Catalyst 9000 Series 스위치에서 레이어 2 하드웨어 검증
다운로드 옵션
편견 없는 언어
본 제품에 대한 문서 세트는 편견 없는 언어를 사용하기 위해 노력합니다. 본 설명서 세트의 목적상, 편견 없는 언어는 나이, 장애, 성별, 인종 정체성, 민족 정체성, 성적 지향성, 사회 경제적 지위 및 교차성에 기초한 차별을 의미하지 않는 언어로 정의됩니다. 제품 소프트웨어의 사용자 인터페이스에서 하드코딩된 언어, RFP 설명서에 기초한 언어 또는 참조된 서드파티 제품에서 사용하는 언어로 인해 설명서에 예외가 있을 수 있습니다. 시스코에서 어떤 방식으로 포용적인 언어를 사용하고 있는지 자세히 알아보세요.
이 번역에 관하여
Cisco는 전 세계 사용자에게 다양한 언어로 지원 콘텐츠를 제공하기 위해 기계 번역 기술과 수작업 번역을 병행하여 이 문서를 번역했습니다. 아무리 품질이 높은 기계 번역이라도 전문 번역가의 번역 결과물만큼 정확하지는 않습니다. Cisco Systems, Inc.는 이 같은 번역에 대해 어떠한 책임도 지지 않으며 항상 원본 영문 문서(링크 제공됨)를 참조할 것을 권장합니다.
목차
소개
이 문서에서는 Catalyst 9400 Series 스위치에서 레이어 2 하드웨어 프로그래밍 및 포워딩을 검증하는 방법에 대해 설명합니다.
사전 요구 사항
요구 사항
이 문서에 대한 특정 요건이 없습니다.
사용되는 구성 요소
이 문서의 정보는 Catalyst 9400(UADP 2.0) 시리즈 스위치를 기반으로 합니다.
참고: 이 문서에 사용된 소프트웨어 버전은 16.6.1이지만, 이 버전은 이후 버전의 Cisco IOS-XE에 적용할 수 있어야 합니다.
참고: 이 문서는 다른 유형의 Catalyst 9000 스위치에 사용할 수 있지만 라인 카드를 참조하는 명령은 무시합니다.
이 문서의 정보는 특정 랩 환경의 디바이스를 토대로 작성되었습니다. 이 문서에 사용된 모든 디바이스는 초기화된(기본) 컨피그레이션으로 시작되었습니다. 현재 네트워크가 작동 중인 경우 모든 명령의 잠재적인 영향을 미리 숙지하시기 바랍니다.
배경 정보
- Catalyst 9400 Supervisor1(C9400-SUP-1)에는 3개의 UADP 2.0 포워딩 ASIC(0, 1, 2)이 있습니다.
- 각 UADP 2.0 포워딩 ASIC에는 다음이 포함됩니다.
- 듀얼 코어(0, 1) - 이전 세대의 UADP 2.0 ASICS에는 이러한 기능이 없었습니다.
- SIF(Stack Interfaces) - 내부 스택 링을 통해 다른 2개의 UADP 2.0 ASIC에 연결하는 데 사용됩니다.
- NIF(Network Interfaces) - 백플레인을 통해 하나 이상의 라인 카드에 연결하는 데 사용됩니다.
- 라인 카드 및 수퍼바이저 업링크 인터페이스에 대한 모든 패킷 포워딩 결정은 활성 수퍼바이저의 3 UADP 2.0 포워딩 ASIC에 의해 이루어집니다.
- 이 예에서 사용되는 라인 카드에는 1개의 라인 카드 단일 코어 stub ASIC가 있으며, 이는 패킷 포워딩 결정과 관련이 없습니다.
- 라인 카드의 라인 카드 stub ASIC는 백플레인을 통해 수퍼바이저의 3개 UADP 2.0 포워딩 ASIC 중 1개 이상에 연결됩니다.
- 수퍼바이저의 3개의 UADP 2.0 포워딩 ASIC는 모든 패킷 포워딩 결정을 수행합니다.
용어
| 약어 |
정의 |
| RP |
라우트 프로세서 |
| FP |
포워딩 프로세서 |
| 연방 |
포워딩 엔진 드라이버. Supervisor Forwarding ASIC를 프로그래밍하는 소프트웨어 프로세스입니다. |
| 개체 관리자 |
개체 데이터베이스에 비동기 개체로 저장되는 FP 소프트웨어 MAC 항목입니다. |
| LSMPI |
Linux 공유 메모리 펀트 인터페이스. 데이터 플레인(hardware-UADP 2.0)과 컨트롤 플레인(software-CPU) 간의 전송. |
| IFM |
인터페이스 관리자 소프트웨어 프로세스 |
| IF_ID |
인터페이스 IDentifier는 특정 인터페이스를 나타내는 고유한 값입니다. 스위치에서 내부 프로그래밍하는 동안 사용됩니다. |
| 초기 |
인스턴스. 인터페이스가 연결된 UADP 2.0 Asic/Core를 나타냅니다. 0=Asic0/Core0, 1=Asic0/Core1, 2=Asic1/Core0, 3=Asic1/Core1, 4=Asic2/Core0, 5=Asic2/Core1. |
| 아식 |
인터페이스가 연결된 UADP 2.0을 지정합니다. 0=UADP 2.0 #0, 1=UADP 2.0 #1, 2= UADP 2.0 #2. |
| 코어 |
UADP 2.0 인터페이스의 어떤 코어와 연결되어 있는지 지정합니다. 0=core0, 1=core1. |
| 포트 |
슬롯 내의 포트의 서수 인스턴스 번호입니다. 동일한 슬롯 내에서 모든 포트 번호는 고유합니다. |
| 하위 포트 |
포트 그룹(Cntx)에서 하위 포트(Cntx 및 SubPort)가 포함된 전면 패널 포트에 대한 포트를 식별합니다(Cntx 및 SubPort는 함께 하위 포트 고유 포트를 식별합니다). |
| 맥 |
인터페이스에서 MACsec(보안 인증 및 암호화)을 실행할 때 사용되는 인터페이스 식별자입니다. |
| Cntx |
상황. 전면 패널 인터페이스가 하위 포트(Cntx 및 SubPort 모두 하위 포트)될 때 포트가 속한 그룹 번호. |
| LPN |
인터페이스와 연결된 논리적 포트 번호입니다. |
| GPN |
인터페이스와 연결된 전역 포트 번호입니다. |
| NIF 입력 |
네트워크 인터페이스; NRU = 네트워크 이중화 업링크 |
| IF_IS |
인터페이스 IDentifier입니다. 이는 특정 인터페이스를 나타내는 고유한 값입니다. 스위치에서 내부적으로 다양한 프로그래밍을 하는 동안 사용됩니다. |
| 포트_LE |
포트 논리 엔터티입니다. 인터페이스 컨피그레이션입니다. |
| AOM |
비동기 개체 관리자 FP는 개체 데이터베이스에 정보를 개체로 프로그래밍합니다. |
| 부사장 |
가상 포트 |
| MATM |
MAC 주소 테이블 관리자 |
| RP |
라우트 프로세서 |
| OM_PTR |
개체 관리자 포인터 |
| 테이블_ID |
테이블 식별자 = vlan |
| CMAN |
섀시 관리자 |
| FP |
포워딩 프로세서 |
| fp_port |
전면 패널 포트입니다. |
| 시프 |
스택 인터페이스(수퍼바이저의 다른 2개의 UADP 2.0 포워딩 ASIC에 연결). |
| 니프 |
네트워크 인터페이스(전면 패널 인터페이스) |
| IGR / EGR |
인그레스/이그레스 |
| IQS |
인그레스 대기열 스케줄러 |
| SQS |
스택 큐 스케줄러 |
| PBC |
패킷 버퍼 복합 |
| AQM |
활성 대기열 관리. 이렇게 하면 혼잡 관리 확인이 수행됩니다. |
| AQMRed |
활성 대기열 관리 임의 초기 탐지 |
| EQC |
이그레스 대기열 컨트롤러 |
| ESM |
이그레스 스케줄러 관리 |
| RWE |
엔진 재작성 패킷에서 헤더 정보를 추가하거나 삭제합니다. |
| IOMD |
입력 출력 모듈 드라이버 |
| fp_port |
전면 패널 포트입니다. |
| 니프 |
네트워크 인터페이스(전면 패널 인터페이스) |
| SLI |
시스템 링크 인터페이스(수퍼바이저 대상) |
| IGR / EGR = |
인그레스/이그레스 |
| AQMRed |
활성 대기열 관리 임의 초기 탐지 |
| OCI |
대역 외 제어 인터페이스 = 라인 카드와 활성 수퍼바이저 간의 내부 통신 채널 |
| MATM |
MAC 주소 테이블 관리자 |
| MAC 이동 수 |
MAC 주소가 새 인터페이스에서 이동(학습된 경우)할 횟수입니다. 이동 횟수는 엔드 호스트가 한 인터페이스에서 다른 인터페이스로 물리적으로 이동되거나, 무선 호스트가 한 액세스 포인트(AP)에서 다른 인터페이스에 연결된 다른 AP로 로밍하거나, 스패닝 트리 경로가 변경되거나 루프가 변경될 때 발생할 수 있습니다. |
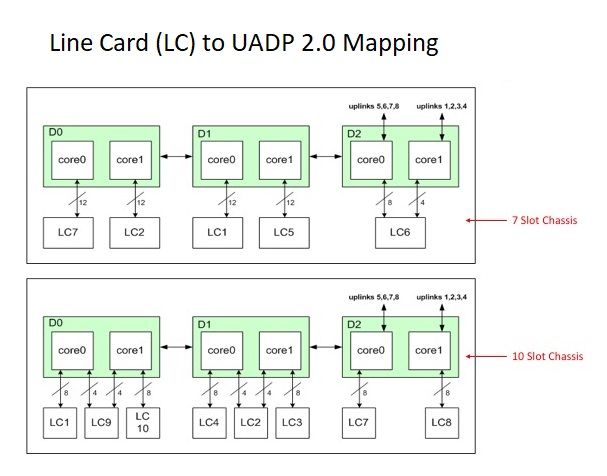 UADP에 대한 라인 카드
UADP에 대한 라인 카드
토폴로지
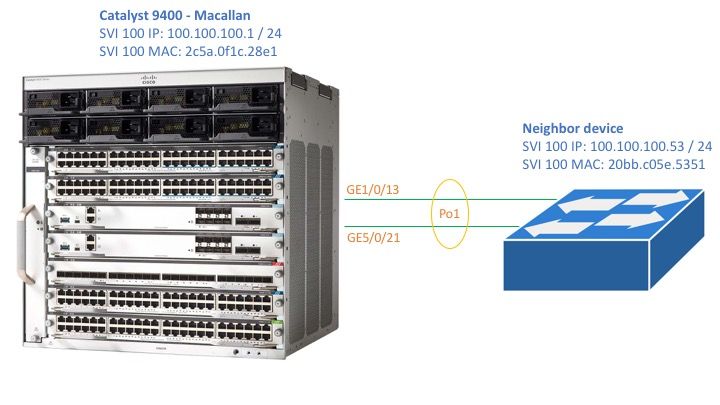
C9400#show version Cisco IOS XE Software, Version 16.06.01 Cisco IOS Software [Everest], Catalyst L3 Switch Software (CAT9K_IOSXE), Version 16.6.1, RELEASE SOFTWARE (fc2) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2017 by Cisco Systems, Inc. Compiled Sat 22-Jul-17 05:51 by mcpre --snip--
C9400#show module Chassis Type: C9407R Mod Ports Card Type Model Serial No. ---+-----+--------------------------------------+--------------+-------------- 1 48 48-Port 10/100/1000 (RJ-45) C9400-LC-48T JAE211703RC 2 48 48-Port UPOE 10/100/1000 (RJ-45) C9400-LC-48U JAE21150CGD 3 10 Supervisor 1 Module C9400-SUP-1 JAE21240235 4 10 Supervisor 1 Module C9400-SUP-1 JAE21240235 5 48 48-Port UPOE 10/100/1000 (RJ-45) C9400-LC-48U JAE21150CG9 Mod MAC addresses Hw Fw Sw Status ---+--------------------------------+----+------------+------------------+-------- 1 E4AA.5D54.C84C to E4AA.5D54.C87B 0.6 16.6.1r [FC 16.06.01 ok 2 E4AA.5D54.B430 to E4AA.5D54.B45F 0.6 16.6.1r [FC 16.06.01 ok 3 2C5A.0F1C.28EC to 2C5A.0F1C.28F5 0.6 16.6.1r [FC 16.06.01 ok 4 2C5A.0F1C.28F6 to 2C5A.0F1C.28FF 0.6 16.6.1r [FC 16.06.01 ok 5 E4AA.5D54.B658 to E4AA.5D54.B687 0.6 16.6.1r [FC 16.06.01 ok Mod Redundancy Role Operating Redundancy Mode Configured Redundancy Mode ---+-------------------+-------------------------+--------------------------- 3 Active sso sso 4 Standby sso sso
C9400#show running-config interface port-channel 1 interface Port-channel1 switchport trunk allowed vlan 100 switchport mode trunk
C9400#show running-config interface gigabitEthernet 1/0/13 interface GigabitEthernet1/0/13 switchport trunk allowed vlan 100 switchport mode trunk channel-group 1 mode active
C9400#show running-config interface gigabitEthernet 5/0/21 interface GigabitEthernet5/0/21 switchport trunk allowed vlan 100 switchport mode trunk channel-group 1 mode active
C9400#show etherchannel summary --snip-- Group Port-channel Protocol Ports ------+-------------+-----------+----------------------------------------------- 1 Po1(SU) LACP Gi1/0/13(P) Gi5/0/21(P)
참고: show platform 명령을 사용하려면 service internal global configuration 명령이 문에 포함되어야 합니다.
인터페이스 프로그래밍
UADP 2.0 인스턴스 매핑에 대한 인터페이스
interface programming 명령은 모든 라인 카드에 대한 전면 패널 인터페이스 매핑을 Active Supervisor의 3 UADP 2.0 포워딩 ASIC 중 하나에 표시합니다.
출력 예
이 예에서는 다음을 보여 줍니다.
- Interface Gig1/0/3은 다음에 연결됩니다. 수퍼바이저의 UADP 2.0 인스턴스 2(UADP 2.0 Asic 1, Core 0)
- Interface Gig5/0/21이 Supervisor의 UADP 2.0 인스턴스 3(UADP 2.0 Asic 1, Core 1)에 연결되어 있습니다.
C9400#show platform software fed active ifm mappings
Interface IF_ID Inst Asic Core Port SubPort Mac Cntx LPN GPN Type Active GigabitEthernet1/0/1 0x7 2 1 0 0 0 4 4 1 101 NIF Y GigabitEthernet1/0/2 0x8 2 1 0 1 1 4 4 2 102 NIF Y --snip-- GigabitEthernet1/0/13 0x13 2 1 0 12 4 0 0 13 1105 NIF Y --snip-- GigabitEthernet5/0/21 0x8f 3 1 1 20 4 5 5 21 1104 NIF Y --snip--
물리적 인터페이스 프로그래밍
show platform 명령은 이전 명령 예의 IF_ID 값에 따라 Gig1/0/3에 대한 소프트웨어 컨피그레이션 세부 정보를 표시합니다.
C9400#show platform software fed active ifm if-id 0x13
Interface IF_ID : 0x0000000000000013
Interface Name : GigabitEthernet1/0/13
Interface Block Pointer : 0x7fe5c5aab7b8
Interface State : READY
Interface Status : ADD, UPD
Interface Ref-Cnt : 7
Interface Type : ETHER
Port Type : SWITCH PORT
Port Location : LOCAL
Slot : 1
Unit : 0
Slot Unit : 13
SNMP IF Index : 14
GPN : 1105
EC Channel : 1
EC Index : 1
Port Handle : 0x72000285
LISP v4 Mobility : false
LISP v6 Mobility : false
QoS Trust Type : 0
Port Information
Handle ............ [0x72000285]
Type .............. [Layer2]
Identifier ........ [0x13]
Slot .............. [1]
Unit .............. [13]
Port Physical Subblock
Affinity .......... [local]
Asic Instance ..... [2 (A:1,C:0)]
AsicPort .......... [12]
AsicSubPort ....... [4]
MacNum ............ [0]
ContextId ......... [0]
LPN ............... [13]
GPN ............... [113]
Speed ............. [1GB]
type .............. [NIF]
PORT_LE ........... [0x7fe5c5aabc28]
L3IF_LE ........... [0x0]
EC GPN ............ [1105]
EC L3IF_LE ........ [0x0]
EC Port Mask ...... [0xaaaaaaaaaaaaaaaa]
DI ................ [0x7fe5c5ab5c48]
Port L2 Subblock
Enabled ............. [Yes]
Allow dot1q ......... [Yes] ---> interface Gig1/0/13 is configured as a trunk
Allow native ........ [Yes]
Default VLAN ........ [1]
Allow priority tag ... [Yes]
Allow unknown unicast [Yes]
Allow unknown multicast[Yes]
Allow unknown broadcast[Yes]
Allow unknown multicast[Enabled]
Allow unknown unicast [Enabled]
IPv4 ARP snoop ....... [No]
IPv6 ARP snoop ....... [No]
Jumbo MTU ............ [1500]
Learning Mode ........ [1]
Port QoS Subblock
Trust Type .................... [0x2]
Default Value ................. [0]
Ingress Table Map ............. [0x0]
Egress Table Map .............. [0x0]
Queue Map ..................... [0x0]
Port Netflow Subblock
Port Policy Subblock
List of Ingress Policies attached to an interface
List of Egress Policies attached to an interface
Ref Count : 7 (feature Ref Counts + 1)
IFM Feature Ref Counts
FID : 100, Ref Count : 1
FID : 57, Ref Count : 1
FID : 115, Ref Count : 1
FID : 17, Ref Count : 1
FID : 78, Ref Count : 1
FID : 30, Ref Count : 1
IFM Feature Sub block information
FID : 57, Private Data : 0x7fe5c685e748
FID : 17, Private Data : 0x7fe5c5e85f38
FID : 30, Private Data : 0x7fe5c5e85aa8
이 명령은 이전 명령의 PORT_LE 값에 따라 Gig1/0/3에 대한 하드웨어 컨피그레이션 세부 정보를 표시합니다.
| 가치 |
정의 |
| 값 0 |
값이 설정되지 않았습니다. |
| 값 1 |
대부분의 경우 설정된 값입니다. |
C9400#show platform hardware fed active fwd-asic abstraction print-resource-handle 0x7fe5c5aabc28 1 Handle:0x7fe5c5aabc28 Res-Type:ASIC_RSC_PORT_LE Res-Switch-Num:0 Asic-Num:2 Feature-ID:AL_FID_IFM Lkp-ftr-id:LKP_FEAT_INGRESS_PRECLASS1_IPV4 ref_count:1 priv_ri/priv_si Handle: (nil)Hardware Indices/Handles: index2:0xc mtu_index/l3u_ri_index2:0x4 sm handle [ASIC 2]: 0x7fe5c5abb588 Detailed Resource Information (ASIC#2) ----------------------------------------
LEAD_PORT_ALLOW_BROADCAST value 1 Pass LEAD_PORT_ALLOW_CAPWAP value 0 Pass LEAD_PORT_ALLOW_CTS value 0 Pass LEAD_PORT_ALLOW_DOT1Q_TAGGED value 1 Pass LEAD_PORT_ALLOW_MULTICAST value 1 Pass LEAD_PORT_ALLOW_NATIVE value 1 Pass LEAD_PORT_ALLOW_NON_CTS value 0 Pass LEAD_PORT_ALLOW_PRIORITY_TAGGED value 1 Pass LEAD_PORT_ALLOW_UNICAST value 1 Pass LEAD_PORT_ALLOW_UNKNOWN_ETHER_TYPE value 0 Pass LEAD_PORT_ALLOW_UNKNOWN_UNICAST value 1 Pass LEAD_PORT_ALLOW_VLAN_LOAD_BALANCE_GROUP value 15 Pass LEAD_PORT_ALLOW_VRF value 0 Pass LEAD_PORT_ARP_OR_ND_SNOOPING_ENABLED_IPV4 value 0 Pass LEAD_PORT_ARP_OR_ND_SNOOPING_ENABLED_IPV6 value 0 Pass LEAD_PORT_AUTH_MODE value 0 Pass LEAD_PORT_CAPWAP_TUNNEL value 0 Pass LEAD_PORT_CONTENT_MATCHING_ENABLED value 0 Pass LEAD_PORT_CTS_ENABLED value 0 Pass LEAD_PORT_CUSTOMER_PORT value 0 Pass LEAD_PORT_DAI_OR_ND_TRUST_MODE_IPV4 value 0 Pass LEAD_PORT_DAI_OR_ND_TRUST_MODE_IPV6 value 0 Pass LEAD_PORT_DATA_GLEAN_LEARN_IPV4 value 0 Pass --snip--
Etherchannel 프로그래밍
이러한 Etherchannel 프로그래밍 예제 출력에서 RP는 FP를 프로그래밍하고, FP는 FED를 프로그래밍하고, FED는 Supervisor 포워딩 ASIC 하드웨어를 프로그래밍합니다. RP 소프트웨어 항목은 객체 데이터베이스에 객체로 저장되고, FP 소프트웨어 항목은 객체 데이터베이스에 비동기 객체로 저장됩니다.
C9400#show etherchannel summary --snip-- Group Port-channel Protocol Ports ------+-------------+-----------+----------------------------------------------- 1 Po1(SU) LACP Gi1/0/13(P) Gi5/0/21(P)
이 출력에서 그룹 마스크는 0이 아닙니다. 이는 트래픽 흐름이 전송되는 이더넷 채널의 링크를 결정하는 데 해시 프로세스에 사용됩니다.
C9400#show platform software interface rp active brief Forwarding Manager Interfaces Information Name ID QFP ID ------------------------------------------------------------- Null0 1 0 GigabitEthernet1/0/1 7 0 GigabitEthernet1/0/2 8 0 GigabitEthernet1/0/3 9 0 —snip— GigabitEthernet1/0/13 19 0 —snip— GigabitEthernet5/0/21 143 0 —snip— Port-channel1 748 0 —snip—
C9400#show platform software fed active etherchannel 1 group-mask
Group Mask Info
Aggport IIF Id: 00000000000002EC ---> hex 0x2EC = dec 748
Active Port: : 2 -------------------> 2 active interfaces in the etherchannel = the Member ports below
Member Ports
If Name If Id local Group Mask
-------------------------------------------------------------------
GigabitEthernet1/0/13 0000000000000013 true 5555555555555555 ---> hex 0x13 = dec 19
GigabitEthernet5/0/21 000000000000008f true aaaaaaaaaaaaaaaa ---> hex 0x8f = dec 143
이 명령은 Port-channel 1의 컨피그레이션을 보여줍니다.
C9400#show platform software fed active ifm if-id 0x000002ec Interface IF_ID : 0x00000000000002ec Interface Name : Port-channel1 Interface Block Pointer : 0x7fe5c685df98 Interface State : READY Interface Status : ADD, UPD Interface Ref-Cnt : 5 Interface Type : ETHERCHANNEL Port Type : SWITCH PORT Channel Number : 1 SNMP IF Index : 720 Port Handle : 0x50002f6 #Of Active Ports : 2 Base GPN : 1104 Index[2] : 0000000000000013 ---> Gig1/0/13 from previous command output Index[3] : 000000000000008f ---> Gig5/0/21 from previous command output Port Information Handle ............ [0x50002f6] Type .............. [L2-Ethchannel] Identifier ........ [0x2ec] Unit .............. [1] Port Logical Subblock L3IF_LE handle .... [0x0] Num physical port . [2] GPN Base .......... [1104] Num physical port on asic [0] is [0] DiBcam handle on asic [0].... [0x0] Num physical port on asic [1] is [0] DiBcam handle on asic [1].... [0x0] Num physical port on asic [2] is [1] ------------> Gig1/0/13 is on ASIC instance 2 (Supervisor ASIC 1, core 0) DiBcam handle on asic [2].... [0x7fe5c6ae3608] Num physical port on asic [3] is [1] ------------> Gig5/0/21 is on ASIC instance 3 (Supervisor ASIC 1, core 1) DiBcam handle on asic [3].... [0x7fe5c685d7e8] Num physical port on asic [4] is [0] DiBcam handle on asic [4].... [0x0] Num physical port on asic [5] is [0] DiBcam handle on asic [5].... [0x0] Port L2 Subblock Enabled ............. [No] Allow dot1q ......... [No] Allow native ........ [No] Default VLAN ........ [0] Allow priority tag ... [No] Allow unknown unicast [No] Allow unknown multicast[No] Allow unknown broadcast[No] Allow unknown multicast[Enabled] Allow unknown unicast [Enabled] IPv4 ARP snoop ....... [No] IPv6 ARP snoop ....... [No] Jumbo MTU ............ [0] Learning Mode ........ [0] Port QoS Subblock Trust Type .................... [0x7] Default Value ................. [0] Ingress Table Map ............. [0x0] Egress Table Map .............. [0x0] Queue Map ..................... [0x0] Port Netflow Subblock Port Policy Subblock List of Ingress Policies attached to an interface List of Egress Policies attached to an interface Ref Count : 5 (feature Ref Counts + 1) IFM Feature Ref Counts FID : 115, Ref Count : 1 FID : 78, Ref Count : 1 No Sub Blocks Present
이 명령은 매핑 인터페이스의 컨피그레이션을 표시합니다.
| 약어/인스턴스 |
정의 |
| IFM |
인터페이스 관리자 |
| 인스턴스 |
Gig1/0/13은 인터페이스 ID가 0x13인 ASIC 인스턴스 2(UADP 2.0 ASIC 1, 코어 0)에 있습니다. |
| 인스턴스 |
Gig5/0/21은 인터페이스 ID가 0x8f인 ASIC 인스턴스 3(UADP 2.0 ASIC 1, 코어 1)에 있습니다. |
C9400#show platform software fed active ifm mappings
Interface IF_ID Inst Asic Core Port SubPort Mac Cntx LPN GPN Type Active GigabitEthernet1/0/1 0x7 2 1 0 0 0 4 4 1 101 NIF Y GigabitEthernet1/0/2 0x8 2 1 0 1 1 4 4 2 102 NIF Y --snip-- GigabitEthernet1/0/13 0x13 2 1 0 12 4 0 0 13 1105 NIF Y --snip-- GigabitEthernet5/0/21 0x8f 3 1 1 20 4 5 5 21 1104 NIF Y --snip--
전역 Etherchannel 컨피그레이션
C9400#show platform software ether-channel rp active global-config Forwarding Manager EtherChannel Global Configuration Information Frame Dist Method: Dest-IP-Address ---> distribution (hash) method: a packet's destination IP address is used to determine which etherchannel member link it is sent out on
C9400#show platform software ether-channel fp active global-config
Forwarding Manager EtherChannel Global Configuration Information
Frame Dist Method: Dest-IP-Address
AOM ID: 27
Status: Done ----------------> Programming in hardware is complete (FP received acknowledgement from FED)
C9400#show platform software object-manager fp active object 27 Object identifier: 27 Description: EtherChannel global configuration object Status: Done, Epoch: 0, Client data: 0x792e6e28
VLAN 프로그래밍
C9400#show platform software fed active vlan 100 VLAN Fed Information Vlan Id IF Id LE Handle STP Handle L3 IF Handle SVI IF ID MVID --------------------------------------------------------------------------------------------------------------- 100 0x0000000000420011 0x00007fe5c4616ef8 0x00007fe5c4617778 0x00007fe5c50dac28 0x00000000000002ea 10
이 명령은 VLAN 100에 대한 하드웨어 컨피그레이션 설정 세부사항을 표시합니다.
| 가치 |
정의 |
| 값 0 |
값이 설정되지 않았습니다. |
| 값 1 |
대부분의 경우 설정된 값입니다. |
C9400#show platform hardware fed active fwd-asic abstraction print-resource-handle 0x00007fe5c4616ef8 1 Handle:0x7fe5c4616ef8 Res-Type:ASIC_RSC_VLAN_LE Res-Switch-Num:255 Asic-Num:255 Feature-ID:AL_FID_L2 Lkp-ftr-id:LKP_FEAT_INVALID ref_count:1 priv_ri/priv_si Handle: (nil)Hardware Indices/Handles: index0:0xa mtu_index/l3u_ri_index0:0x0 sm handle [ASIC 0]: 0x7fe5c461c1d8 index1:0xa mtu_index/l3u_ri_index1:0x0 sm handle [ASIC 1]: 0x7fe5c461d688 index2:0xa mtu_index/l3u_ri_index2:0x0 sm handle [ASIC 2]: 0x7fe5c461eb38 index3:0xa mtu_index/l3u_ri_index3:0x0 index4:0xa mtu_index/l3u_ri_index4:0x0 index5:0xa mtu_index/l3u_ri_index5:0x0 Cookie length: 56 00 00 00 00 00 00 00 00 64 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 Detailed Resource Information (ASIC#0) ---> ASIC instance 0 = Supervisor ASIC 0, core 0 --snip-- Detailed Resource Information (ASIC#1) ---> ASIC instance 1 = Supervisor ASIC 0, core 1 --snip-- Detailed Resource Information (ASIC#2) ---> ASIC instance 2 = Supervisor ASIC 1, core 0 ---------------------------------------- LEAD_VLAN_ALLOW_SNOOPING_IGMP_OR_MLD_IPV4 value 0 Pass LEAD_VLAN_ALLOW_SNOOPING_IGMP_OR_MLD_IPV6 value 0 Pass LEAD_VLAN_ARP_OR_ND_SNOOPING_ENABLED_IPV4 value 0 Pass LEAD_VLAN_ARP_OR_ND_SNOOPING_ENABLED_IPV6 value 0 Pass LEAD_VLAN_BLOCK_L2_LEARN value 0 Pass LEAD_VLAN_CONTENT_MATCHING_ENABLED value 0 Pass LEAD_VLAN_DEST_MOD_INDEX_TVLAN_LE value 0 Pass LEAD_VLAN_DHCP_SNOOPING_ENABLED_IPV4 value 0 Pass LEAD_VLAN_DHCP_SNOOPING_ENABLED_IPV6 value 0 Pass LEAD_VLAN_ENABLE_SECURE_VLAN_LEARNING_IPV4 value 0 Pass LEAD_VLAN_ENABLE_SECURE_VLAN_LEARNING_IPV6 value 0 Pass LEAD_VLAN_EPOCH value 0 Pass LEAD_VLAN_L2_PROCESSING_STP_TCN value 0 Pass LEAD_VLAN_L2FORWARD_IPV4_MULTICAST_PKT value 0 Pass LEAD_VLAN_L2FORWARD_IPV6_MULTICAST_PKT value 0 Pass LEAD_VLAN_L3_IF_LE_INDEX_PRIO value 1 Pass LEAD_VLAN_L3IF_LE_INDEX value 111 Pass LEAD_VLAN_LOOKUP_VLAN value 10 Pass ------------> MVID 10 = vlan 100 LEAD_VLAN_MCAST_LOOKUP_VLAN value 10 Pass LEAD_VLAN_RIET_OFFSET value 1 Pass LEAD_VLAN_SNOOPING_FLOODING_ENABLED_IGMP_OR_MLD_IPV4 value 0 Pass LEAD_VLAN_SNOOPING_FLOODING_ENABLED_IGMP_OR_MLD_IPV6 value 1 Pass LEAD_VLAN_SNOOPING_PROCESSING_STP_TCN_IGMP_OR_MLD_IPV4 value 0 Pass LEAD_VLAN_SNOOPING_PROCESSING_STP_TCN_IGMP_OR_MLD_IPV6 value 0 Pass LEAD_VLAN_VLAN_CLIENT_LABEL value 0 Pass LEAD_VLAN_VLAN_CONFIG value 0 Pass LEAD_VLAN_VLAN_FLOOD_ENABLED value 0 Pass LEAD_VLAN_VLAN_ID_VALID value 1 Pass LEAD_VLAN_VLAN_LOAD_BALANCE_GROUP value 15 Pass LEAD_VLAN_VLAN_ROLE value 0 Pass LEAD_VLAN_VLAN_FLOOD_MODE_BITS value 3 Pass LEAD_VLAN_LVX_VLAN value 0 Pass LEAD_VLAN_EGRESS_DEJAVU_CANON value 0 Pass LEAD_VLAN_EGRESS_INGRESS_VLAN_MODE value 0 Pass LEAD_VLAN_EGRESS_LOOKUP_VLAN value 0 Pass LEAD_VLAN_EGRESS_SGACL_DISABLED value 3 Pass LEAD_VLAN_EGRESS_VLAN_CLIENT_LABEL value 0 Pass LEAD_VLAN_EGRESS_VLAN_ID_VALID value 1 Pass LEAD_VLAN_EGRESS_VLAN_LOAD_BALANCE_GROUP value 15 Pass LEAD_VLAN_EGRESS_INTRA_POD_BCAST value 0 Pass LEAD_VLAN_EGRESS_INTER_POD_BCAST value 0 Pass LEAD_VLAN_MAX value 0 Pass Detailed Resource Information (ASIC#3) ---> ASIC instance 3 = Supervisor ASIC 1, core 1 --snip-- Detailed Resource Information (ASIC#4) ---> ASIC instance 4 = Supervisor ASIC 2, core 0 --snip- Detailed Resource Information (ASIC#5) ---> ASIC instance 5 = Supervisor ASIC 2, core 1 --snip--
스패닝 트리 프로그래밍
C9400#show spanning-tree vlan 100
VLAN0100
Spanning tree enabled protocol rstp Root ID Priority 32868 Address 20bb.c05e.5300 Cost 4 Port 2473 (Port-channel1) Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec Bridge ID Priority 32868 (priority 32768 sys-id-ext 100) Address 2c5a.0f1c.28c0 Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec Aging Time 300 sec Interface Role Sts Cost Prio.Nbr Type ------------------- ---- --- --------- -------- -------------------------------- Gi1/0/1 Desg FWD 19 128.1 Shr Gi2/0/11 Desg FWD 4 128.107 P2p Po1 Root FWD 3 128.2473 P2p Peer(STP)
C9400#show etherchannel summary --snip-- Group Port-channel Protocol Ports ------+-------------+-----------+----------------------------------------------- 1 Po1(SU) LACP Gi1/0/13(P) Gi5/0/21(P)
이러한 명령은 Port-channel 1의 스패닝 트리 포워딩 상태를 표시합니다.
C9400#show platform software interface rp active brief Forwarding Manager Interfaces Information Name ID QFP ID ------------------------------------------------------------- Null0 1 0 GigabitEthernet1/0/1 7 0 GigabitEthernet1/0/2 8 0 GigabitEthernet1/0/3 9 0 —snip— Port-channel1 748 0 —snip—
C9400#show platform software fed active vp summary interface if_id 748
if_id vlan_id pvlan_mode pvlan_vlan stp_state vtp pruned Untagged
-------------------------------------------------------------------------------------------------
748 100 trunk 1 forwarding No No
다음 명령은 VLAN 100에 대한 스패닝 트리 하드웨어 포워딩 상태를 표시합니다.
C9400#show platform software fed active vp summary vlan 100
if_id vlan_id pvlan_mode pvlan_vlan stp_state vtp pruned Untagged
-------------------------------------------------------------------------------------------------
--snip--
748 100 trunk 1 forwarding No No
--snip--
C9400#show platform hardware fed active vlan 100 ingress VLAN STP State in hardware vlan id is:: 100 Interfaces in forwarding state: : Gi2/0/11(Tagged), Gi1/0/1(Tagged), Gi1/0/13(Tagged), Gi5/0/21(Tagged) flood list: : Gi2/0/11, Gi1/0/1, Gi1/0/13, Gi5/0/21
C9400#show platform hardware fed active vlan 100 egress VLAN STP State in hardware vlan id is:: 100 Interfaces in forwarding state: : Gi2/0/11(Tagged), Gi1/0/1(Tagged), Gi1/0/13(Tagged), Gi5/0/21(Tagged)
스패닝 트리 안정성을 확인합니다. TCN(Topology Change Notifications)이 자주 표시되지 않는지 확인합니다.
C9400#show spanning-tree vlan 100 detail
VLAN0100 is executing the rstp compatible Spanning Tree protocol
Bridge Identifier has priority 32768, sysid 10, address 2c5a.0f1c.28c0
Configured hello time 2, max age 20, forward delay 15, transmit hold-count 6
Current root has priority 32868, address 2c5a.0f1c.5300
Root port is 2473 (Port-channel1), cost of root path is 4
Topology change flag not set, detected flag not set
Number of topology changes 1 last change occurred 2w6d ago
from Port-channel1
Times: hold 1, topology change 35, notification 2
hello 2, max age 20, forward delay 15
Timers: hello 0, topology change 0, notification 0, aging 300
--snip--
L2 포워딩 프로그래밍
C9400#show etherchannel summary --snip-- Group Port-channel Protocol Ports ------+-------------+-----------+----------------------------------------------- 1 Po1(SU) LACP Gi1/0/13(P) Gi5/0/21(P)
C9400#ping 100.100.900.53 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 100.100.900.53, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 3/4/5 ms
C9400#show mac address-table dynamic vlan 100 Mac Address Table ------------------------------------------- Vlan Mac Address Type Ports ---- ----------- -------- ----- 100 0000.0200.0800 DYNAMIC Gi1/0/1 100 20bb.c05e.5318 DYNAMIC Po1 100 20bb.c05e.5351 DYNAMIC Po1 Total Mac Addresses for this criterion: 3
소프트웨어 프로그래밍
다음 출력 예에서 RP는 FP를 프로그래밍하고, FP는 FED를 프로그래밍한 다음, FED는 Supervisor 포워딩 ASIC 하드웨어를 마지막으로 프로그래밍합니다. RP 소프트웨어 MAC 항목은 객체 데이터베이스에 객체로 저장되고, FP 소프트웨어 MAC 항목은 객체 데이터베이스에 비동기 객체로 저장됩니다.
C9400#show platform software matm rp active mac 20bb.c05e.5351 1 100 ---> 100 = vlan Tbl_Type Tbl_ID MAC_Address Type Ports AOM_ID/OM_PTR MAT_VLAN 100 20bb.c05e.5351 1 1 OM: 0x3700860010
List of Ports: 748
C9400#show platform software interface rp active brief Forwarding Manager Interfaces Information Name ID QFP ID ------------------------------------------------------------- Null0 1 0 GigabitEthernet1/0/1 7 0 GigabitEthernet1/0/2 8 0 GigabitEthernet1/0/3 9 0 —snip— Port-channel1 748 0 —snip—
C9400#show platform software matm fp active mac 20bb.c05e.5351 Tbl_Type Tbl_ID MAC_Address Type Ports AOM_ID/OM_PTR MAT_VLAN 100 20bb.c05e.5351 1 1 6567 created List of Ports: 748
C9400#show platform software object-manager fp active object 6567 Object identifier: 6567 Description: matm mac entry type VLAN, id 100, 20bb.c05e.5351
Status: Done, Epoch: 0, Client data: 0x799633f8
하드웨어 프로그래밍 - 방법 1
C9400#show platform software fed active matm macTable vlan 100
VLAN MAC Type Seq# macHandle siHandle diHandle *a_time *e_time ports 100 2c5a.0f1c.28e1 0X8002 0 0x7fe5c5eaf1c8 0x7fe5c5924f38 0x0 0 0 Vlan100 100 20bb.c05e.5351 0X1 589 0x7fe5c6b03d68 0x7fe5c6865f78 0x7fe51001b458 300 1 Port-channel1 100 0000.0200.0800 0X1 610 0x7fe5c6b07888 0x7fe5c6b076e8 0x7fe5c5972ce8 300 1 GigabitEthernet1/0/1 Total Mac number of addresses:: 3 *a_time=aging_time(secs) *e_time=total_elapsed_time(secs) Type: MAT_DYNAMIC_ADDR 0x1 MAT_STATIC_ADDR 0x2 ---> Type = dynamically learned MAC address entry MAT_CPU_ADDR 0x4 MAT_DISCARD_ADDR 0x8 MAT_ALL_VLANS 0x10 MAT_NO_FORWARD 0x20 MAT_IPMULT_ADDR 0x40 MAT_RESYNC 0x80 MAT_DO_NOT_AGE 0x100 MAT_SECURE_ADDR 0x200 MAT_NO_PORT 0x400 MAT_DROP_ADDR 0x800 MAT_DUP_ADDR 0x1000 MAT_NULL_DESTINATION 0x2000 MAT_DOT1X_ADDR 0x4000 MAT_ROUTER_ADDR 0x8000 MAT_WIRELESS_ADDR 0x10000 MAT_SECURE_CFG_ADDR 0x20000 MAT_OPQ_DATA_PRESENT 0x40000 MAT_WIRED_TUNNEL_ADDR 0x80000 MAT_DLR_ADDR 0x100000 MAT_MRP_ADDR 0x200000 MAT_MSRP_ADDR 0x400000 MAT_LISP_LOCAL_ADDR 0x800000 MAT_LISP_REMOTE_ADDR 0x1000000 MAT_VPLS_ADDR 0x2000000
macHandle 프로그래밍
| 약어/용어 |
정의 |
| vlan:10 |
MVID 10. VLAN 100은 스위치 내부에서 매핑된 VLAN ID(MVID) 10을 사용합니다. |
| gpn:1104 |
포트 채널 1의 전역 포트 번호입니다. |
| mac:0x20bbc05e5351 |
MAC 주소 20bb.c05e.5351 |
다음은 macHandle 프로그래밍 출력 예입니다.
C9400#show platform hardware fed active fwd-asic abstraction print-resource-handle 0x7fe5c6b03d68 1 Handle:0x7fe5c6b03d68 Res-Type:ASIC_RSC_HASH_TCAM Res-Switch-Num:0 Asic-Num:255 Feature-ID:AL_FID_L2 Lkp-ftr-id:LKP_FEAT_L2_SRC_MAC_VLAN ref_count:1 priv_ri/priv_si Handle: (nil)Hardware Indices/Handles: handle [ASIC: 0]: 0x7fe5c6aed898 handle [ASIC: 1]: 0x7fe5c6b00fd8 handle [ASIC: 2]: 0x7fe5c6858208 Features sharing this resource:Cookie length: 12 5e c0 bb 20 51 53 0a 80 07 00 00 00 Detailed Resource Information (ASIC#0) ---------------------------------------- Number of HTM Entries: 1
Entry 0: (handle 0x7fe5c6aed898) Abs_hash_index: 294 KEY - vlan:10 mac:0x20bbc05e5351 l3_if:0 gpn:1104 epoch:0 static:0 flood_en: 0 vlan_lead_wless_flood_en: 0 client_home_asic: 0 MASK - vlan:0 mac:0x0 l3_if:0 gpn:0 epoch:0 static:0 flood_en:0 vlan_lead_wless_flood_en: 0 client_home_asic: 0 SRC_AD - need_to_learn:0 lrn_v:0 catchall:0 static_mac:0 chain_ptr_v:0 chain_ptr: 0 static_entry_v:0 auth_state:0 auth_mode:0 auth_behavior_tag:0 traf_m:0 is_src_ce:0 DST_AD - si:0xcd bridge:0 replicate:0 blk_fwd_o:0 v4_rmac:0 v6_rmac:0 catchall:0 ign_src_lrn:0 port_mask_o:0 afd_cli_f:0 afd_lbl:0 prio:3 dest_mod_idx:0 destined_to_us:0 pv_trunk:1 smr:0 Detailed Resource Information (ASIC#1) --snip-- Detailed Resource Information (ASIC#2) --snip--
C9400#show platform software fed active vlan 100 VLAN Fed Information Vlan Id IF Id LE Handle STP Handle L3 IF Handle SVI IF ID MVID --------------------------------------------------------------------------------------------------------------- 100 0x0000000000420011 0x00007fe5c4616ef8 0x00007fe5c4617778 0x00007fe5c50dac28 0x00000000000002ea 10
C9400#show platform software fed active ifm mappings etherchannel Mappings Table Chan Interface IF_ID ---------------------------------------------------- 1 Port-channel1 0x000002ec --snip--
C9400#show platform software fed active ifm if-id 0x000002ec <-- IF_ID from previous output Interface IF_ID : 0x00000000000002ec Interface Name : Port-channel1 Interface Block Pointer : 0x7fe5c685df98 Interface State : READY Interface Status : ADD, UPD Interface Ref-Cnt : 5 Interface Type : ETHERCHANNEL Port Type : SWITCH PORT Channel Number : 1 SNMP IF Index : 720 Port Handle : 0x50002f6 #Of Active Ports : 2 Base GPN : 1104 Index[2] : 0000000000000013 Index[3] : 000000000000008f Port Information Handle ............ [0x50002f6] Type .............. [L2-Ethchannel] Identifier ........ [0x2ec] Unit .............. [1] Port Logical Subblock L3IF_LE handle .... [0x0] Num physical port . [2] GPN Base .......... [1104] --snip--
참고: mac에서 학습한 인터페이스는 포트 채널 대신 단일 인터페이스였으며, 이 명령은 GPN과 인터페이스 매핑을 결정하는 데 사용됩니다
C9400#show platform software fed active ifm mappings gpn Mappings Table GPN Interface IF_ID ---------------------------------------------------------------- 101 GigabitEthernet1/0/1 0x00000007 102 GigabitEthernet1/0/2 0x00000008 103 GigabitEthernet1/0/3 0x00000009 --snip--
siHandle 프로그래밍
| 약어/용어 |
정의 |
||
| siHandle |
스테이션 인덱스 핸들 패킷 재작성 정보(RI = Rewrite Index) 및 발신 인터페이스 정보(DI = Destination Index). |
||
| 단일 Supervisor ASIC의 듀얼 코어용 복제 비트맵: |
|||
| 약어/용어 |
정의 |
||
| 로컬 ASIC(LD = 로컬 데이터) |
동일한 ASIC의 목적지, 소스와 동일한 코어 |
||
| 코어 복사(CD = 코어 데이터) |
동일한 ASIC의 목적지, 또 다른 코어 |
||
| 원격 ASIC(RD = 원격 데이터) |
다른 ASIC의 대상. |
||
C9400#show platform hardware fed active fwd-asic abstraction print-resource-handle 0x7fe5c6865f78 1 Handle:0x7fe5c6865f78 Res-Type:ASIC_RSC_SI Res-Switch-Num:255 Asic-Num:255 Feature-ID:AL_FID_L3_UNICAST_IPV4 Lkp-ftr-id:LKP_FEAT_INVALID ref_count:2 priv_ri/priv_si Handle: 0x7fe5c6864938Hardware Indices/Handles: index0:0xcd mtu_index/l3u_ri_index0:0x0 index1:0xcd mtu_index/l3u_ri_index1:0x0 index2:0xcd mtu_index/l3u_ri_index2:0x0 index3:0xcd mtu_index/l3u_ri_index3:0x0 index4:0xcd mtu_index/l3u_ri_index4:0x0 index5:0xcd mtu_index/l3u_ri_index5:0x0 Features sharing this resource:64 (1)] 55 (1)] Cookie length: 56 00 00 00 00 00 00 00 00 64 00 00 00 00 00 00 00 00 00 00 00 07 00 20 bb c0 5e 53 51 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 Detailed Resource Information (ASIC#0) ---> ASIC instance 0 = Supervisor ASIC 0, core 0 ---------------------------------------- Station Index (SI) [0xcd] RI = 0x29 -------------------------------> Rewrite index (no MAC rewrite for L2 forwarding)
DI = 0x51c2 -------------------------------> Destination index = outgoing interface stationTableGenericLabel = 0 stationFdConstructionLabel = 0 lookupSkipIdIndex = 0 rcpServiceId = 0 dejaVuPreCheckEn = 0x1 Replication Bitmap: LD RD CD Detailed Resource Information (ASIC#1) ---> ASIC instance 1 = Supervisor ASIC 0, core 1 --snip-- Detailed Resource Information (ASIC#2) ---> ASIC instance 2 = Supervisor ASIC 1, core 0 --snip-- Detailed Resource Information (ASIC#3) ---> ASIC instance 3 = Supervisor ASIC 1, core 1 --snip-- Detailed Resource Information (ASIC#4) ---> ASIC instance 4 = Supervisor ASIC 2, core 0 --snip-- Detailed Resource Information (ASIC#5) ---> ASIC instance 5 = Supervisor ASIC 2, core 1 --snip--
C9400#show platform hardware fed active fwd-asic resource asic all destination-index range 0x51c2 0x51c2 ASIC#0: --snip-- ASIC#1: --snip-- ASIC#2: -------------------------> ASIC Instance 2 = Supervisor ASIC 1, core 0 Destination Index (DI) [0x51c2] portMap = 0x00000000 00001000 ---> binary 0001 0000 0000 0000 = Port 12 (see next command output) cmi1 = 0 (read right to left, zero based) rcpPortMap = 0 CPU Map Index (CMI) [0] ctiLo0 = 0 ctiLo1 = 0 ctiLo2 = 0 cpuQNum0 = 0 cpuQNum1 = 0 cpuQNum2 = 0 npuIndex = 0 stripSeg = 0 copySeg = 0 ASIC#3: -------------------------> ASIC instance 3 = Supervisor ASIC 1, core 1 Destination Index (DI) [0x51c2] portMap = 0x00000000 00100000 ---> binary 0001 0000 0000 0000 0000 0000 = Port 20 (see next command output) cmi1 = 0 (read right to left, zero based) rcpPortMap = 0 CPU Map Index (CMI) [0] ctiLo0 = 0 ctiLo1 = 0 ctiLo2 = 0 cpuQNum0 = 0 cpuQNum1 = 0 cpuQNum2 = 0 npuIndex = 0 stripSeg = 0 copySeg = 0 ASIC#4: --snip-- ASIC#5: --snip--
C9400#show platform software fed active ifm mappings Interface IF_ID Inst Asic Core Port SubPort Mac Cntx LPN GPN Type Active GigabitEthernet1/0/1 0x7 2 1 0 0 0 4 4 1 101 NIF Y GigabitEthernet1/0/2 0x8 2 1 0 1 1 4 4 2 102 NIF Y --snip-- GigabitEthernet1/0/13 0x13 2 1 0 12 4 0 0 13 1105 NIF Y --snip-- GigabitEthernet5/0/21 0x8f 3 1 1 20 4 5 5 21 1104 NIF Y --snip--
C9400#show etherchannel summary --snip-- Group Port-channel Protocol Ports ------+-------------+-----------+----------------------------------------------- 1 Po1(SU) LACP Gi1/0/13(P) Gi5/0/21(P)
레이어 2 MAC 포워딩 항목이므로 예상 MAC 재작성 정보가 없습니다.
C9400#show platform hardware fed active fwd-asic resource asic all rewrite-index range 0x29 0x29 1 ASIC#0: Rewrite Data Table Entry, ASIC#:0, rewrite_type:1, RI:41 ---> dec 41 = hex 0x29 MAC Addr: MAC Addr: 20:bb:c0:5e:53:51, L3IF LE Index 111 ASIC#1: Rewrite Data Table Entry, ASIC#:1, rewrite_type:1, RI:41 MAC Addr: MAC Addr: 20:bb:c0:5e:53:51, L3IF LE Index 111 ASIC#2:
--snip--
ASIC#3:
--snip--
ASIC#4:
--snip--
ASIC#5:
--snip--
C9400#show mac address-table address 20bb.c05e.5351
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
100 20bb.c05e.5351 DYNAMIC Po1
Total Mac Addresses for this criterion: 1
diHandle 프로그래밍
| 약어 |
정의 |
| diHandle |
대상 인덱스 핸들 발신 인터페이스 정보입니다. |
C9400#show platform hardware fed active fwd-asic abstraction print-resource-handle 0x7fe51001b458 1 Handle:0x7fe51001b458 Res-Type:ASIC_RSC_DI Res-Switch-Num:0 Asic-Num:255 Feature-ID:AL_FID_INVALID Lkp-ftr-id:LKP_FEAT_INVALID ref_count:21 priv_ri/priv_si Handle: (nil)Hardware Indices/Handles: index0:0x51c2 mtu_index/l3u_ri_index0:0x0 index1:0x51c2 mtu_index/l3u_ri_index1:0x0 index2:0x51c2 mtu_index/l3u_ri_index2:0x0 index3:0x51c2 mtu_index/l3u_ri_index3:0x0 index4:0x51c2 mtu_index/l3u_ri_index4:0x0 index5:0x51c2 mtu_index/l3u_ri_index5:0x0 Features sharing this resource:Cookie length: 8 01 00 00 00 c2 51 00 00 Detailed Resource Information (ASIC#0) --snip-- Detailed Resource Information (ASIC#1) --snip-- Detailed Resource Information (ASIC#2) ---> ASIC Instance 2 = Supervisor ASIC 1, core 0 ---------------------------------------- Destination Index (DI) [0x51c2] portMap = 0x00000000 00001000 -------------> binary 0001 0000 0000 0000 = Port 12 (see next command output) cmi1 = 0 (read right to left, zero based) rcpPortMap = 0 CPU Map Index (CMI) [0] ctiLo0 = 0 ctiLo1 = 0 ctiLo2 = 0 cpuQNum0 = 0 cpuQNum1 = 0 cpuQNum2 = 0 npuIndex = 0 stripSeg = 0 copySeg = 0
Detailed Resource Information (ASIC#3) ---> ASIC Instance 3 = Supervisor ASIC 1, core 1 ---------------------------------------- Destination Index (DI) [0x51c2] portMap = 0x00000000 00100000 ---> binary 0001 0000 0000 0000 0000 0000 = Port 20 (see next command output) cmi1 = 0 (read right to left, zero based) rcpPortMap = 0 CPU Map Index (CMI) [0] ctiLo0 = 0 ctiLo1 = 0 ctiLo2 = 0 cpuQNum0 = 0 cpuQNum1 = 0 cpuQNum2 = 0 npuIndex = 0 stripSeg = 0 copySeg = 0
Detailed Resource Information (ASIC#4) --snip-- Detailed Resource Information (ASIC#5) --snip--
C9400#show platform software fed active ifm mappings
Interface IF_ID Inst Asic Core Port SubPort Mac Cntx LPN GPN Type Active GigabitEthernet1/0/1 0x7 2 1 0 0 0 4 4 1 101 NIF Y GigabitEthernet1/0/2 0x8 2 1 0 1 1 4 4 2 102 NIF Y --snip-- GigabitEthernet1/0/13 0x13 2 1 0 12 4 0 0 13 1105 NIF Y --snip-- GigabitEthernet5/0/21 0x8f 3 1 1 20 4 5 5 21 1104 NIF Y --snip--
C9400#show etherchannel summary --snip-- Group Port-channel Protocol Ports ------+-------------+-----------+----------------------------------------------- 1 Po1(SU) LACP Gi1/0/13(P) Gi5/0/21(P)
하드웨어 프로그래밍 - 방법 2
| 약어/용어 |
정의 |
| vlan:10 |
MVID 10. VLAN 100은 스위치 내부에서 매핑된 VLAN ID(MVID) 10을 사용합니다. |
| gpn:1104 |
포트 채널 1의 전역 포트 번호입니다. |
| mac:0x20bbc05e5351 |
MAC 주소 20bb.c05e.5351 |
하드웨어 프로그래밍 방법 2 출력 예:
C9400#show platform hardware fed active matm macTable vlan 100 --snip-- HEAD: MAC address 20bb.c05e.5351 in VLAN 100 KEY: vlan 10, mac 0x20bbc05e5351, l3_if 0, gpn 1104, epoch 0, static 0, flood_en 0, vlan_lead_wless_flood_en 0, client_home_asic 0 MASK: vlan 0, mac 0x0, l3_if 0, gpn 0, epoch 0, static 0, flood_en 0, vlan_lead_wless_flood_en 0, client_home_asic 0 SRC_AD: need_to_learn 0, lrn_v 0, catchall 0, static_mac 0, chain_ptr_v 0, chain_ptr 0, static_entry_v 0, auth_state 0, auth_mode 0, traf_mode 0, is_src_ce 0 DST_AD: si 0xc7, bridge 0, replicate 0, blk_fwd_o 0, v4_mac 0, v6_mac 0, catchall 0, ign_src_lrn 0, port_mask_o 0, afd_cli_f 0, afd_lbl 0, priority 3, dest_mod_idx 0, destined_to_us 0, pv_trunk 1
--snip--
C9400#show platform software fed active vlan 100 VLAN Fed Information Vlan Id IF Id LE Handle STP Handle L3 IF Handle SVI IF ID MVID --------------------------------------------------------------------------------------------------------------- 100 0x0000000000420011 0x00007fe5c4616ef8 0x00007fe5c4617778 0x00007fe5c50dac28 0x00000000000002ea 10
C9400#show platform software fed active ifm mappings etherchannel Mappings Table Chan Interface IF_ID ---------------------------------------------------- 1 Port-channel1 0x000002ec --snip--
C9400#show platform software fed active ifm if-id 0x000002ec Interface IF_ID : 0x00000000000002ec Interface Name : Port-channel1 Interface Block Pointer : 0x7fe5c685df98 Interface State : READY Interface Status : ADD, UPD Interface Ref-Cnt : 5 Interface Type : ETHERCHANNEL Port Type : SWITCH PORT Channel Number : 1 SNMP IF Index : 720 Port Handle : 0x50002f6 #Of Active Ports : 2 Base GPN : 1104 Index[2] : 0000000000000013 Index[3] : 000000000000008f Port Information Handle ............ [0x50002f6] Type .............. [L2-Ethchannel] Identifier ........ [0x2ec] Unit .............. [1] Port Logical Subblock L3IF_LE handle .... [0x0] Num physical port . [2] GPN Base .......... [1104] --snip--
참고: mac에서 학습한 인터페이스가 포트 채널 대신 단일 인터페이스인 경우 다음 명령을 사용하여 gpn-인터페이스 매핑을 결정합니다.
C9400#show platform software fed active ifm mappings gpn Mappings Table GPN Interface IF_ID ---------------------------------------------------------------- 101 GigabitEthernet1/0/1 0x00000007 102 GigabitEthernet1/0/2 0x00000008 103 GigabitEthernet1/0/3 0x00000009 --snip--
TCAM 사용률
각 Supervisor ASIC 인스턴스의 MAC 주소 항목에 대한 TCAM 사용률을 확인하여 스위치에 TCAM 공간이 부족하지 않게 하여 하드웨어에 항목을 저장하십시오.
C9400show platform hardware fed active fwd-asic resource tcam utilization CAM Utilization for ASIC Instance [0] --snip-- CAM Utilization for ASIC Instance [1] --snip-- CAM Utilization for ASIC Instance [2] --snip-- CAM Utilization for ASIC Instance [3]---> ASIC instance 3 = Supervisor ASIC 1, Core 1
Table Max Values Used Values -------------------------------------------------------------------------------- Unicast MAC addresses 65536/1024 13/1 -------------> prefix/mask IGMP and Multicast groups 16384/1024 0/7 L2 Multicast groups 16384/1024 1/9 Directly or indirectly connected routes 49152/65536 0/0 NAT/PAT SA address and Port 0 0 QoS Access Control Entries 18432 34 Security Access Control Entries 18432 0 Ingress Netflow ACEs 1024 0 Policy Based Routing ACEs 2048 9 Egress Netflow ACEs 2048 8 Input Microflow policer ACEs 0 0 Output Microflow policer ACEs 0 0 Flow SPAN ACEs 1024 13 Control Plane Entries 1024 0 Tunnels 1024 0 Lisp Instance Mapping Entries 1024 0 Input Security Associations 512 3 Output Security Associations and Policies 512 0 SGT_DGT 8192/512 0/0 CLIENT_LE 4096/256 2/0 INPUT_GROUP_LE 1024 0 OUTPUT_GROUP_LE 1024 0 Macsec SPD 256 0 CAM Utilization for ASIC Instance [4] --snip-- CAM Utilization for ASIC Instance [5] --snip--
성공적인 하드웨어 프로그래밍
모든 기능(mac 주소, 인터페이스, VLAN 등)은 개체 데이터베이스에 저장되고 하드웨어에서 개체로 프로그래밍됩니다.
RP는 FP를 프로그래밍하고, FP는 FED를 프로그래밍하고, FED는 마지막으로 수퍼바이저 포워딩 ASIC 하드웨어를 프로그래밍합니다. RP 소프트웨어 항목은 개체 데이터베이스에 개체로 저장되고 FP 소프트웨어 항목은 개체 데이터베이스에 비동기 개체로 저장됩니다.
FP가 FED를 프로그래밍할 때(ASIC를 전달하는 수퍼바이저 프로그램), FED는 FP에 승인을 다시 보냅니다. 그런 다음 FP는 하드웨어 프로그래밍이 성공적으로 완료되었음을 나타내기 위해 RP에 전달합니다. FED 하드웨어 프로그래밍이 없거나 잘못된 경우 다음 명령을 사용하여 문제 및/또는 확인을 확인할 수 있습니다.
C9400#show platform software object-manager fp active statistics Forwarding Manager Asynchronous Object Manager Statistics Object update: Pending-issue: 0, Pending-acknowledgement: 0 Batch begin: Pending-issue: 0, Pending-acknowledgement: 0 Batch end: Pending-issue: 0, Pending-acknowledgement: 0 Command: Pending-acknowledgement: 0 Total-objects: 3269 Stale-objects: 0 Resolve-objects: 0 Error-objects: 0 Paused-types: 0
이전 명령에서 보류 중인 문제 상태의 0이 아닌 객체를 표시할 경우 다음 명령을 사용하여 관련 객체 번호를 찾습니다.
C9400#show platform software object-manager fp active pending-issue-update
그런 다음 이 명령을 사용하여 개체 번호와 연결된 고정 프로세스를 확인합니다.
C9400#show platform software object-manager fp active object {object#}
RP 측에서 이 명령을 사용하여 FP가 승인하지 않은 객체에 대한 삭제 보류(Del Pend)를 확인합니다.
C9400#show platform software object-manager rp active object-type-info
Object type Name Count Del Pend Layer ------------------------------------------------------------------------------ CC cc 5 0 2 SPA spa 0 0 4 PORT_DPIDB port_dpidb 164 0 10 CHANNEL_DPIDB channel_dpidb 0 0 12 VIRTUAL_DPIDB virtual_dpidb 503 0 13 SW_DPIDB sw_dpidb 0 0 17 VLAN vlan 0 0 19
--snip--
상태 확인
컨트롤 플레인 트래픽 및 정책
소프트웨어-CPU로 전송된 트래픽에 대해 hardware-UADP 2.0에서 CoPP(컨트롤 플레인 정책) 삭제를 확인합니다. 이는 MAC 학습 및 스패닝 트리 안정성에 영향을 줄 수 있습니다.
C9400#show policy-map control-plane
Control Plane
Service-policy input: system-cpp-policy
--snip--
Class-map: system-cpp-police-sw-forward (match-any)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: none
police:
rate 1000 pps, burst 244 packets
conformed 1298 bytes; actions:
transmit
exceeded 0 bytes; actions:
drop
--snip--
Class-map: system-cpp-police-l2-control (match-any)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: none
police:
rate 500 pps, burst 122 packets
conformed 239197001 bytes; actions:
transmit
exceeded 0 bytes; actions:
drop
--snip--
Class-map: system-cpp-default (match-any)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: none
police:
rate 1000 pps, burst 244 packets
conformed 0 bytes; actions:
transmit
exceeded 0 bytes; actions:
drop
Class-map: class-default (match-any)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: any
이전 예와 동일한 CoPP 출력이 여기에 더 세분화되고 읽기 쉬운(압축) 형식으로 표시됩니다.
C9400#show platform hardware fed active qos queue stats internal cpu policer
CPU Queue Statistics
============================================================================================
(default) (set) Queue Queue
QId PlcIdx Queue Name Enabled Rate Rate Drop(Bytes) Drop(Frames)
0 11 DOT1X Auth Yes 1000 1000 0 0
1 1 L2 Control Yes 2000 400 0 0
2 14 Forus traffic Yes 1000 1000 0 0
3 0 ICMP GEN Yes 600 600 0 0
4 2 Routing Control Yes 5400 1800 0 0
5 14 Forus Address resolution Yes 1000 1000 0 0
6 0 ICMP Redirect Yes 600 600 0 0
7 16 Unused Yes 1000 1000 0 0
8 4 L2 LVX Cont Pack Yes 1000 1000 0 0
9 16 EWLC Control Yes 1000 1000 0 0
10 16 EWLC Data Yes 1000 1000 0 0
11 13 L2 LVX Data Pack Yes 1000 1000 0 0
12 0 BROADCAST Yes 600 600 0 0
13 10 Learning cache ovfl Yes 100 200 0 0
14 13 Sw forwarding Yes 1000 1000 0 0
15 8 Topology Control Yes 13000 13000 0 0
16 12 Proto Snooping Yes 2000 2000 0 0
17 16 DHCP Snooping Yes 1000 1000 0 0
18 9 Transit Traffic Yes 500 400 0 0
19 10 RPF Failed Yes 100 200 0 0
20 15 MCAST END STATION Yes 2000 2000 0 0
21 13 LOGGING Yes 1000 1000 0 0
22 7 Punt Webauth Yes 1000 1000 0 0
23 10 Crypto Control Yes 100 200 0 0
24 10 Exception Yes 100 200 0 0
25 3 General Punt Yes 200 200 0 0
26 10 NFL SAMPLED DATA Yes 100 200 0 0
27 2 Low Latency Yes 5400 1800 0 0
28 10 EGR Exception Yes 100 200 0 0
29 5 Stackwise Virtual Control No 8000 8000 0 0
30 9 MCAST Data Yes 500 400 0 0
31 10 Gold Pkt Yes 100 200 0 0
* NOTE: CPU queue policer rates are configured to the closest hardware supported value
CPU Queue Policer Statistics
====================================================================
Policer Policer Accept Policer Accept Policer Drop Policer Drop
Index Bytes Frames Bytes Frames
-------------------------------------------------------------------
0 3132 36 0 0
1 239197001 721952 0 0
2 123004776 978818 0 0
3 0 0 0 0
4 0 0 0 0
5 0 0 0 0
6 0 0 0 0
7 0 0 0 0
8 1024 16 0 0
9 0 0 0 0
10 13600 200 0 0
11 0 0 0 0
12 0 0 0 0
13 1298 3 0 0
14 80520 9158 0 0
15 2189268 23733 0 0
16 0 0 0 0
17 0 0 0 0
CPP Classes to queue map
======================================================================================
PlcIdx CPP Class : Queues
--------------------------------------------------------------------------------------
0 system-cpp-police-data : ICMP GEN/BROADCAST/ICMP Redirect/
10 system-cpp-police-sys-data : Learning cache ovfl/Crypto Control/Exception/EGR Exception/NFL SAMPLED DATA/Gold Pkt/RPF Failed/
13 system-cpp-police-sw-forward : Sw forwarding/LOGGING/L2 LVX Data Pack/
9 system-cpp-police-multicast : Transit Traffic/MCAST Data/
15 system-cpp-police-multicast-end-station : MCAST END STATION /
7 system-cpp-police-punt-webauth : Punt Webauth/
1 system-cpp-police-l2-control : L2 Control/
5 system-cpp-police-stackwise-virt-control : Stackwise Virtual Control/
2 system-cpp-police-routing-control : Routing Control/Low Latency/
3 system-cpp-police-control-low-priority : General Punt/
4 system-cpp-police-l2lvx-control : L2 LVX Cont Pack/
8 system-cpp-police-topology-control : Topology Control/
11 system-cpp-police-dot1x-auth : DOT1X Auth/
12 system-cpp-police-protocol-snooping : Proto Snooping/
14 system-cpp-police-forus : Forus Address resolution/Forus traffic/
5 system-cpp-police-stackwise-virt-control : Stackwise Virtual Control/
16 system-cpp-default : DHCP Snooping/Unused/EWLC Control/EWLC Data/
소프트웨어(CPU) 관점에서 CPU 펀트 경로(하드웨어-UADP 2.0에서 소프트웨어-CPU로) 통계를 확인합니다.
C9400#show platform software infrastructure lsmpi
LSMPI interface internal stats:
enabled=0, disabled=0, throttled=0, unthrottled=0, state is ready
Input Buffers = 8801257
Output Buffers = 5506129
rxdone count = 8801257
txdone count = 5506128
Rx no particletype count = 0
Tx no particletype count = 0
Txbuf from shadow count = 0
No start of packet = 0
No end of packet = 0
Punt drop stats:
Bad version 0
Bad type 0
Had feature header 0
Had platform header 0
Feature header missing 0
Common header mismatch 0
Bad total length 0
Bad packet length 0
Bad network offset 0
Not punt header 0
Unknown link type 0
No swidb 0
Bad ESS feature header 0
No ESS feature 0
No SSLVPN feature 0
No PPP bridge feature 0
Punt For PPP bridge type packets 0
Punt For Us type unknown 0
EPC CP RX Pkt cleansed 0
Punt cause out of range 0
IOSXE-RP Punt packet causes:
42879 Layer2 control and legacy packets
3644168 ARP request or response packets
7584 For-us data packets
1794 Mcast Directly Connected Source packets
1573 Mcast PIM signaling packets
750076 For-us control packets
38058 Layer2 bridge domain data packet packets
3823736 Layer2 control protocols packets
FOR_US Control IPv4 protcol stats:
750076 [proto=0] packets
Packet histogram(500 bytes/bin), avg size in 125, out 126:
Pak-Size In-Count Out-Count
0+: 8228322 5207592
500+: 41355 1717
1000+: 4331 2402
1500+: 35860 20017
Lsmpi11/3 is up, line protocol is up <-- CPU interface
Hardware is LSMPI
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive not set
Unknown, Unknown, media type is unknown media type
output flow-control is unsupported, input flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input never, output never, output hang never
Last clearing of "show interface" counters never
Input queue: 0/1500/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
8309868 packets input, 0 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
0 watchdog, 0 multicast, 0 pause input
5231728 packets output, 659535525 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out
C9400#show platform software infrastructure lsmpi punt
LSMPI punt statistics
Total packets consumed: 876
Total packets forwarded: 8468766
First frag packets: 0
Total packets consumed & forwarded: 0
Cause Total Total Length Dot1q encap Other SKB
consumed forwarded error exceeded linktype invalid
MPLS ICMP Can't Fragment 0 0 0 0 0 0
IPv4 Options 0 0 0 0 0 0
Layer2 control and legacy 0 0 0 0 0 0
PPP Control 0 0 0 0 0 0
CLNS IS-IS Control 0 0 0 0 0 0
HDLC keepalives 0 0 0 0 0 0
--snip--
소프트웨어(CPU) 관점에서 CPU 삽입 경로(소프트웨어-CPU에서 하드웨어-수퍼바이저를 위한) 통계를 확인합니다.
C9400#show platform software infrastructure inject Statistics for L3 injected packets: 5233473 total inject pak, 3 failed 0 sent, 859329 prerouted 0 non-CEF capable, 855296 non-unicast 859826 IP, 0 IPv6 0 MPLS, 0 Non-IP Tunnel 0 UDLR tunnel, 0 P2MP replicated mcast 0 Non-IP Fastswitched over Tunnel, 4373497 legacy pak path 0 Other packet 0 IP fragmented 644 normal, 391 nexthop 858788 adjacency, 150 feature 0 undefined 3 pak find no adj, 0 no adj-id 137322 sb alloc, 856085 sb local 0 p2mcast failed count 0 p2mcast enqueue fail 0 unicast dhc 0 mobile ip 0 IPv6 NA 0 IPv6 NS 0 Transport failed cases 0 Grow packet buffer per feature packet inject statistics 150 Feature multicast 0 Feature Edge Switching Service 0 Feature Session Border Controller 0 Feature interrupt level 0 Feature use outbound interface 0 Feature interrupt level with OCE 0 Feature ICMPv6 error message 0 Feature Session Border Controller media packet injection 0 Feature Tunnel Ethernet over GRE 0 Feature Secure Socket Layer Virtual Private Network 0 Feature EPC Wireshark injecting packets Statistics for L2 injected packets: 0 total L2 inject pak, 0 failed 0 total BD inject pak, 0 failed 0 total EFP inject pak, 0 failed 0 total VLAN inject pak, 0 failed
FED(UADP 2.0) 관점에서 CPU punt/inject 경로 통계를 확인합니다.
C9400#show platform software fed active lsmpi stat
LSMPI Statistics
-------------------------------------------
Transmit: -----------------------------------> FED transmit = FED (Supervisor) punt to CPU
Packet Count : 8469445
Bytes Count : 1055390613
particle Count : 8951009
particle with App : 7258
Ring Full Error : 0
No Buff Error : 0
TX Ring Free : 2047
TX Ring Busy : 0
TX Ring Size : 2048
TXDone Ring Free : 6816
TXDone Ring Busy : 9567
TXDone Ring Size : 16384
Receive: ---------------------------------> FED receive = CPU inject to FED (Supervisor)
Packet Count : 5450099
Bytes Count : 675084903
Particle Count : 5695697
Particles with App : 4294966854
RX Done Count : 5696139
No SOP : 0
No EOP : 0
Not Enough Buf : 0
Max Not Enough Buf : 0
RX Ring Free : 4095
RX Ring Busy : 0
RX Ring Size : 4096
RXDone Ring Free : 8191
RXDone Ring Busy : 0
RXDone Ring Size : 8192
-------------------------------------------
FED(Supervisor) 관점에서 CPU 펀트 경로(하드웨어-Supervisor에서 소프트웨어-CPU로) 통계를 확인합니다.
C9400#show platform software fed active punt cause summary Statistics for all causes Cause Cause Info Rcvd Dropped ------------------------------------------------------------------------------ 7 ARP request or response 3644168 0 11 For-us data 1524 0 12 Mcast Directly Connected Source 1794 0 25 Mcast PIM signaling 1573 0 55 For-us control 750461 0 58 Layer2 bridge domain data packet 38058 0 96 Layer2 control protocols 3825228 0 ------------------------------------------------------------------------------
FED(Supervisor) 관점에서 31개의 개별 CPU 펀트 대기열의 상태를 확인합니다.
C9400#show platform software fed active cpu-interface queue retrieved dropped invalid hol-block ------------------------------------------------------------------------- Routing Protocol 790844 0 0 0 L2 Protocol 2774488 0 0 0 sw forwarding 0 0 0 0 broadcast 0 0 0 0 icmp 0 0 0 0 icmp redirect 0 0 0 0 logging 0 0 0 0 rpf-fail 1573 0 0 0 DOT1X authentication 0 0 0 0 Forus Traffic 1524 0 0 0 Forus Resolution 3644192 0 0 0 Wireless q5 0 0 0 0 Wireless q1 0 0 0 0 Wireless q2 0 0 0 0 Wireless q3 0 0 0 0 Wireless q4 0 0 0 0 Learning cache 0 0 0 0 Topology control 1198807 0 0 0 Proto snooping 0 0 0 0 BFD Low latency 0 0 0 0 Transit Traffic 0 0 0 0 Multi End station 38058 0 0 0 Health Check 0 0 0 0 Health Check 0 0 0 0 Crypto control 0 0 0 0 Exception 0 0 0 0 General Punt 0 0 0 0 NFL sampled data 0 0 0 0 STG cache 0 0 0 0 EGR exception 0 0 0 0 FSS 0 0 0 0 Multicast data 1794 0 0 0
C9400#show platform software fed active punt cpuq all
Punt CPU Q Statistics
===========================================
—snip—
CPU Q Id : 1
CPU Q Name : CPU_Q_L2_CONTROL
Packets received from ASIC : 2669864 -----------> Packets received by the FED process from the Supervisor forwarding ASICs
Send to IOSd total attempts : 2669864 -----------> Packets sent from the FED process to IOSd
Send to IOSd failed count : 0
RX suspend count : 0
RX unsuspend count : 0
RX unsuspend send count : 0
RX unsuspend send failed count : 0
RX consumed count : 0
RX dropped count : 0
RX non-active dropped count : 0
RX conversion failure dropped : 0
RX INTACK count : 2243784
RX packets dq'd after intack : 5074
Active RxQ event : 2243785
RX spurious interrupt : 322266
CPU Q Id : 2
CPU Q Name : CPU_Q_FORUS_TRAFFIC
Packets received from ASIC : 1524
Send to IOSd total attempts : 1524
Send to IOSd failed count : 0
RX suspend count : 0
RX unsuspend count : 0
RX unsuspend send count : 0
RX unsuspend send failed count : 0
RX consumed count : 0
RX dropped count : 0
RX non-active dropped count : 0
RX conversion failure dropped : 0
RX INTACK count : 1347
RX packets dq'd after intack : 8
Active RxQ event : 1347
RX spurious interrupt : 38
—snip—
FED(Supervisor) 관점에서 CPU 주입 경로(소프트웨어-CPU를 하드웨어-수퍼바이저로) 통계를 확인합니다.
C9400#show platform software fed active inject cause summary Statistics for all causes Cause Cause Info Rcvd Dropped ------------------------------------------------------------------------------ 1 L2 control/legacy 4331682 0 2 QFP destination lookup 290 0 3 QFP IPv4/v6 nexthop lookup 391 0 7 QFP adjacency-id lookup 859393 265 8 Mcast specific inject packet 150 0 12 ARP request or response 601 0 ------------------------------------------------------------------------------
FED(UADP 2.0) 관점에서 2개의 개별 CPU 삽입 대기열의 상태를 확인합니다.
C9400#show platform software fed active inject cpuq all Inject CPU Q Statistics =========================================== CPU Q Id : 0 CPU Q Name : TX_CPUQ_PRIO_LOW ---> low priority CPU inject queue Packets received from IOSd : 168342 Enq to pkt driver total attempts : 168277 Enq to pkt driver failed count : 0 Count of TX CMPL received : 168277 TX suspend count : 0 TX unsuspend count : 0 TX dropped count : 265 TX punted count : 0 TX App enq failed : 0 CPU Q Id : 7 CPU Q Name : TX_CPUQ_PRIO_HI ---> high priority CPU inject queue Packets received from IOSd : 5024664 Enq to pkt driver total attempts : 5024664 Enq to pkt driver failed count : 0 Count of TX CMPL received : 5024664 TX suspend count : 0 TX unsuspend count : 0 TX dropped count : 0 TX punted count : 0 TX App enq failed : 0 Stats for all txq: --------------------------------------------- TX chunk malloc fail count : 0 ---------------------------------------------
MAC 테이블 이벤트 통계
C9400#show platform software fed active matm stats MATM counters Total non-cpu mac entries : 10 Mac Learn SPI Msg Count : 0 Mac Learn SPI Err Count : 0 Mac Delete SPI Msg Count : 0 Mac Delete SPI Err Count : 0 Mac Learn Count : 967 Mac Add Count : 989 Mac AL add Count : 971 Mac Del Count : 957 Mac AL Del Count : 961 Mac Move Count : 2 ---> MAC moves between interfaces (see details above) Mac AL Move Count : 0 Mac Clear Count : 0 Mac Del all count : 6 Mac table create Count : 9 Mac VP event Count : 5 Mac Update info Count : 0 Mac Vlan age config Event Count : 0 Mac Vlan Link Event Count : 6 Mac SVI linkEvent Count : 3 Mac Bsync Event Count : 0 Mac Isync Event Count : 0 Mac Recon Start Count : 0 Mac Recon Event Count : 0 Mac IFM event Count : 75 Mac FEC Event Count : 0 Mac Aging Tick Count : 0 Mac Retry event Count : 0 Mac Hw Update Err Count : 0 Mac In retryQ Count : 0
C9400#configure terminal C9400(config)#mac address-table notification ? change Enable/Disable MAC Notification feature on the switch mac-move Enable Mac Move Notification threshold Configure L2 Table monitoring C9400(config)#mac address-table notification mac-move ---> enabled by default, syslog generated for any MAC move (show logging) C9400(config)#mac address-table notification change ? history-size Number of MAC notifications to be stored interval Interval between the MAC notifications <cr> <cr> C9400(config)#mac address-table notification change ---> disabled by default
C9400#show mac address-table notification mac-move MAC Move Notification: enabled
C9400#show mac address-table notification change
MAC Notification Feature is Enabled on the switch Interval between Notification Traps : 1 secs Number of MAC Addresses Added : 0 Number of MAC Addresses Removed : 0 Number of Notifications sent to NMS : 0 Maximum Number of entries configured in History Table : 1 Current History Table Length : 0 MAC Notification Traps are Disabled History Table contents ----------------------
UADP 2.0 예외 삭제
이 명령은 UADP 2.0 포워딩 ASIC에서 패킷을 삭제하는 모든 이유를 자세히 설명합니다.
C9400#show platform hardware fed active fwd-asic drops exceptions
****EXCEPTION STATS ASIC INSTANCE 0 (asic/core 0/0)**** ================================================================================= Asic/core | NAME | prev | current | delta ================================================================================= 0 0 NO_EXCEPTION 0 0 0 0 0 IPV4_CHECKSUM_ERROR 0 0 0 0 0 ROUTED_AND_IP_OPTIONS_EXCEPTION 0 0 0 0 0 CTS_FILTERED_EXCEPTION 0 0 0 0 0 SIA_TTL_ZERO 0 0 0 0 0 ALLOW_NATIVE_EXCEPTION_COUNT 0 0 0 0 0 ALLOW_DOT1Q_EXCEPTION_COUNT 0 0 0 0 0 ALLOW_PRIORITY_TAGGED_EXCEPTION_COUNT 0 0 0 0 0 ALLOW_UNKNOWN_ETHER_TYPE_EXCEPTION 0 0 0 0 0 IP_SOURCE_GUARD_VIOLATION 0 0 0 0 0 SECURE_L3IF_LEARNING_VIOLATION 0 0 0 0 0 AUTH_DRIVEN_DROP 0 0 0 0 0 VLAN_LOADBALANCE_GROUP_DENY 0 0 0 0 0 RPF_UNICAST_FAIL 0 0 0 0 0 RPF_UNICAST_FAIL_SUPPRESS 0 0 0 0 0 RPF_UNICAST_CHECK_INCOMPLETE 0 0 0 0 0 RPF_MULTICAST_FAIL 0 0 0 0 0 PKT_DROP_COUNT 0 0 0 0 0 SOURCE_ROUTE_EXCEPTION 0 0 0 0 0 IGR_MISC_FATAL_ERROR 0 0 0 0 0 BLOCK_FORWARD 0 0 0 0 0 POLICER_DROP 0 0 0 0 0 DENY_ROUTE 0 0 0 0 0 DENY_BRIDGE 0 0 0 0 0 STATIC_MAC_VIOLATION 0 0 0 0 0 STATIC_IP_VIOLATION 0 0 0 0 0 FPM_DROP_PACKET 0 0 0 0 0 IGR_EXCEPTION_L4_ERROR 0 0 0 0 0 IGR_EXCEPTION_L5_ERROR 0 0 0 0 0 IGR_EXCEPTION_HARDWARE_PARSE_EXCEPTION 0 0 0 0 0 IGR_EXCEPTION_INVALID_VLAN_DROP 0 0 0 0 0 IGR_EXCEPTION_31 0 0 0 0 0 FRAGMENTING_IPV4_WITH_OPTIONS 0 0 0 0 0 FRAGMENTING_IPV6_WITH_EXTENSIONS 0 0 0 0 0 ICMP_REDIRECT 0 0 0 0 0 MTU_FAIL_PUNT_TO_CPU_NO_IP_UNREACHABLE 0 0 0 0 0 LINK_LOCAL_CHECK_FAIL_NO_IP_UNREACHABLE 0 0 0 0 0 IP_UNICAST_TTL_REACHED_ZERO 0 0 0 0 0 MISC_FATAL_ERROR 0 0 0 0 0 STP_OR_FLEXLINK_DROP 0 0 0 0 0 PROTECTED_PORT_DROP 0 0 0 0 0 PVLAN_ISOLATED_CHECK_FAILED 0 0 0 0 0 PVLAN_COMMUNITY_CHECK_FAILED 0 0 0 0 0 DEJA_VU_CHECK_FAILED 0 0 0 0 0 NOT_VLAN_LOAD_BALANCE_GROUP_ALLOWED 0 0 0 0 0 RSPAN_DROP 0 0 0 0 0 SPLIT_HORIZON_DROP 0 0 0 0 0 SYSTEM_TTL_DROP 0 0 0 0 0 PRUNED 0 0 0 0 0 DENY_NO_IP_UNREACHABLE 0 0 0 0 0 IP_MULTICAST_TTL_REACHED_ZERO 0 0 0 0 0 MTU_FAIL_DROP_BRIDGED 0 0 0 0 0 MTU_FAIL_DROP_BRIDGED_IP_ROUTED 0 0 0 0 0 MTU_FAIL_ERSPAN 0 0 0 0 0 LINK_LOCAL_CHECK_FAIL_L3M_VALID 0 0 0 0 0 DENY_NOT_NO_IP_UNREACHABLE 0 0 0 0 0 MTU_FAIL_PUNT_TO_CPU_NOT_NO_IP_UNREACHABLE 0 0 0 0 0 LINK_LOCAL_CHECK_FAIL_NOT_NO_IP_UNREACHABLE 0 0 0 0 0 COPY_TO_CPU 0 0 0 0 0 EGR_L3_ERROR 0 0 0 0 0 EGR_L4_ERROR 0 0 0 0 0 EGR_L5_ERROR 0 0 0 0 0 EGR_HARDWARE_PARSE_EXCEPTION 0 0 0 0 0 EGR_SHOW_FORWARD_DROP 0 0 0 ****EXCEPTION STATS ASIC INSTANCE 1 (asic/core 0/1)**** ================================================================================= Asic/core | NAME | prev | current | delta ================================================================================= 0 1 NO_EXCEPTION 13168 16679 3511 0 1 IPV4_CHECKSUM_ERROR 0 0 0 0 1 ROUTED_AND_IP_OPTIONS_EXCEPTION 81 103 22
--snip--
수퍼바이저 통계 - 수퍼바이저-라인 카드 데이터 경로
특정 전면 패널 인터페이스와 연결된 활성 Supervisor UADP 2.0 포워딩 ASIC 통계를 확인합니다. 이 예에서는 Gig1/0/13 인터페이스가 사용됩니다.
출력 예:
- 라인 카드의 어떤 인터페이스가 동일한 포트 그룹에 속하는지 확인합니다.
- 각 포트 그룹은 라인 카드 stub ASIC에서 수퍼바이저 포워딩 ASIC로 8Gbps의 대역폭을 공유했습니다.
- 각 포트 그룹은 라인 카드 stub ASIC의 SLI(System Link Interface) 중 하나와 연결되어 수퍼바이저 포워딩 ASIC에 연결됩니다.
C9400#show platform hardware cman fp active data-path 1 13 detail ---> Slot 1, interface 13
showing cman data-path for frontpanel 1/0/13 fp_portmap.xml: ---> Supervisor ASIC 1, core 0 is associated with front panel (fp) interface Gig1/0/13 id 13 asic 1 core 0 port 12 mac 0 subport 4 contextid 0 maxspeed DEV_PORT_SPEED_1G gpn 113 active 1 data path: slot 3 +- ACTIVE_SUP --+ | Sif 0 | | IQS SQS | ---> Supervisor ASIC 1, core 0 on the slot 3 active Supervisor associated with interface Gig1/0/13 | PBC | | AQM | | EQC | | ESM | | RWE | | ASIC 1 | | Core 0 | | Asic Port 12 | | | | (Mac 0) | |Nif_Rx NifTx| +--------------+ ^ | | | | | | V ============================================== Nif MAC 0 Inforation: NifRxByteGroupStats: NifTxByteGroupStats: rxBytes 4495494 txBytes 6499427 NifRxByteDestinationGroupStats: NifTxByteDestinationGroupStats: rxUnicastBytes 1174628 txUnicastBytes 1175536 rxMulticastBytes 3320866 txMulticastBytes 5298482 rxBroadcastBytes 0 txBroadcastBytes 25409 NifRxPortStatusGroupStats: NifTxFrameDestinationGroupStats: rxUnicastFrames 18326 txUnicastFrames 18330 rxMulticastFrames 21387 txMulticastFrames 24834 rxBroadcastFrames 0 txBroadcastFrames 51 rxPauseFrames 0 txPauseFrames 0 rxCos0PauseFrames 0 txCos0PauseFrames 0 rxCos1PauseFrames 0 txCos1PauseFrames 0 rxCos2PauseFrames 0 txCos2PauseFrames 0 rxCos3PauseFrames 0 txCos3PauseFrames 0 rxCos4PauseFrames 0 txCos4PauseFrames 0 rxCos5PauseFrames 0 txCos5PauseFrames 0 rxCos6PauseFrames 0 txCos6PauseFrames 0 rxCos7PauseFrames 0 txCos7PauseFrames 0 rxOamProcessedFrames 0 txOamFrames 0 NifRxPortStatusGroupStats: NifTxPortStatusGroupStats: rxCollisionFragments 0 txLateCollisionFrames 0 rxFcsErrorFrames 0 txsystemFcsErrorFrames 0 rxInvalidOversizeFrames 0 txOversizeFrames 0 rxMacOverrunFrames 0 txMacUnderrunFrames 0 rxIpgViolationFrames 0 txDeferredFrames 0 rxOamDroppedFrames 0 txExcessiveDeferralFrames 0 rxSymbolErrorFrames 0 txOkMultipleCollisionFrames 0 rxValidOversizeFrames 0 txOkSingleCollisionFrames 0 rxValidUndersizeFrames 0 goldFramesTruncated 0 NifRxSizeGroupStats: NifTxSizeGroupStats: rx32768toMtuFrames 0 tx32768toMtuFrames 0 rx16384to32767ByteFrames 0 tx16384to32767ByteFrames 0 rx8192to16383ByteFrames 0 tx8192to16383ByteFrames 0 rx4096to8191ByteFrames 0 tx4096to8191ByteFrames 0 rx2048to4095ByteFrames 0 tx2048to4095ByteFrames 0 rx1519to2047ByteFrames 51 tx1519to2047ByteFrames 0 rx1024to1518ByteFrames 15 tx1024to1518ByteFrames 0 rx512to1023ByteFrames 17 tx512to1023ByteFrames 187 rx256to511ByteFrames 3406 tx256to511ByteFrames 9407 rx128to255ByteFrames 6567 tx128to255ByteFrames 6580 rx65to127ByteFrames 11295 tx65to127ByteFrames 8583 rx64ByteFrames 18362 tx64ByteFrames 18458 ============================================== ----------------------------------------------------> Input queue (Igr = Ingress) IgrPacketCounters: EgrPacketCounters: packetsIn 97777 packetsIn 580324 packetsOut 97777 packetsEnqueueFcd_val 0 packetsDropped 3383 packetsMarkedForDrop 278 fpsSourcedPadErrorCount 0 padErrorPacketsIn 0 igrSourcedPadErrorCount 0 padErrorPacketsOut 0 ============================================== For RWE for core 0: RweTotalEnqStats: packetCount 580324 RweTotalDeqStats: packetCount 580046 FragmentCount 580046 ============================================== For EQC for core 0: EqcTotalEnqStats: Count 580704 EqcTotalDeqStats: Count 580324 ============================================== For aqmRedQueueStats for asic port 12: AqmRedQueueStats: (sum of all queues) ---> Output queue (Aqm = Active queue management) acceptByteCnt0 0 acceptFrameCnt0 0 acceptByteCnt1 6407742 acceptFrameCnt1 43070 acceptByteCnt2 39609 acceptFrameCnt2 395 dropByteCnt0 0 dropFrameCnt0 0 dropByteCnt1 0 dropFrameCnt1 0 dropByteCnt2 0 dropFrameCnt2 0 outOfSoftBufDropByteCnt 0 outOfSoftBufDropFrameCnt 0 maxQebDropByteCnt 0 maxQebDropFrameCnt 0 ============================================== For PBC for core 0: PbcIngressErrorDropCount: PbcEgressErrorDropCount: iCount 0 eS0Count 0 iCount 0 eS1Count 0 PbcCreditCount: PbcEnqFcErrorDropCount: creditCount 64 fCount 0 rwePbcStall 0 ============================================== For local/core 0 Switching: SqsCumulativeStatistics totalEnqStat 1368200 totalDeqStat 1368200 totalDropStat 0 SqsCumulativeStatisticsB totalEnqStat 173449513 totalDeqStat 173449513 totalDropStat 0 ============================================== For local/core 1 Switching: SqsCumulativeStatistics totalEnqStat 890114 totalDeqStat 890114 totalDropStat 0 SqsCumulativeStatisticsB totalEnqStat 105061923 totalDeqStat 105061923 totalDropStat 0 ============================================== For Sif 0 Switching: SifSifPbcCnt0: Count 81302675 SifSifPbcCnt1: Count 58187651 SifRacInsertedCnt: SifRacCopiedCnt: SifRacInsertedCnt[0] 2295051 SifRacCopiedCnt[0] 35850468 SifRacInsertedCnt[1] 1738892 SifRacCopiedCnt[1] 19265491 SifRacInsertedCnt[2] 1666479 SifRacCopiedCnt[2] 23814855 SifRacInsertedCnt[3] 2773364 SifRacCopiedCnt[3] 32727259 SifRacInsertedCnt[4] 3126116 SifRacCopiedCnt[4] 38376676 SifRacInsertedCnt[5] 2066567 SifRacCopiedCnt[5] 22176467 ============================================== For Sif 1 Switching: SifSifPbcCnt0: Count 40956521 SifSifPbcCnt1: Count 40956521 SifRacInsertedCnt: SifRacCopiedCnt: SifRacInsertedCnt[0] 11713808 SifRacCopiedCnt[0] 8615615 SifRacInsertedCnt[1] 8319576 SifRacCopiedCnt[1] 7489596 SifRacInsertedCnt[2] 8816344 SifRacCopiedCnt[2] 7608895 SifRacInsertedCnt[3] 15404080 SifRacCopiedCnt[3] 8717898 SifRacInsertedCnt[4] 16161715 SifRacCopiedCnt[4] 9685735 SifRacInsertedCnt[5] 9745420 SifRacCopiedCnt[5] 7866174
전면 패널 인터페이스의 Supervisor(수퍼바이저) 관점에서 흐름 제어 상태를 확인합니다. 이렇게 하면 인터페이스에 혼잡이 있는지 확인할 수 있습니다.
C9400#show platform hardware cman fp active flowcontrol status
slot 1:Port 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 EsmF - - - - - - - - - - - - - - - - - - - - - - - - IqsC - - - - - - - - - - - - - - - - - - - - - - - - Port 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 EsmF - - - - - - - - - - - - - - - - - - - - - - - - IqsC - - - - - - - - - - - - - - - - - - - - - - - - slot 2: Port 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 EsmF - - - - - - - - - - - - - - - - - - - - - - - - IqsC - - - - - - - - - - - - - - - - - - - - - - - - Port 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 EsmF - - - - - - - - - - - - - - - - - - - - - - - - IqsC - - - - - - - - - - - - - - - - - - - - - - - - slot 3: Port 01 02 03 04 05 06 07 08 09 10 EsmF - - - - - - - - - - IqsC 01 - - - - - - - - - slot 4: Port 01 02 03 04 05 06 07 08 09 10 EsmF - - - - - - - - - - IqsC - - - - - - - - - - slot 5: Port 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 EsmF - - - - - - - - - - - - - - - - - - - - - - - - IqsC - - - - - - - - - - - - - - - - - - - - 01 - - - Port 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 EsmF - - - - - - - - - - - - - - - - - - - - - - - - IqsC - - - - - - - - - - - - - - - - - - - - - - - - slot 6: Possibly linecard is not inserted slot 7: Possibly linecard is not inserted
활성 수퍼바이저의 Supervisor 포워딩 ASIC와 OCI 인터페이스를 통해 라인 카드의 Line card stub ASIC 간에 Supervisor 포워딩 ASIC 관점에서 제어 트래픽이 이동하는지 확인합니다.
C9400#show platform hardware cman fp active oci status
processing oci information:
chassis_type: 1
sup slot: 4
sup num oci ports: 8
slot_id 1 : oci_enable Enabled Link Status 0 (UP)
asic_id 1 core_id 0 oci_port 3 mac_id 0
NruRxByteGroupStats: rxBytes 417829462717812 NruTxByteGroupStats: txBytes 588911286106332
slot_id 2 : oci_enable Enabled Link Status 0 (UP)
asic_id 0 core_id 0 oci_port 1 mac_id 1
NruRxByteGroupStats: rxBytes 417938235716344 NruTxByteGroupStats: txBytes 588917607864892
slot_id 5 : oci_enable Enabled Link Status 0 (UP)
asic_id 1 core_id 0 oci_port 4 mac_id 1
NruRxByteGroupStats: rxBytes 53195855717244 NruTxByteGroupStats: txBytes 588915422236932
slot_id 6 : oci_enable Enabled Link Status 1 (DOWN)
asic_id 2 core_id 0 oci_port 6 mac_id 0
NruRxByteGroupStats: rxBytes 0 NruTxByteGroupStats: txBytes 0
slot_id 7 : oci_enable Enabled Link Status 1 (DOWN)
asic_id 0 core_id 0 oci_port 2 mac_id 2
NruRxByteGroupStats: rxBytes 0 NruTxByteGroupStats: txBytes 0
라인 카드 통계 - 수퍼바이저-라인 카드 데이터 경로
특정 전면 패널 인터페이스와 연결된 라인 카드 stub ASIC 통계를 확인합니다. 이 예에서는 인터페이스 Gig1/0/13이 포커스입니다.
출력 예:
-
Gig 1/0/13에서 수신된 패킷에 네트워크 인터페이스 수신 포트를 입력하고 IQS를 통해 스택 인터페이스로 진행합니다.
-
여기에서 패킷은 스택 인터페이스를 통해 다른 Supervisor ASIC로 이동하거나 SQS, AQM, EQC, ESM, RWE를 통해 돌아와 Gig 1/0/13의 네트워크 인터페이스 전송을 시작합니다.
-
Gig 1/0/13에서 이그레스(egress)되는 다른 Supervisor ASIC 인터페이스에서 전송된 패킷은 Sif로 이동한 다음 SQS, AQM, EQC, ESM, RWE를 통과한 다음 Gig 1/0/13의 NifTx로 이동합니다.
-
AQM에는 8개의 Tx 대기열이 있습니다. 이러한 대기열에서 드롭이 표시되면 이 명령을 사용하여 어떤 대기열에서 드롭이 발생하는지 확인할 수 있습니다. show platform hardware fed active goes queue stats interface 1/0/13
C9400#show platform hardware iomd 1/0 data-path 13 detail ----> slot 1, interface 13 lcportmap.xml: ---> Line Card (lc) ASIC instance 0 is associated with interface Gig1/0/13 id 13 asic 0 asicport 12 mac 23 contextid 12 intl_port_sup0 9 intl_port_sup1 1 maxspeed DEV_PORT_SPEED_1G asic_subport 4 fp_portmap.xml: ---> Supervisor ASIC 1, core 0 is associated with front panel (fp) interface Gig1/0/13 id 13 asic 1 core 0 port 12 mac 0 subport 4 contextid 0 maxspeed DEV_PORT_SPEED_1G gpn 113 active 1 data path:
slot 3 +--ACTIVE SUP--+ | | ---> Supervisor ASIC 1, core 0 on the slot 3 active Supervisor associated with interface Gig1/0/13 | ASIC 1 | | Core 0 | | Asic Port 12 | | | | (Mac 0) | |Nif_Rx NifTx| +--------------+ | | | | SLI MAC 9 | | +---------------+ | SLI_Tx SLI_Rx| ---> Line Card 1. The statistic output below is only for this Line card ASIC | | | ASIC 0 | | Asic Port 12 | | | | (Mac 23) | | NIF_Rx NIF_Tx| +---------------+ Front Port 1/0/13 ^ | | | | | | V ============================================== Nif MAC 23 Inforation: NifRxByteGroupStats: NifTxByteGroupStats: rxBytes 4457854 txBytes 6440428 NifRxByteDestinationGroupStats: NifTxByteDestinationGroupStats: rxUnicastBytes 1163684 txUnicastBytes 1164528 rxMulticastBytes 3294170 txMulticastBytes 5250491 rxBroadcastBytes 0 txBroadcastBytes 25409 NifRxPortStatusGroupStats: NifTxFrameDestinationGroupStats: rxUnicastFrames 18155 txUnicastFrames 18158 rxMulticastFrames 21235 txMulticastFrames 24625 rxBroadcastFrames 0 txBroadcastFrames 51 rxPauseFrames 0 txPauseFrames 0 rxCos0PauseFrames 0 txCos0PauseFrames 0 rxCos1PauseFrames 0 txCos1PauseFrames 0 rxCos2PauseFrames 0 txCos2PauseFrames 0 rxCos3PauseFrames 0 txCos3PauseFrames 0 rxCos4PauseFrames 0 txCos4PauseFrames 0 rxCos5PauseFrames 0 txCos5PauseFrames 0 rxCos6PauseFrames 0 txCos6PauseFrames 0 rxCos7PauseFrames 0 txCos7PauseFrames 0 rxOamProcessedFrames 0 txOamFrames 0 NifRxPortStatusGroupStats: NifTxPortStatusGroupStats: rxCollisionFragments 0 txLateCollisionFrames 0 rxFcsErrorFrames 0 txsystemFcsErrorFrames 0 rxInvalidOversizeFrames 0 txOversizeFrames 0 rxMacOverrunFrames 0 txMacUnderrunFrames 0 rxIpgViolationFrames 0 txDeferredFrames 0 rxOamDroppedFrames 0 txExcessiveDeferralFrames 0 rxSymbolErrorFrames 0 txOkMultipleCollisionFrames 0 rxValidOversizeFrames 0 txOkSingleCollisionFrames 0 rxValidUndersizeFrames 0 goldFramesTruncated 0 NifRxSizeGroupStats: NifTxSizeGroupStats: rx32768toMtuFrames 0 tx32768toMtuFrames 0 rx16384to32767ByteFrames 0 tx16384to32767ByteFrames 0 rx8192to16383ByteFrames 0 tx8192to16383ByteFrames 0 rx4096to8191ByteFrames 0 tx4096to8191ByteFrames 0 rx2048to4095ByteFrames 0 tx2048to4095ByteFrames 0 rx1519to2047ByteFrames 51 tx1519to2047ByteFrames 0 rx1024to1518ByteFrames 15 tx1024to1518ByteFrames 0 rx512to1023ByteFrames 17 tx512to1023ByteFrames 186 rx256to511ByteFrames 3374 tx256to511ByteFrames 9318 rx128to255ByteFrames 6505 tx128to255ByteFrames 6518 rx65to127ByteFrames 11237 tx65to127ByteFrames 8526 rx64ByteFrames 18191 tx64ByteFrames 18286 ============================================== ----------------------------------------------------> Input queue (Igr = Ingress) IgrPacketCounters: EgrPacketCounters: packetsIn 97078 packetsIn 576307 packetsOut 97078 packetsEnqueueFcd_val 0 packetsDropped 0 packetsMarkedForDrop 0 fpsSourcedPadErrorCount 0 padErrorPacketsIn 0 igrSourcedPadErrorCount 0 padErrorPacketsOut 0 ============================================== For aqmRedQueueStats for asic port 12: AqmRedQueueStats: (sum of all queues) ---> Output queue (Agm = Active queue management) acceptByteCnt0 0 acceptFrameCnt0 0 acceptByteCnt1 0 acceptFrameCnt1 0 acceptByteCnt2 6440428 acceptFrameCnt2 42834 dropByteCnt0 0 dropFrameCnt0 0 dropByteCnt1 0 dropFrameCnt1 0 dropByteCnt2 0 dropFrameCnt2 0 outOfSoftBufDropByteCnt 0 outOfSoftBufDropFrameCnt 0 maxQebDropByteCnt 0 maxQebDropFrameCnt 0 ============================================== SLI MAC 9 - SUP 0: ( an ACTIVE sup in slot 3 ) SliTxByteGroupStats: SliRxByteGroupStats: txBytes 4457854 rxBytes 6440428 SLI MAC 1 - SUP 1: SliTxByteGroupStats: SliRxByteGroupStats: txBytes 0 rxBytes 0
전면 패널 인터페이스의 라인 카드 관점에서 흐름 제어 상태를 확인합니다. 이렇게 하면 인터페이스의 혼잡을 식별할 수 있습니다.
- 흐름 제어가 없으면 값이 "-"입니다. 그렇지 않으면 흐름 제어(혼잡)를 경험하는 대기열 번호가 표시됩니다.
- 인터페이스에 의해 수신된 흐름 제어는 라인 카드의 라인 카드 ASIC에서 수퍼바이저 ASIC의 수퍼바이저 ASIC로 전달되며, 수퍼바이저 ASIC에서는 AQM이 삭제됩니다. OCI(Out-of-band Control Interface)는 라인 카드와 활성 수퍼바이저 간의 내부 통신 채널로서 라인 카드에서 수퍼바이저로의 흐름 제어를 알리는 데 사용됩니다.
C9400#show platform hardware iomd 1/0 flowcontrol status ---> slot 1
Slot 1 - number of ports 48
slot 1: Port 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
IsmF - - - - - - - - - - - - - - - - - - - - - - - -
IqmC - - - - - - - - - - - - - - - - - - - - - - - -
Port 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48
IsmF - - - - - - - - - - - - - - - - - - - - - - - -
IqmC - - - - - - - - - - - - - - - - - - - - - - - -
라인 카드의 라인 카드 stub ASIC과 OCI 인터페이스를 통해 활성 및 대기 수퍼바이저의 수퍼바이저 포워딩 ASIC 간에 라인 카드 stub ASIC 관점에서 제어 트래픽이 이동하는지 확인합니다.
- OCI = 대역 외 제어 인터페이스 = 라인 카드와 액티브 및 스탠바이 수퍼바이저 간의 내부 통신 채널
C9400#show platform hardware iomd 1/0 oci status ---> slot 1 Asic 0, Mac 10, Tx OCI Config 0, OCI Merge FALSE, OCI Enabled, Link Status 0 (UP) Network Port Range 0---47, Local Port Range 0---47 NifRxByteGroupStats: rxBytes 177402572782108 NifTxByteGroupStats: txBytes 141925777717156 Asic 0, Mac 11, Tx OCI Config 0, OCI Merge FALSE, OCI Enabled, Link Status 0 (UP) Network Port Range 0---47, Local Port Range 0---47 NifRxByteGroupStats: rxBytes 963489284 NifTxByteGroupStats: txBytes 770809988
라인 카드의 어떤 인터페이스가 활성 수퍼바이저의 수퍼바이저 포워딩 ASIC를 향해 라인 카드의 라인 카드 stub ASIC에서 8Gbps의 대역폭을 공유하는 동일한 포트 그룹의 일부인지 확인합니다. 각 포트 그룹은 Line Card stub ASIC의 SLI(System Link Interface) 중 하나와 Supervisor에 연결됩니다.
C9400#show platform hardware iomd 1/0 portgroups ---> slot 1
Port Interface Status Interface Group Max <-- aggregate bandwidth for 8 ports
Group Bandwith Bandwidth 1 TenGigabitEthernet1/0/1 up 1G 1 TenGigabitEthernet1/0/2 down 1G 1 TenGigabitEthernet1/0/3 admindown 1G 1 TenGigabitEthernet1/0/4 down 1G 1 TenGigabitEthernet1/0/5 down 1G 8G 1 TenGigabitEthernet1/0/6 down 1G 1 TenGigabitEthernet1/0/7 down 1G 1 TenGigabitEthernet1/0/8 down 1G 2 TenGigabitEthernet1/0/9 down 1G 2 TenGigabitEthernet1/0/10 down 1G 2 TenGigabitEthernet1/0/11 down 1G 2 TenGigabitEthernet1/0/12 down 1G 2 TenGigabitEthernet1/0/13 up 1G 8G 2 TenGigabitEthernet1/0/14 down 1G 2 TenGigabitEthernet1/0/15 down 1G 2 TenGigabitEthernet1/0/16 down 1G 3 TenGigabitEthernet1/0/17 down 1G 3 TenGigabitEthernet1/0/18 down 1G 3 TenGigabitEthernet1/0/19 down 1G 3 TenGigabitEthernet1/0/20 down 1G 3 TenGigabitEthernet1/0/21 down 1G 8G 3 TenGigabitEthernet1/0/22 down 1G 3 TenGigabitEthernet1/0/23 down 1G 3 TenGigabitEthernet1/0/24 down 1G 4 TenGigabitEthernet1/0/25 down 1G 4 TenGigabitEthernet1/0/26 down 1G 4 TenGigabitEthernet1/0/27 down 1G 4 TenGigabitEthernet1/0/28 down 1G 4 TenGigabitEthernet1/0/29 down 1G 8G 4 TenGigabitEthernet1/0/30 down 1G 4 TenGigabitEthernet1/0/31 down 1G 4 TenGigabitEthernet1/0/32 down 1G 5 TenGigabitEthernet1/0/33 down 1G 5 TenGigabitEthernet1/0/34 down 1G 5 TenGigabitEthernet1/0/35 down 1G 5 TenGigabitEthernet1/0/36 down 1G 5 TenGigabitEthernet1/0/37 down 1G 8G 5 TenGigabitEthernet1/0/38 down 1G 5 TenGigabitEthernet1/0/39 down 1G 5 TenGigabitEthernet1/0/40 down 1G 6 TenGigabitEthernet1/0/41 down 1G 6 TenGigabitEthernet1/0/42 down 1G 6 TenGigabitEthernet1/0/43 down 1G 6 TenGigabitEthernet1/0/44 down 1G 6 TenGigabitEthernet1/0/45 down 1G 8G 6 TenGigabitEthernet1/0/46 down 1G 6 TenGigabitEthernet1/0/47 down 1G 6 TenGigabitEthernet1/0/48 up 1G
개정 이력
| 개정 | 게시 날짜 | 의견 |
|---|---|---|
1.0 |
23-Jun-2022 |
최초 릴리스 |
 피드백
피드백