Wi-Fi 6E WLAN에서 레이어 3 보안 구성 및 확인
편견 없는 언어
본 제품에 대한 문서 세트는 편견 없는 언어를 사용하기 위해 노력합니다. 본 설명서 세트의 목적상, 편견 없는 언어는 나이, 장애, 성별, 인종 정체성, 민족 정체성, 성적 지향성, 사회 경제적 지위 및 교차성에 기초한 차별을 의미하지 않는 언어로 정의됩니다. 제품 소프트웨어의 사용자 인터페이스에서 하드코딩된 언어, RFP 설명서에 기초한 언어 또는 참조된 서드파티 제품에서 사용하는 언어로 인해 설명서에 예외가 있을 수 있습니다. 시스코에서 어떤 방식으로 포용적인 언어를 사용하고 있는지 자세히 알아보세요.
이 번역에 관하여
Cisco는 전 세계 사용자에게 다양한 언어로 지원 콘텐츠를 제공하기 위해 기계 번역 기술과 수작업 번역을 병행하여 이 문서를 번역했습니다. 아무리 품질이 높은 기계 번역이라도 전문 번역가의 번역 결과물만큼 정확하지는 않습니다. Cisco Systems, Inc.는 이 같은 번역에 대해 어떠한 책임도 지지 않으며 항상 원본 영문 문서(링크 제공됨)를 참조할 것을 권장합니다.
소개
이 문서에서는 Wi-Fi 6E WLAN에서 레이어 3 보안을 구성하는 방법 및 여러 클라이언트에서 예상되는 사항에 대해 설명합니다.
사전 요구 사항
요구 사항
다음 주제에 대한 지식을 보유하고 있으면 유용합니다.
- Cisco WLC(Wireless Lan Controller) 9800
- Wi-Fi 6E를 지원하는 Cisco AP(액세스 포인트)
- IEEE 표준 802.11ax.
- 도구: Wireshark v4.0.6
사용되는 구성 요소
이 문서의 정보는 다음 소프트웨어 및 하드웨어 버전을 기반으로 합니다.
- IOS® XE 17.9.4가 포함된 WLC 9800-CL
- AP C9136, CW9162, CW9164 및 CW9166.
- Wi-Fi 6E 클라이언트
- Lenovo X1 Carbon Gen11(Intel AX211 Wi-Fi 6 및 6E 어댑터, 드라이버 버전 22.200.2(1).
- Android 13이 있는 휴대폰 픽셀 6a;
- 휴대 전화 삼성 S23 안드로이드 13.
이 문서의 정보는 특정 랩 환경의 디바이스를 토대로 작성되었습니다. 이 문서에 사용된 모든 디바이스는 초기화된(기본) 컨피그레이션으로 시작되었습니다. 현재 네트워크가 작동 중인 경우 모든 명령의 잠재적인 영향을 미리 숙지하시기 바랍니다.
배경 정보
Wi-Fi 6E는 완전히 새로운 표준이 아니라 확장형이라는 것을 알아야 합니다. Wi-Fi 6E는 기본적으로 Wi-Fi 6(802.11ax) 무선 표준을 6GHz 무선 주파수 대역으로 확장한 것입니다.
Wi-Fi 6E는 최신 Wi-Fi 표준인 Wi-Fi 6를 기반으로 구축되지만, Wi-Fi 6E 장치 및 애플리케이션만 6GHz 대역에서 작동할 수 있습니다.
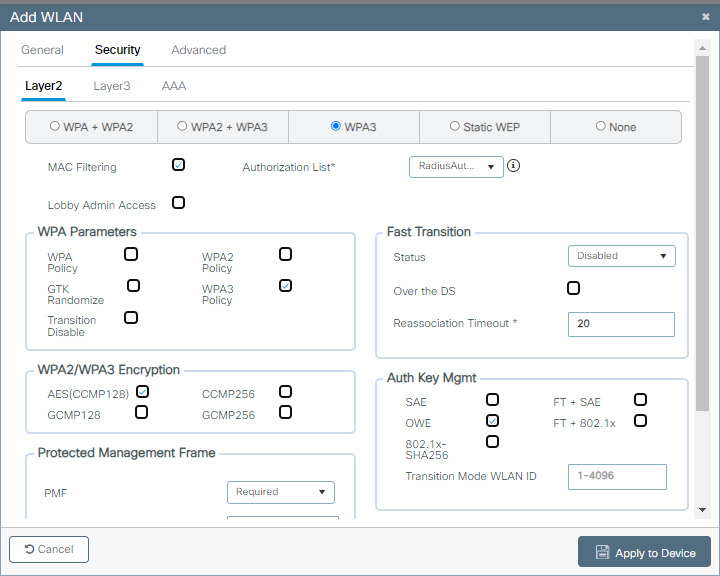
WiFi 6E의 레이어 3 보안은 WiFi 5 또는 6과 동일하며, 어떤 시나리오에서도 웹 인증 흐름이 다르지 않다는 의미입니다. WiFI 6E에서 레이어 3 보안을 사용하는 것의 유일한 차이점은 WiFI 6E의 모든 WLAN에는 WiFi 6E에서 필수인 WPA3 및 PMF로 구성된 레이어 2 보안이 있어야 한다는 사실입니다.
WiFi 6E Layer 2 보안에 대한 자세한 내용은 Wi-Fi 6E WLAN Layer 2 보안 구성 및 확인 문서를 참조하십시오.
웹 인증
웹 인증은 개방형 인증 또는 적절한 레이어 2 보안 방법을 통해 WLAN의 호스트에 쉽고 안전한 게스트 액세스를 제공하도록 설계된 레이어 3 보안 솔루션입니다.
다음은 다양한 유형의 웹 인증 방법입니다.
-
LWA(Local Web Authentication: 로컬 웹 인증): 컨트롤러에서 레이어 3 보안으로 구성되며, 웹 인증 페이지 및 사전 인증 ACL은 컨트롤러에서 로컬로 구성됩니다. 컨트롤러는 http(s) 트래픽을 인터셉트하고 인증을 위해 클라이언트를 내부 웹 페이지로 리디렉션합니다. 클라이언트가 로그인 페이지에서 입력한 자격 증명은 컨트롤러에서 로컬로 또는 RADIUS 또는 LDAP 서버를 통해 인증됩니다.
-
EWA(External Web Authentication): 컨트롤러에서 레이어 3 보안으로 구성된 컨트롤러는 http(s) 트래픽을 인터셉트하고 클라이언트를 외부 웹 서버에 호스팅된 로그인 페이지로 리디렉션합니다. 클라이언트가 로그인 페이지에서 입력한 자격 증명은 컨트롤러에서 로컬로 또는 RADIUS 또는 LDAP 서버를 통해 인증됩니다. 사전 인증 ACL은 컨트롤러에서 정적으로 구성됩니다.
-
CWA(Central Web Authentication): 컨트롤러에서 대부분 레이어 2 보안으로 구성되며, 리디렉션 URL 및 사전 인증 ACL은 ISE에 상주하며 레이어 2 인증 중에 컨트롤러에 푸시됩니다. 컨트롤러는 클라이언트의 모든 웹 트래픽을 ISE 로그인 페이지로 리디렉션합니다. ISE는 HTTPS를 통해 클라이언트가 입력한 자격 증명을 검증하고 사용자를 인증합니다.
자세한 내용은 Cisco Catalyst 9800 Series Controller의 웹 기반 인증 문서를 참조하십시오.
전통적으로 Wi-Fi 핫스팟과 게스트 WLAN은 암호화나 인증 없이 개방형 보안을 사용했습니다. Wi-Fi CERTIFIED Enhanced Open Certification은 개방형 Wi-Fi 네트워크에서 향상된 데이터 프라이버시를 정의합니다.
이 인증은 OWE(Opportunistic Wireless Encryption) 프로토콜을 기반으로 합니다. OWE는 IETF RFC 8110에 정의되어 있습니다. OWE 프로토콜은 설정된 암호화 메커니즘을 통합하여 각 사용자에게 고유한 개별 암호화를 제공하여 사용자와 액세스 포인트 간의 데이터 교환을 보호합니다.
OWE는 Cryptography 기반의 Diffie-Hellman 알고리즘을 사용하여 무선 암호화를 설정합니다. OWE를 사용하면 클라이언트와 AP는 액세스 절차 중에 Diffie-Hellman 키 교환을 수행하고 4-way 핸드셰이크로 결과 PMK(pairwise master key) 암호를 사용합니다.
다음 다이어그램에서 볼 수 있듯이 표준 개방 인증 및 연결이 수행된 다음 4방향 핸드셰이크 프로세스에서 암호화에 필요한 키를 생성합니다.
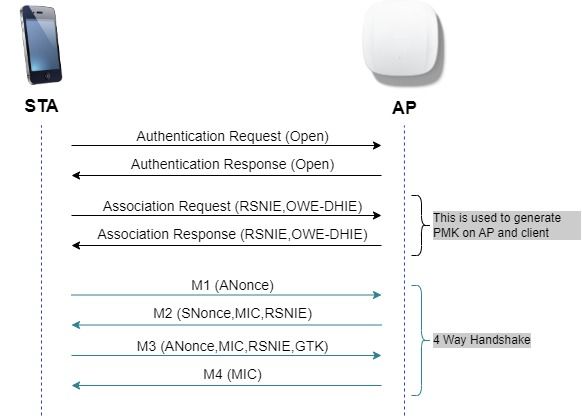 OWE 프레임 교환
OWE 프레임 교환
자세한 내용은 Configure Enhanced Open SSID with Transition Mode - OWE에서 확인할 수 있습니다.
OWE는 WiFi 6E에서 열린 네트워크의 자연스러운 후속 버전이므로 이 문서에서는 WiFi6E 규정 준수를 위해 OWE를 레이어 2 보안으로 사용합니다.
Cisco Catalyst Wi-Fi 6E AP
이 문서를 작성할 때 사용할 수 있는 WiFi 6E AP에 대한 빠른 참조:
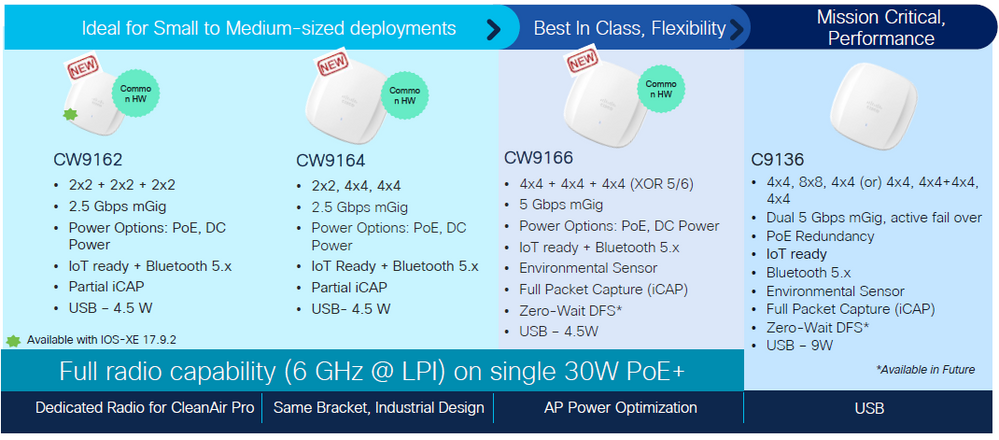 Wi-Fi 6E 액세스 포인트
Wi-Fi 6E 액세스 포인트
구성 및 확인
이 섹션에서는 L3 인증을 사용하여 WiFi 6E 클라이언트와 WLAN의 연결을 구성하고 확인하는 방법을 보여줍니다.
레이어 2 보안 설정은 WiFi 6E에서 사용할 수 있는 "개방형" 네트워크에 가장 가까운 OWE(Opportunistic Wireless Encryption)에 잠깁니다.
WiFi 6E를 사용하여 다음 유형의 웹 인증을 구성하고 확인합니다.
- 로컬 웹 인증
- 외부 웹 인증
- 중앙 웹 인증
네트워크 다이어그램
이 문서에서 사용된 랩 설정 다이어그램입니다.
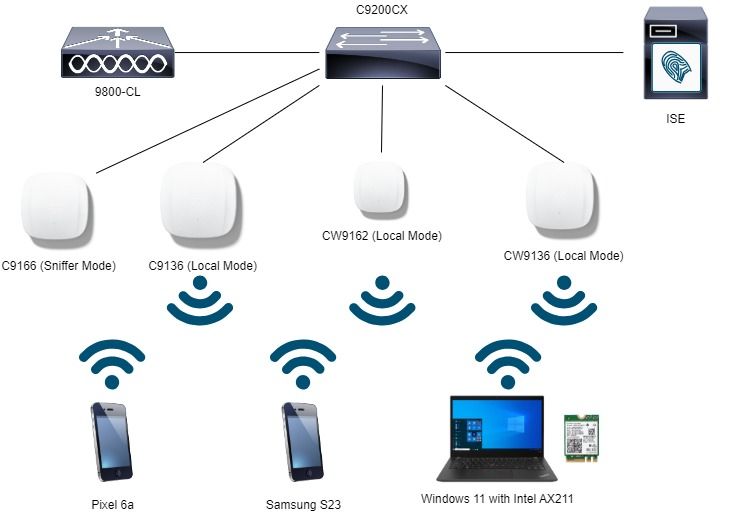 네트워크 다이어그램
네트워크 다이어그램
로컬 웹 인증으로 OWE 구성
1단계. 로컬 웹 인증을 위한 매개변수 맵을 만듭니다.
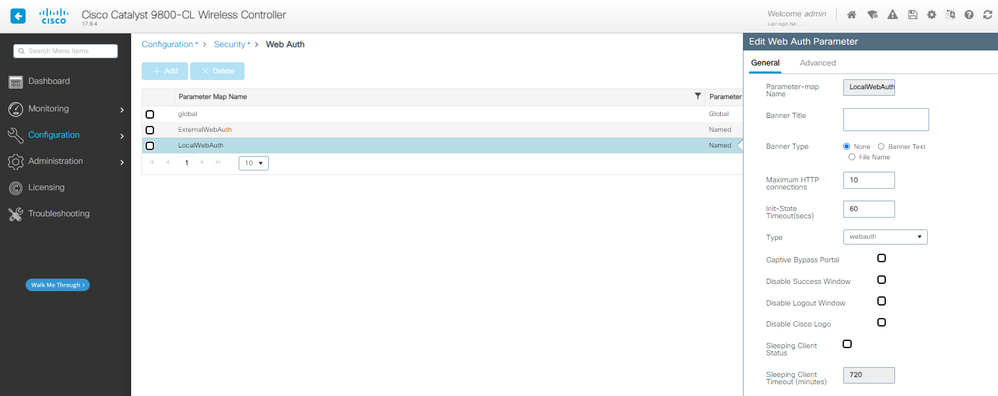 LWA 매개변수 맵
LWA 매개변수 맵
2단계. 이 예에서는 클라이언트 인증에 외부 사용자 데이터베이스를 사용합니다. AAA 서버는 ISE입니다. RADIUS 서버 및 인증 프로필을 구성합니다.
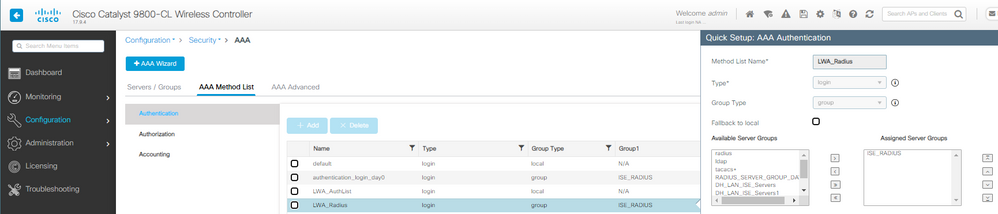 LWA AAA 인증 방법
LWA AAA 인증 방법
3단계. OWE Layer 2 보안 및 웹 인증을 사용하여 WLAN을 Layer 3 보안으로 구성합니다. LocalWebAuth 매개변수 맵 및 LWA_Radius 인증 목록을 선택했는지 확인합니다.
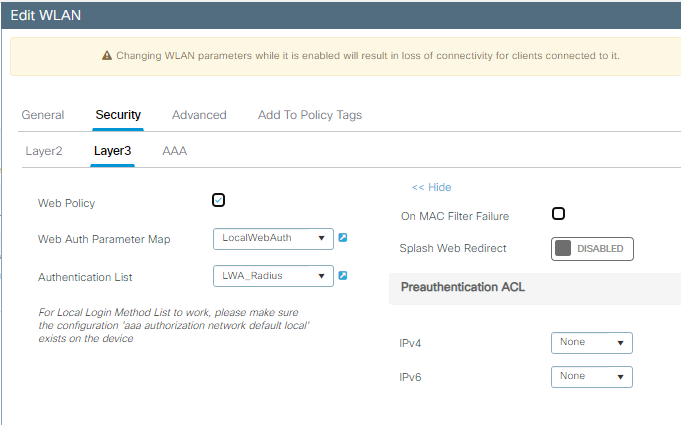 LWA Layer 3 컨피그레이션 세부사항이 포함된 OWE
LWA Layer 3 컨피그레이션 세부사항이 포함된 OWE
WLAN은 오른쪽에 표시된 보안 설정을 생성합니다.
 WLAN은 LWA L3 보안과 함께 해야 함
WLAN은 LWA L3 보안과 함께 해야 함
4단계. WLAN을 정책 태그의 정책 프로필에 매핑합니다.
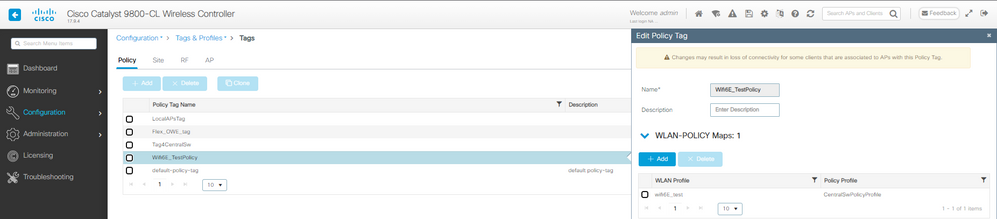 LWA 정책 태그 컨피그레이션
LWA 정책 태그 컨피그레이션
5단계. AP에 정책 태그를 할당합니다.
6단계. 그에 따라 ISE를 구성합니다.

참고: 자세한 컨피그레이션은 문서 Configure Local Web Authentication with External Authentication(외부 인증을 사용하여 로컬 웹 인증 구성)을 참조하십시오.
다음을 확인합니다.
로컬 웹 인증의 확인 섹션입니다.
CLI에서 컨피그레이션을 확인합니다.
!
aaa new-model
!
aaa group server radius ISE_RADIUS
server name PSN01
deadtime 5
load-balance method least-outstanding
subscriber mac-filtering security-mode mac
mac-delimiter colon
!
aaa authentication login LWA_Radius group ISE_RADIUS
!
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
trustpoint eWLC-9800-01_WLC_TP
webauth-http-enable
!
parameter-map type webauth LocalWebAuth
type webauth
timeout init-state sec 60
max-http-conns 10
custom-page login device bootflash:/custom_webauth/login.html
custom-page success device bootflash:/custom_webauth/aup.html
custom-page failure device bootflash:/custom_webauth/failed.html
custom-page login expired device bootflash:/custom_webauth/logout.html
!
radius server PSN01
address ipv4 192.168.1.7 auth-port 1812 acct-port 1813
key 7 xxxxxxxxxxxx
!
wireless profile policy CentralSwPolicyProfile
!
ipv4 dhcp required
vlan default
no shutdown
!
wireless tag policy Wifi6E_TestPolicy
wlan wifi6E_test policy CentralSwPolicyProfile
!
wlan wifi6E_test 5 wifi6E_test
dot11ax target-waketime
dot11ax twt-broadcast-support
radio policy dot11 6ghz
no security ft adaptive
no security wpa wpa2
no security wpa akm dot1x
security wpa akm owe
security wpa wpa3
security dot1x authentication-list ISE_RADIUS
security pmf mandatory
security web-auth
security web-auth authentication-list LWA_Radius
security web-auth parameter-map LocalWebAuth
no shutdown
!
여기서는 AX211 클라이언트를 사용하여 OWE 단계를 관찰합니다. WLC 인터페이스의 EPC입니다.
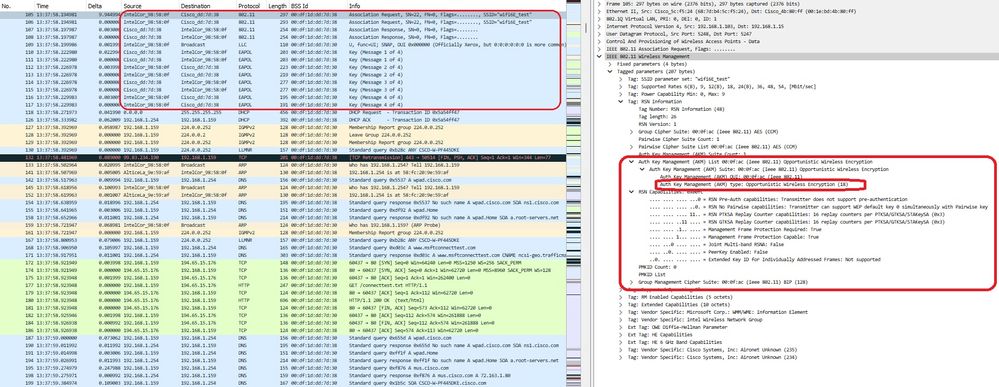 LWA OWE ASSOCIATION
LWA OWE ASSOCIATION
그 다음에는 DHCP, DNS 및 HTTP 리디렉션이 옵니다.
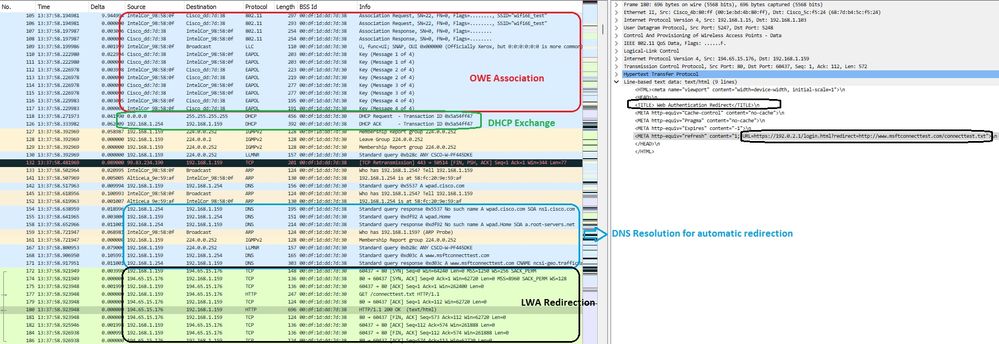 LWA OWE 리디렉션
LWA OWE 리디렉션
WLC GUI에서 클라이언트 세부사항을 볼 수 있습니다.
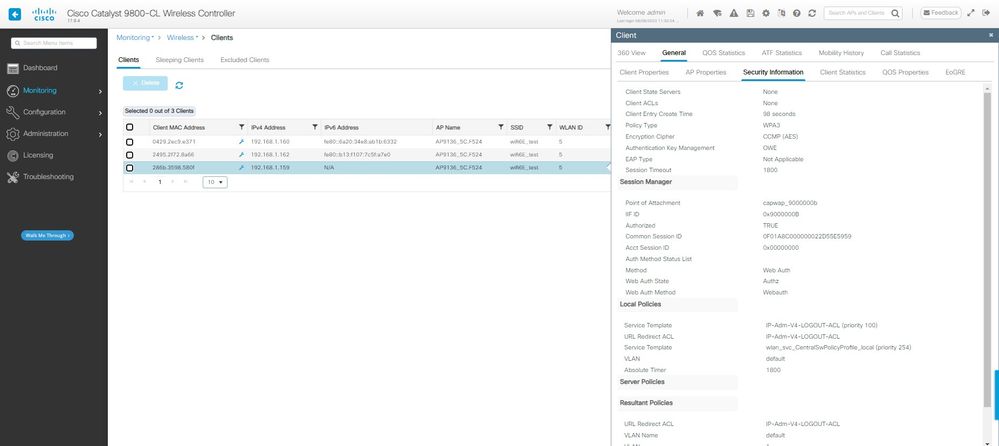 WLC GUI에서 LWA OWE 클라이언트 세부 정보
WLC GUI에서 LWA OWE 클라이언트 세부 정보
외부 웹 인증으로 OWE 구성
1단계. 외부 웹 인증을 위한 매개변수 맵을 만듭니다.
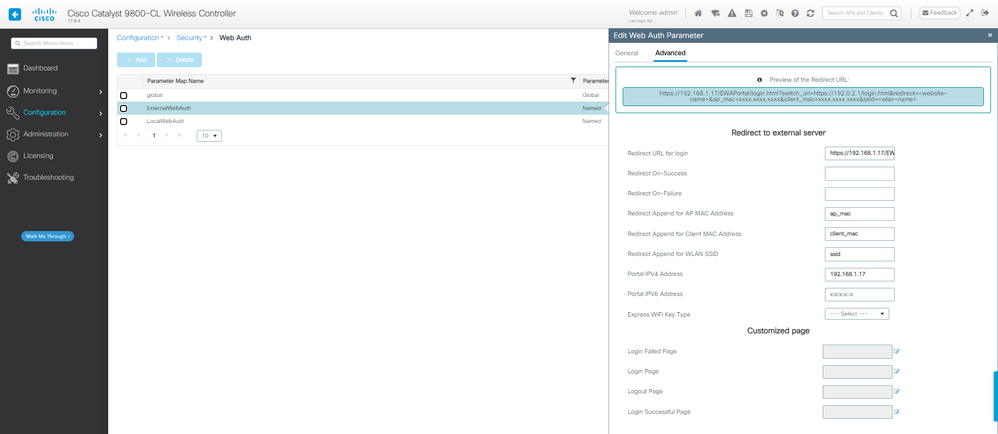 EWA 매개변수 맵
EWA 매개변수 맵
2단계. 이 예에서는 클라이언트 인증에 외부 사용자 데이터베이스를 사용합니다. AAA 서버는 ISE입니다. RADIUS 서버 및 인증 프로필을 구성합니다.
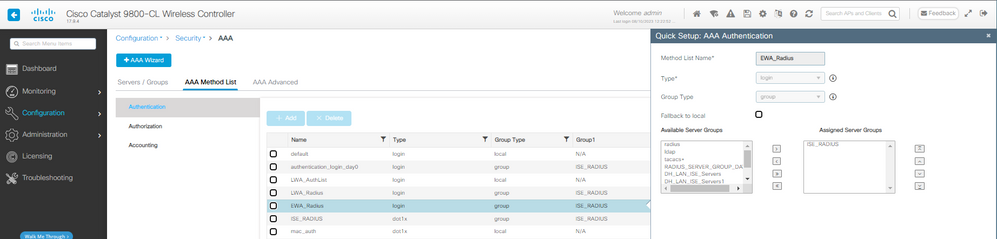 AAA 인증 방법 컨피그레이션
AAA 인증 방법 컨피그레이션
3단계. OWE Layer 2 보안 및 웹 인증을 사용하여 WLAN을 Layer 3 보안으로 구성합니다. ExternalWebAuth Parameter(외부 웹 인증 매개변수) 맵 및 EWA_Radius 인증 목록을 선택해야 합니다.
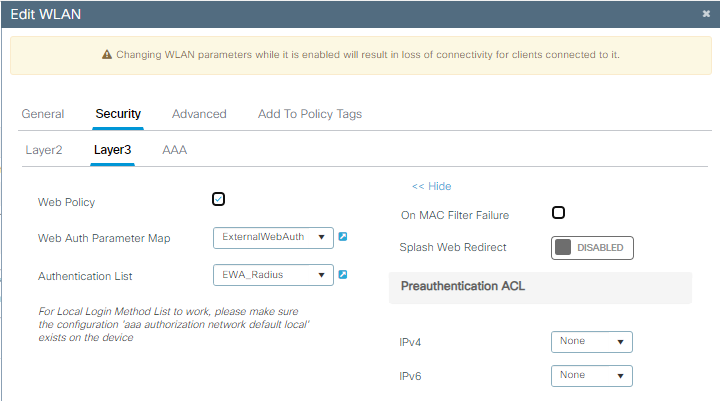 OWE EWA 보안 컨피그레이션
OWE EWA 보안 컨피그레이션
WLAN은 오른쪽에 표시된 보안 설정을 생성합니다.
 OWE EWA 보안 설정
OWE EWA 보안 설정
4단계. WLAN을 정책 태그의 정책 프로필에 매핑합니다.
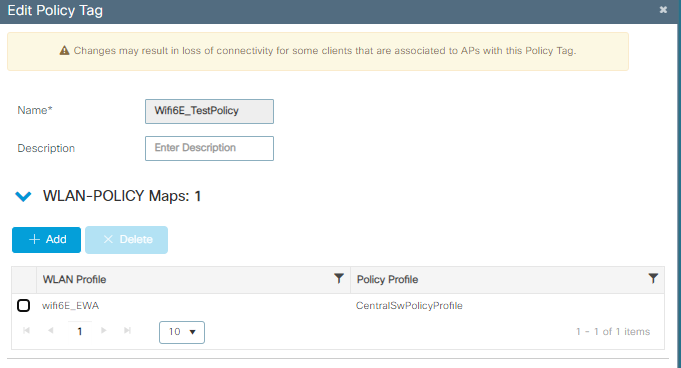 정책 태그 구성
정책 태그 구성
5단계. AP에 정책 태그를 할당합니다.
6단계. 그에 따라 ISE를 구성합니다.

참고: 자세한 컨피그레이션은 문서 9800 WLC에서 외부 웹 인증 구성 및 문제 해결을 참조하십시오.
다음을 확인합니다.
외부 웹 인증의 확인 섹션입니다.
CLI에서 컨피그레이션을 확인합니다.
!
aaa new-model
!
aaa group server radius ISE_RADIUS
server name PSN01
deadtime 5
load-balance method least-outstanding
subscriber mac-filtering security-mode mac
mac-delimiter colon
!
aaa authentication login EWA_Radius group ISE_RADIUS
!
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
trustpoint eWLC-9800-01_WLC_TP
webauth-http-enable
!
parameter-map type webauth ExternalWebAuth
type webauth
timeout init-state sec 60
redirect for-login https://192.168.1.17/EWAPortal/login.html
redirect append ap-mac tag ap_mac
redirect append client-mac tag client_mac
redirect append wlan-ssid tag ssid
redirect portal ipv4 192.168.1.17
max-http-conns 10
!
radius server PSN01
address ipv4 192.168.1.7 auth-port 1812 acct-port 1813
key 7 xxxxxxxxxxxx
!
wireless profile policy CentralSwPolicyProfile
!
ipv4 dhcp required
vlan default
no shutdown
!
wireless tag policy Wifi6E_TestPolicy
wlan wifi6E_EWA policy CentralSwPolicyProfile
!
wlan wifi6E_EWA 6 wifi6E_EWA
radio policy dot11 6ghz
no security ft adaptive
no security wpa wpa2
no security wpa akm dot1x
security wpa akm owe
security wpa wpa3
security pmf mandatory
security web-auth
security web-auth authentication-list EWA_Radius
security web-auth parameter-map ExternalWebAuth
no shutdown
!
여기에서는 Samsung S23을 사용하여 OTA OWE 단계를 관찰할 수 있습니다.
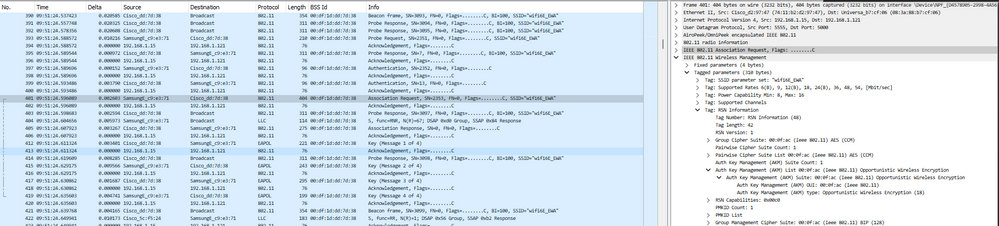 EWA WLAN 연결/인증에 대한 세부 정보
EWA WLAN 연결/인증에 대한 세부 정보
DHCP, DNS 및 HTTP 리디렉션이 그 뒤에 옵니다. OTA 트래픽이 암호화되기 때문에 이 캡처는 WLC에서 EPC를 통한 보기입니다.
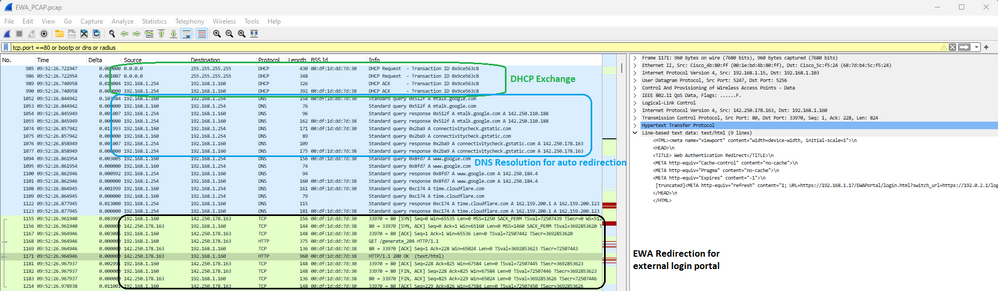 EWA의 패킷 캡처 세부사항
EWA의 패킷 캡처 세부사항
이 단계에서 클라이언트는 웹 인증 보류 중입니다.
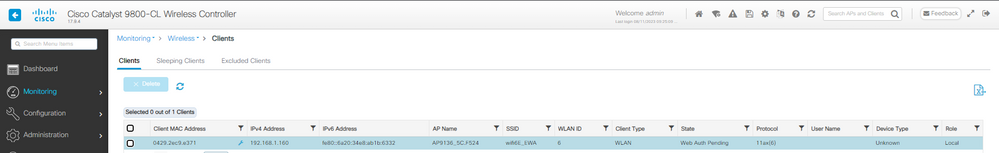 웹 인증 보류 중인 EWA 클라이언트
웹 인증 보류 중인 EWA 클라이언트
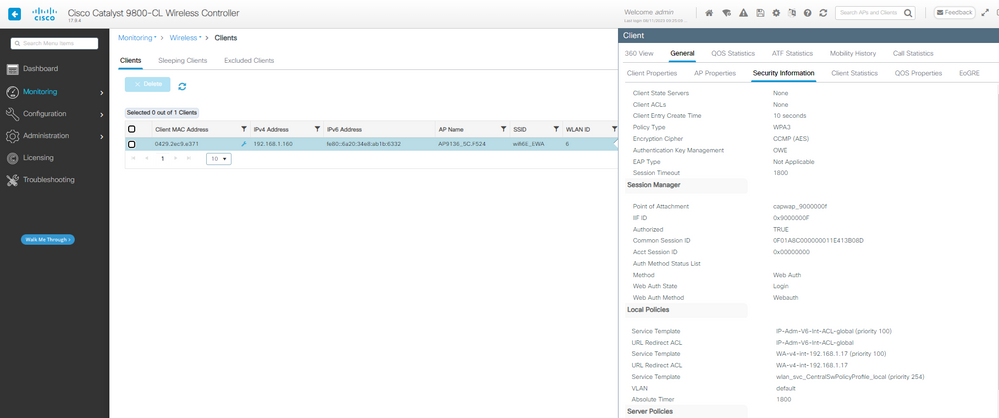 EWA 웹 인증의 클라이언트 보안 세부 정보 보류 중
EWA 웹 인증의 클라이언트 보안 세부 정보 보류 중
WLC에서 ISE로 제공된 자격 증명의 Radius 인증:
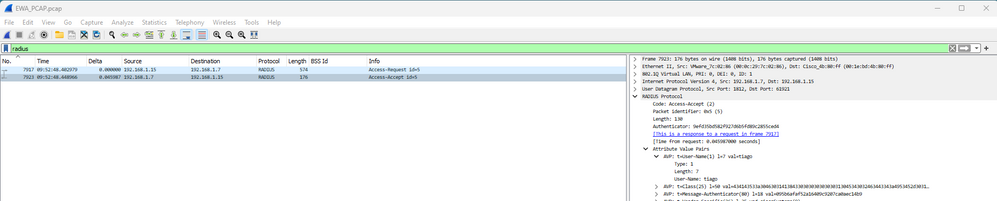 EWA Radius 인증
EWA Radius 인증
그리고 성공적으로 로그인하면 클라이언트 세부사항이 표시됩니다.
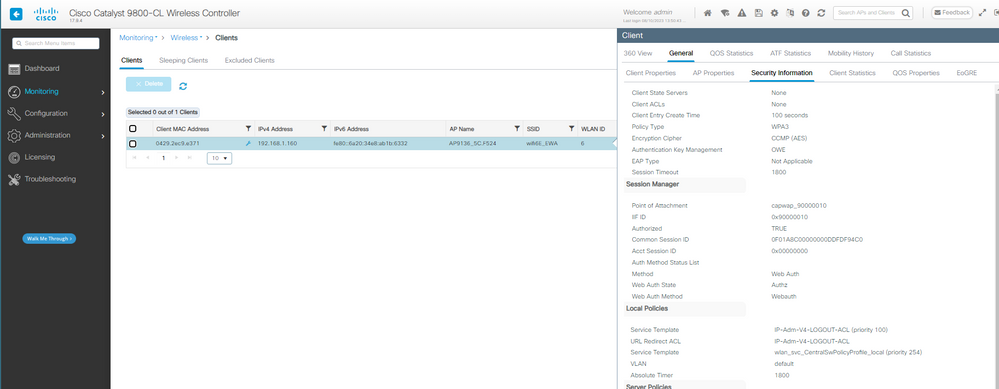 OWE EWA 클라이언트 세부사항
OWE EWA 클라이언트 세부사항
중앙 웹 인증으로 OWE 구성
1단계. 리디렉션 ACL 생성:
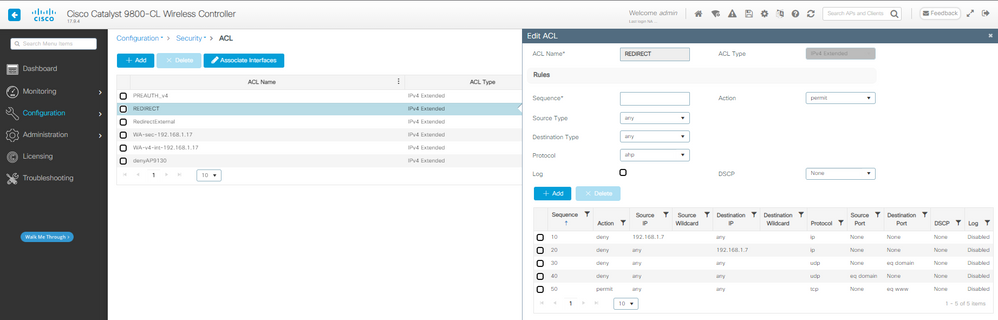 CWA 리디렉션 ACL
CWA 리디렉션 ACL
2단계. mac 필터링에 사용할 권한 부여 방법을 생성합니다.
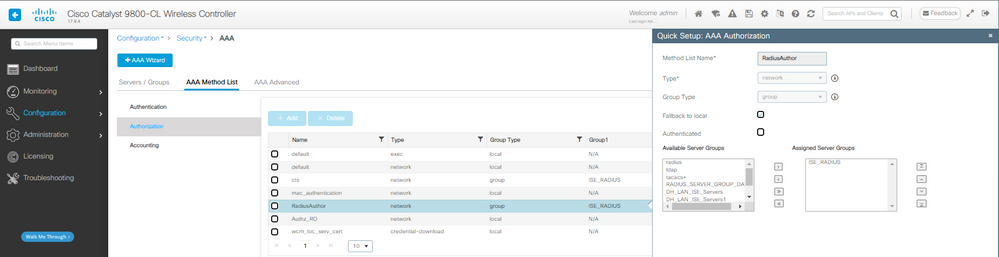 CWA AAA 권한 부여 방법
CWA AAA 권한 부여 방법
3단계. OWE Layer 2 보안 및 mac 필터링으로 WLAN을 구성합니다. 이전에 생성한 권한 부여 목록을 선택합니다.
 OWE CWA 보안 컨피그레이션
OWE CWA 보안 컨피그레이션
WLAN은 오른쪽에 표시된 보안 설정을 생성합니다.
 OWE CWA 보안 설정
OWE CWA 보안 설정
4단계. AAA 재정의 및 Radius NAC가 활성화된 정책 프로파일을 생성합니다.
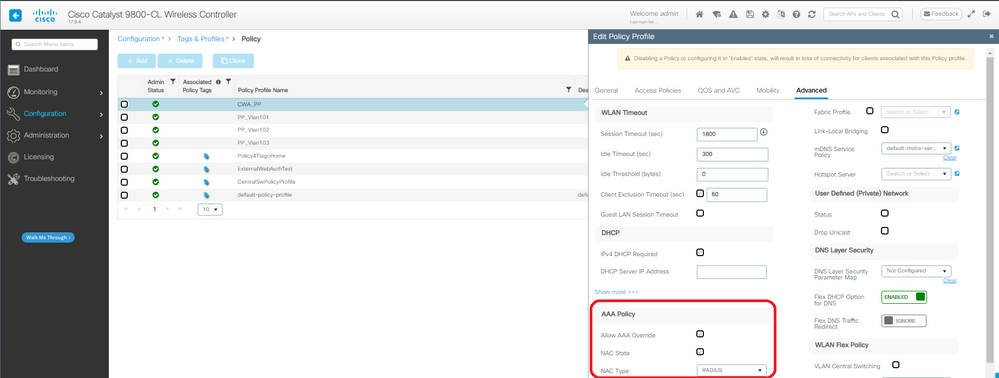 CWA 정책 프로필
CWA 정책 프로필
5단계. WLAN을 정책 태그의 정책 프로필에 매핑합니다.
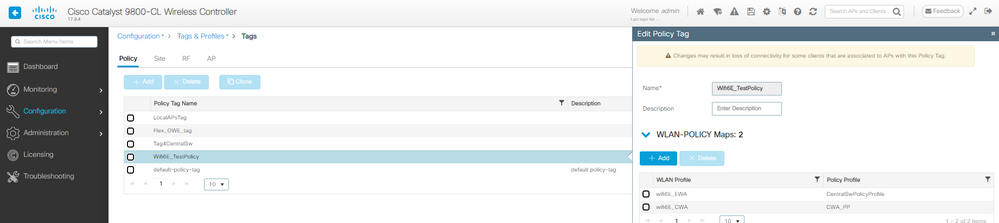 CWA 정책 태그
CWA 정책 태그
6단계. AP에 정책 태그를 할당합니다.
7단계. 그에 따라 ISE를 구성합니다.

참고: 자세한 CWA 컨피그레이션은 Catalyst 9800 WLC 및 ISE에서 CWA(Central Web Authentication) 구성 문서를 참조하십시오.
다음을 확인합니다.
중앙 웹 인증의 확인 섹션입니다.
CLI에서 컨피그레이션을 확인합니다.
!
aaa new-model
!
aaa group server radius ISE_RADIUS
server name PSN01
deadtime 5
load-balance method least-outstanding
subscriber mac-filtering security-mode mac
mac-delimiter colon
!
aaa authorization network RadiusAuthor group ISE_RADIUS local
!
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
trustpoint eWLC-9800-01_WLC_TP
webauth-http-enable
!
radius server PSN01
address ipv4 192.168.1.7 auth-port 1812 acct-port 1813
key 7 xxxxxxxxxxxx
!
wireless profile policy CentralSwPolicyProfile
!
ipv4 dhcp required
vlan default
no shutdown
!
wireless tag policy Wifi6E_TestPolicy
wlan wifi6E_CWA policy CentralSwPolicyProfile
!
wlan wifi6E_CWA 7 wifi6E_CWA
mac-filtering RadiusAuthor
radio policy dot11 6ghz
no security ft adaptive
no security wpa wpa2
no security wpa akm dot1x
security wpa akm owe
security wpa wpa3
security pmf mandatory
no shutdown
!
여기서 우리는 픽셀 6a를 사용하여 OTA를 관찰할 수 있다.
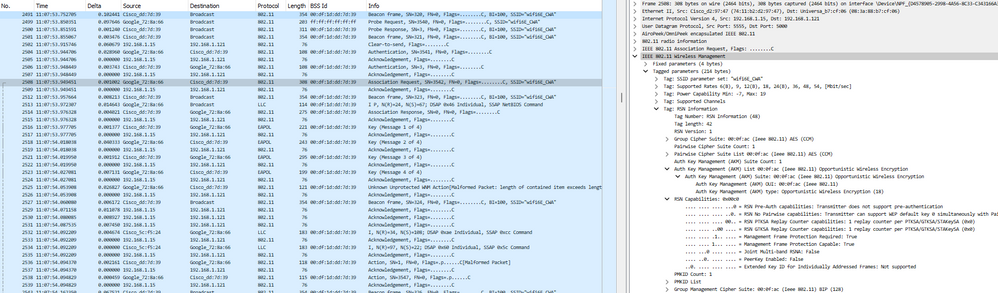 CWA OTA 연결 부채
CWA OTA 연결 부채
그런 다음 mac 필터링을 위한 Radius Exchange가 있습니다.
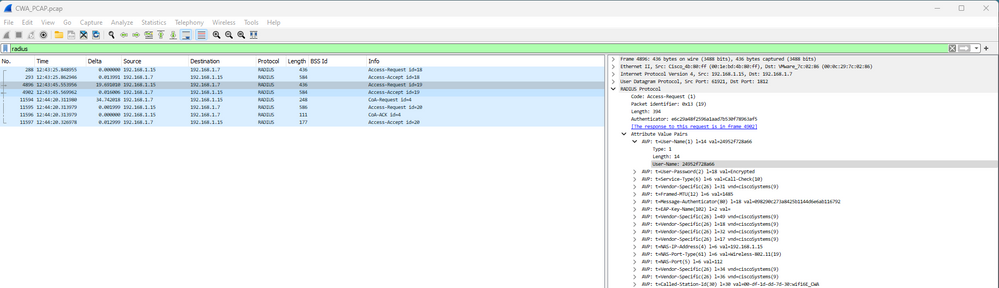 OEW CWA Mac 필터링
OEW CWA Mac 필터링
그 다음에는 DHCP, DNS 및 HTTP 리디렉션이 옵니다.
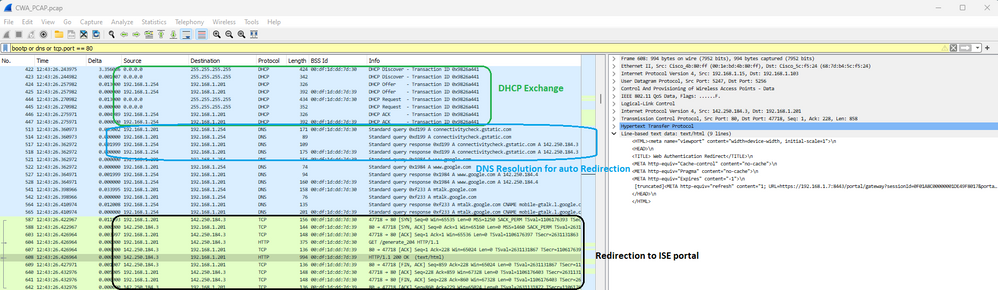 CWA DHCP, DNS 및 리디렉션
CWA DHCP, DNS 및 리디렉션
ISE 라이브 로그에서는 CWA 리디렉션을 볼 수 있습니다.
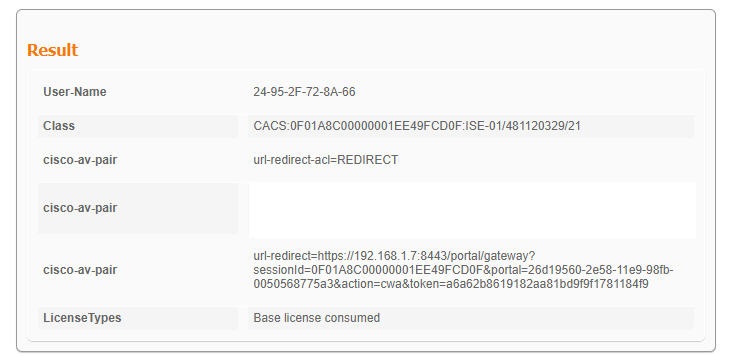 CWA 리디렉션 URL 및 ACL
CWA 리디렉션 URL 및 ACL
ISE 라이브 로그는 클라이언트가 게스트 자격 증명을 입력하고 인증을 통과했음을 보여줍니다.
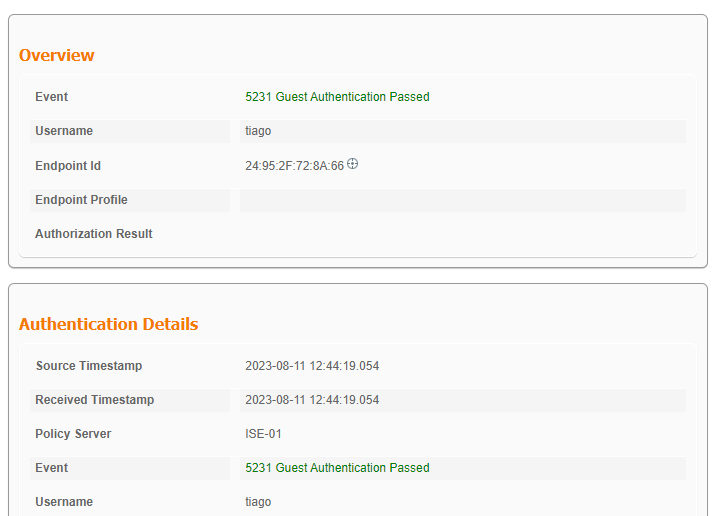 CWA 게스트 로그인 성공
CWA 게스트 로그인 성공
그리고 성공적으로 로그인하면 클라이언트 세부사항이 표시됩니다.
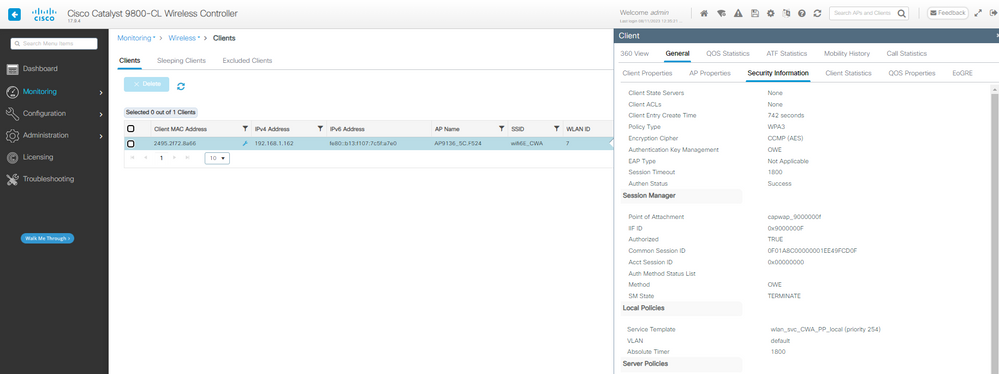 WLC GUI에서 CWA 클라이언트 세부 정보 확인
WLC GUI에서 CWA 클라이언트 세부 정보 확인
문제 해결
이 문서에서 사용된 문제 해결은 온라인 문서를 기반으로 합니다.
트러블슈팅에 대한 일반적인 지침은 클라이언트가 임의 MAC 주소가 아닌 장치 MAC을 사용하여 연결하는지 확인하기 위해 클라이언트 MAC 주소를 사용하여 WLC에서 디버그 모드에서 RA 추적을 수집하는 것입니다.
무선 문제 해결의 경우 클라이언트 서비스 AP의 채널에서 트래픽을 캡처하는 스니퍼 모드에서 AP를 사용하는 것이 좋습니다.

참고: debug 명령을 사용하기 전에 Debug 명령에 대한 중요 정보를 참조하십시오.
LWA와 함께 해야 할 일
여기서는 RA 추적에서 LWA의 예를 볼 수 있습니다.
2023/08/08 13:37:58.196529135 {wncd_x_R0-0}{1}: [client-orch-sm] [15154]: (note): MAC: 286b.3598.580f Association received. BSSID 00df.1ddd.7d38, WLAN wifi6E_test, Slot 3 AP 00df.1ddd.7d30, AP9136_5C.F524
[...]
2023/08/08 13:37:58.198092314 {wncd_x_R0-0}{1}: [dot11] [15154]: (note): MAC: 286b.3598.580f Association success. AID 36, Roaming = False, WGB = False, 11r = False, 11w = True Fast roam = False
[...]
2023/08/08 13:37:58.198287303 {wncd_x_R0-0}{1}: [client-orch-sm] [15154]: (debug): MAC: 286b.3598.580f Starting L2 authentication. Bssid in state machine:00df.1ddd.7d38 Bssid in request is:00df.1ddd.7d38
2023/08/08 13:37:58.198308994 {wncd_x_R0-0}{1}: [client-orch-state] [15154]: (note): MAC: 286b.3598.580f Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
[...]
2023/08/08 13:37:58.200859342 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [15154]: (note): Authentication Success. Resolved Policy bitmap:11 for client 286b.3598.580f
[...]
2023/08/08 13:37:58.222523865 {wncd_x_R0-0}{1}: [client-auth] [15154]: (info): MAC: 286b.3598.580f Client auth-interface state transition: S_AUTHIF_ADD_MOBILE_ACK_WAIT_KM -> S_AUTHIF_PSK_AUTH_KEY_XCHNG_PENDING
2023/08/08 13:37:58.222547149 {mobilityd_R0-0}{1}: [mm-client] [16404]: (debug): MAC: 0000.0000.0000 Received pmk_update, sub type: 0 of XID (0) from (WNCD[0])
2023/08/08 13:37:58.222630557 {mobilityd_R0-0}{1}: [mm-dgram-io] [16404]: (debug): MAC: 0000.0000.0000 Sending message: pmk_update to group: holyfountain
2023/08/08 13:37:58.222641428 {mobilityd_R0-0}{1}: [mm-dgram-io] [16404]: (debug): MAC: 0000.0000.0000 Failed to send message: pmk_update, total configured peers: 2, no active peers
2023/08/08 13:37:58.222666535 {wncd_x_R0-0}{1}: [client-keymgmt] [15154]: (info): MAC: 286b.3598.580f EAP key M1 Sent successfully
2023/08/08 13:37:58.222678418 {wncd_x_R0-0}{1}: [client-keymgmt] [15154]: (info): MAC: 286b.3598.580f Client key-mgmt state transition: S_INITPMK -> S_PTK_START
2023/08/08 13:37:58.227626495 {wncd_x_R0-0}{1}: [client-keymgmt] [15154]: (info): MAC: 286b.3598.580f M2 Status: EAP key M2 validation success
2023/08/08 13:37:58.227791247 {wncd_x_R0-0}{1}: [client-keymgmt] [15154]: (info): MAC: 286b.3598.580f EAP key M3 Sent successfully
2023/08/08 13:37:58.227792680 {wncd_x_R0-0}{1}: [client-keymgmt] [15154]: (info): MAC: 286b.3598.580f Client key-mgmt state transition: S_PTK_START -> S_PTKINITNEGOTIATING
2023/08/08 13:37:58.230572903 {wncd_x_R0-0}{1}: [client-keymgmt] [15154]: (info): MAC: 286b.3598.580f M4 Status: EAP key M4 validation is successful
2023/08/08 13:37:58.230575999 {wncd_x_R0-0}{1}: [client-keymgmt] [15154]: (note): MAC: 286b.3598.580f EAP Key management successful. AKM:OWE Cipher:CCMP WPA Version: WPA3
2023/08/08 13:37:58.230603571 {wncd_x_R0-0}{1}: [client-keymgmt] [15154]: (info): MAC: 286b.3598.580f Client key-mgmt state transition: S_PTKINITNEGOTIATING -> S_PTKINITDONE
2023/08/08 13:37:58.230702678 {wncd_x_R0-0}{1}: [client-auth] [15154]: (note): MAC: 286b.3598.580f L2 Authentication initiated. method WEBAUTH, Policy VLAN 0, AAA override = 1
2023/08/08 13:37:58.230791777 {wncd_x_R0-0}{1}: [auth-mgr] [15154]: (info): [286b.3598.580f:capwap_9000000b] Session Start event called from SANET-SHIM, vlan: 0
2023/08/08 13:37:58.230807848 {wncd_x_R0-0}{1}: [auth-mgr] [15154]: (info): [286b.3598.580f:capwap_9000000b] Wireless session sequence, create context with method WebAuth
2023/08/08 13:37:58.230831713 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [15154]: (info): [286b.3598.580f:capwap_9000000b] - authc_list: LWA_Radius
2023/08/08 13:37:58.230834488 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [15154]: (info): [286b.3598.580f:capwap_9000000b] - authz_list: Not present under wlan configuration
2023/08/08 13:37:58.230857151 {wncd_x_R0-0}{1}: [client-auth] [15154]: (info): MAC: 286b.3598.580f Client auth-interface state transition: S_AUTHIF_PSK_AUTH_KEY_XCHNG_PENDING -> S_AUTHIF_L2_WEBAUTH_PENDING
2023/08/08 13:37:58.230912145 {wncd_x_R0-0}{1}: [auth-mgr] [15154]: (info): [286b.3598.580f:capwap_9000000b] Raised event RX_IDENTITY_UPDATE (18)
2023/08/08 13:37:58.230915511 {wncd_x_R0-0}{1}: [auth-mgr] [15154]: (info): [286b.3598.580f:capwap_9000000b] SESSION_START from WCM (exp 1476396949, got 1476396949) overriding with latest
2023/08/08 13:37:58.230971648 {wncd_x_R0-0}{1}: [auth-mgr] [15154]: (info): [286b.3598.580f:capwap_9000000b] Retrieved Client IIF ID 0x1476396949x in clientrx event
2023/08/08 13:37:58.230998298 {wncd_x_R0-0}{1}: [auth-mgr] [15154]: (info): [286b.3598.580f:capwap_9000000b] DC Profile-name has been changed to LENOVO 21CCS43W0T
2023/08/08 13:37:58.231001354 {wncd_x_R0-0}{1}: [auth-mgr] [15154]: (info): [286b.3598.580f:capwap_9000000b] DC Device-name has been changed to CSCO-W-PF445DKE
2023/08/08 13:37:58.231043724 {wncd_x_R0-0}{1}: [auth-mgr] [15154]: (info): [286b.3598.580f:capwap_9000000b] Session start (restart) for 286b.3598.580f
[...]
2023/08/08 13:37:58.231245206 {wncd_x_R0-0}{1}: [webauth-state] [15154]: (info): capwap_9000000b[286b.3598.580f][ 0.0.0.0]Param-map used: LocalWebAuth
2023/08/08 13:37:58.231251037 {wncd_x_R0-0}{1}: [webauth-state] [15154]: (info): capwap_9000000b[286b.3598.580f][ 0.0.0.0]State INIT -> INIT
2023/08/08 13:37:58.231273499 {wncd_x_R0-0}{1}: [webauth-acl] [15154]: (info): capwap_9000000b[286b.3598.580f][ 0.0.0.0]Applying IPv4 intercept ACL via SVM, name: IP-Adm-V4-Int-ACL-global, priority: 50, IIF-ID: 0
[...]
2023/08/08 13:37:58.239843453 {wncd_x_R0-0}{1}: [client-iplearn] [15154]: (info): MAC: 286b.3598.580f IP-learn state transition: S_IPLEARN_INIT -> S_IPLEARN_IN_PROGRESS
2023/08/08 13:37:58.239903667 {wncd_x_R0-0}{1}: [client-iplearn] [15154]: (note): MAC: 286b.3598.580f Client IP learn successful. Method: DHCP IP: 192.168.1.159
[...]
2023/08/08 13:37:58.240371152 {wncd_x_R0-0}{1}: [auth-mgr-feat_acct] [15154]: (info): [286b.3598.580f:capwap_9000000b] SM Notified attribute Add/Update addr 192.168.1.159
2023/08/08 13:37:58.240390128 {wncd_x_R0-0}{1}: [client-iplearn] [15154]: (info): MAC: 286b.3598.580f IP-learn state transition: S_IPLEARN_IN_PROGRESS -> S_IPLEARN_COMPLETE
2023/08/08 13:37:58.240437257 {wncd_x_R0-0}{1}: [client-orch-sm] [15154]: (debug): MAC: 286b.3598.580f Received ip learn response. method: IPLEARN_METHOD_DHCP
2023/08/08 13:37:58.240457105 {wncd_x_R0-0}{1}: [client-orch-sm] [15154]: (debug): MAC: 286b.3598.580f Triggered L3 authentication. status = 0x0, Success
2023/08/08 13:37:58.240459018 {wncd_x_R0-0}{1}: [client-orch-state] [15154]: (note): MAC: 286b.3598.580f Client state transition: S_CO_IP_LEARN_IN_PROGRESS -> S_CO_L3_AUTH_IN_PROGRESS
2023/08/08 13:37:58.240527728 {wncd_x_R0-0}{1}: [dot1x] [15154]: (info): [0000.0000.0000:capwap_9000000b] Couldn't find the supplicant in the list
2023/08/08 13:37:58.240760238 {wncd_x_R0-0}{1}: [client-auth] [15154]: (note): MAC: 286b.3598.580f L3 Authentication initiated. LWA
2023/08/08 13:37:58.240767232 {wncd_x_R0-0}{1}: [client-auth] [15154]: (info): MAC: 286b.3598.580f Client auth-interface state transition: S_AUTHIF_L2_WEBAUTH_DONE -> S_AUTHIF_WEBAUTH_PENDING
[...]
2023/08/08 13:37:58.924439975 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60437/5 IO state NEW -> READING
2023/08/08 13:37:58.924590710 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60437/5 Read event, Message ready
2023/08/08 13:37:58.924606621 {wncd_x_R0-0}{1}: [webauth-httpd] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]GET rcvd when in INIT state
2023/08/08 13:37:58.924617631 {wncd_x_R0-0}{1}: [webauth-httpd] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]HTTP GET request
2023/08/08 13:37:58.924646336 {wncd_x_R0-0}{1}: [webauth-httpd] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]Parse GET, src [192.168.1.159] dst [x.x.x.x] url [http://www.msftconnecttest.com/connecttest.txt]
2023/08/08 13:37:58.924811559 {wncd_x_R0-0}{1}: [webauth-httpd] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]Read complete: parse_request return 8
2023/08/08 13:37:58.924823291 {wncd_x_R0-0}{1}: [webauth-state] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]Param-map used: LocalWebAuth
2023/08/08 13:37:58.924830184 {wncd_x_R0-0}{1}: [webauth-state] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]State INIT -> GET_REDIRECT
2023/08/08 13:37:58.924836706 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60437/5 IO state READING -> WRITING
2023/08/08 13:37:58.924893704 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60437/5 IO state WRITING -> END
[...]
2023/08/08 13:38:16.814516928 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60515/217 IO state NEW -> SSL_HANDSHAKING
2023/08/08 13:38:16.814739389 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60516/218 IO state NEW -> SSL_HANDSHAKING
2023/08/08 13:38:16.843721875 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60517/217 IO state NEW -> SSL_HANDSHAKING
2023/08/08 13:38:16.863779947 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60517/217 Read event, Message ready
2023/08/08 13:38:16.863799384 {wncd_x_R0-0}{1}: [webauth-httpd] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]POST rcvd when in LOGIN state
2023/08/08 13:38:16.863812318 {wncd_x_R0-0}{1}: [webauth-httpd] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]get url: /undefined
2023/08/08 13:38:16.863857023 {wncd_x_R0-0}{1}: [webauth-httpd] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]Read complete: parse_request return 4
2023/08/08 13:38:16.863981829 {wncd_x_R0-0}{1}: [caaa-authen] [15154]: (info): [CAAA:AUTHEN:c8000018] NULL ATTR LIST
2023/08/08 13:38:16.864023268 {wncd_x_R0-0}{1}: [webauth-state] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]Param-map used: LocalWebAuth
2023/08/08 13:38:16.864026684 {wncd_x_R0-0}{1}: [webauth-state] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]State LOGIN -> AUTHENTICATING
2023/08/08 13:38:16.864039067 {wncd_x_R0-0}{1}: [webauth-io] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]60517/217 IO state READING -> AUTHENTICATING
2023/08/08 13:38:16.864184873 {wncd_x_R0-0}{1}: [radius] [15154]: (info): RADIUS: Send Access-Request to 192.168.1.7:1812 id 0/5, len 390
2023/08/08 13:38:16.864190705 {wncd_x_R0-0}{1}: [radius] [15154]: (info): RADIUS: authenticator 50 a9 ab 0d 42 ef 39 22 - 33 3d 07 b0 77 78 80 88
2023/08/08 13:38:16.864194552 {wncd_x_R0-0}{1}: [radius] [15154]: (info): RADIUS: Calling-Station-Id [31] 19 "28-6b-35-98-58-0f"
2023/08/08 13:38:16.864197568 {wncd_x_R0-0}{1}: [radius] [15154]: (info): RADIUS: User-Name [1] 7 "tiago"
[...]
2023/08/08 13:38:16.879241798 {wncd_x_R0-0}{1}: [radius] [15154]: (info): RADIUS: Received from id 1812/5 192.168.1.7:0, Access-Accept, len 128
[...]
2023/08/08 13:38:16.879504014 {wncd_x_R0-0}{1}: [webauth-state] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]Param-map used: LocalWebAuth
2023/08/08 13:38:16.879513532 {wncd_x_R0-0}{1}: [webauth-state] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]State AUTHENTICATING -> AUTHC_SUCCESS
2023/08/08 13:38:16.879530745 {wncd_x_R0-0}{1}: [webauth-acl] [15154]: (info): capwap_9000000b[286b.3598.580f][ 192.168.1.159]Unapply IPv4 intecept ACL via SVM, name "IP-Adm-V4-Int-ACL-global", pri 50, IIF 0
[...]
2023/08/08 13:38:16.880956564 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [15154]: (note): Authentication Success. Resolved Policy bitmap:4 for client 286b.3598.580f
[...]
2023/08/08 13:38:16.882320225 {wncd_x_R0-0}{1}: [errmsg] [15154]: (info): %CLIENT_ORCH_LOG-6-CLIENT_ADDED_TO_RUN_STATE: R0/0: wncd: Username entry (tiago) joined with ssid (wifi6E_test) for device with MAC: 286b.3598.580f
[...]
2023/08/08 13:38:16.882451875 {wncd_x_R0-0}{1}: [rog-proxy-capwap] [15154]: (debug): Managed client RUN state notification: 286b.3598.580f
2023/08/08 13:38:16.882495928 {wncd_x_R0-0}{1}: [client-orch-state] [15154]: (note): MAC: 286b.3598.580f Client state transition: S_CO_L3_AUTH_IN_PROGRESS -> S_CO_RUN
[...]
자세한 문제 해결 단계는 외부 인증을 사용하여 로컬 웹 인증 구성 문서를 참조하십시오.
웨인 위드 EWA
여기서는 RA 추적에서 EWA의 예를 볼 수 있습니다.
2023/08/10 14:35:20.685078384 {wncd_x_R0-0}{1}: [client-orch-sm] [15195]: (note): MAC: 0429.2ec9.e371 Association received. BSSID 00df.1ddd.7d39, WLAN wifi6E_EWA, Slot 3 AP 00df.1ddd.7d30, AP9136_5C.F524
2023/08/10 14:35:20.685117718 {wncd_x_R0-0}{1}: [client-orch-sm] [15195]: (debug): MAC: 0429.2ec9.e371 Received Dot11 association request. Processing started,SSID: wifi6E_EWA, Policy profile: CentralSwPolicyProfile, AP Name: AP9136_5C.F524, Ap Mac Address: 00df.1ddd.7d30BSSID MAC0000.0000.0000wlan ID: 6RSSI: -57, SNR: 41
2023/08/10 14:35:20.685226454 {wncd_x_R0-0}{1}: [client-orch-state] [15195]: (note): MAC: 0429.2ec9.e371 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2023/08/10 14:35:20.685420591 {wncd_x_R0-0}{1}: [dot11-validate] [15195]: (info): MAC: 0429.2ec9.e371 Dot11 ie validate ext/supp rates. Validation Passed for Supported rates radio_type 16
2023/08/10 14:35:20.685422154 {wncd_x_R0-0}{1}: [dot11-validate] [15195]: (info): MAC: 0429.2ec9.e371 WiFi direct: Dot11 validate P2P IE. P2P IE not present.
2023/08/10 14:35:20.685864592 {wncd_x_R0-0}{1}: [dot11] [15195]: (debug): MAC: 0429.2ec9.e371 dot11 send association response. Framing association response with resp_status_code: 0
2023/08/10 14:35:20.685865002 {wncd_x_R0-0}{1}: [dot11] [15195]: (info): MAC: 0429.2ec9.e371 Dot11 capability privacy bit set TRUE
2023/08/10 14:35:20.685867818 {wncd_x_R0-0}{1}: [dot11] [15195]: (debug): MAC: 0429.2ec9.e371 Dot11 Capability info byte1 11, byte2: 10
2023/08/10 14:35:20.685886032 {wncd_x_R0-0}{1}: [dot11-frame] [15195]: (info): MAC: 0429.2ec9.e371 WiFi direct: skip build Assoc Resp with P2P IE: Wifi direct policy disabled
2023/08/10 14:35:20.685991953 {wncd_x_R0-0}{1}: [dot11] [15195]: (info): MAC: 0429.2ec9.e371 dot11 send association response. Sending assoc response of length: 183 with resp_status_code: 0, DOT11_STATUS: DOT11_STATUS_SUCCESS
2023/08/10 14:35:20.685995339 {wncd_x_R0-0}{1}: [dot11] [15195]: (note): MAC: 0429.2ec9.e371 Association success. AID 33, Roaming = False, WGB = False, 11r = False, 11w = True Fast roam = False
2023/08/10 14:35:20.686003685 {wncd_x_R0-0}{1}: [dot11] [15195]: (info): MAC: 0429.2ec9.e371 DOT11 state transition: S_DOT11_INIT -> S_DOT11_ASSOCIATED
2023/08/10 14:35:20.686061695 {wncd_x_R0-0}{1}: [client-orch-sm] [15195]: (debug): MAC: 0429.2ec9.e371 Station Dot11 association is successful.
2023/08/10 14:35:20.686088796 {wncd_x_R0-0}{1}: [client-orch-sm] [15195]: (debug): MAC: 0429.2ec9.e371 Starting L2 authentication. Bssid in state machine:00df.1ddd.7d39 Bssid in request is:00df.1ddd.7d39
2023/08/10 14:35:20.686099576 {wncd_x_R0-0}{1}: [client-orch-state] [15195]: (note): MAC: 0429.2ec9.e371 Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2023/08/10 14:35:20.686125926 {wncd_x_R0-0}{1}: [client-auth] [15195]: (note): MAC: 0429.2ec9.e371 L2 Authentication initiated. method PSK, Policy VLAN 0, AAA override = 1, NAC = 0
[...]
2023/08/10 14:35:20.687526737 {wncd_x_R0-0}{1}: [auth-mgr] [15195]: (info): [0429.2ec9.e371:capwap_90000010] Raised event AUTHZ_SUCCESS (11)
2023/08/10 14:35:20.687530575 {wncd_x_R0-0}{1}: [auth-mgr] [15195]: (info): [0429.2ec9.e371:capwap_90000010] Context changing state from 'Idle' to 'Authz Success'
2023/08/10 14:35:20.687533620 {wncd_x_R0-0}{1}: [auth-mgr] [15195]: (info): [0429.2ec9.e371:capwap_90000010] Authorized open auth session for 0429.2ec9.e371
[...]
2023/08/10 14:35:20.687804543 {wncd_x_R0-0}{1}: [client-auth] [15195]: (info): MAC: 0429.2ec9.e371 Client auth-interface state transition: S_AUTHIF_AWAIT_PSK_AUTH_START_RESP -> S_AUTHIF_PSK_AUTH_PENDING
2023/08/10 14:35:20.687807038 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [15195]: (note): Authentication Success. Resolved Policy bitmap:11 for client 0429.2ec9.e371
[...]
2023/08/10 14:35:20.691676380 {wncd_x_R0-0}{1}: [client-auth] [15195]: (info): MAC: 0429.2ec9.e371 Client auth-interface state transition: S_AUTHIF_ADD_MOBILE_ACK_WAIT_KM -> S_AUTHIF_PSK_AUTH_KEY_XCHNG_PENDING
2023/08/10 14:35:20.691841904 {wncd_x_R0-0}{1}: [client-keymgmt] [15195]: (info): MAC: 0429.2ec9.e371 EAP key M1 Sent successfully
2023/08/10 14:35:20.691844278 {wncd_x_R0-0}{1}: [client-keymgmt] [15195]: (info): MAC: 0429.2ec9.e371 Client key-mgmt state transition: S_INITPMK -> S_PTK_START
2023/08/10 14:35:20.721636921 {wncd_x_R0-0}{1}: [client-keymgmt] [15195]: (info): MAC: 0429.2ec9.e371 M2 Status: EAP key M2 validation success
2023/08/10 14:35:20.721730809 {wncd_x_R0-0}{1}: [client-keymgmt] [15195]: (info): MAC: 0429.2ec9.e371 EAP key M3 Sent successfully
2023/08/10 14:35:20.721736890 {wncd_x_R0-0}{1}: [client-keymgmt] [15195]: (info): MAC: 0429.2ec9.e371 Client key-mgmt state transition: S_PTK_START -> S_PTKINITNEGOTIATING
2023/08/10 14:35:20.739641625 {wncd_x_R0-0}{1}: [client-keymgmt] [15195]: (info): MAC: 0429.2ec9.e371 M4 Status: EAP key M4 validation is successful
2023/08/10 14:35:20.739644982 {wncd_x_R0-0}{1}: [client-keymgmt] [15195]: (note): MAC: 0429.2ec9.e371 EAP Key management successful. AKM:OWE Cipher:CCMP WPA Version: WPA3
2023/08/10 14:35:20.739650121 {wncd_x_R0-0}{1}: [client-keymgmt] [15195]: (info): MAC: 0429.2ec9.e371 Client key-mgmt state transition: S_PTKINITNEGOTIATING -> S_PTKINITDONE
2023/08/10 14:35:20.739744971 {wncd_x_R0-0}{1}: [client-auth] [15195]: (note): MAC: 0429.2ec9.e371 L2 Authentication initiated. method WEBAUTH, Policy VLAN 0, AAA override = 1
2023/08/10 14:35:20.739838779 {wncd_x_R0-0}{1}: [auth-mgr] [15195]: (info): [0429.2ec9.e371:capwap_90000010] Session Start event called from SANET-SHIM, vlan: 0
2023/08/10 14:35:20.739847004 {wncd_x_R0-0}{1}: [auth-mgr] [15195]: (info): [0429.2ec9.e371:capwap_90000010] Wireless session sequence, create context with method WebAuth
2023/08/10 14:35:20.739861071 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [15195]: (info): [0429.2ec9.e371:capwap_90000010] - authc_list: EWA_Radius
[...]
2023/08/10 14:35:20.740069114 {wncd_x_R0-0}{1}: [webauth-state] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 0.0.0.0]Param-map used: ExternalWebAuth
2023/08/10 14:35:20.740071629 {wncd_x_R0-0}{1}: [webauth-state] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 0.0.0.0]State INIT -> INIT
2023/08/10 14:35:20.740083452 {wncd_x_R0-0}{1}: [webauth-sm] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 0.0.0.0]Initiate session, forward state to 0 IF 0x90000010 mac [0429.2ec9.e371]
2023/08/10 14:35:20.740085425 {wncd_x_R0-0}{1}: [webauth-sm] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 0.0.0.0]Initiate session, SM init sessions 1
2023/08/10 14:35:20.740091236 {wncd_x_R0-0}{1}: [webauth-state] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 0.0.0.0]Param-map used: ExternalWebAuth
2023/08/10 14:35:20.740093601 {wncd_x_R0-0}{1}: [webauth-state] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 0.0.0.0]State INIT -> INIT
2023/08/10 14:35:20.740103810 {wncd_x_R0-0}{1}: [webauth-acl] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 0.0.0.0]Applying IPv4 intercept ACL via SVM, name: WA-v4-int-192.168.1.17, priority: 50, IIF-ID: 0
[...]
2023/08/10 14:35:21.942607594 {wncd_x_R0-0}{1}: [client-iplearn] [15195]: (note): MAC: 0429.2ec9.e371 Client IP learn successful. Method: DHCP IP: 192.168.1.160
[...]
2023/08/10 14:35:21.943838504 {wncd_x_R0-0}{1}: [client-iplearn] [15195]: (info): MAC: 0429.2ec9.e371 IP-learn state transition: S_IPLEARN_IN_PROGRESS -> S_IPLEARN_COMPLETE
2023/08/10 14:35:21.944028273 {wncd_x_R0-0}{1}: [client-orch-sm] [15195]: (debug): MAC: 0429.2ec9.e371 Received ip learn response. method: IPLEARN_METHOD_DHCP
2023/08/10 14:35:21.944069521 {wncd_x_R0-0}{1}: [client-orch-sm] [15195]: (debug): MAC: 0429.2ec9.e371 Triggered L3 authentication. status = 0x0, Success
2023/08/10 14:35:21.944074851 {wncd_x_R0-0}{1}: [client-orch-state] [15195]: (note): MAC: 0429.2ec9.e371 Client state transition: S_CO_IP_LEARN_IN_PROGRESS -> S_CO_L3_AUTH_IN_PROGRESS
2023/08/10 14:35:21.944201671 {wncd_x_R0-0}{1}: [dot1x] [15195]: (info): [0000.0000.0000:capwap_90000010] Couldn't find the supplicant in the list
2023/08/10 14:35:21.944759066 {wncd_x_R0-0}{1}: [client-auth] [15195]: (note): MAC: 0429.2ec9.e371 L3 Authentication initiated. LWA
2023/08/10 14:35:21.944776669 {wncd_x_R0-0}{1}: [client-auth] [15195]: (info): MAC: 0429.2ec9.e371 Client auth-interface state transition: S_AUTHIF_L2_WEBAUTH_DONE -> S_AUTHIF_WEBAUTH_PENDING
[...]
2023/08/10 14:35:24.110614486 {wncd_x_R0-0}{1}: [webauth-io] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 60486/213 IO state NEW -> READING
2023/08/10 14:35:24.110679789 {wncd_x_R0-0}{1}: [webauth-io] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 60486/213 Read event, Message ready
2023/08/10 14:35:24.110699827 {wncd_x_R0-0}{1}: [webauth-httpd] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 GET rcvd when in LOGIN state
2023/08/10 14:35:24.110718893 {wncd_x_R0-0}{1}: [webauth-httpd] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 HTTP GET request
2023/08/10 14:35:24.110754721 {wncd_x_R0-0}{1}: [webauth-httpd] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 Parse GET, src [2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e] dst [2a00:1450:4003:811::2003] url [http://connectivitycheck.gstatic.com/generate_204]
2023/08/10 14:35:24.110951163 {wncd_x_R0-0}{1}: [webauth-httpd] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 Read complete: parse_request return 10
2023/08/10 14:35:24.110960801 {wncd_x_R0-0}{1}: [webauth-state] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 Param-map used: ExternalWebAuth
2023/08/10 14:35:24.110971331 {wncd_x_R0-0}{1}: [webauth-state] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 State LOGIN -> LOGIN
2023/08/10 14:35:24.111046654 {wncd_x_R0-0}{1}: [webauth-page] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:96e8:ab91:47c8:3d6e]capwap_90000010 Sending Webauth login form, len 8077
[...]
2023/08/10 14:35:35.761960632 {wncd_x_R0-0}{1}: [webauth-io] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 47440/213 IO state NEW -> SSL_HANDSHAKING
2023/08/10 14:35:35.776669018 {wncd_x_R0-0}{1}: [webauth-io] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 47450/213 IO state NEW -> SSL_HANDSHAKING
2023/08/10 14:35:37.805884475 {wncd_x_R0-0}{1}: [webauth-io] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 55760/213 IO state NEW -> READING
2023/08/10 14:35:37.807261842 {wncd_x_R0-0}{1}: [webauth-io] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 55760/213 Read event, Message ready
2023/08/10 14:35:37.807273253 {wncd_x_R0-0}{1}: [webauth-httpd] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 POST rcvd when in LOGIN state
2023/08/10 14:35:37.807287911 {wncd_x_R0-0}{1}: [webauth-httpd] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 get url: /login.html
2023/08/10 14:35:37.807331213 {wncd_x_R0-0}{1}: [webauth-httpd] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 Read complete: parse_request return 4
[...]
2023/08/10 14:35:37.807498470 {wncd_x_R0-0}{1}: [webauth-state] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 Param-map used: ExternalWebAuth
2023/08/10 14:35:37.807503619 {wncd_x_R0-0}{1}: [webauth-state] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 State LOGIN -> AUTHENTICATING
2023/08/10 14:35:37.807515502 {wncd_x_R0-0}{1}: [webauth-io] [15195]: (info): capwap_90000010[0429.2ec9.e371][ 192.168.1.160][2001:8a0:fb91:1c00:d20a:fcc:5919:3f1a]capwap_90000010 55760/213 IO state READING -> AUTHENTICATING
2023/08/10 14:35:37.807653884 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Send Access-Request to 192.168.1.7:1812 id 0/1, len 531
2023/08/10 14:35:37.807663221 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: authenticator 56 a6 f6 4e 84 f8 00 e9 - 06 14 c9 b3 8d 77 2b 4c
2023/08/10 14:35:37.807667159 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Calling-Station-Id [31] 19 "04-29-2e-c9-e3-71"
2023/08/10 14:35:37.807670215 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: User-Name [1] 7 "tiago"
2023/08/10 14:35:37.807673040 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Vendor, Cisco [26] 49
2023/08/10 14:35:37.807676226 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Cisco AVpair [1] 43 "audit-session-id=0F01A8C00000000DDFDF94C0"
2023/08/10 14:35:37.807680083 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Framed-IP-Address [8] 6 192.168.1.160
2023/08/10 14:35:37.807682217 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Message-Authenticator[80] 18 ...
2023/08/10 14:35:37.807701825 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Service-Type [6] 6 Outbound [5]
2023/08/10 14:35:37.807703838 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Vendor, Cisco [26] 29
2023/08/10 14:35:37.807709459 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Cisco AVpair [1] 23 "service-type=Outbound"
2023/08/10 14:35:37.807711783 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Vendor, Cisco [26] 22
2023/08/10 14:35:37.807714509 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Cisco AVpair [1] 16 "method=webauth"
[...]
2023/08/10 14:35:37.887128821 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: Received from id 1812/1 192.168.1.7:0, Access-Accept, len 130
2023/08/10 14:35:37.887152085 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: authenticator c1 c5 a3 4b 49 5d 11 42 - 74 50 bd e7 37 f3 07 1f
2023/08/10 14:35:37.887166342 {wncd_x_R0-0}{1}: [radius] [15195]: (info): RADIUS: User-Name [1] 7 "tiago"
[...]
2023/08/10 14:35:37.890143566 {wncd_x_R0-0}{1}: [auth-mgr] [15195]: (info): [0429.2ec9.e371:capwap_90000010] Authc success from WebAuth, Auth event success
[...]
2023/08/10 14:35:37.893926155 {wncd_x_R0-0}{1}: [rog-proxy-capwap] [15195]: (debug): Managed client RUN state notification: 0429.2ec9.e371
2023/08/10 14:35:37.893979316 {wncd_x_R0-0}{1}: [client-orch-state] [15195]: (note): MAC: 0429.2ec9.e371 Client state transition: S_CO_L3_AUTH_IN_PROGRESS -> S_CO_RUN
[...]
자세한 트러블슈팅 단계는 문서 9800 WLC에서 외부 웹 인증 구성 및 트러블슈팅을 참조하십시오.
CWA와 함께 해야 할 일
여기서는 RA 추적에서 CWA의 예를 볼 수 있습니다.
2023/08/11 12:43:45.551148898 {wncd_x_R0-0}{1}: [client-orch-sm] [15200]: (note): MAC: 2495.2f72.8a66 Association received. BSSID 00df.1ddd.7d39, WLAN wifi6E_CWA, Slot 3 AP 00df.1ddd.7d30, AP9136_5C.F524
2023/08/11 12:43:45.551185236 {wncd_x_R0-0}{1}: [client-orch-sm] [15200]: (debug): MAC: 2495.2f72.8a66 Received Dot11 association request. Processing started,SSID: wifi6E_CWA, Policy profile: CWA_PP, AP Name: AP9136_5C.F524, Ap Mac Address: 00df.1ddd.7d30BSSID MAC0000.0000.0000wlan ID: 7RSSI: -57, SNR: 41
[...]
2023/08/11 12:43:45.551873379 {wncd_x_R0-0}{1}: [client-auth] [15200]: (note): MAC: 2495.2f72.8a66 MAB Authentication initiated. Policy VLAN 0, AAA override = 1, NAC = 1
2023/08/11 12:43:45.551925177 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Session Start event called from SANET-SHIM, vlan: 0
2023/08/11 12:43:45.551935427 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Wireless session sequence, create context with method MAB
2023/08/11 12:43:45.551947760 {wncd_x_R0-0}{1}: [auth-mgr-feat_wireless] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] - authc_list: RadiusAuthor
[...]
2023/08/11 12:43:45.553164283 {wncd_x_R0-0}{1}: [mab] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] MAB authentication started for 2495.2f72.8a66
[...]
2023/08/11 12:43:45.553769929 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Send Access-Request to 192.168.1.7:1812 id 0/19, len 394
2023/08/11 12:43:45.553775189 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: authenticator e6 c2 9a 48 f2 59 6a 1a - ad 7b 53 0f 78 96 3a f5
2023/08/11 12:43:45.553778666 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: User-Name [1] 14 "24952f728a66"
2023/08/11 12:43:45.553781110 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: User-Password [2] 18 *
2023/08/11 12:43:45.553786901 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Service-Type [6] 6 Call Check [10]
2023/08/11 12:43:45.553789196 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 31
2023/08/11 12:43:45.553792211 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 25 "service-type=Call Check"
2023/08/11 12:43:45.553795428 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Framed-MTU [12] 6 1485
2023/08/11 12:43:45.553797431 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Message-Authenticator[80] 18 ...
2023/08/11 12:43:45.553814193 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: EAP-Key-Name [102] 2 *
2023/08/11 12:43:45.553818431 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 49
2023/08/11 12:43:45.553821036 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 43 "audit-session-id=0F01A8C00000001EE49FCD0F"
2023/08/11 12:43:45.553823100 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 18
2023/08/11 12:43:45.553829221 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 12 "method=mab"
2023/08/11 12:43:45.553831265 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 32
2023/08/11 12:43:45.553833720 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 26 "client-iif-id=2801797648"
2023/08/11 12:43:45.553835684 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 17
2023/08/11 12:43:45.553838048 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 11 "vlan-id=1"
2023/08/11 12:43:45.553841395 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: NAS-IP-Address [4] 6 192.168.1.15
2023/08/11 12:43:45.553844270 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: NAS-Port-Type [61] 6 802.11 wireless [19]
2023/08/11 12:43:45.553846955 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: NAS-Port [5] 6 112
2023/08/11 12:43:45.553848758 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 34
2023/08/11 12:43:45.553851193 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 28 "cisco-wlan-ssid=wifi6E_CWA"
2023/08/11 12:43:45.553853177 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 36
2023/08/11 12:43:45.553855591 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 30 "wlan-profile-name=wifi6E_CWA"
2023/08/11 12:43:45.553858246 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Called-Station-Id [30] 30 "00-df-1d-dd-7d-30:wifi6E_CWA"
2023/08/11 12:43:45.553860811 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Calling-Station-Id [31] 19 "24-95-2f-72-8a-66"
2023/08/11 12:43:45.553863015 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Airespace [26] 12
2023/08/11 12:43:45.553865510 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Airespace-WLAN-ID [1] 6 7
2023/08/11 12:43:45.553867995 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Nas-Identifier [32] 14 "eWLC-9800-01"
2023/08/11 12:43:45.553929331 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Started 5 sec timeout
2023/08/11 12:43:45.570301533 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Received from id 1812/19 192.168.1.7:0, Access-Accept, len 538
2023/08/11 12:43:45.570313767 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: authenticator 17 42 8f 8e 13 78 91 01 - 6c 89 9e cb 51 3b 69 c8
2023/08/11 12:43:45.570319247 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: User-Name [1] 19 "24-95-2F-72-8A-66"
2023/08/11 12:43:45.570321902 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Class [25] 51 ...
2023/08/11 12:43:45.570375383 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Message-Authenticator[80] 18 ...
2023/08/11 12:43:45.570390662 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 33
2023/08/11 12:43:45.570393618 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 27 "url-redirect-acl=REDIRECT"
2023/08/11 12:43:45.570395732 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 208
2023/08/11 12:43:45.570403947 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 183 "url-redirect=https://192.168.1.7:8443/portal/gateway?sessionId=0F01A8C00000001EE49FCD0F&portal=26d19560-2e58-11e9-98fb-0050568775a3&action=cwa&token=a6a62b8619182aa81bd9f9f1781184f9"
2023/08/11 12:43:45.570435186 {wncd_x_R0-0}{1}: [radius] [15200]: (info): Valid Response Packet, Free the identifier
2023/08/11 12:43:45.570612622 {wncd_x_R0-0}{1}: [mab] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] MAB received an Access-Accept for (2495.2f72.8a66)
2023/08/11 12:43:45.570621699 {wncd_x_R0-0}{1}: [mab] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Received event 'MAB_RESULT' on (2495.2f72.8a66)
2023/08/11 12:43:45.570648140 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Authc success from MAB, Auth event success
2023/08/11 12:43:45.570657648 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Raised event APPLY_USER_PROFILE (14)
2023/08/11 12:43:45.570668839 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Raised event RX_METHOD_AUTHC_SUCCESS (3)
2023/08/11 12:43:45.570709836 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): Applying Attribute : username 0 "24-95-2F-72-8A-66"
2023/08/11 12:43:45.570718393 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): Applying Attribute : class 0 43 41 43 53 3a 30 46 30 31 41 38 43 30 30 30 30 30 30 30 31 45 45 34 39 46 43 44 30 46 3a 49 53 45 2d 30 31 2f 34 38 31 31 32 30 33 32 39 2f 32 31
2023/08/11 12:43:45.570719545 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): Applying Attribute : Message-Authenticator 0
2023/08/11 12:43:45.570720517 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): Applying Attribute : url-redirect-acl 0 "REDIRECT"
2023/08/11 12:43:45.570722440 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): Applying Attribute : url-redirect 0 "https://192.168.1.7:8443/portal/gateway?sessionId=0F01A8C00000001EE49FCD0F&portal=26d19560-2e58-11e9-98fb-0050568775a3&action=cwa&token=a6a62b8619182aa81bd9f9f1781184f9"
[...]
2023/08/11 12:43:45.571261140 {wncd_x_R0-0}{1}: [webauth-dev] [15200]: (info): [2495.2f72.8a66][ 192.168.1.162][2001:8a0:fb91:1c00:c093:8034:ca09:9d4f] Central Webauth URL Redirect, Received a request to create a CWA session for a mac [24:95:2f:72:8a:66]
[...]
2023/08/11 12:43:45.571316064 {wncd_x_R0-0}{1}: [webauth-state] [15200]: (info): [2495.2f72.8a66][ 0.0.0.0]Param-map used: global
2023/08/11 12:43:45.571318869 {wncd_x_R0-0}{1}: [webauth-state] [15200]: (info): [2495.2f72.8a66][ 0.0.0.0]State Invalid State -> INIT
[...]
2023/08/11 12:43:45.572346865 {wncd_x_R0-0}{1}: [dot11] [15200]: (info): MAC: 2495.2f72.8a66 dot11 send association response. Sending assoc response of length: 183 with resp_status_code: 0, DOT11_STATUS: DOT11_STATUS_SUCCESS
[...]
2023/08/11 12:43:45.576047520 {wncd_x_R0-0}{1}: [client-auth] [15200]: (info): MAC: 2495.2f72.8a66 Client auth-interface state transition: S_AUTHIF_ADD_MOBILE_ACK_WAIT_KM -> S_AUTHIF_PSK_AUTH_KEY_XCHNG_PENDING
2023/08/11 12:43:45.576136850 {wncd_x_R0-0}{1}: [client-keymgmt] [15200]: (info): MAC: 2495.2f72.8a66 EAP key M1 Sent successfully
2023/08/11 12:43:45.576138984 {wncd_x_R0-0}{1}: [client-keymgmt] [15200]: (info): MAC: 2495.2f72.8a66 Client key-mgmt state transition: S_INITPMK -> S_PTK_START
2023/08/11 12:43:45.576247599 {mobilityd_R0-0}{1}: [mm-client] [16431]: (debug): MAC: 0000.0000.0000 Received pmk_update, sub type: 0 of XID (0) from (WNCD[0])
2023/08/11 12:43:45.576379639 {mobilityd_R0-0}{1}: [mm-dgram-io] [16431]: (debug): MAC: 0000.0000.0000 Sending message: pmk_update to group: holyfountain
2023/08/11 12:43:45.576397212 {mobilityd_R0-0}{1}: [mm-dgram-io] [16431]: (debug): MAC: 0000.0000.0000 Failed to send message: pmk_update, total configured peers: 2, no active peers
2023/08/11 12:43:45.632584865 {wncd_x_R0-0}{1}: [client-keymgmt] [15200]: (info): MAC: 2495.2f72.8a66 M2 Status: EAP key M2 validation success
2023/08/11 12:43:45.632765557 {wncd_x_R0-0}{1}: [client-keymgmt] [15200]: (info): MAC: 2495.2f72.8a66 EAP key M3 Sent successfully
2023/08/11 12:43:45.632766960 {wncd_x_R0-0}{1}: [client-keymgmt] [15200]: (info): MAC: 2495.2f72.8a66 Client key-mgmt state transition: S_PTK_START -> S_PTKINITNEGOTIATING
2023/08/11 12:43:45.641844995 {wncd_x_R0-0}{1}: [client-keymgmt] [15200]: (info): MAC: 2495.2f72.8a66 M4 Status: EAP key M4 validation is successful
2023/08/11 12:43:45.641846798 {wncd_x_R0-0}{1}: [client-keymgmt] [15200]: (note): MAC: 2495.2f72.8a66 EAP Key management successful. AKM:OWE Cipher:CCMP WPA Version: WPA3
2023/08/11 12:43:45.641851597 {wncd_x_R0-0}{1}: [client-keymgmt] [15200]: (info): MAC: 2495.2f72.8a66 Client key-mgmt state transition: S_PTKINITNEGOTIATING -> S_PTKINITDONE
[...]
2023/08/11 12:43:45.645536693 {wncd_x_R0-0}{1}: [client-orch-state] [15200]: (note): MAC: 2495.2f72.8a66 Client state transition: S_CO_DPATH_PLUMB_IN_PROGRESS -> S_CO_IP_LEARN_IN_PROGRESS
[...]
2023/08/11 12:43:46.103210515 {wncd_x_R0-0}{1}: [client-iplearn] [15200]: (note): MAC: 2495.2f72.8a66 Client IP learn successful. Method: DHCP IP: 192.168.1.162
2023/08/11 12:43:46.103745268 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] auth mgr attr add/change notification is received for attr addr(8)
2023/08/11 12:43:46.104324815 {wncd_x_R0-0}{1}: [webauth-sess] [15200]: (info): [2495.2f72.8a66][ 0.0.0.0]Change notif CB, Add address 192.168.1.162 [2495.2f72.8a66]
2023/08/11 12:43:46.104343430 {wncd_x_R0-0}{1}: [webauth-sess] [15200]: (info): adding webauth session to ipv4 hash table for vrf id 0, ipv4 vrf table id 0
2023/08/11 12:43:46.104416388 {wncd_x_R0-0}{1}: [auth-mgr-feat_acct] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] SM Notified attribute Add/Update addr 192.168.1.162
2023/08/11 12:43:46.104460371 {wncd_x_R0-0}{1}: [client-iplearn] [15200]: (info): MAC: 2495.2f72.8a66 IP-learn state transition: S_IPLEARN_IN_PROGRESS -> S_IPLEARN_COMPLETE
2023/08/11 12:43:46.104607690 {wncd_x_R0-0}{1}: [client-orch-sm] [15200]: (debug): MAC: 2495.2f72.8a66 Received ip learn response. method: IPLEARN_METHOD_DHCP
2023/08/11 12:43:46.104669668 {wncd_x_R0-0}{1}: [client-orch-sm] [15200]: (debug): MAC: 2495.2f72.8a66 Triggered L3 authentication. status = 0x0, Success
2023/08/11 12:43:46.104674096 {wncd_x_R0-0}{1}: [client-orch-state] [15200]: (note): MAC: 2495.2f72.8a66 Client state transition: S_CO_IP_LEARN_IN_PROGRESS -> S_CO_L3_AUTH_IN_PROGRESS
2023/08/11 12:43:46.104749168 {wncd_x_R0-0}{1}: [dot1x] [15200]: (info): [0000.0000.0000:capwap_9000000f] Couldn't find the supplicant in the list
2023/08/11 12:43:46.104996176 {wncd_x_R0-0}{1}: [client-auth] [15200]: (note): MAC: 2495.2f72.8a66 L3 Authentication initiated. CWA
2023/08/11 12:43:46.105004562 {wncd_x_R0-0}{1}: [client-auth] [15200]: (info): MAC: 2495.2f72.8a66 Client auth-interface state transition: S_AUTHIF_L2_WEBAUTH_DONE -> S_AUTHIF_WEBAUTH_PENDING
[...]
2023/08/11 12:43:46.281818709 {wncd_x_R0-0}{1}: [webauth-state] [15200]: (info): [2495.2f72.8a66][ 192.168.1.162]Param-map used: global
2023/08/11 12:43:46.281822877 {wncd_x_R0-0}{1}: [webauth-state] [15200]: (info): [2495.2f72.8a66][ 192.168.1.162]State INIT -> GET_REDIRECT
2023/08/11 12:43:46.281825292 {wncd_x_R0-0}{1}: [webauth-io] [15200]: (info): [2495.2f72.8a66][ 192.168.1.162]43506/5 IO state READING -> WRITING
2023/08/11 12:43:46.281856060 {wncd_x_R0-0}{1}: [webauth-io] [15200]: (info): [2495.2f72.8a66][ 192.168.1.162]43506/5 IO state WRITING -> END
2023/08/11 12:43:46.281857933 {wncd_x_R0-0}{1}: [webauth-httpd] [15200]: (info): [2495.2f72.8a66][ 192.168.1.162]43506/5 Remove IO ctx and close socket, id [8800000D]
[...]
2023/08/11 12:44:20.312534457 {wncd_x_R0-0}{1}: [caaa-ch] [15200]: (info): [CAAA:COMMAND HANDLER:35000014] Processing CoA request under Command Handler ctx.
2023/08/11 12:44:20.312571788 {wncd_x_R0-0}{1}: [caaa-ch] [15200]: (info): [CAAA:COMMAND HANDLER:35000014] Reauthenticate request (0x560210e99bf8) for 2495.2f72.8a66
2023/08/11 12:44:20.312626401 {wncd_x_R0-0}{1}: [sadb-attr] [15200]: (info): Removing ipv6 addresses from the attr list 318769545,sm_ctx = 0x80806aea40, num_ipv6 = 3
2023/08/11 12:44:20.312673230 {wncd_x_R0-0}{1}: [mab] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] MAB re-authentication started for (2495.2f72.8a66)
2023/08/11 12:44:20.312713736 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Context changing state from 'Authz Success' to 'Running'
2023/08/11 12:44:20.312720158 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Method mab changing state from 'Authc Success' to 'Running'
2023/08/11 12:44:20.312740637 {wncd_x_R0-0}{1}: [aaa-coa] [15200]: (info): radius coa proxy relay coa resp(wncd)
2023/08/11 12:44:20.312746478 {wncd_x_R0-0}{1}: [aaa-coa] [15200]: (info): CoA Response Details
2023/08/11 12:44:20.312756237 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): << ssg-command-code 0 32 >>
2023/08/11 12:44:20.312758912 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): << formatted-clid 0 "2495.2f72.8a66">>
2023/08/11 12:44:20.312762318 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): << error-cause 0 1 [Success]>>
2023/08/11 12:44:20.312774040 {wncd_x_R0-0}{1}: [aaa-coa] [15200]: (info): server:192.168.1.15 cfg_saddr:192.168.1.15 udpport:42721 sport:0, tableid:0iden:4 rad_code:43 msg_auth_rcvd:TRUE coa_resp:ACK
2023/08/11 12:44:20.312876905 {wncd_x_R0-0}{1}: [caaa-ch] [15200]: (info): [CAAA:COMMAND HANDLER] CoA response sent
2023/08/11 12:44:20.312886633 {wncd_x_R0-0}{1}: [caaa-ch] [15200]: (info): [CAAA:COMMAND HANDLER:35000014] Identity preserved: mac (2495.2f72.8a66), ip (0), audit_sid (0F01A8C00000001EE49FCD0F), aaa_session_id (0)
2023/08/11 12:44:20.312902744 {wncd_x_R0-0}{1}: [mab] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Received event 'MAB_REAUTHENTICATE' on (2495.2f72.8a66)
2023/08/11 12:44:20.313249801 {wncd_x_R0-0}{1}: [sadb-attr] [15200]: (info): Removing ipv6 addresses from the attr list -855635574,sm_ctx = 0x80806aea40, num_ipv6 = 3
2023/08/11 12:44:20.313380288 {wncd_x_R0-0}{1}: [caaa-author] [15200]: (info): [CAAA:AUTHOR:35000014] NULL ATTR LIST
2023/08/11 12:44:20.313702758 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Send Access-Request to 192.168.1.7:1812 id 0/20, len 544
2023/08/11 12:44:20.313714140 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: authenticator 7b 62 36 99 3d 55 15 f1 - c3 b9 08 ea 93 7f 26 79
2023/08/11 12:44:20.313722686 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: User-Name [1] 14 "24952f728a66"
[...]
2023/08/11 12:44:20.313914609 {smd_R0-0}{1}: [aaa-coa] [17281]: (info): ++++++ Received CoA response Attribute List ++++++
2023/08/11 12:44:20.313917665 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: NAS-IP-Address [4] 6 192.168.1.15
2023/08/11 12:44:20.313924488 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: NAS-Port-Type [61] 6 802.11 wireless [19]
2023/08/11 12:44:20.313931051 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: NAS-Port [5] 6 112
2023/08/11 12:44:20.313935559 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 34
2023/08/11 12:44:20.313941611 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 28 "cisco-wlan-ssid=wifi6E_CWA"
2023/08/11 12:44:20.313946640 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 36
2023/08/11 12:44:20.313952692 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 30 "wlan-profile-name=wifi6E_CWA"
2023/08/11 12:44:20.313959174 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Called-Station-Id [30] 30 "00-df-1d-dd-7d-30:wifi6E_CWA"
2023/08/11 12:44:20.313965616 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Calling-Station-Id [31] 19 "24-95-2f-72-8a-66"
2023/08/11 12:44:20.313978210 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Airespace [26] 12
2023/08/11 12:44:20.313978350 {smd_R0-0}{1}: [radius] [17281]: (info): RADIUS(00000000): Send CoA Ack Response to 192.168.1.7:42721 id 4, len 69
2023/08/11 12:44:20.313984442 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Airespace-WLAN-ID [1] 6 7
2023/08/11 12:44:20.313989972 {smd_R0-0}{1}: [radius] [17281]: (info): RADIUS: authenticator c3 10 c5 26 16 87 54 7f - 9f 63 a2 03 db 61 3a 65
2023/08/11 12:44:20.313990713 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Nas-Identifier [32] 14 "eWLC-9800-01"
2023/08/11 12:44:20.313993459 {smd_R0-0}{1}: [radius] [17281]: (info): RADIUS: Vendor, Cisco [26] 9
2023/08/11 12:44:20.313996655 {smd_R0-0}{1}: [radius] [17281]: (info): RADIUS: ssg-command-code [252] 3 ...
2023/08/11 12:44:20.314073240 {smd_R0-0}{1}: [radius] [17281]: (info): RADIUS: Calling-Station-Id [31] 16 "2495.2f72.8a66"
2023/08/11 12:44:20.314077337 {smd_R0-0}{1}: [radius] [17281]: (info): RADIUS: Dynamic-Author-Error-Cause[101] 6 Success [200]
2023/08/11 12:44:20.314079431 {smd_R0-0}{1}: [radius] [17281]: (info): RADIUS: Message-Authenticator[80] 18 ...
2023/08/11 12:44:20.314098387 {smd_R0-0}{1}: [aaa-pod] [17281]: (info): CoA response source port = 0, udpport = 42721,
2023/08/11 12:44:20.314099289 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Started 5 sec timeout
2023/08/11 12:44:20.327831023 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Received from id 1812/20 192.168.1.7:0, Access-Accept, len 131
2023/08/11 12:44:20.327850400 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: authenticator a6 13 03 f0 f7 62 06 e0 - f3 c6 95 6e 36 cb 13 0b
2023/08/11 12:44:20.327861140 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: User-Name [1] 7 "tiago"
2023/08/11 12:44:20.327867512 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Class [25] 51 ...
2023/08/11 12:44:20.327938827 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Message-Authenticator[80] 18 ...
2023/08/11 12:44:20.327978472 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Vendor, Cisco [26] 35
2023/08/11 12:44:20.327985516 {wncd_x_R0-0}{1}: [radius] [15200]: (info): RADIUS: Cisco AVpair [1] 29 "profile-name=Android-Google"
2023/08/11 12:44:20.328027385 {wncd_x_R0-0}{1}: [radius] [15200]: (info): Valid Response Packet, Free the identifier
2023/08/11 12:44:20.328322423 {wncd_x_R0-0}{1}: [mab] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] MAB received an Access-Accept for (2495.2f72.8a66)
2023/08/11 12:44:20.328341299 {wncd_x_R0-0}{1}: [mab] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Received event 'MAB_RESULT' on (2495.2f72.8a66)
2023/08/11 12:44:20.328394871 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Authc success from MAB, Auth event success
2023/08/11 12:44:20.328412885 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Raised event APPLY_USER_PROFILE (14)
2023/08/11 12:44:20.328421270 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Raised event RX_METHOD_AUTHC_SUCCESS (3)
2023/08/11 12:44:20.328519506 {wncd_x_R0-0}{1}: [aaa-attr-inf] [15200]: (info): Applying Attribute : username 0 "tiago"
[...]
2023/08/11 12:44:20.328759310 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Received User-Name tiago for client 2495.2f72.8a66
2023/08/11 12:44:20.328773066 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Method mab changing state from 'Running' to 'Authc Success'
2023/08/11 12:44:20.328791892 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Context changing state from 'Running' to 'Authc Success'
[...]
2023/08/11 12:44:20.330928236 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Raised event AUTHZ_SUCCESS (11)
2023/08/11 12:44:20.330937604 {wncd_x_R0-0}{1}: [auth-mgr] [15200]: (info): [2495.2f72.8a66:capwap_9000000f] Context changing state from 'Authc Success' to 'Authz Success'
2023/08/11 12:44:20.331059194 {wncd_x_R0-0}{1}: [client-auth] [15200]: (note): MAC: 2495.2f72.8a66 L3 Authentication Successful. ACL:[]
2023/08/11 12:44:20.331065276 {wncd_x_R0-0}{1}: [client-auth] [15200]: (info): MAC: 2495.2f72.8a66 Client auth-interface state transition: S_AUTHIF_WEBAUTH_PENDING -> S_AUTHIF_WEBAUTH_DONE
[...]
2023/08/11 12:44:20.332171950 {wncd_x_R0-0}{1}: [errmsg] [15200]: (info): %CLIENT_ORCH_LOG-6-CLIENT_ADDED_TO_RUN_STATE: R0/0: wncd: Username entry (tiago) joined with ssid (wifi6E_CWA) for device with MAC: 2495.2f72.8a66
[...]
2023/08/11 12:44:20.332437363 {wncd_x_R0-0}{1}: [rog-proxy-capwap] [15200]: (debug): Managed client RUN state notification: 2495.2f72.8a66
2023/08/11 12:44:20.332544836 {wncd_x_R0-0}{1}: [client-orch-state] [15200]: (note): MAC: 2495.2f72.8a66 Client state transition: S_CO_L3_AUTH_IN_PROGRESS -> S_CO_RUN
[...]
2023/08/11 12:44:20.337221359 {wncd_x_R0-0}{1}: [client-auth] [15200]: (info): MAC: 2495.2f72.8a66 Client auth-interface state transition: S_AUTHIF_WEBAUTH_DONE -> S_AUTHIF_WEBAUTH_DONE
자세한 문제 해결 단계는 Catalyst 9800 WLC 및 ISE에서 CWA(Central Web Authentication) 구성 문서를 참조하십시오.
관련 정보
Cisco Live - Catalyst Wi-Fi 6E 액세스 포인트를 사용한 차세대 무선 네트워크 아키텍처
Cisco Catalyst 9800 Series Wireless Controller 소프트웨어 컨피그레이션 가이드 17.9.x
Catalyst 9800 WLC 및 ISE에서 CWA(Central Web Authentication) 구성
개정 이력
| 개정 | 게시 날짜 | 의견 |
|---|---|---|
1.0 |
14-Aug-2023 |
최초 릴리스 |
Cisco 엔지니어가 작성
- Tiago Antunes시스코 TAC
지원 문의
- 지원 케이스 접수

- (시스코 서비스 계약 필요)
이 문서가 적용되는 제품
- Catalyst 9136 Series Access Points
- Catalyst 9162 Series Access Points
- Catalyst 9164 Series Access Points
- Catalyst 9166 Series Access Points
- Catalyst 9800 Series Wireless Controllers
- Catalyst 9800 Wireless Controllers for Cloud
- Catalyst 9800-40 Wireless Controller
- Catalyst 9800-80 Wireless Controller
- Catalyst 9800-CL Wireless Controller for Cloud
- Catalyst 9800-L Wireless Controller
 피드백
피드백