配置、驗證Firepower裝置註冊並排除故障
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
目錄
簡介
本檔案說明Firepower威脅防禦(FTD)與Firepower管理中心(FMC)之間連線的疑難排解程式。
必要條件
需求
本文件沒有特定需求。
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- FTD軟體6.6.x和6.5.x
- FMC軟體6.6.x
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
背景資訊
本檔案介紹受管理FTD和受管理FMC之間的連線(sftunnel)的作業、驗證和疑難排解程式。
資訊和示例基於FTD,但大多數概念也完全適用於NGIPS(7000/8000系列裝置)或ASA55xx上的FirePOWER模組。
FTD支援兩種主要管理模式:
- 透過FMC進行開箱即用-也稱為遠端管理
- 透過Firepower裝置管理器(FDM)和/或Cisco Defense Orchestrator (CDO)進行開箱即用-也稱為本地管理
在遠端管理的情況下,FTD需要先使用稱為裝置註冊的程式註冊到FMC。
完成註冊後,FTD和FMC會建立一個稱為sftunnel(名稱從Sourcefire隧道派生)的安全隧道。
設計選項
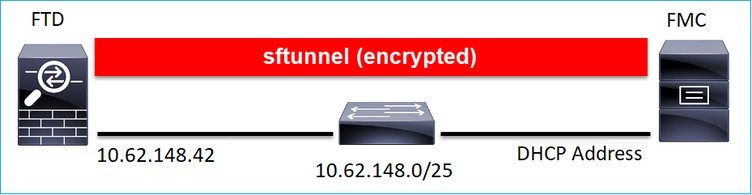
從設計的角度來看,FTD - FMC可以位於相同的L3子網路中:
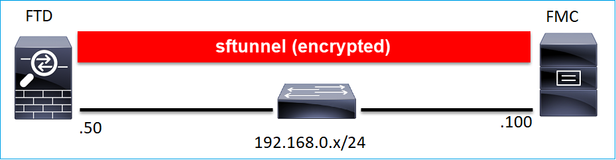
或由不同的網路分隔:
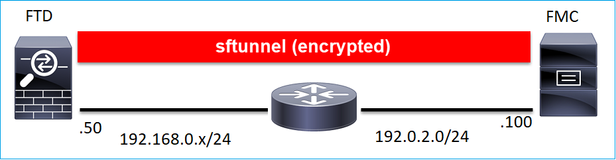
192.0.2.0
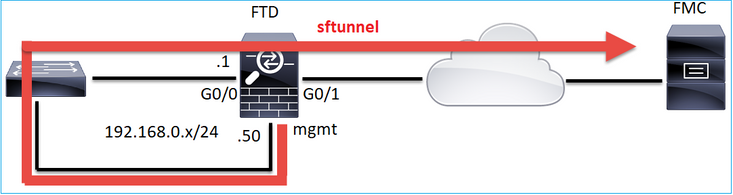
附註: sftunnel也可以透過FTD本身。不建議採用這種設計。原因是FTD資料平面問題可能會中斷FTD和FMC之間的通訊。
透過sftunnel交換什麼資訊?
此清單包含透過sftunnel傳輸的大部分資訊:
- 裝置心跳(keepalive)
- 時間同步(NTP)
- 事件(連線、入侵/IPS、檔案、SSL等)
- 惡意軟體查詢
- 健康事件/警示
- 使用者和組資訊(用於身份策略)
- FTD HA狀態資訊
- FTD叢集狀態資訊
- 安全智慧(SI)資訊/事件
- 威脅情報導向器(TID)資訊/事件
- 捕獲的檔案
- 網路發現事件
- 策略捆綁包(策略部署)
- 軟體升級套件
- 軟體修補套件
- VDB
- SRU
sftunnel使用什麼協定/埠?
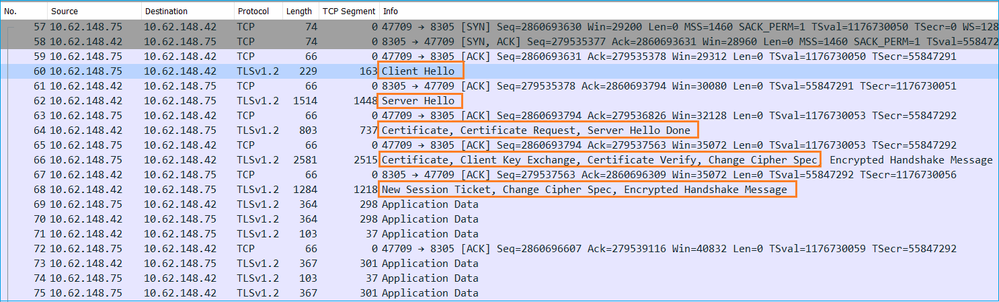
Sftunnel使用TCP埠8305。後端是TLS隧道:
如何變更FTD上的Sftunnel TCP連線埠?
> configure network management-port 8306 Management port changed to 8306.
注意:在這種情況下,還必須更改FMC上的埠(配置>管理介面>共用設定)。這會影響已註冊到同一FMC的所有其他裝置。思科強烈建議您保留遠端管理埠的預設設定,但如果管理埠與網路中的其他通訊衝突,則可以選擇其他埠。如果更改管理埠,則必須為部署中需要相互通訊的所有裝置更改管理埠。
sftunnel建立了多少個連線?
Sftunnel建立2個連線(通道):
- 控制通道
- 事件頻道
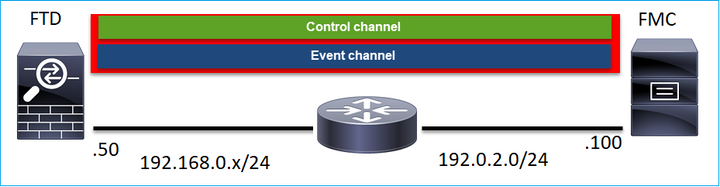
哪個裝置啟動每個通道?
這要看情況。檢查檔案中其餘部分的情境描述。
設定
註冊基礎知識
FTD CLI
在FTD上,裝置註冊的基本語法為:
> configure manager add <FMC Host> <Registration Key> <NAT ID>
| 價值 | 說明 |
| FMC主機 | 這可以是:
|
| 註冊金鑰 | 這是用於裝置註冊的共用金鑰字母數字字串(介於2到36個字元之間)。只允許使用字母數字字元、連字元(-)、下劃線(_)和句點(.)。 |
| NAT ID | 在FMC和裝置之間的註冊過程中使用的字母數字字串,當一端未指定IP地址時。在FMC上指定相同的NAT ID。 |
有關其他詳細資訊,請檢視Cisco Firepower威脅防禦命令參考
FMC UI
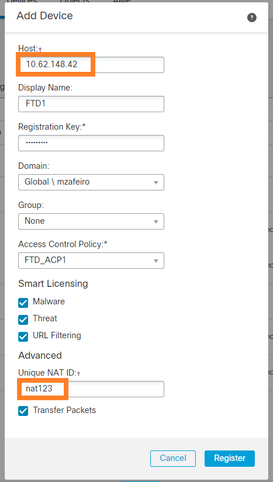
在FMC上,導航到裝置>裝置管理。選擇Add > Device
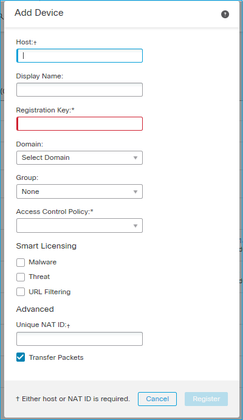
- 在「主機」中指定FTD IP位址。
- 在「顯示名稱」中指定您想要的任何內容。
- 註冊金鑰必須與FTD CLI中指定的金鑰相符。
- 如果您使用多個網域,請指定您要在其下新增FTD的網域。
- 在「群組」中,指定您要新增FTD的「裝置群組」。
- 在「存取控制原則」中,指定您要在FTD上部署的安全原則。
- 智慧許可:指定配置功能所需的許可證。
- NAT ID:本文檔後面介紹的特定場景中需要。
有關其他詳細資訊,請檢視《Firepower管理中心配置指南》,向Firepower管理中心增加裝置
案例 1.FMC和FTD靜態IP位址
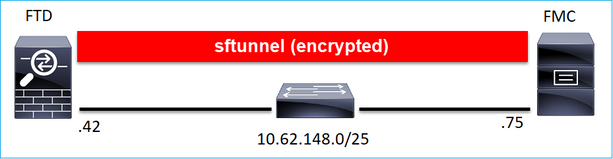
FTD CLI
> configure manager add <FMC Static IP> <Registration Key>
舉例來說:
> configure manager add 10.62.148.75 Cisco-123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
背景資訊
輸入FTD指令後,FTD會每20秒嘗試連線到FMC,但由於尚未設定FMC,因此它會使用TCP RST回覆:
> capture-traffic Please choose domain to capture traffic from: 0 - eth0 1 - Global Selection? 0 Please specify tcpdump options desired. (or enter '?' for a list of supported options) Options: -n host 10.62.148.75 HS_PACKET_BUFFER_SIZE is set to 4. tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 18:53:33.365513 IP 10.62.148.42.46946 > 10.62.148.75.8305: Flags [S], seq 2274592861, win 29200, options [mss 1460,sackOK,TS val 55808298 ecr 0,nop,wscale 7], length 0 18:53:33.365698 IP 10.62.148.75.8305 > 10.62.148.42.46946: Flags [R.], seq 0, ack 2274592862, win 0, length 0 18:53:53.365973 IP 10.62.148.42.57607 > 10.62.148.75.8305: Flags [S], seq 1267517632, win 29200, options [mss 1460,sackOK,TS val 55810298 ecr 0,nop,wscale 7], length 0 18:53:53.366193 IP 10.62.148.75.8305 > 10.62.148.42.57607: Flags [R.], seq 0, ack 1267517633, win 0, length 0 18:54:13.366383 IP 10.62.148.42.55484 > 10.62.148.75.8305: Flags [S], seq 4285875151, win 29200, options [mss 1460,sackOK,TS val 55812298 ecr 0,nop,wscale 7], length 0 18:54:13.368805 IP 10.62.148.75.8305 > 10.62.148.42.55484: Flags [R.], seq 0, ack 4285875152, win 0, length 0
裝置註冊狀態:
> show managers Host : 10.62.148.75 Registration Key : **** Registration : pending RPC Status : Type : Manager Host : 10.62.148.75 Registration : Pending
FTD監聽連線埠TCP 8305:
admin@vFTD66:~$ netstat -na | grep 8305 tcp 0 0 10.62.148.42:8305 0.0.0.0:* LISTEN
FMC UI
在這種情況下,請指定:
- 主機(FTD的IP位址)
- 顯示名稱
- 註冊金鑰(必須與FTD上設定的金鑰相符)
- 存取控制原則
- 網域
- 智慧許可資訊
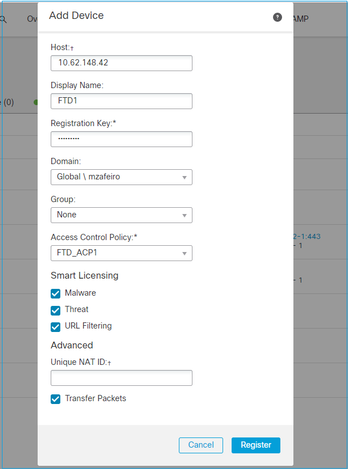
選擇註冊
註冊過程開始:
FMC開始偵聽埠TCP 8305:
admin@FMC2000-2:~$ netstat -na | grep 8305 tcp 0 0 10.62.148.75:8305 0.0.0.0:* LISTEN
FMC在後台啟動TCP連線:
20:15:55.437434 IP 10.62.148.42.49396 > 10.62.148.75.8305: Flags [S], seq 655146775, win 29200, options [mss 1460,sackOK,TS val 56302505 ecr 0,nop,wscale 7], length 0 20:15:55.437685 IP 10.62.148.75.8305 > 10.62.148.42.49396: Flags [R.], seq 0, ack 655146776, win 0, length 0 20:16:00.463637 ARP, Request who-has 10.62.148.42 tell 10.62.148.75, length 46 20:16:00.463655 ARP, Reply 10.62.148.42 is-at 00:50:56:85:7b:1f, length 28 20:16:08.342057 IP 10.62.148.75.50693 > 10.62.148.42.8305: Flags [S], seq 2704366385, win 29200, options [mss 1460,sackOK,TS val 1181294721 ecr 0,nop,wscale 7], length 0 20:16:08.342144 IP 10.62.148.42.8305 > 10.62.148.75.50693: Flags [S.], seq 1829769842, ack 2704366386, win 28960, options [mss 1460,sackOK,TS val 56303795 ecr 1181294721,nop,wscale 7], length 0 20:16:08.342322 IP 10.62.148.75.50693 > 10.62.148.42.8305: Flags [.], ack 1, win 229, options [nop,nop,TS val 1181294722 ecr 56303795], length 0 20:16:08.342919 IP 10.62.148.75.50693 > 10.62.148.42.8305: Flags [P.], seq 1:164, ack 1, win 229, options [nop,nop,TS val 1181294722 ecr 56303795], length 163 20:16:08.342953 IP 10.62.148.42.8305 > 10.62.148.75.50693: Flags [.], ack 164, win 235, options [nop,nop,TS val 56303795 ecr 1181294722], length 0
已建立sftunnel Control channel:
admin@FMC2000-2:~$ netstat -na | grep 8305 tcp 0 0 10.62.148.75:8305 0.0.0.0:* LISTEN tcp 0 0 10.62.148.75:50693 10.62.148.42:8305 ESTABLISHED
> sftunnel-status
SFTUNNEL Start Time: Sat Apr 18 20:14:20 2020
Both IPv4 and IPv6 connectivity is supported
Broadcast count = 4
Reserved SSL connections: 0
Management Interfaces: 1
eth0 (control events) 10.62.148.42,
***********************
**RUN STATUS****ksec-fs2k-2-mgmt.cisco.com*************
Cipher used = AES256-GCM-SHA384 (strength:256 bits)
ChannelA Connected: Yes, Interface eth0
ChannelB Connected: No
Registration: Completed.
IPv4 Connection to peer '10.62.148.75' Start Time: Sat Apr 18 20:16:08 2020
PEER INFO:
sw_version 6.6.0
sw_build 90
Management Interfaces: 1
eth0 (control events) 10.62.148.75,
Peer channel Channel-A is valid type (CONTROL), using 'eth0', connected to '10.62.148.75' via '10.62.148.42'
Peer channel Channel-B is not valid
幾分鐘後,事件通道即建立。事件通道的發起者可以是任一端。在本示例中,它是FMC:
20:21:15.347587 IP 10.62.148.75.43957 > 10.62.148.42.8305: Flags [S], seq 3414498581, win 29200, options [mss 1460,sackOK,TS val 1181601702 ecr 0,nop,wscale 7], length 0 20:21:15.347660 IP 10.62.148.42.8305 > 10.62.148.75.43957: Flags [S.], seq 2735864611, ack 3414498582, win 28960, options [mss 1460,sackOK,TS val 56334496 ecr 1181601702,nop,wscale 7], length 0 20:21:15.347825 IP 10.62.148.75.43957 > 10.62.148.42.8305: Flags [.], ack 1, win 229, options [nop,nop,TS val 1181601703 ecr 56334496], length 0 20:21:15.348415 IP 10.62.148.75.43957 > 10.62.148.42.8305: Flags [P.], seq 1:164, ack 1, win 229, options [nop,nop,TS val 1181601703 ecr 56334496], length 163
隨機源埠表示連線啟動器:
admin@FMC2000-2:~$ netstat -na | grep 10.62.148.42 tcp 0 0 10.62.148.75:50693 10.62.148.42:8305 ESTABLISHED tcp 0 0 10.62.148.75:43957 10.62.148.42:8305 ESTABLISHED
如果Event channel由FTD啟動,則輸出為:
admin@FMC2000-2:~$ netstat -na | grep 10.62.148.42 tcp 0 0 10.62.148.75:58409 10.62.148.42:8305 ESTABLISHED tcp 0 0 10.62.148.75:8305 10.62.148.42:46167 ESTABLISHED
從FTD端:
> sftunnel-status
SFTUNNEL Start Time: Sat Apr 18 20:14:20 2020
Both IPv4 and IPv6 connectivity is supported
Broadcast count = 6
Reserved SSL connections: 0
Management Interfaces: 1
eth0 (control events) 10.62.148.42,
***********************
**RUN STATUS****ksec-fs2k-2-mgmt.cisco.com*************
Cipher used = AES256-GCM-SHA384 (strength:256 bits)
ChannelA Connected: Yes, Interface eth0
Cipher used = AES256-GCM-SHA384 (strength:256 bits)
ChannelB Connected: Yes, Interface eth0
Registration: Completed.
IPv4 Connection to peer '10.62.148.75' Start Time: Sat Apr 18 20:16:08 2020
PEER INFO:
sw_version 6.6.0
sw_build 90
Management Interfaces: 1
eth0 (control events) 10.62.148.75,
Peer channel Channel-A is valid type (CONTROL), using 'eth0', connected to '10.62.148.75' via '10.62.148.42'
Peer channel Channel-B is valid type (EVENT), using 'eth0', connected to '10.62.148.75' via '10.62.148.42'
> show managers Type : Manager Host : 10.62.148.75 Registration : Completed >
案例 2.FTD DHCP IP位址- FMC靜態IP位址
在此案例中,FTD管理介面從DHCP伺服器取得其IP位址:
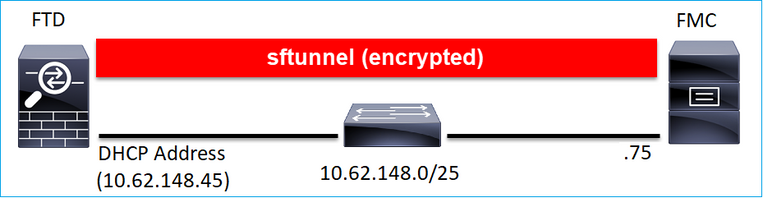
FTD CLI
您必須指定NAT ID:
> configure manager add <FMC Static IP> <Registration Key> <NAT ID>
舉例來說:
> configure manager add 10.62.148.75 Cisco-123 nat123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC. >
FTD註冊狀態:
> show managers Host : 10.62.148.75 Registration Key : **** Registration : pending RPC Status : Type : Manager Host : 10.62.148.75 Registration : Pending
FMC UI
在這種情況下,請指定:
- 顯示名稱
- 註冊金鑰(必須與FTD上設定的金鑰相符)
- 存取控制原則
- 網域
- 智慧許可資訊
- NAT ID(未指定主機時需要此ID。它必須與FTD上設定的專案相符)
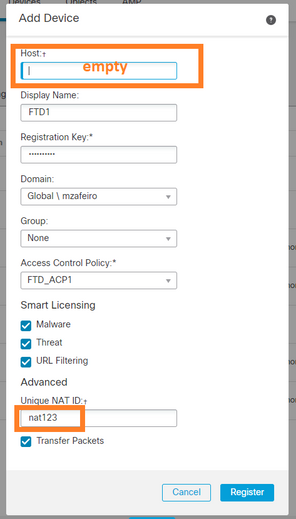
在這種情況下,誰啟動sftunnel?
FTD會起始兩個通道連線:
ftd1:/home/admin# netstat -an | grep 148.75 tcp 0 0 10.62.148.45:40273 10.62.148.75:8305 ESTABLISHED tcp 0 0 10.62.148.45:39673 10.62.148.75:8305 ESTABLISHED
案例 3.FTD靜態IP位址- FMC DHCP IP位址
> configure manager add DONTRESOLVE Cisco-123 nat123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC. >
注意:使用DONTRESOLVE時需要NAT ID。
FMC UI
在這種情況下,請指定:
- FTD IP位址
- 顯示名稱
- 註冊金鑰(必須與FTD上設定的金鑰相符)
- 存取控制原則
- 網域
- 智慧許可資訊
- NAT ID(必須與FTD上設定的ID相符)
完成註冊後的FTD:
> show managers Type : Manager Host : 5a8454ea-8273-11ea-a7d3-d07d71db8f19DONTRESOLVE Registration : Completed
在這種情況下,誰啟動sftunnel?
- FMC啟動控制通道。
- 事件通道可由任一端啟動。
root@FMC2000-2:/Volume/home/admin# netstat -an | grep 148.42 tcp 0 0 10.62.148.75:50465 10.62.148.42:8305 ESTABLISHED tcp 0 0 10.62.148.75:48445 10.62.148.42:8305 ESTABLISHED
案例 4.FTD註冊FMC HA
在FTD上,僅設定作用中FMC:
> configure manager add 10.62.184.22 cisco123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
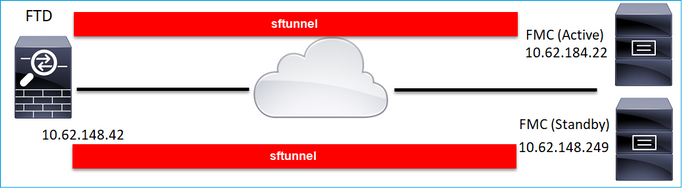
注意:確保TCP埠8305流量允許從FTD傳送到兩個FMC。
首先,建立到活動FMC的sftunnel:
> show managers Type : Manager Host : 10.62.184.22 Registration : Completed
幾分鐘後,FTD開始註冊到待命FMC:
> show managers Type : Manager Host : 10.62.184.22 Registration : Completed Type : Manager Host : 10.62.148.249 Registration : Completed
在FTD後端中,已建立2個控制通道(每個FMC一個)和2個事件通道(每個FMC一個):
ftd1:/home/admin# netstat -an | grep 8305 tcp 0 0 10.62.148.42:8305 10.62.184.22:36975 ESTABLISHED tcp 0 0 10.62.148.42:42197 10.62.184.22:8305 ESTABLISHED tcp 0 0 10.62.148.42:8305 10.62.148.249:45373 ESTABLISHED tcp 0 0 10.62.148.42:8305 10.62.148.249:51893 ESTABLISHED
案例 5.FTD高可用性
在FTD HA的情況下,每個單元都有連線到FMC的獨立通道:
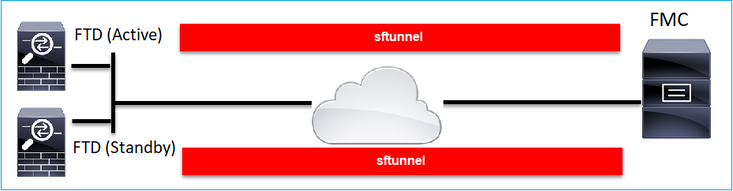
您分別註冊兩個FTD,然後從FMC建立FTD HA。如需詳細資訊,請檢查:
案例 6.FTD叢集
在FTD叢集的情況下,每個單元都有一個連線到FMC的單獨通道。從6.3 FMC版本開始,您只需要將FTD控制單元註冊到FMC。然後FMC處理其餘裝置,並自動發現+註冊它們。
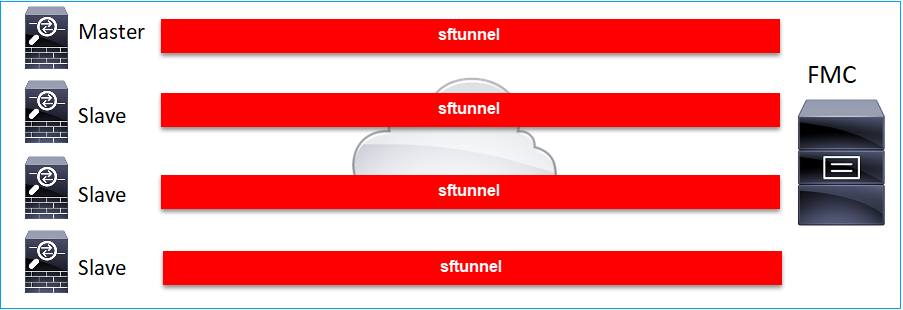
註:我們建議增加控制單元以獲得最佳效能,但您可以增加集群的任何單元。有關其他詳細資訊,請檢查:建立Firepower威脅防禦集群
排除常見問題
1. FTD CLI上的語法無效
如果FTD上的語法無效,且註冊嘗試失敗,則FMC UI會顯示非常一般的錯誤訊息:
在此命令中,關鍵字key是註冊金鑰,而cisco123是NAT ID。增加關鍵字鍵是相當常見的,而技術上並沒有這樣的關鍵字:
> configure manager add 10.62.148.75 key cisco123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
建議的動作
請使用正確的語法,並且不要使用不存在的關鍵字。
> configure manager add 10.62.148.75 cisco123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
2. FTD - FMC之間的註冊金鑰不符
FMC UI顯示:
建議的動作
在FTD上,檢查/ngfw/var/log/messages檔案以瞭解驗證問題。
方法1 -檢查過去的日誌
> system support view-files Type a sub-dir name to list its contents: s Type the name of the file to view ([b] to go back, [Ctrl+C] to exit) > messages Apr 19 04:02:05 vFTD66 syslog-ng[1440]: Configuration reload request received, reloading configuration; Apr 19 04:02:07 vFTD66 SF-IMS[3116]: [3116] pm:control [INFO] ControlHandler auditing message->type 0x9017, from '', cmd '/ngf w/usr/bin/perl /ngfw/usr/local/sf/bin/run_hm.pl --persistent', pid 19455 (uid 0, gid 0) /authenticate Apr 19 20:17:14 vFTD66 SF-IMS[18974]: [19131] sftunneld:sf_ssl [WARN] Accept: Failed to authenticate peer '10.62.148.75' <- The problem
方法2 -檢查即時日誌
> expert ftd1:~$ sudo su Password: ftd1::/home/admin# tail -f /ngfw/var/log/messages
在FTD上,檢查/etc/sf/sftunnel.conf檔案的內容,以確保註冊金鑰正確:
ftd1:~$ cat /etc/sf/sftunnel.conf | grep reg_key
reg_key cisco-123;
3. FTD - FMC之間的連線問題
FMC UI顯示:
建議的動作
- 確保路徑中沒有阻止流量的裝置(例如防火牆) (TCP 8305)。就FMC HA而言,請確保允許到TCP連線埠8305的流量流向兩個FMC。
- 進行捕獲以驗證雙向通訊。在FTD上,使用capture-traffic 命令。確儲存在TCP三次握手,並且沒有TCP FIN或RST資料包。
> capture-traffic Please choose domain to capture traffic from: 0 - eth0 1 - Global Selection? 0 Please specify tcpdump options desired. (or enter '?' for a list of supported options) Options: -n host 10.62.148.75 HS_PACKET_BUFFER_SIZE is set to 4. tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 20:56:09.393655 IP 10.62.148.42.53198 > 10.62.148.75.8305: Flags [S], seq 3349394953, win 29200, options [mss 1460,sackOK,TS val 1033596 ecr 0,nop,wscale 7], length 0 20:56:09.393877 IP 10.62.148.75.8305 > 10.62.148.42.53198: Flags [R.], seq 0, ack 3349394954, win 0, length 0 20:56:14.397412 ARP, Request who-has 10.62.148.75 tell 10.62.148.42, length 28 20:56:14.397602 ARP, Reply 10.62.148.75 is-at a4:6c:2a:9e:ea:10, length 46
同樣,在FMC上進行捕獲以確保雙向通訊:
root@FMC2000-2:/var/common# tcpdump -i eth0 host 10.62.148.42 -n -w sftunnel.pcap
還建議以pcap格式導出捕獲並檢查資料包內容:
ftd1:/home/admin# tcpdump -i eth0 host 10.62.148.75 -n -w tunnel.pcap HS_PACKET_BUFFER_SIZE is set to 4. tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
可能原因:
- FMC未新增FTD裝置。
- 路徑中的裝置(例如防火牆)會封鎖或修改流量。
- 路徑中的封包未正確路由。
- FTD或FMC上的Sftunnel程式關閉(檢查案例6)
- 路徑中存在MTU問題(檢查案例)。
對於擷取分析,請檢查此檔案:
分析 Firepower 防火牆擷取,以有效針對網路問題進行疑難排解
4. FTD - FMC之間不相容的軟體
FMC UI顯示:
建議的動作
檢查FTD /ngfw/var/log/messages檔案:
Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_connections [INFO] Need to send SW version and Published Services to 10.62.148.247 Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_channel [INFO] >> ChannelState do_dataio_for_heartbeat peer 10.62.148.247 / channelA / CONTROL [ msgSock & ssl_context ] << Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_heartbeat [INFO] Saved SW VERSION from peer 10.62.148.247 (10.10.0.4) Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:ssl_mac [WARN] FMC(manager) 10.62.148.247 send unsupported version 10.10.0.4 Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_connections [INFO] <<<<<<<<<<<<<<<<<<<<<< ShutDownPeer 10.62.148.247 >>>>>>>>>>>>>>>>>>>>>>>> Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:stream_file [INFO] Stream CTX destroyed for 10.62.148.247 Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_channel [INFO] >> ChannelState ShutDownPeer peer 10.62.148.247 / channelA / CONTROL [ msgSock & ssl_context ] <<
檢視Firepower相容性清單:
5. FTD和FMC之間的時間差異
FTD-FMC通訊對兩個裝置之間的時間差異很敏感。要求同一NTP伺服器同步FTD和FMC。
具體而言,當FTD安裝在41xx或93xx等平台上時,會從父機箱(FXOS)進行時間設定。
建議的動作
確保機箱管理器(FCM)和FMC使用同一時間源(NTP伺服器)
6. sftunnel進程關閉或停用
在FTD上,sftunnel 程式處理註冊程式。這是管理員配置前的進程狀態:
> pmtool status … sftunnel (system) - Waiting Command: /ngfw/usr/local/sf/bin/sftunnel -d -f /etc/sf/sftunnel.conf PID File: /ngfw/var/sf/run/sftunnel.pid Enable File: /ngfw/etc/sf/sftunnel.conf CPU Affinity: Priority: 0 Next start: Mon Apr 20 06:12:06 2020 Required by: sfmgr,sfmbservice,sfipproxy CGroups: memory=System/ProcessHigh
註冊狀態:
> show managers No managers configured.
設定管理員:
> configure manager add 10.62.148.75 cisco123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
現在流程已啟動:
> pmtool status … sftunnel (system) - Running 24386 Command: /ngfw/usr/local/sf/bin/sftunnel -d -f /etc/sf/sftunnel.conf PID File: /ngfw/var/sf/run/sftunnel.pid Enable File: /ngfw/etc/sf/sftunnel.conf CPU Affinity: Priority: 0 Next start: Mon Apr 20 07:12:35 2020 Required by: sfmgr,sfmbservice,sfipproxy CGroups: memory=System/ProcessHigh(enrolled)
在極少數情況下,進程可能關閉或停用:
> pmtool status … sftunnel (system) - User Disabled Command: /ngfw/usr/local/sf/bin/sftunnel -d -f /etc/sf/sftunnel.conf PID File: /ngfw/var/sf/run/sftunnel.pid Enable File: /ngfw/etc/sf/sftunnel.conf CPU Affinity: Priority: 0 Next start: Mon Apr 20 07:09:46 2020 Required by: sfmgr,sfmbservice,sfipproxy CGroups: memory=System/ProcessHigh
管理員狀態看起來正常:
> show managers Host : 10.62.148.75 Registration Key : **** Registration : pending RPC Status :
另一方面,裝置註冊失敗:
在FTD上,/ngfw/var/log/messages中看不到相關訊息
建議的動作
收集FTD疑難排解檔案,並連絡思科TAC
7. FTD暫緩於次要FMC註冊
某些情況下,在初始FTD註冊到FMC HA設定後,FTD裝置不會新增到次要FMC。
建議的動作
請使用本文檔中介紹的步驟:
使用CLI解決Firepower管理中心高可用性中的裝置註冊
警告:此過程是強制型的,因為它包含裝置取消註冊。這會影響FTD裝置組態(已刪除)。建議僅在初始FTD註冊和設定期間使用此程式。在不同案例中,收集FTD和FMC疑難排解檔案並連絡思科TAC。
8. 由於路徑MTU,註冊失敗
在Cisco TAC中可以看到,sftunnel流量必須透過具有小MTU的鏈路傳輸的情況。Sftunnel資料包具有不分段位設定,因此不允許分段:
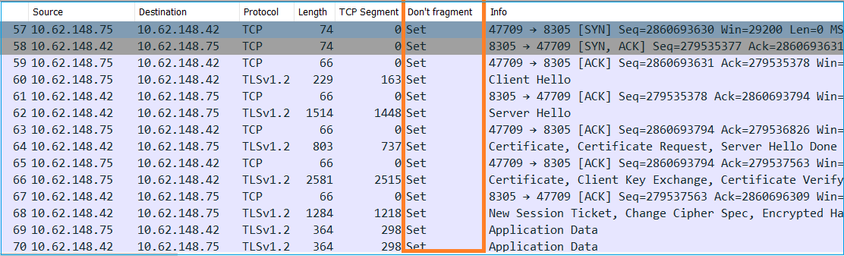
此外,在/ngfw/var/log/messages檔案中,您可以看到如下消息:
消息: 10-09 14:41:11 ftd1 SF-IMS[7428]: [6612] sftunneld:sf_ssl [ERROR] Connect:SSL握手失敗
建議的動作
要驗證是否存在由於分段而導致的資料包丟失,請捕獲FTD、FMC和路徑中的理想裝置。檢查是否看到兩端都到達的資料包。
在FTD上,降低FTD管理介面的MTU。預設值為1500位元組。管理介面的最大值為1500,事件介面的最大值為9000。FTD 6.6版本中已增加該命令。
範例
> configure network mtu 1300 MTU set successfully to 1300 from 1500 for eth0 Refreshing Network Config... Interface eth0 speed is set to '10000baseT/Full'
驗證
> show network ===============[ System Information ]=============== Hostname : ksec-sfvm-kali-3.cisco.com DNS Servers : 192.168.200.100 Management port : 8305 IPv4 Default route Gateway : 10.62.148.1 Netmask : 0.0.0.0 ======================[ eth0 ]====================== State : Enabled Link : Up Channels : Management & Events Mode : Non-Autonegotiation MDI/MDIX : Auto/MDIX MTU : 1300 MAC Address : 00:50:56:85:7B:1F ----------------------[ IPv4 ]---------------------- Configuration : Manual Address : 10.62.148.42 Netmask : 255.255.255.128 Gateway : 10.62.148.1 ----------------------[ IPv6 ]----------------------
若要驗證來自FTD的路徑MTU,您可以使用以下命令:
root@firepower:/home/admin# ping -M do -s 1472 10.62.148.75
do 選項設定ICMP資料包中的不分段位。此外,當您指定1472時,裝置會傳送1500位元組:(IP標頭= 20位元組) +(ICMP標頭= 8位元組) + (1472位元組ICMP資料)
在FMC上,按本文檔所述降低FMC管理介面上的MTU值:
9. 從機箱管理器UI更改載入程式後,FTD將取消註冊
這適用於FP41xx和FP93xx平台,並且已記錄在思科漏洞ID CSCvn45138中 。
。
一般而言,除非執行災難恢復,否則不能從機箱管理器(FCM)進行載入程式更改。
建議的動作
如果進行了引導更改並且匹配了條件(FTD-FMC通訊中斷,而FTD在引導更改後啟動),則必須刪除並重新向FMC註冊FTD。
10. 由於ICMP重新導向訊息,FTD失去存取FMC的許可權
此問題可能影響註冊程式,或在註冊後中斷FTD-FMC通訊。
在這種情況下,問題是網路裝置將ICMP重新導向訊息傳送到FTD管理介面和黑洞FTD-FMC通訊。
如何辨識此問題
在本例中,10.100.1.1是FMC IP地址。在FTD上,由於FTD在管理介面上收到的ICMP重新導向訊息,存在快取的路由:
ftd1:/ngfw/var/common# ip route get 10.100.1.1
10.100.1.1 via 10.10.1.1 dev br1 src 10.10.1.23
cache <redirected>
建議的動作
步驟 1
在傳送重定向消息的裝置(例如,上游L3交換機、路由器等)上停用ICMP重定向。
步驟 2
從FTD CLI清除FTD路由快取:
ftd1:/ngfw/var/common# ip route flush 10.100.1.1
如果未重新導向,則顯示如下:
ftd1:/ngfw/var/common# ip route get 10.100.1.1
10.100.1.1 via 10.62.148.1 dev eth0 src 10.10.1.23
cache mtu 1500 advmss 1460 hoplimit 64
參考資料
- 瞭解ICMP重定向消息
- 思科漏洞ID CSCvm53282 FTD:由ICMP重定向增加的路由表將永久卡在路由表快取中
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
3.0 |
14-Aug-2023 |
已更新參與者清單。 |
2.0 |
19-Jul-2022 |
本文已針對格式化、機器翻譯、德語、SEO、樣式要求等進行更新,以符合當前思科指南。 |
1.0 |
20-May-2020 |
初始版本 |
由思科工程師貢獻
- Mikis ZafeiroudisCisco TAC Engineer
- Ilkin GasimovCisco TAC Engineer
 意見
意見