to
209.165.202.129 (R) QM_IDLE
18:05:33: ISAKMP (0:1): Node -1335371103,
Input = IKE_MESG_FROM_IPSEC, IKE_SPI_REPLY
Old State = IKE_QM_SPI_STARVE New State = IKE_QM_R_QM2
18:05:33: ISAKMP (0:1): received packet
from 209.165.202.129 (R) QM_IDLE
18:05:33: ISAKMP (0:1): Creating IPSec SAs
18:05:33: inbound SA from 209.165.202.129 to 209.165.202.226
(proxy 192.168.10.0 to 172.16.15.0)
18:05:33: has spi 0x800022D3 and conn_id 200 and flags 4
18:05:33: lifetime of 3600 seconds
18:05:33: outbound SA from 209.165.202.226 to 209.165.202.129
(proxy 172.16.15.0 to 192.168.10.0 )
18:05:33: has spi -2006413528 and conn_id 201 and flags C
18:05:33: lifetime of 3600 seconds
18:05:33: ISAKMP (0:1): deleting node -1335371103 error
FALSE reason "quick mode done (await()"
18:05:33: ISAKMP (0:1): Node -1335371103, Input = IKE_MESG_FROM_PEER,
IKE_QM_EXCH
Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE
18:05:33: IPSEC(key_engine): got a queue event...
18:05:33: IPSEC(initialize_sas): ,
(key eng. msg.) INBOUND local= 209.165.202.226,
remote=209.165.202.129,
local_proxy= 172.16.15.0/255.255.255.0/0/0 (type=4),
remote_proxy= 192.168.10.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 3600s and 0kb,
spi= 0x800022D3(2147492563), conn_id= 200, keysize= 0,
flags= 0x4
18:05:33: IPSEC(initialize_sas): ,
(key eng. msg.) OUTBOUND local= 209.165.202.226,
remote=209.165.202.129,
local_proxy= 172.16.15.0/255.255.255.0/0/0 (type=4),
remote_proxy= 192.168.10.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 3600s and 0kb,
spi= 0x88688F28(2288553768), conn_id= 201, keysize= 0,
flags= 0xC
18:05:33: IPSEC(create_sa): sa created,
(sa) sa_dest= 209.165.202.226, sa_prot= 50,
sa_spi= 0x800022D3(2147492563),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 200
18:05:33: IPSEC(create_sa): sa created,
(sa) sa_dest= 209.165.202.129, sa_prot= 50,
sa_spi= 0x88688F28(2288553768),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 201
18:05:34: ISAKMP (0:1): received packet
from 209.165.202.129 (R) QM_IDLE
18:05:34: ISAKMP (0:1): phase 2 packet is a duplicate
of a previous packet.
18:05:34: ISAKMP (0:1): retransmitting due to retransmit phase 2
18:05:34: ISAKMP (0:1): ignoring retransmission, because phase2
node marked dead -1335371103
18:05:34: ISAKMP (0:1): received packet
from 209.165.202.129 (R) QM_IDLE
18:05:34: ISAKMP (0:1): phase 2 packet is a duplicate
of a previous packet.
18:05:34: ISAKMP (0:1): retransmitting due to retransmit phase 2
18:05:34: ISAKMP (0:1): ignoring retransmission, because phase2
node marked dead -1335371103
sv1-6#show crypto isakmp sa
dst src state conn-id slot
209.165.202.226 209.165.202.129 QM_IDLE 1 0
sv1-6#show crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: aptmap, local addr. 209.165.202.226
local ident (addr/mask/prot/port): (172.16.15.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0)
current_peer: 209.165.202.129
PERMIT, flags={origin_is_acl,}
#pkts encaps: 21, #pkts encrypt: 21, #pkts digest 21
#pkts decaps: 24, #pkts decrypt: 24, #pkts verify 24
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 209.165.202.226, remote crypto endpt.: 209.165.202.129
path mtu 1500, media mtu 1500
current outbound spi: 88688F28
inbound esp sas:
spi: 0x800022D3(2147492563)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 200, flow_id: 1, crypto map: aptmap
sa timing: remaining key lifetime (k/sec): (4607997/3559)
IV size: 8 bytes
replay detection support: Y
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x88688F28(2288553768)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 201, flow_id: 2, crypto map: aptmap
sa timing: remaining key lifetime (k/sec): (4607997/3550)
IV size: 8 bytes
replay detection support: Y
outbound ah sas:
outbound pcp sas:
sv1-6#show crypto engine conn act
ID Interface IP- Address State Algorithm Encrypt Decrypt
1 Ethernet0/0 209.165.202.226 set HMAC_MD5+3DES_56_C 0 0
200 Ethernet0/0 209.165.202.226 set HMAC_MD5+3DES_56_C 0 24
201 Ethernet0/0 209.165.202.226 set HMAC_MD5+3DES_56_C 21 0
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
14-Jan-2008 |
初始版本 |
 意見
意見