Introdução
Este documento descreve como testar a conectividade de estrutura entre dois Virtual Tunnel End Points (VTEPs) em Virtual Extensible LAN (VxLAN).
Pré-requisitos
Requisitos
A Cisco recomenda que você tenha conhecimento destes tópicos:
- Software NX-OS Nexus
- Protocolo de gateway de borda (BGP)
- VxLAN
Componentes Utilizados
As informações neste documento são baseadas no Cisco Nexus N9K-C93180YC-EX com NXOS versão 10.3(3).
As informações neste documento foram criadas a partir de dispositivos em um ambiente de laboratório específico. Todos os dispositivos utilizados neste documento foram iniciados com uma configuração (padrão) inicial. Se a rede estiver ativa, certifique-se de que você entenda o impacto potencial de qualquer comando.
Configurar
Depois que a VxLAN estiver configurada, os usuários normalmente querem testar se ela funciona como esperado. Embora a maneira recomendada de fazer isso seja fazer um teste de ping entre dois hosts finais, que estão conectados a VTEPs diferentes, também é possível testar a conectividade da estrutura usando interfaces de loopback nos VTEPs.

Observação: usar a interface virtual do switch (SVI) como origem ou destino do teste de ping não é um teste válido para conectividade de estrutura. O motivo é que temos o mesmo IP em SVIs de estrutura devido ao recurso de gateway Anycast.
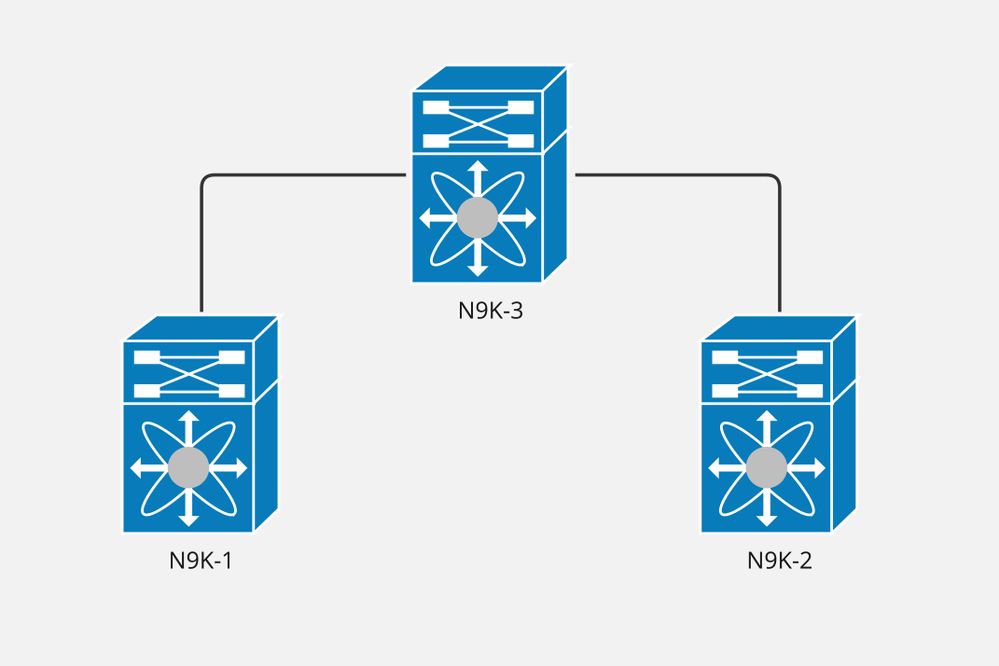
Diagrama de Rede
Configurações
O Nexus N9K-2 está configurado como SPINE, enquanto o N9K-1 e o N9K-2 estão configurados como VTEPs nesta implantação de VxLAN.
A camada 3 é estendida, portanto temos uma interface de rede virtual (VNI) da camada 3 em ambos os VTEPs para cada Virtual Routing and Forwarding (VRF).
O VNI da camada 3 configurado para VRF evpn_a é 50100.
N9K-1
Etapa 1. Configuramos um loopback como parte do VRF que queremos testar.
N9K-1(config)# interface loopback50
N9K-1(config-if)# vrf member evpn_a
Message reported by command :: vrf member evpn_a
Warning: Deleted all L3 config on interface loopback50
N9K-1(config-if)# ip address 10.255.255.1/32
Etapa 2. Anunciamos esse loopback na malha. Caso contrário, mesmo que a solicitação ICMP chegue ao destino, o próprio destino não poderá enviar de volta a resposta ICMP.
N9K-1(config)# router bgp 65522
N9K-1(config-router)# vrf evpn_a
N9K-1(config-router-vrf)# address-family ipv4 unicast
N9K-1(config-router-vrf-af)# network 10.255.255.1/32
N9K-2
Etapa 1. Configuramos um loopback como parte do VRF que queremos testar.
N9K-2(config)# interface loopback50
N9K-2(config-if)# vrf member evpn_a
Message reported by command :: vrf member evpn_a
Warning: Deleted all L3 config on interface loopback50
N9K-2(config-if)# ip address 10.255.255.2/32
Etapa 2. Anunciamos esse loopback na malha. Caso contrário, mesmo que a solicitação ICMP chegue ao destino, o próprio destino não poderá enviar de volta a resposta ICMP.
N9K-2(config)# router bgp 65522
N9K-2(config-router)# vrf evpn_a
N9K-2(config-router-vrf)# address-family ipv4 unicast
N9K-2(config-router-vrf-af)# network 10.255.255.2/32
Verificar
Etapa 1. Confirme se o loopback está presente na tabela BGP local para a família de endereços IPv4 Unicast.
N9K-1# show ip bgp 10.255.255.1/32 vrf evpn_a
BGP routing table information for VRF evpn_a, address family IPv4 Unicast
BGP routing table entry for 10.255.255.1/32, version 732
Paths: (1 available, best #1)
Flags: (0x80c0002) (high32 0x000020) on xmit-list, is not in urib, exported
vpn: version 1053, (0x00000000100002) on xmit-list
Multipath: eBGP iBGP
Advertised path-id 1, VPN AF advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop, is extd
AS-Path: NONE, path locally originated
0.0.0.0 (metric 0) from 0.0.0.0 (10.2.254.100)
Origin IGP, MED not set, localpref 100, weight 32768
Extcommunity: RT:65522:50100
VRF advertise information:
Path-id 1 not advertised to any peer
VPN AF advertise information:
Path-id 1 not advertised to any peer
N9K-2# show ip bgp 10.255.255.2/32 vrf evpn_a
BGP routing table information for VRF evpn_a, address family IPv4 Unicast
BGP routing table entry for 10.255.255.2/32, version 241
Paths: (1 available, best #1)
Flags: (0x80c0002) (high32 0x000020) on xmit-list, is not in urib, exported
vpn: version 417, (0x00000000100002) on xmit-list
Multipath: eBGP iBGP
Advertised path-id 1, VPN AF advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop, is extd
AS-Path: NONE, path locally originated
0.0.0.0 (metric 0) from 0.0.0.0 (10.2.254.100)
Origin IGP, MED not set, localpref 100, weight 32768
Extcommunity: RT:65522:50100
VRF advertise information:
Path-id 1 not advertised to any peer
VPN AF advertise information:
Path-id 1 not advertised to any peer
Etapa 2. Confirme se o loopback está presente na tabela de BGP local para a família de endereços L2VPN EVPN e se é anunciado para os peers de Network Virtual Interface (NVE) esperados.
N9K-1# show bgp l2vpn evpn 10.255.255.1 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.49:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.1]/224, version 36993
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn
Advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop
Gateway IP: 0.0.0.0
AS-Path: NONE, path locally originated
10.2.1.49 (metric 0) from 0.0.0.0 (10.2.0.49)
Origin IGP, MED not set, localpref 100, weight 32768
Received label 50100
Extcommunity: RT:65522:50100 ENCAP:8 Router MAC:a0e0.af67.511d
Path-id 1 advertised to peers:
10.2.0.33 10.2.0.34
N9K-2#
LEAF48# show bgp l2vpn evpn 10.255.255.2 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.48:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.2]/224, version 13373
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn
Advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop
Gateway IP: 0.0.0.0
AS-Path: NONE, path locally originated
10.2.1.48 (metric 0) from 0.0.0.0 (10.2.0.48)
Origin IGP, MED not set, localpref 100, weight 32768
Received label 50100
Extcommunity: RT:65522:50100 ENCAP:8 Router MAC:6cb2.aeee.5a97
Path-id 1 advertised to peers:
10.2.0.33 10.2.0.34
Etapa 3. Confirmação de atualização recebida do par NVE remoto.
N9K-1# show bgp l2vpn evpn 10.255.255.2 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.49:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.2]/224, version 36995
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Advertised path-id 1
Path type: internal, path is valid, is best path, no labeled nexthop
Imported from 10.2.0.48:4:[5]:[0]:[0]:[32]:[10.255.255.2]/224
Gateway IP: 0.0.0.0
AS-Path: NONE, path sourced internal to AS
10.2.1.48 (metric 6) from 10.2.0.33 (10.2.0.33)
Origin IGP, MED not set, localpref 100, weight 0
Received label 50100
Extcommunity: RT:65522:50100 Route-Import:10.2.1.147:3100 Source AS:65522:0
ENCAP:8 Router MAC:6cb2.aeee.5a97
Originator: 10.2.0.48 Cluster list: 0.0.255.242
Path-id 1 not advertised to any peer
N9K-2# show bgp l2vpn evpn 10.255.255.1 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.48:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.1]/224, version 13372
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Advertised path-id 1
Path type: internal, path is valid, is best path, no labeled nexthop
Imported from 10.2.0.49:4:[5]:[0]:[0]:[32]:[10.255.255.1]/224
Gateway IP: 0.0.0.0
AS-Path: NONE, path sourced internal to AS
10.2.1.49 (metric 6) from 10.2.0.33 (10.2.0.33)
Origin IGP, MED not set, localpref 100, weight 0
Received label 50100
Extcommunity: RT:65522:50100 Route-Import:10.2.1.49:3100 Source AS:65522:0
ENCAP:8 Router MAC:a0e0.af67.511d
Originator: 10.2.0.49 Cluster list: 0.0.255.242
Path-id 1 not advertised to any peer
Etapa 4. Confirme se há uma rota para loopback remoto na tabela de roteamento e o próximo salto é o peer NVE esperado.
N9K-1# show ip route 10.255.255.2 vrf evpn_a
IP Route Table for VRF "evpn_a"
'*' denotes best ucast next-hop
'**' denotes best mcast next-hop
'[x/y]' denotes [preference/metric]
'%
' in via output denotes VRF
10.255.255.2/32, ubest/mbest: 1/0 *via 10.2.1.48%default, [200/0], 00:12:39, bgp-65522, internal, tag 65522, segid: 50100 tunnelid: 0xa020130 encap: VXLAN N9K-2# show ip route 10.255.255.1 vrf evpn_a IP Route Table for VRF "evpn_a" '*' denotes best ucast next-hop '**' denotes best mcast next-hop '[x/y]' denotes [preference/metric] '%
' in via output denotes VRF
10.255.255.1/32, ubest/mbest: 1/0 *via 10.2.1.49%default, [200/0], 00:15:36, bgp-65522, internal, tag 65522, segid: 50100 tunnelid: 0xa020131 encap: VXLAN
Etapa 5. Enviar solicitação ICMP para loopback remoto, usando como origem o loopback local.
N9K-1# ping 10.255.255.2 source-interface loopback 50
PING 10.255.255.2 (10.255.255.2): 56 data bytes
64 bytes from 10.255.255.2: icmp_seq=0 ttl=254 time=2.009 ms
64 bytes from 10.255.255.2: icmp_seq=1 ttl=254 time=1.26 ms
64 bytes from 10.255.255.2: icmp_seq=2 ttl=254 time=1.231 ms
64 bytes from 10.255.255.2: icmp_seq=3 ttl=254 time=1.142 ms
64 bytes from 10.255.255.2: icmp_seq=4 ttl=254 time=1.127 ms
--- 10.255.255.2 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 1.127/1.353/2.009 ms
N9K-2# ping 10.255.255.1 source-interface loopback 50
PING 10.255.255.1 (10.255.255.1): 56 data bytes
64 bytes from 10.255.255.1: icmp_seq=0 ttl=254 time=1.47 ms
64 bytes from 10.255.255.1: icmp_seq=1 ttl=254 time=1.396 ms
64 bytes from 10.255.255.1: icmp_seq=2 ttl=254 time=1.327 ms
64 bytes from 10.255.255.1: icmp_seq=3 ttl=254 time=1.451 ms
64 bytes from 10.255.255.1: icmp_seq=4 ttl=254 time=1.366 ms
--- 10.255.255.1 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 1.327/1.402/1.47 ms
Informações Relacionadas
Configurando o VXLAN BGP EVPN



 Feedback
Feedback