Installatie en upgrade van Firepower Threat Defense op ASA 555x-X applicaties
Downloadopties
Inclusief taalgebruik
De documentatie van dit product is waar mogelijk geschreven met inclusief taalgebruik. Inclusief taalgebruik wordt in deze documentatie gedefinieerd als taal die geen discriminatie op basis van leeftijd, handicap, gender, etniciteit, seksuele oriëntatie, sociaaleconomische status of combinaties hiervan weerspiegelt. In deze documentatie kunnen uitzonderingen voorkomen vanwege bewoordingen die in de gebruikersinterfaces van de productsoftware zijn gecodeerd, die op het taalgebruik in de RFP-documentatie zijn gebaseerd of die worden gebruikt in een product van een externe partij waarnaar wordt verwezen. Lees meer over hoe Cisco gebruikmaakt van inclusief taalgebruik.
Over deze vertaling
Cisco heeft dit document vertaald via een combinatie van machine- en menselijke technologie om onze gebruikers wereldwijd ondersteuningscontent te bieden in hun eigen taal. Houd er rekening mee dat zelfs de beste machinevertaling niet net zo nauwkeurig is als die van een professionele vertaler. Cisco Systems, Inc. is niet aansprakelijk voor de nauwkeurigheid van deze vertalingen en raadt aan altijd het oorspronkelijke Engelstalige document (link) te raadplegen.
Inhoud
Inleiding
In dit document worden de installatie-, upgrade- en registratieprocedures van Firepower Threat Defense (FTD) op ASA 555x-X-apparatuur beschreven.
Voorwaarden
Vereisten
Er zijn geen specifieke vereisten van toepassing op dit document.
Gebruikte componenten
De informatie in dit document is gebaseerd op de volgende software- en hardware-versies:
- ASA 5508-X
- ASA 5512-X
- FireSIGHT Management Center (FMC) van 6.0.1 (gebouw 1213)
De informatie in dit document is gebaseerd op de apparaten in een specifieke laboratoriumomgeving. Alle apparaten die in dit document worden beschreven, hadden een opgeschoonde (standaard)configuratie. Als uw netwerk levend is, zorg er dan voor dat u de mogelijke impact van om het even welke opdracht begrijpt.
Achtergrondinformatie
FTD is een uniform softwarebeeld dat op deze platforms kan worden geïnstalleerd:
- ASA 5506-X, ASA 5506W-X, ASA 5506H-X, ASA 5508-X, ASA 5516-X
- ASA 5512-X, ASA 5515-X, ASA 5525-X, ASA 5545-X, ASA 5555-X, ASA 555-X
- FPR4100, FPR9300
- VMware (ESXi)
- Amazon Web Services (AWS)
- KVM
- ISR-routermodule
Het doel van dit document is het aantonen van:
- De installatie van FTD versie 6.0.0 op ASA 5508-X en ASA 5512-X platform
- De upgradeprocedure van FTD van versie 6.0.0 tot 6.0.1
- Registratie en basislicenties voor Firepower Management Center (FMC)
Configureren
Netwerkdiagram
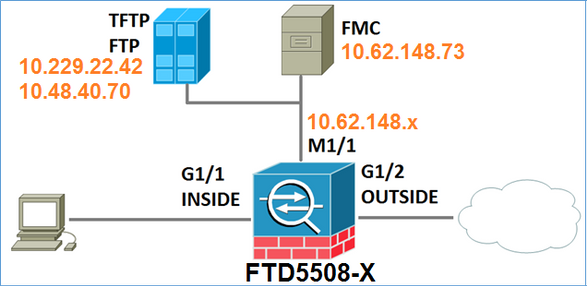
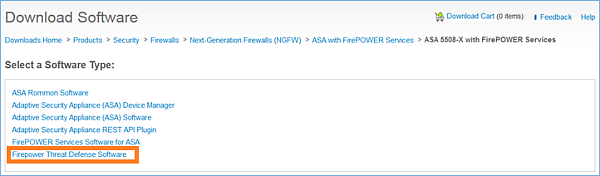
FTD Software Download
Navigatie naar Next-generation firewalls (NGFW) > ASA met FirePOWER Services > ASA 5508-X met FirePOWER Services en selecteer Firepower Threat Defense Software:
Evenzo voor de ASA 5512-X-software.
Task 1. Controleer de voorwaarden
Controleer de vereisten voordat de FTD-installatie wordt geïnstalleerd.
Oplossing:
Voor een FTD-installatie gebruikt u twee afbeeldingen:
- OS-afbeelding (AKA-opstartbeeld) - Voor FirePOWER Threat Defense op ASA 5506-X, ASA 5506H-X, ASA 5506W-X, ASA 5508-X, ASA 5516-X is een DBF-bestand. Voor Firepower Threat Defense op Saleen (ASA 5512-X, ASA 5515-X, ASA 5525-X, ASA 5545-X, ASA 5555-X, ASA 5555-X) is een schijfbestand.
- Systeemafbeelding - Dit is een .pkg-bestand.
Controleer voordat u doorgaat met de installatie van de FTD dit:
- ASA-flitser moet minimaal 3,1 GBytes (3 GBytes + grootte van bootbeeld) vrije ruimte hebben
- De opstartafbeelding wordt geüpload naar een TFTP-server
- Het systeembeeld wordt geüpload naar een HTTP- of FTP-server
- Op ASA 5506/08/16 is de ROMON tenminste 1.1.8 versie
Controleer de vrije ruimte:
FTD5508X# show flash | i free 7859437568 bytes total (4273819648 bytes free)
Controleer deze afbeeldingen:
| Bestandsnaam |
Beschrijving |
| ftd-start-9.6.1.0.lfbff |
v6.0.1. Firepower Threat Defense-opstartbeeld voor 5506/5508/5516. Dit is het opstartbeeld voor de schone installatie op 5506/5508/5516 |
| ftd-start-9.6.1.0.cdisk |
v6.0.1 Firepower Threat Defense-boogbeeld voor ASA 5512/5515/5525/5545/5555. Dit is het opstartbeeld voor de schone installatie op 5512/5515/5525/5545/5555 |
| ftd-6,0,0-1005,pkg |
v6.0.0 Firepower Threat Defense voor alle ondersteunde ASA’s: 5506/5508/5512/5515/5516/5525/5545/5555. Dit is het systeembeeld voor een schone installatie |
Task 2. upgrade van de ASA 5508-X ROMMON
Zoals het in de vereisten wordt vermeld, moeten de apparaten ASA 5506-X, ASA 5508-X en ASA 5516-X op ROMMON v1.1.8 zijn geïnstalleerd. Als u ASA 5500-firmware-1108.SPA dan niet installeert (beschikbaar in de Cisco ASA downloadpagina).
Taakvereiste:
upgrade ASA 5508-ROMMON van 1.1.1 tot 1.1.8.
Oplossing:
De procedure wordt beschreven in de ASA ROMMON-upgradegids.
Stap 1. Controleer de bestaande ROMMON-versie:
FTD5508X# show module Mod Card Type Model Serial No. ---- -------------------------------------------- ------------------ ----------- 1 ASA 5508-X with FirePOWER services, 8GE, AC, ASA5508 JAD192100SZ sfr FirePOWER Services Software Module ASA5508 JAD192100SZ Mod MAC Address Range Hw Version Fw Version Sw Version ---- --------------------------------- ------------ ------------ --------------- 1 188b.9d1e.ca7c to 188b.9d1e.ca84 1.0 1.1.1 9.5(2) sfr 188b.9d1e.ca7b to 188b.9d1e.ca7b N/A N/A 5.4.1-211
Stap 2.Download de ROMMON firmware in ASA's flitser:
FTD5508X# copy ftp://10.48.40.70/ANG/mzafeiro/asa5500-firmware-1108.SPA disk0:asa5500-firmware-1108.SPA
Address or name of remote host [10.48.40.70]?
Source filename [ANG/mzafeiro/asa5500-firmware-1108.SPA]?
Destination filename [asa5500-firmware-1108.SPA]?
Accessing ftp://10.48.40.70/ANG/mzafeiro/asa5500-firmware-1108.SPA...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Done!
Computed Hash SHA2: d824bdeecee1308fc64427367fa559e9
eefe8f182491652ee4c05e6e751f7a4f
5cdea28540cf60acde3ab9b65ff55a9f
4e0cfb84b9e2317a856580576612f4af
Embedded Hash SHA2: d824bdeecee1308fc64427367fa559e9
eefe8f182491652ee4c05e6e751f7a4f
5cdea28540cf60acde3ab9b65ff55a9f
4e0cfb84b9e2317a856580576612f4af
Digital signature successfully validated
Writing file disk0:/asa5500-firmware-1108.SPA...
!!!!!!!!!
9241408 bytes copied in 18.890 secs (513411 bytes/sec)
Stap 3. upgrade van het ASA-ROMMON-beeld:
FTD5508X# upgrade rommon disk0:asa5500-firmware-1108.SPA
Verifying file integrity of disk0:/asa5500-firmware-1108.SPA
Computed Hash SHA2: d824bdeecee1308fc64427367fa559e9
eefe8f182491652ee4c05e6e751f7a4f
5cdea28540cf60acde3ab9b65ff55a9f
4e0cfb84b9e2317a856580576612f4af
Embedded Hash SHA2: d824bdeecee1308fc64427367fa559e9
eefe8f182491652ee4c05e6e751f7a4f
5cdea28540cf60acde3ab9b65ff55a9f
4e0cfb84b9e2317a856580576612f4af
Digital signature successfully validated
File Name : disk0:/asa5500-firmware-1108.SPA
Image type : Release
Signer Information
Common Name : abraxas
Organization Unit : NCS_Kenton_ASA
Organization Name : CiscoSystems
Certificate Serial Number : 55831CF6
Hash Algorithm : SHA2 512
Signature Algorithm : 2048-bit RSA
Key Version : A
Verification successful.
System config has been modified. Save? [Y]es/[N]o: Y
Cryptochecksum: cb47de8a cad3b773 7fc07212 3e76ef4f
2804 bytes copied in 0.260 secs
Proceed with reload? [confirm]
***
*** --- START GRACEFUL SHUTDOWN ---
***
*** Message to all terminals:
***
*** Performing upgrade on rom-monitor.
Shutting down License Controller
Shutting down File system
***
*** --- SHUTDOWN NOW ---
***
*** Message to all terminals:
***
*** Performing upgrade on rom-monitor.
Process shutdown finished
Rebooting.....
INIT: Sending processes the TERM signal
Deconfiguring network interfaces... done.
Sending all processes the TERM signal...
Sending all processes the KILL signal...
Deactivating swap...
Unmounting local filesystems...
Rebooting...
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.01, RELEASE SOFTWARE
Copyright (c) 1994-2014 by Cisco Systems, Inc.
Compiled Mon 10/20/2014 15:59:12.05 by builder
Current image running: Boot ROM0
Last reset cause: PowerCycleRequest
DIMM Slot 0 : Present
DIMM Slot 1 : Present
INFO: Rommon upgrade state: ROMMON_UPG_START (1)
INFO: Reset code: 0x00002000
Firmware upgrade step 1... Looking for file 'disk0:asa5500-firmware-1108.SPA' Located 'asa5500-firmware-1108.SPA' @ cluster 856765.
###########################################################################################
Image base 0x77014018, size 9241408
LFBFF signature verified.
Objtype: lfbff_object_rommon (0x800000 bytes @ 0x77014238)
Objtype: lfbff_object_fpga (0xd0100 bytes @ 0x77814258)
INFO: FPGA version in upgrade image: 0x0202
INFO: FPGA version currently active: 0x0202
INFO: The FPGA image is up-to-date.
INFO: Rommon version currently active: 1.1.01. INFO: Rommon version in upgrade image: 1.1.08.
Active ROMMON: Preferred 0, selected 0, booted 0
Switching SPI access to standby rommon 1.
Please DO NOT reboot the unit, updating ROMMON................... INFO: Duplicating machine state...... Reloading now as step 1 of the rommon upgrade process... Toggling power on system board... Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.01, RELEASE SOFTWARE
Copyright (c) 1994-2014 by Cisco Systems, Inc.
Compiled Mon 10/20/2014 15:59:12.05 by builder
Current image running: Boot ROM0
Last reset cause: RP-Reset
DIMM Slot 0 : Present
DIMM Slot 1 : Present
INFO: Rommon upgrade state: ROMMON_UPG_START (1)
INFO: Reset code: 0x00000008
Active ROMMON: Preferred 0, selected 0, booted 0
Firmware upgrade step 2...
Detected current rommon upgrade is available, continue rommon upgrade process
Rommon upgrade reset 0 in progress
Reloading now as step 2 of the rommon upgrade process...
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE
Copyright (c) 1994-2015 by Cisco Systems, Inc.
Compiled Thu 06/18/2015 12:15:56.43 by builders
Current image running: *Upgrade in progress* Boot ROM1
Last reset cause: BootRomUpgrade
DIMM Slot 0 : Present
DIMM Slot 1 : Present
INFO: Rommon upgrade state: ROMMON_UPG_START (1)
INFO: Reset code: 0x00000010
PROM B: stopping boot timer
Active ROMMON: Preferred 0, selected 0, booted 1
INFO: Rommon upgrade state: ROMMON_UPG_TEST
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!! Please manually or auto boot ASAOS now to complete firmware upgrade !!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Platform ASA5508 with 8192 Mbytes of main memory
MAC Address: 18:8b:9d:1e:ca:7c
Use BREAK or ESC to interrupt boot.
Use SPACE to begin boot immediately.
Located '.boot_string' @ cluster 859024.
#
Attempt autoboot: "boot disk0:/asa952-lfbff-k8.SPA"
Located 'asa952-lfbff-k8.SPA' @ cluster 818273.
####################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
There are differences between boot sector and its backup.
Differences: (offset:original/backup)
65:01/00
Not automatically fixing this.
Starting check/repair pass.
/csco_config
"." is missing. Can't fix this yet.
/csco_config
".." is missing. Can't fix this yet.
Starting verification pass.
/csco_config
"." is missing. Can't fix this yet.
/csco_config
".." is missing. Can't fix this yet.
/dev/sdb1: 182 files, 849380/1918808 clusters
dosfsck(/dev/sdb1) returned 0
IO Memory Nodes: 1
IO Memory Per Node: 499122176 bytes
Global Reserve Memory Per Node: 314572800 bytes Nodes=1
Processor memory 3807834603
LCMB: got 499122176 bytes on numa-id=0, phys=0x1b8000000, virt=0x2aaaaae00000
LCMB: HEAP-CACHE POOL got 314572800 bytes on numa-id=0, virt=0x2aaac8a00000
Compiled on Sat 28-Nov-15 00:16 PST by builders
Total NICs found: 13
i354 rev03 Gigabit Ethernet @ irq255 dev 20 index 08 MAC: 188b.9d1e.ca7c
ivshmem rev03 Backplane Data Interface @ index 09 MAC: 0000.0001.0002
en_vtun rev00 Backplane Control Interface @ index 10 MAC: 0000.0001.0001
en_vtun rev00 Backplane Int-Mgmt Interface @ index 11 MAC: 0000.0001.0003
en_vtun rev00 Backplane Ext-Mgmt Interface @ index 12 MAC: 0000.0000.0000
Rom-monitor was successfully upgraded.
...
Verifiëren:
U kunt de opdracht Show Module gebruiken om de ROMMON softwareversie te controleren:
FTD5508X> enable Password: FTD5508X# show module Mod Card Type Model Serial No. ---- -------------------------------------------- ------------------ ----------- 1 ASA 5508-X with FirePOWER services, 8GE, AC, ASA5508 JAD192100SZ sfr FirePOWER Services Software Module ASA5508 JAD192100SZ Mod MAC Address Range Hw Version Fw Version Sw Version ---- --------------------------------- ------------ ------------ --------------- 1 188b.9d1e.ca7c to 188b.9d1e.ca84 1.0 1.1.8 9.5(2) sfr 188b.9d1e.ca7b to 188b.9d1e.ca7b N/A N/A 5.4.1-211
Task 3. Installeer de FTD Boot Image op ASA 555xx-X
Taakeis:
Installeer het FTD-boogbeeld ftd-start-9.6.1.0.lfbff op ASA 5508-X.
Oplossing:
Er zijn meer dan één methode om dit te doen. Dit is de eerste:
Methode 1 van ROMMON
Stap 1. Neem de ASA uit en voer de ROMMON-modus in:
FTD5508X# reload Proceed with reload? [confirm] FTD5508X# *** *** --- START GRACEFUL SHUTDOWN --- Shutting down isakmp Shutting down webvpn Shutting down sw-module Shutting down License Controller Shutting down File system *** *** --- SHUTDOWN NOW --- Process shutdown finished Rebooting..... INIT: Sending processes the TERM signal Deconfiguring network interfaces... done. Sending all processes the TERM signal... Sending all processes the KILL signal... Deactivating swap... Unmounting local filesystems... Rebooting... ÿ Rom image verified correctly Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE Copyright (c) 1994-2015 by Cisco Systems, Inc. Compiled Thu 06/18/2015 12:15:56.43 by builders Current image running: Boot ROM1 Last reset cause: PowerCycleRequest DIMM Slot 0 : Present DIMM Slot 1 : Present Platform ASA5508 with 8192 Mbytes of main memory MAC Address: 18:8b:9d:1e:ca:7c Use BREAK or ESC to interrupt boot. Use SPACE to begin boot immediately. Boot interrupted. rommon 1 >
Stap 2. Het configureren van basisnetwerkinstellingen:
rommon 1 > ADDRESS=10.62.148.29 rommon 2 > SERVER=10.229.22.42 rommon 3 > GATEWAY=10.62.148.1 rommon 4 > IMAGE=ftd-boot-9.6.1.0.lfbff rommon 5 > netmask 255.255.255.128 rommon 6 > ping 10.229.22.42 Sending 10, 32-byte ICMP Echoes to 10.229.22.42 timeout is 4 seconds ?!!!!!!!!! Success rate is 90 percent (9/10) rommon 7 > sync rommon 8 > tftpdnld ADDRESS: 10.62.148.29
NETMASK: 255.255.255.128
GATEWAY: 10.62.148.1
SERVER: 10.229.22.42
IMAGE: ftd-boot-9.6.1.0.lfbff
MACADDR: 18:8b:9d:1e:ca:7c
VERBOSITY: Progress
RETRY: 40
PKTTIMEOUT: 7200
BLKSIZE: 1460
CHECKSUM: Yes
PORT: GbE/1
PHYMODE: Auto Detect
Receiving ftd-boot-9.6.1.0.lfbff from 10.229.22.42!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! .. output omitted ..
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
File reception completed.
Boot buffer bigbuf=348bd018
Boot image size = 100308208 (0x5fa94f0) bytes
[image size] 100308208
[MD5 signaure] 781dde41844d750f8c0db1cd1e1e164f
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
Detected PID ASA5508.
Found device serial number JAD192100SZ.
Found USB flash drive /dev/sdb
Found hard drive(s): /dev/sda
fsck from util-linux 2.23.2
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
/dev/sdb1: 47 files, 24618/1919063 clusters ============================================== Launching boot CLI ... Configuring network interface using static IP Bringing up network interface. Depending on your network, this might take a couple of minutes when using DHCP... ifup: interface lo already configured Using IPv4 address: 10.62.148.62
Using IPv6 address: fe80::1a8b:9dff:fe1e:ca7b
Using DNS server: 10.62.145.72
Using default gateway: 10.62.148.100
INIT: Starting system message bus: dbus.
Starting OpenBSD Secure Shell server: sshd
generating ssh RSA key...
generating ssh ECDSA key...
generating ssh DSA key...
done.
Starting Advanced Configuration and Power Interface daemon: acpid.
acpid: starting up
acpid: 1 rule loaded
acpid: waiting for events: event logging is off
Starting ntpd: done
Starting syslog-ng:.
Starting crond: OK
Cisco FTD Boot 6.0.0 (9.6.1.)
Type ? for list of commands
firepower-boot>
Op ASA 5512/15/25/45/55 is de procedure gelijk met alleen verschil in de naam van de opstapafbeelding:
rommon #0> ADDRESS=10.62.148.10 rommon #1> SERVER=10.229.22.42 rommon #2> GATEWAY=10.62.148.1 rommon #3> IMAGE=ftd-boot-9.6.1.0.cdisk
Methode 2. Van ASA modus
Stap 1. Van ASA EXec Mode (geen ROMMON) kopieert het FTD-boogbeeld naar ASA-flitser:
ciscoasa# copy ftp://10.48.40.70/ANG/mzafeiro/ftd-boot-9.6.1.0.lfbff flash
Stap 2. Verwijder alle ASA-afbeeldingen van de schijf:
ciscoasa# delete flash:asa*
De flitsinhoud nadat u ASA beelden verwijdert:
ciscoasa# show flash --#-- --length-- -----date/time------ path 131 33 May 20 2016 09:27:28 .boot_string 11 4096 Mar 03 2016 11:48:34 log 154 16767 May 20 2016 09:23:48 log/asa-appagent.log 155 465 Mar 03 2016 11:54:58 log/asa-ssp_ntp.log 21 4096 Jun 10 2015 06:45:42 crypto_archive 22 4096 Jun 10 2015 06:46:00 coredumpinfo 23 59 Jun 10 2015 06:46:00 coredumpinfo/coredump.cfg 134 25627616 Dec 01 2015 04:01:58 asdm-752.bin 135 52563 Feb 09 2016 02:49:58 system.cfg 136 25028660 Feb 09 2016 02:50:28 asdm-751-112.bin 137 38409858 Feb 09 2016 02:51:14 anyconnect-win-3.1.10010-k9.pkg 138 25629676 Feb 09 2016 04:38:10 asdm-752-153.bin 151 100308208 May 20 2016 09:39:57 ftd-boot-9.6.1.0.lfbff <--
Stap 3. Start de ASA opnieuw. De computer start vanaf het FTD-opstartbeeld:
Located 'ftd-boot-9.6.1.0.lfbff' @ cluster 45093.
#####################################################################
..
LFBFF signature verified.
INIT: version 2.88 booting
..
Cisco FTD Boot 6.0.0 (9.6.1.)
Type ? for list of commands
firepower-boot>
Task 4. Installeer de FTD System Image op ASA 555xx-X
Installeer het FTD systeembeeld op ASA 5508-X.
Oplossing
firepower-boot> setup
Welcome to Cisco FTD Setup
[hit Ctrl-C to abort]
Default values are inside []
Enter a hostname [firepower]: FTD5508
Do you want to configure IPv4 address on management interface?(y/n) [Y]:
Do you want to enable DHCP for IPv4 address assignment on management interface?(y/n) [Y]: N
Enter an IPv4 address: 10.62.148.29
Enter the netmask: 255.255.255.128
Enter the gateway: 10.62.148.1
Do you want to enable DHCP for IPv4 address assignment on management interface?(y/n) [N]:
Enter an IPv4 address [10.62.148.29]:
Enter the netmask [255.255.255.128]:
Enter the gateway [10.62.148.1]:
Do you want to configure static IPv6 address on management interface?(y/n) [N]:
Stateless autoconfiguration will be enabled for IPv6 addresses.
Enter the primary DNS server IP address: 173.38.200.100
Do you want to configure Secondary DNS Server? (y/n) [n]: y
Enter the secondary DNS server IP address: 144.254.71.184
Do you want to configure Local Domain Name? (y/n) [n]:
Do you want to configure Search domains? (y/n) [n]:
Do you want to enable the NTP service? [Y]:
Enter the NTP servers separated by commas [203.0.113.126]: 171.68.38.65
Please review the final configuration:
Hostname: FTD5508
Management Interface Configuration
IPv4 Configuration: static
IP Address: 10.62.148.29
Netmask: 255.255.255.128
Gateway: 10.62.148.1
IPv6 Configuration: Stateless autoconfiguration
DNS Configuration:
DNS Server:
173.38.200.100
144.254.71.184
NTP configuration:
171.68.38.65
CAUTION:
You have selected IPv6 stateless autoconfiguration, which assigns a global address
based on network prefix and a device identifier. Although this address is unlikely
to change, if it does change, the system will stop functioning correctly.
We suggest you use static addressing instead.
Apply the changes?(y,n) [Y]:
Configuration saved successfully!
Applying...
Done.
Press ENTER to continue...
firepower-boot>
Controleer de connectiviteit met de FTP-server:
firepower-boot> ping 10.229.22.42
PING 10.229.22.42 (10.229.22.42) 56(84) bytes of data.
64 bytes from 10.229.22.42: icmp_seq=1 ttl=124 time=1.30 ms
64 bytes from 10.229.22.42: icmp_seq=2 ttl=124 time=1.32 ms
64 bytes from 10.229.22.42: icmp_seq=3 ttl=124 time=1.45 ms
^C
--- 10.229.22.42 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 1.302/1.360/1.458/0.075 ms
Installeer de systeemverpakking:
firepower-boot> system install ftp://10.229.22.42/ftd-6.0.0-1005.pkg
######################## WARNING ############################
# The content of disk0: will be erased during installation! #
#############################################################
Do you want to continue? [y/N] y
Erasing disk0 ...
Verifying
Enter credentials to authenticate with ftp server
Username: ftp
Password:
Verifying Downloading Extracting <-- Here give it some time (~10 min)
Package Detail
Description: Cisco ASA-NGFW 6.0.0-1005 System Install
Requires reboot: Yes
Do you want to continue with upgrade? [y]: <-- Press Enter
Warning: Please do not interrupt the process or turn off the system.
Doing so might leave system in unusable state.
Starting upgrade process ...
Populating new system image <-- Here give it some time (~5 min)
Reboot is required to complete the upgrade. Press 'Enter' to reboot the system. <-- Press Enter
Broadcast message from root@firepowStopping OpenBSD Secure Shell server: sshdstopped /usr/sbin/sshd (pid 1963)
.
Stopping Advanced Configuration and Power Interface daemon: stopped /usr/sbin/acpid (pid 1967)
acpid: exiting
acpid.
Stopping system message bus: dbus.
Stopping ntpd: stopped process in pidfile '/var/run/ntp.pid' (pid 2055)
done
Stopping crond: OK
Deconfiguring network interfaces... done.
Sending all processes the TERM signal...
Sending all processes the KILL signal...
Deactivating swap...
Unmounting local filesystems...
Rebooting... ÿ
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE
Copyright (c) 1994-2015 by Cisco Systems, Inc.
Compiled Thu 06/18/2015 12:15:56.43 by builders
Current image running: Boot ROM1
Last reset cause: PowerCycleRequest
DIMM Slot 0 : Present
DIMM Slot 1 : Present
Platform ASA5508 with 8192 Mbytes of main memory
MAC Address: 18:8b:9d:1e:ca:7c
Use BREAK or ESC to interrupt boot.
Use SPACE to begin boot immediately.
Located '.boot_string' @ cluster 186016.
#
Attempt autoboot: "boot disk0:os.img"
Located 'os.img' @ cluster 160001.
########################################
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
Detected PID ASA5508.
Found device serial number JAD192100SZ.
Found USB flash drive /dev/sdb
Found hard drive(s): /dev/sda
fsck from util-linux 2.23.2
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
/dev/sdb1: 7 files, 26064/1919063 clusters
==============================================
Use ESC to interrupt boot and launch boot CLI.
Use SPACE to launch Cisco FTD immediately.
Cisco FTD launch in 20 seconds ...
Running on kenton
Mounting disk partitions ...
Initializing Threat Defense ... [ OK ]
Starting system log daemon... [ OK ]
Flushing all current IPv4 rules and user defined chains: ...success
Clearing all current IPv4 rules and user defined chains: ...success
Applying iptables firewall rules:
Flushing chain `PREROUTING'
Flushing chain `INPUT'
Flushing chain `FORWARD'
Flushing chain `OUTPUT'
Flushing chain `POSTROUTING'
Flushing chain `INPUT'
Flushing chain `FORWARD'
Flushing chain `OUTPUT'
Applying rules successed
Flushing all current IPv6 rules and user defined chains: ...success
Clearing all current IPv6 rules and user defined chains: ...success
Applying ip6tables firewall rules:
Flushing chain `PREROUTING'
Flushing chain `INPUT'
Flushing chain `FORWARD'
Flushing chain `OUTPUT'
Flushing chain `POSTROUTING'
Flushing chain `INPUT'
Flushing chain `FORWARD'
Flushing chain `OUTPUT'
Applying rules successed
Starting nscd...
mkdir: created directory '/var/run/nscd' [ OK ]
Starting , please wait...grep: /ngfw/etc/motd: No such file or directory
...complete.
Firstboot detected, executing scripts
Executing S01reset_failopen_if [ OK ]
Executing S04fix-httpd.sh [ OK ]
Executing S05set-mgmnt-port [ OK ]
Executing S06addusers [ OK ]
Executing S07uuid-init [ OK ]
Executing S09configure_mysql [ OK ]
************ Attention *********
Initializing the configuration database. Depending on available
system resources (CPU, memory, and disk), this may take 30 minutes
or more to complete.
************ Attention *********
Executing S10database [ OK ]
Executing S12install_infodb [ OK ]
Executing S15set-locale.sh [ OK ]
Executing S16update-sensor.pl [ OK ]
Executing S19cert-tun-init [ OK ]
Executing S20cert-init [ OK ]
Executing S21disable_estreamer [ OK ]
Executing S25create_default_des.pl [ OK ]
Executing S30init_lights_out_mgmt.pl [ OK ]
Executing S40install_default_filters.pl [ OK ]
Executing S42install_default_dashboards.pl [ OK ]
Executing S43install_default_report_templates.pl [ OK ]
Executing S44install_default_app_filters.pl [ OK ]
Executing S45install_default_realms.pl [ OK ]
Executing S47install_default_sandbox_EO.pl [ OK ]
Executing S50install-remediation-modules [ OK ]
Executing S51install_health_policy.pl [ OK ]
Executing S52install_system_policy.pl [ OK ]
Executing S53change_reconciliation_baseline.pl [ OK ]
Executing S70update_sensor_objects.sh [ OK ]
Executing S85patch_history-init [ OK ]
Executing S90banner-init [ OK ]
Executing S95copy-crontab [ OK ]
Executing S96grow_var.sh [ OK ]
********** Attention **********
Initializing the system's localization settings. Depending on available
system resources (CPU, memory, and disk), this may take 10 minutes
or more to complete.
********** Attention **********
Executing S96localize-templates [ OK ]
Executing S96ovf-data.pl [ OK ]
Executing S97compress-client-resources [ OK ]
Executing S97create_platinum_forms.pl [ OK ]
Executing S97install_cloud_support.pl [ OK ]
Executing S97install_geolocation.pl [ OK ]
Executing S97install_ssl_inspection.pl [ OK ]
Executing S97update_modprobe.pl [ OK ]
Executing S98check-db-integrity.sh [ OK ]
Executing S98htaccess-init [ OK ]
Executing S99correct_ipmi.pl [ OK ]
Executing S99start-system [ OK ]
Executing S99z_db_restore [ OK ]
Firstboot scripts finished.
Configuring NTP... [ OK ]
Model reconfigure detected, executing scripts
Pinging mysql
Found mysql is running
Executing 45update-sensor.pl [ OK ]
Executing 55recalculate_arc.pl [ OK ]
Starting xinetd:
Mon Mar 14 18:28:11 UTC 2016
Starting MySQL...
Pinging mysql
Pinging mysql, try 1
Found mysql is running
Running initializeObjects...
Stopping MySQL...
Killing mysqld with pid 10993
Wait for mysqld to exit\c
done
Mon Mar 14 18:28:21 UTC 2016
Starting sfifd... [ OK ]
Starting Cisco ASA5508-X Threat Defense, please wait...No PM running!
...started.
INIT: Starting system message bus: dbus.
Starting OpenBSD Secure Shell server: sshd
generating ssh RSA key...
generating ssh ECDSA key...
generating ssh DSA key...
done.
Starting Advanced Configuration and Power Interface daemon: acpid.
Starting crond: OK
Mar 14 18:28:26 ciscoasa SF-IMS[11490]: [11490] init script:system [INFO] pmmon Setting affinity to 5-7...
pid 11486's current affinity list: 0-7
pid 11486's new affinity list: 5-7
Mar 14 18:28:26 ciscoasa SF-IMS[11492]: [11492] init script:system [INFO] pmmon The Process Manager is not running...
Mar 14 18:28:26 ciscoasa SF-IMS[11493]: [11493] init script:system [INFO] pmmon Starting the Process Manager...
Mar 14 18:28:26 ciscoasa SF-IMS[11494]: [11494] pm:pm [INFO] Using model number 75K
Cisco ASA5508-X Threat Defense v6.0.0 (build 1005)
ciscoasa login:
Compiled on Sat 07-Nov-15 16:13 PST by builders
Total NICs found: 13
i354 rev03 Gigabit Ethernet @ irq255 dev 20 index 08 MAC: 188b.9d1e.ca7c
ivshmem rev03 Backplane Data Interface @ index 09 MAC: 0000.0001.0002
en_vtun rev00 Backplane Control Interface @ index 10 MAC: 0000.0001.0001
en_vtun rev00 Backplane Int-Mgmt Interface @ index 11 MAC: 0000.0001.0003
en_vtun rev00 Backplane Ext-Mgmt Interface @ index 12 MAC: 0000.0000.0000
INFO: Unable to read firewall mode from flash
Writing default firewall mode (single) to flash
INFO: Unable to read cluster interface-mode from flash
Writing default mode "None" to flash
Verify the activation-key, it might take a while...
Failed to retrieve permanent activation key.
Running Permanent Activation Key: 0x00000000 0x00000000 0x00000000 0x00000000 0x00000000
The Running Activation Key is not valid, using default settings:
Licensed features for this platform:
Maximum Physical Interfaces : Unlimited perpetual
Maximum VLANs : 50 perpetual
Inside Hosts : Unlimited perpetual
Failover : Active/Active perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Disabled perpetual
Security Contexts : 2 perpetual
GTP/GPRS : Disabled perpetual
AnyConnect Premium Peers : 4 perpetual
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 100 perpetual
Total VPN Peers : 100 perpetual
Shared License : Disabled perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
Total UC Proxy Sessions : 320 perpetual
Botnet Traffic Filter : Disabled perpetual
Cluster : Disabled perpetual
VPN Load Balancing : Enabled perpetual
Encryption hardware device : Cisco ASA Crypto on-board accelerator (revision 0x1)
Cisco Adaptive Security Appliance Software Version 99.1(3)194
****************************** Warning *******************************
This product contains cryptographic features and is
subject to United States and local country laws
governing, import, export, transfer, and use.
Delivery of Cisco cryptographic products does not
imply third-party authority to import, export,
distribute, or use encryption. Importers, exporters,
distributors and users are responsible for compliance
with U.S. and local country laws. By using this
product you agree to comply with applicable laws and
regulations. If you are unable to comply with U.S.
and local laws, return the enclosed items immediately.
A summary of U.S. laws governing Cisco cryptographic
products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by
sending email to export@cisco.com.
******************************* Warning *******************************
... output omitted ...
Reading from flash...
!
Cryptochecksum (changed): 6129864f 6298b553 75f279ea e547792b
INFO: Power-On Self-Test in process.
.......................
INFO: Power-On Self-Test complete.
INFO: Starting HW-DRBG health test...
INFO: HW-DRBG health test passed.
INFO: Starting SW-DRBG health test...
INFO: SW-DRBG health test passed.
Cisco ASA5508-X Threat Defense v6.0.0 (build 1005)
firepower login: admin
Password: <-- Admin123
You must accept the EULA to continue.
Press
to display the EULA:
... EULA is displayed - output is omitted
END USER LICENSE AGREEMENT
Please enter 'YES' or press to AGREE to the EULA:
System initialization in progress. Please stand by.
You must change the password for 'admin' to continue.
Enter new password:
Confirm new password:
You must configure the network to continue.
You must configure at least one of IPv4 or IPv6.
Do you want to configure IPv4? (y/n) [y]: Do you want to configure IPv6? (y/n) [n]:
Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]:
Enter an IPv4 address for the management interface [192.168.45.45]: 10.62.148.29
Enter an IPv4 netmask for the management interface [255.255.255.0]: 255.255.255.128
Enter the IPv4 default gateway for the management interface []: 10.62.148.1
Enter a fully qualified hostname for this system [firepower]: FTD5508
Enter a comma-separated list of DNS servers or 'none' []: 173.38.200.100,144.254.71.184
Enter a comma-separated list of search domains or 'none' []:
If your networking information has changed, you will need to reconnect.
For HTTP Proxy configuration, run 'configure network http-proxy'
Configure firewall mode? (routed/transparent) [routed]:
Configuring firewall mode ...
Update policy deployment information
- add device configuration
You can register the sensor to a Firepower Management Center and use the
Firepower Management Center to manage it. Note that registering the sensor
to a Firepower Management Center disables on-sensor Firepower Services
management capabilities.
When registering the sensor to a Firepower Management Center, a unique
alphanumeric registration key is always required. In most cases, to register
a sensor to a Firepower Management Center, you must provide the hostname or
the IP address along with the registration key.
'configure manager add [hostname | ip address ] [registration key ]'
However, if the sensor and the Firepower Management Center are separated by a
NAT device, you must enter a unique NAT ID, along with the unique registration
key.
'configure manager add DONTRESOLVE [registration key ] [ NAT ID ]'
Later, using the web interface on the Firepower Management Center, you must
use the same registration key and, if necessary, the same NAT ID when you add
this sensor to the Firepower Management Center.
>
Tip: U kunt de optie voorkomen om de afbeelding te installeren gebruiken. In dat geval wordt u tijdens de installatie niet gevraagd.
firepower-boot>system install noconfirm ftp://10.229.22.42/ftd-6.0.0-1005.pkg
Op FTD 6.1.x en hoger wordt u gevraagd naar de beheermodus (lokaal vs afstandsbediening).
For HTTP Proxy configuration, run 'configure network http-proxy' Manage the device locally? (yes/no) [yes]: no Configure firewall mode? (routed/transparent) [routed]:
Lokale modus = alleen van toepassing op ASA 555xx-X-apparaten. U beheert de FTD vanaf Firepower Devices Manager (FDM).
Afstandsmodus = U beheert de FTD vanaf FMC
Verificatie
> show version -------------------[ FTD5508 ]-------------------- Model : Cisco ASA5508-X Threat Defense (75) Version 6.0.0 (Build 1005) UUID : 8c3f4b7e-ea11-11e5-94f1-f3a55afb51a3 Rules update version : 2015-10-01-001-vrt VDB version : 252 ---------------------------------------------------- >
De installatie van het systeembeeld op ASA 5512/15/25/45/55 is hetzelfde als hierboven.
Task 5. Registreer de FTD aan FMC
FTD aan FMC-server registreren de volgende instellingen gebruiken:
| Host | 10.62.148.29 |
| Naam weergeven | FTD5508 |
| Registratiekanaal | Cisco |
| Groep geen | |
| Toegangsbeheerbeleid | FTD5508 |
| Basisbeleid voor toegangscontrole | None |
| Standaardactie voor toegangsbeleid | Alle verkeer blokkeren |
Oplossing
Stap 1.Specificeer op FTD de FMC-server:
> configure manager add 10.62.148.73 cisco Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC. > show managers Host : 10.62.148.73 Registration Key : **** Registration : pending RPC Status : Type : Manager Host : 10.62.148.73 Registration : Pending >
Stap 2.Voordat u de FTD toevoegt, moet u het FMC registreren bij de Smart Licensing Server. Als u een FTD-apparaat probeert toe te voegen zonder Smart Licentie, krijgt u de volgende fout:
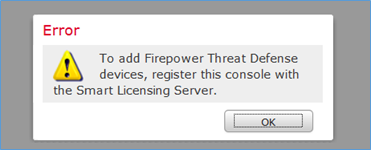
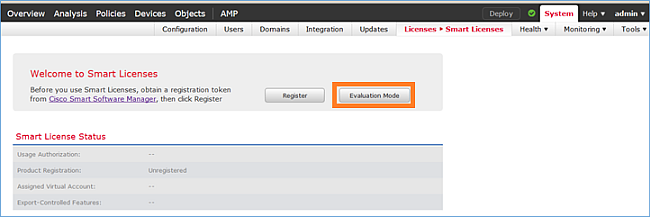
U kunt de evaluatiemodus kiezen. U kunt deze software gedurende 90 dagen gebruiken zonder functies die een sterke versleuteling vereisen (bijvoorbeeld VPN).
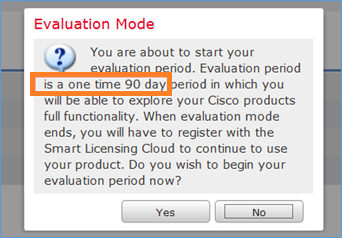
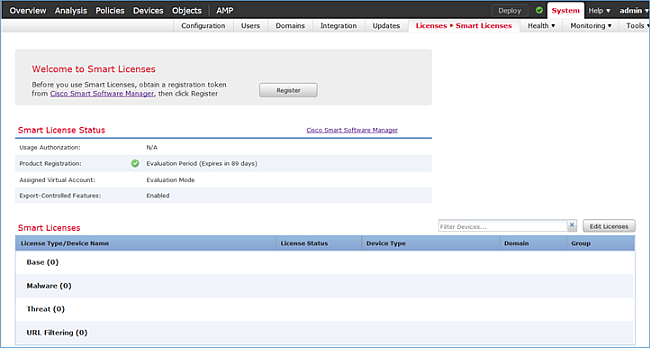
Stap 3. Op FMC moet u eerst het toegangscontrolemiddel definiëren dat door FTD zal worden gebruikt. Navigeer naar beleid > Toegangsbeheer en selecteer Nieuw beleid:

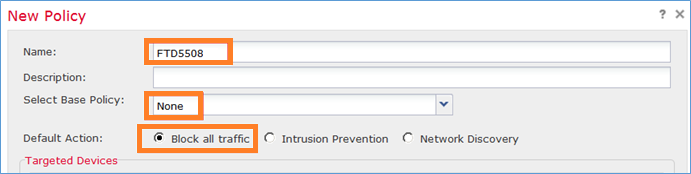
Voeg vervolgens het FTD-apparaat toe:
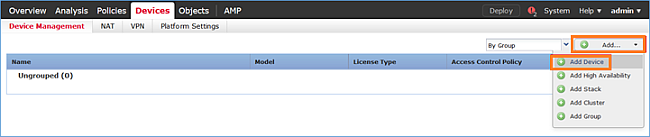
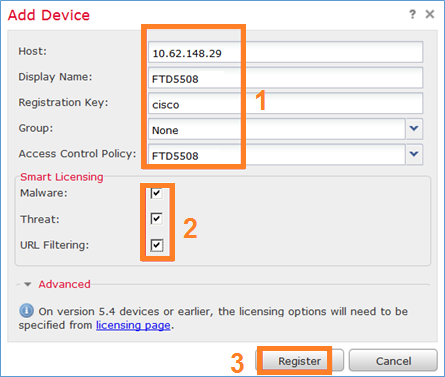
Aan het einde van de FTD-toevoeging wordt een beleid toegepast:
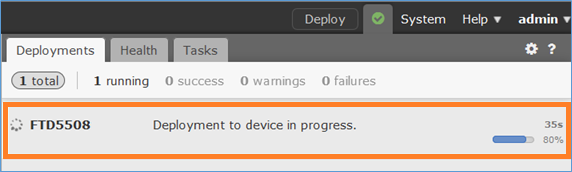
Om te controleren wat er op de achtergrond gebeurt bij het toevoegen van het FTD-apparaat, kan u zowel op het VCC als op het FTD een vlekje plaatsen.
Op FMC:
admin@fs4k:~$ sudo pigtail ***************************************************************************************************************************** ** Displaying logs: ACTQ HTTP DCSM VMSS MOJO NGFW NGUI VMSB TCAT DEPL MSGS USMS *****************************************************************************************************************************
Op FTD:
> pigtail ******************************************************************************** ** Displaying logs: HTTP ACTQ DCSM VMSS MOJO NGUI NGFW TCAT VMSB DEPL USMS MSGS ********************************************************************************
Opmerking: Als de FTD Management Interface status is verminderd, zorg er dan voor dat de conversiewaarde 0x1 is.
Task 6. upgrade van de FTD
Bij deze taakupgrade van 6.0.0 naar 6.0.1.
|
|
Versie |
Bestandsnaam |
| Eerste FTD-afbeelding |
Versie 6.0.0 (gebouwd 1005) |
ftd-6,0,0-1005,pkg |
| Target FTD-afbeelding |
versie 6.0.1 (gebouwd 1213) |
Cisco_FTD_Upgrade-6.0.1-1213.sh |
Oplossing
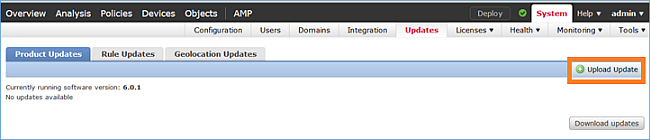
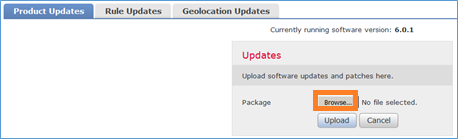
Stap 1. Upload het FTD-beeld naar FMC:
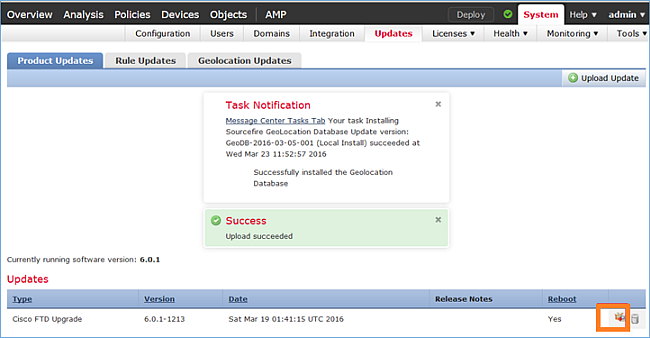
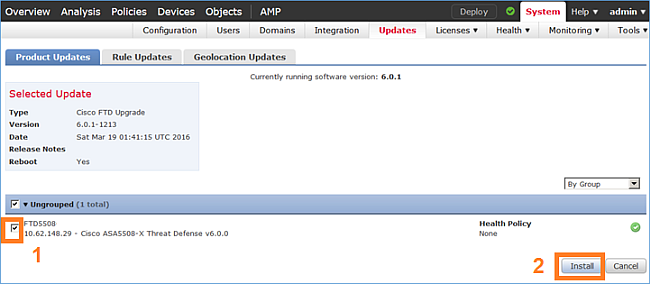
Stap 2. Installeer het FTD-beeld:
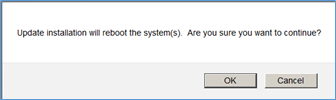
Er wordt een waarschuwing weergegeven over de herlading van FTD:
De upgrade in dit geval duurde ongeveer 35 minuten. Zoals hieronder wordt getoond, moet het beleid opnieuw worden toegepast:
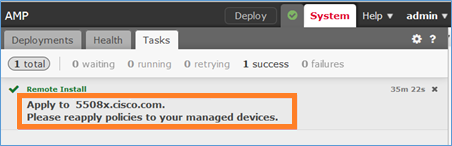
U implementeert het beleid:
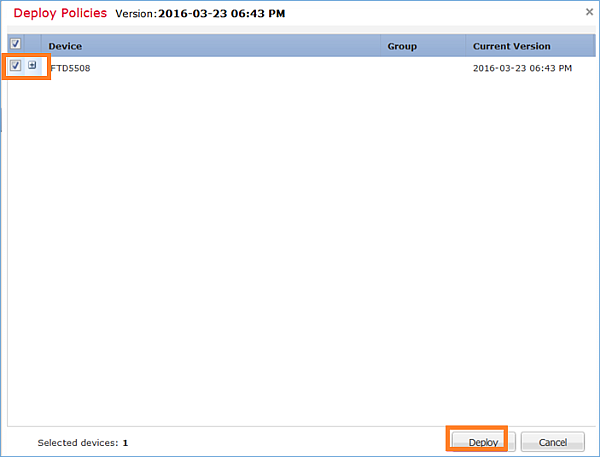
Verificatie
Na de FTD-upgrade:
> show version
-------------------[ FTD5508 ]--------------------
Model : Cisco ASA5508-X Threat Defense (75) Version 6.0.1 (Build 1213)
UUID : 53b44806-f0f4-11e5-88cc-c72c24d24877
Rules update version : 2016-03-04-001-vrt
VDB version : 259
----------------------------------------------------
>
Task 7. Connect en Detectie vanuit LINA Engine CLI-modus
Voer de LINA CLI-modus in en koppel het los.
Oplossing
Typ de volgende opdracht in FTD CLISH-modus:
> system support diagnostic-cli Attaching to ASA console ... Press 'Ctrl+a then d' to detach. Type help or '?' for a list of available commands. firepower>
firepower> enable Password: <-- by default empty (null) firepower#
Zoals in het bovenstaande bericht wordt vermeld, moet u het HDTV-console van het type CTRL + a loskoppelen (verwijderen) en vervolgens op D drukken:
firepower# <- 'Ctrl+a then d' Console connection detached. admin@FTD5508:~$
Task 8. Zoek een bestaande FTD-installatie
Vereisten
De bestaande FTD-afbeelding opslaan en installeren, versie 6.1.0-30
Oplossing
Bij deze taak wordt ervan uitgegaan dat er een FTD-apparaat met code 6.0.1.x bestaat en om welke redenen dan ook dat het apparaat moet worden aangepast (bv. onherstelbare corruptie in databases, een catastrofaal defect dat geen softwareupgrade mogelijk maakt, enz.).
Samenvatting van stappen
- Compatibiliteitscontrole.
- Registratie FTD van VCC ongedaan maken.
- Zet het FTD-apparaat terug en voer de BootCLI in.
- Start de setup-wizard.
- Installeer de FTD System-afbeelding.
- Registreer FTD in het VCC.
Gedetailleerde stappen
Stap 1. Controleer de FirePOWER-opmerkingen en zorg ervoor dat het FTD-beeld dat u wilt gebruiken compatibel is met het FMC. Als u het VCC niet eerst verbetert.
Stap 2. Registreer (verwijder) FTD van het VCC. Deze stap is nodig sinds de FTD zijn UID herafbeelding herstelt en kan niet opnieuw worden geregistreerd, maar moet vanaf de schrammeling worden toegevoegd.
Stap 3. Neem het FTD-apparaat weer in en voer de BootCLI in. Aangezien er al een bestaand FTD-beeld is geïnstalleerd, kan de installatie van het FTD Boot-beeld worden overgeslagen:
> reboot
This command will reboot the system. Continue?
Please enter 'YES' or 'NO': YES
Broadcast messagStopping Cisco ASA5506-X Threat Defense......ok
Shutting down sfifd... [ OK ]
Clearing static routes
Unconfiguring default route [ OK ]
Unconfiguring address on br1 [ OK ]
Unconfiguring IPv6 [ OK ]
Downing interface [ OK ]
Stopping nscd... [ OK ]
Stopping system log daemon... [ OK ]
Stopping Threat Defense ...
cp: cannot stat '/etc/ssh': No such file or directory
Stopping system message bus: dbus.
rmdir: failed to remove directory '/etc': Directory not empty [ OK ]
Un-mounting disk partitions ...
…
Device root is still in use.
mdadm: Cannot get exclusive access to /dev/md0:Perhaps a running process, mounted filesystem or active volume group?
Stopping OpenBSD Secure Shell server: sshdstopped /usr/sbin/sshd (pid 4209)
.
Stopping Advanced Configuration and Power Interface daemon: stopped /usr/sbin/acpid (pid 4213)
acpid: exiting
acpid.
Stopping system message bus: dbus.
Deconfiguring network interfaces... ifdown: interface br1 not configured
done.
Sending all processes the TERM signal...
Sending all processes the KILL signal...
Deactivating swap...
Unmounting local filesystems...
Rebooting... ÿ
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE
Copyright (c) 1994-2015 by Cisco Systems, Inc.
Compiled Thu 06/18/2015 12:15:56.43 by builders
Current image running: Boot ROM0
Last reset cause: PowerCycleRequest
DIMM Slot 0 : Present
Platform ASA5506 with 4096 Mbytes of main memory
MAC Address: 84:3d:c6:1a:cf:39
Use BREAK or ESC to interrupt boot.
Use SPACE to begin boot immediately.
Located '.boot_string' @ cluster 260275.
#
Attempt autoboot: "boot disk0:"
Located 'os.img' @ cluster 235457.
#########################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
Detected PID ASA5506.
Found device serial number JAD2034008E.
Found USB flash drive /dev/sdb
Found hard drive(s): /dev/sda
fsck from util-linux 2.23.2
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
/dev/sdb1: 42 files, 24805/1798467 clusters
==============================================
Use ESC to interrupt boot and launch boot CLI.
Use SPACE to launch Cisco FTD immediately.
Cisco FTD launch in 23 seconds ... < Press ESC to enter BootCLI
Launching boot CLI ...
Configuring network interface using DHCP
Bringing up network interface.
Depending on your network, this might take a couple of minutes when using DHCP...
ifup: interface lo already configured
Using IPv6 address: fe80::863d:c6ff:fe1a:cf38
IPv4 address not assigned. Run 'setup' before installation.
INIT: Starting system message bus: dbus.
Starting OpenBSD Secure Shell server: sshd
generating ssh RSA key...
generating ssh ECDSA key...
generating ssh DSA key...
done.
Starting Advanced Configuration and Power Interface daemon: acpid.
acpid: starting up
acpid: 1 rule loaded
acpid: waiting for events: event logging is off
Starting ntpd: done
Starting syslog-ng:[2017-01-14T11:20:33.699619] Connection failed; fd='15', server='AF_INET(127.128.254.1:514)', local='AF_INET(0.0.0.0:0)', error='Network is unreachable (101)'
[2017-01-14T11:20:33.699704] Initiating connection failed, reconnecting; time_reopen='60'
.
Starting crond: OK
Cisco FTD Boot 6.0.0 (9.6.2.)
Type ? for list of commands
firepower-boot>
Stap 4.Draai de wizard en stel de fundamentele netwerkparameters in:
firepower-boot>setup
Welcome to Cisco FTD Setup
[hit Ctrl-C to abort]
Default values are inside []
Enter a hostname [firepower]: FTD5506
Do you want to configure IPv4 address on management interface?(y/n) [Y]: Y
Do you want to enable DHCP for IPv4 address assignment on management interface?(y/n) [Y]: n
Enter an IPv4 address: 10.48.66.83
Enter the netmask: 255.255.255.128
Enter the gateway: 10.48.66.1
Do you want to configure static IPv6 address on management interface?(y/n) [N]: N
Stateless autoconfiguration will be enabled for IPv6 addresses.
Enter the primary DNS server IP address: 192.168.0.1
Do you want to configure Secondary DNS Server? (y/n) [n]: n
Do you want to configure Local Domain Name? (y/n) [n]: n
Do you want to configure Search domains? (y/n) [n]: n
Do you want to enable the NTP service? [Y]: n
Please review the final configuration:
Hostname: FTD5506
Management Interface Configuration
IPv4 Configuration: static
IP Address: 10.48.66.83
Netmask: 255.255.255.128
Gateway: 10.48.66.1
IPv6 Configuration: Stateless autoconfiguration
DNS Configuration:
DNS Server: 192.168.0.1
NTP configuration: Disabled
CAUTION:
You have selected IPv6 stateless autoconfiguration, which assigns a global address
based on network prefix and a device identifier. Although this address is unlikely
to change, if it does change, the system will stop functioning correctly.
We suggest you use static addressing instead.
Apply the changes?(y,n) [Y]: Y
Configuration saved successfully!
Applying...
Restarting network services...
Done.
Press ENTER to continue...
firepower-boot>
Stap 5.Controleer de connectiviteit met de server (FTP, HTTP enz.) die het FTD systeembeeld bevat en start de installatie:
firepower-boot>ping 10.48.40.70
PING 10.48.40.70 (10.48.40.70) 56(84) bytes of data.
64 bytes from 10.48.40.70: icmp_seq=1 ttl=64 time=555 ms
64 bytes from 10.48.40.70: icmp_seq=2 ttl=64 time=0.465 ms
64 bytes from 10.48.40.70: icmp_seq=3 ttl=64 time=0.511 ms
--- 10.48.40.70 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.465/185.466/555.424/261.599 ms
firepower-boot > system install noconfirm ftp://anonymous:cisco@10.48.40.70/ftd-6. 1.0-330.pkg
######################## WARNING ############################
# The content of disk0: will be erased during installation! #
#############################################################
Do you want to continue? [y/N] y
Erasing disk0 ...
Verifying
Downloading
Extracting
Package Detail
Description: Cisco ASA-FTD 6.1.0-330 System Install
Requires reboot: Yes
Warning: Please do not interrupt the process or turn off the system.
Doing so might leave system in unusable state.
Starting upgrade process ...
Populating new system image
... output omitted ...
Firstboot detected, executing scripts
Executing S01reset_failopen_if [ OK ]
Executing S01virtual-machine-reconfigure [ OK ]
Executing S02aws-pull-cfg [ OK ]
Executing S02configure_onbox [ OK ]
Executing S04fix-httpd.sh [ OK ]
Executing S05set-mgmnt-port [ OK ]
Executing S06addusers [ OK ]
Executing S07uuid-init [ OK ]
Executing S08configure_mysql [ OK ]
************ Attention *********
Initializing the configuration database. Depending on available
system resources (CPU, memory, and disk), this may take 30 minutes
or more to complete.
************ Attention *********
Executing S09database-init [ OK ]
Executing S11database-populate [ OK ]
Executing S12install_infodb [ OK ]
Executing S15set-locale.sh [ OK ]
Executing S16update-sensor.pl [ OK ]
Executing S19cert-tun-init [ OK ]
Executing S20cert-init [ OK ]
Executing S21disable_estreamer [ OK ]
Executing S25create_default_des.pl [ OK ]
Executing S30init_lights_out_mgmt.pl [ OK ]
Executing S40install_default_filters.pl [ OK ]
Executing S42install_default_dashboards.pl [ OK ]
Executing S43install_default_report_templates.pl [ OK ]
Executing S44install_default_app_filters.pl [ OK ]
Executing S45install_default_realms.pl [ OK ]
Executing S47install_default_sandbox_EO.pl [ OK ]
Executing S50install-remediation-modules [ OK ]
Executing S51install_health_policy.pl [ OK ]
Executing S52install_system_policy.pl [ OK ]
Executing S53change_reconciliation_baseline.pl [ OK ]
Executing S70remove_casuser.pl [ OK ]
Executing S70update_sensor_objects.sh [ OK ]
Executing S85patch_history-init [ OK ]
Executing S90banner-init [ OK ]
Executing S95copy-crontab [ OK ]
Executing S96grow_var.sh [ OK ]
Executing S96install_vmware_tools.pl [ OK ]
********** Attention **********
Initializing the system's localization settings. Depending on available
system resources (CPU, memory, and disk), this may take 10 minutes
or more to complete.
********** Attention **********
Executing S96localize-templates [ OK ]
Executing S96ovf-data.pl [ OK ]
Executing S97compress-client-resources [ OK ]
Executing S97create_platinum_forms.pl [ OK ]
Executing S97install_cas [ OK ]
Executing S97install_cloud_support.pl [ OK ]
Executing S97install_geolocation.pl [ OK ]
Executing S97install_ssl_inspection.pl [ OK ]
Executing S97update_modprobe.pl [ OK ]
Executing S98check-db-integrity.sh [ OK ]
Executing S98htaccess-init [ OK ]
Executing S98is-sru-finished.sh [ OK ]
Executing S99correct_ipmi.pl [ OK ]
Executing S99start-system [ OK ]
Executing S99z_db_restore [ OK ]
Executing S99_z_cc-integrity.sh [ OK ]
Firstboot scripts finished.
Configuring NTP... [ OK ]
fatattr: can't open '/mnt/disk0/.private2': No such file or directory
fatattr: can't open '/mnt/disk0/.ngfw': No such file or directory
Model reconfigure detected, executing scripts
Pinging mysql
Found mysql is running
Executing 45update-sensor.pl [ OK ]
Executing 55recalculate_arc.pl [ OK ]
Starting xinetd:
Sat Jan 14 12:07:35 UTC 2017
Starting MySQL...
Pinging mysql
Pinging mysql, try 1
Pinging mysql, try 2
Found mysql is running
Running initializeObjects...
Stopping MySQL...
Killing mysqld with pid 22354
Wait for mysqld to exit\c
done
Sat Jan 14 12:07:57 UTC 2017
Starting sfifd... [ OK ]
Starting Cisco ASA5506-X Threat Defense, please wait...No PM running!
...started.
... output omitted ...
firepower login: admin
Password: < Admin123
You must accept the EULA to continue.
Press <ENTER> to display the EULA:
END USER LICENSE AGREEMENT
…
Please enter 'YES' or press <ENTER> to AGREE to the EULA:
System initialization in progress. Please stand by.
You must change the password for 'admin' to continue.
Enter new password:
Confirm new password:
You must configure the network to continue.
You must configure at least one of IPv4 or IPv6.
Do you want to configure IPv4? (y/n) [y]:
Do you want to configure IPv6? (y/n) [n]:
Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]:
Enter an IPv4 address for the management interface [192.168.45.45]: 10.48.66.83
Enter an IPv4 netmask for the management interface [255.255.255.0]: 255.255.255.128
Enter the IPv4 default gateway for the management interface [192.168.45.1]: 10.48.66.1
Enter a fully qualified hostname for this system [firepower]: FTD5506
Enter a comma-separated list of DNS servers or 'none' []: 192.168.0.1
Enter a comma-separated list of search domains or 'none' []:
If your networking information has changed, you will need to reconnect.
For HTTP Proxy configuration, run 'configure network http-proxy'
Manage the device locally? (yes/no) [yes]: no
Configure firewall mode? (routed/transparent) [routed]:
Configuring firewall mode ...
Update policy deployment information
- add device configuration
- add network discovery
- add system policy
You can register the sensor to a Firepower Management Center and use the
Firepower Management Center to manage it. Note that registering the sensor
to a Firepower Management Center disables on-sensor Firepower Services
management capabilities.
When registering the sensor to a Firepower Management Center, a unique
alphanumeric registration key is always required. In most cases, to register
a sensor to a Firepower Management Center, you must provide the hostname or
the IP address along with the registration key.
'configure manager add [hostname | ip address ] [registration key ]'
However, if the sensor and the Firepower Management Center are separated by a
NAT device, you must enter a unique NAT ID, along with the unique registration
key.
'configure manager add DONTRESOLVE [registration key ] [ NAT ID ]'
Later, using the web interface on the Firepower Management Center, you must
use the same registration key and, if necessary, the same NAT ID when you add
this sensor to the Firepower Management Center.
Stap 6. Registreer FTD in het VCC
> configure manager add 10.62.148.50 cisco Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC. > show managers Host : 10.62.148.50 Registration Key : **** Registration : pending RPC Status :
Op FMC navigeer naar Apparaten > Apparaatbeheer om het FTD apparaat toe te voegen.
Nadat u FTD in FMC hebt toegevoegd, dient u:
- Configureer de instellingen van het apparaat zoals interfaces en routing
- Beleid zoals VPN en QoS hervormen
- Pas het eerder toegepaste beleid en de eerder toegepaste instellingen zoals het beleid van de Toegangscontrole, NAT en de Instellingen van het platform opnieuw toe
Gerelateerde informatie
Bijgedragen door Cisco-engineers
- Mikis ZafeiroudisCisco TAC-ingenieur
- Dinkar SharmaCisco TAC-ingenieur
- Olha YakovenkoCisco TAC-ingenieur
Contact Cisco
- Een ondersteuningscase openen

- (Vereist een Cisco-servicecontract)
 Feedback
Feedback