PPFA(Password Protected File Analysis) 소개
편견 없는 언어
본 제품에 대한 문서 세트는 편견 없는 언어를 사용하기 위해 노력합니다. 본 설명서 세트의 목적상, 편견 없는 언어는 나이, 장애, 성별, 인종 정체성, 민족 정체성, 성적 지향성, 사회 경제적 지위 및 교차성에 기초한 차별을 의미하지 않는 언어로 정의됩니다. 제품 소프트웨어의 사용자 인터페이스에서 하드코딩된 언어, RFP 설명서에 기초한 언어 또는 참조된 서드파티 제품에서 사용하는 언어로 인해 설명서에 예외가 있을 수 있습니다. 시스코에서 어떤 방식으로 포용적인 언어를 사용하고 있는지 자세히 알아보세요.
이 번역에 관하여
Cisco는 전 세계 사용자에게 다양한 언어로 지원 콘텐츠를 제공하기 위해 기계 번역 기술과 수작업 번역을 병행하여 이 문서를 번역했습니다. 아무리 품질이 높은 기계 번역이라도 전문 번역가의 번역 결과물만큼 정확하지는 않습니다. Cisco Systems, Inc.는 이 같은 번역에 대해 어떠한 책임도 지지 않으며 항상 원본 영문 문서(링크 제공됨)를 참조할 것을 권장합니다.
소개
이 문서에서는 ESA(Email Security Appliance) 버전 14.X에 추가된 새로운 PPFA(Password Protected File Analysis)에 대해 설명합니다.
사전 요구 사항
요구 사항
Cisco에서는 ESA 개념 및 컨피그레이션에 대해 알고 있는 것이 좋습니다.
사용되는 구성 요소
이 문서의 정보는 AsyncOS for ESA 14.0 이상을 기반으로 합니다.
이 문서의 정보는 특정 랩 환경의 디바이스를 토대로 작성되었습니다. 이 문서에 사용된 모든 디바이스는 초기화된(기본) 컨피그레이션으로 시작되었습니다. 현재 네트워크가 작동 중인 경우 모든 명령의 잠재적인 영향을 미리 숙지하시기 바랍니다.
배경 정보
기존에는 비밀번호가 알려지지 않아 비밀번호로 보호된 문서나 PDF, Doc, ZIP 등 아카이브 첨부 파일의 내용을 분석할 수 없었다.
PPFA가 도입되면서 암호로 보호된 첨부 파일이 포함된 이메일은 메일 본문에 암호가 있으면 악의적인 활동과 데이터 프라이버시를 분석할 수 있게 되었습니다.
지원되는 형식 및 언어
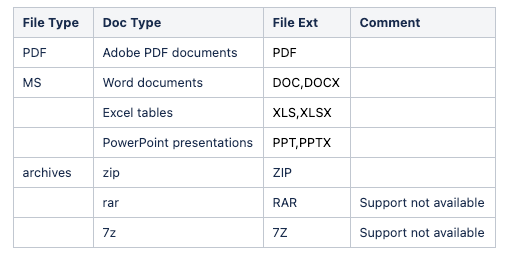
지원되는 형식 목록은 다음과 같습니다.
- MS Office 파일
doc/x 2007-2019 / doc 2002 ~ 2004
xls/x 2007-2019
ppt/x 2007-2019
- 보관
zip, rar, 7z
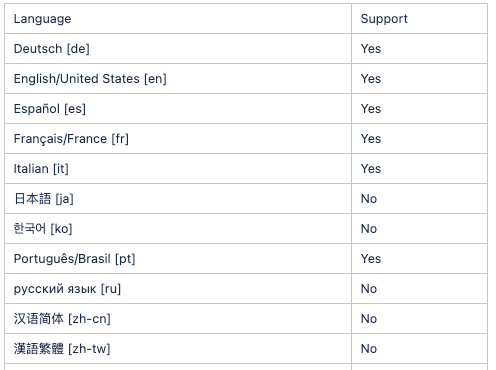
여기에서 지원되는 언어 목록을 찾을 수 있습니다.
고려 사항
PPFA는 기본적으로 비활성화되어 있습니다.
암호로 보호된 첨부 파일은 현재 메일 본문에 암호가 있는 경우에만 분석할 수 있습니다. 비밀번호는 대/소문자를 구분하며 "공백"을 인식하지 않습니다.
이제 관리자가 제공한 최대 5개의 비밀번호 목록이 지원됩니다.
컨피그레이션 단계
그래픽 사용자 인터페이스(GUI)
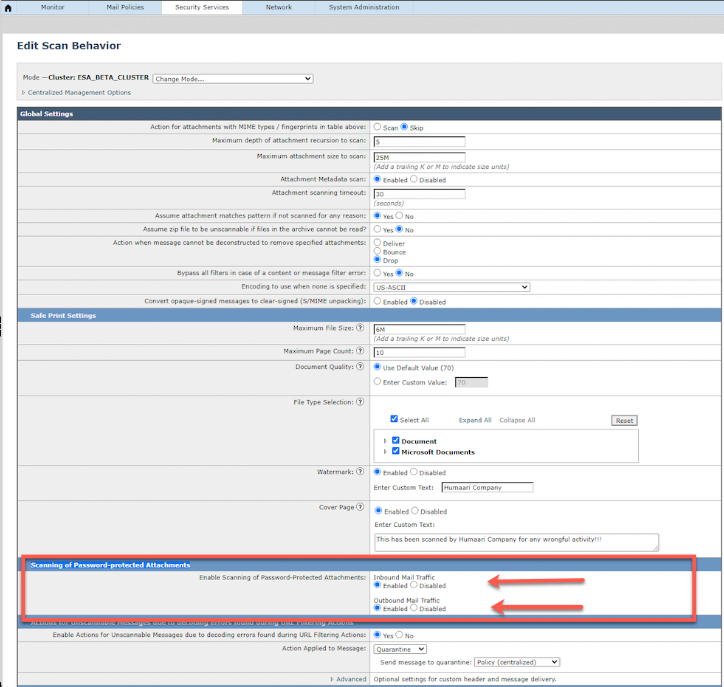
GUI에서 PPFA를 구성하려면 Security Service(보안 서비스) > Scan Behavior(검사 동작) > Edit Global Settings(전역 설정 수정) > Scanning of Password-protected Attachments(암호로 보호된 첨부 파일 검사)로 이동합니다. > Enable for Inbound Mail traffic/Outbound Mail Traffic or Both(인바운드 메일 트래픽/아웃바운드 메일 트래픽에 대해 활성화) >Submit(제출) > Commit(커밋)로 이동합니다.
CLI(Command Line Interface)
CLI에서 PPFA를 구성하려면 scanconfig > PROTECTEDATATACMENTCONFIG > Commit 명령을 실행합니다
(ESA_CLI) (SERVICE)> scanconfig
NOTICE: This configuration command has not yet been configured for the current cluster mode (Machine esa1.lab.cisco.com).
What would you like to do?
1. Switch modes to edit at mode "Cluster ESA_BETA_CLUSTER".
2. Start a new, empty configuration at the current mode (Machine esa1.lab.cisco.com).
3. Copy settings from another cluster mode to the current mode (Machine esa1.lab.cisco.com).
[1]>
There are currently 5 attachment type mappings configured to be SKIPPED.
Choose the operation you want to perform:
- NEW - Add a new entry.
- DELETE - Remove an entry.
- SETUP - Configure scanning behavior.
- IMPORT - Load mappings from a file.
- EXPORT - Save mappings to a file.
- PRINT - Display the list.
- CLEAR - Remove all entries.
- SMIME - Configure S/MIME unpacking.
- SAFEPRINT - Configure safeprint settings.
- PROTECTEDATTACHMENTCONFIG - Scan password protected attachments.
- CLUSTERSET - Set how scanconfig is configured in a cluster.
- CLUSTERSHOW - Display how scanconfig is configured in a cluster.
[]> PROTECTEDATTACHMENTCONFIG
Scanning of password-protected attachments for inbound mails: enabled.
Scanning of password-protected attachments for outbound mails: enabled.
Do you want to scan password-protected attachments for inbound mails? y/n [Y]>
Do you want to scan password-protected attachments for outbound mails? y/n [Y]>
Scan password protected attachments configuration unchanged.
참고: 기본적으로 이메일 본문의 비밀번호 5개는 스캔/추출됩니다.
전자 메일 본문에서 추출된 최대 비밀번호 수를 늘리기 위해 CLI에서 숨겨진 명령 "scanconfig > password_list_size"를 사용할 수 있습니다. 최대 10개의 비밀번호를 구성할 수 있습니다.

주의: 이 설정을 더 높은 값으로 변경하면 성능에 영향을 미칠 수 있습니다.
(ESA_CLI) (SERVICE)> scanconfig
There are currently 5 attachment type mappings configured to be SKIPPED.
Choose the operation you want to perform:
- NEW - Add a new entry.
- DELETE - Remove an entry.
- SETUP - Configure scanning behavior.
- IMPORT - Load mappings from a file.
- EXPORT - Save mappings to a file.
- PRINT - Display the list.
- CLEAR - Remove all entries.
- SMIME - Configure S/MIME unpacking.
- SAFEPRINT - Configure safeprint settings.
- PROTECTEDATTACHMENTCONFIG - Scan password protected attachments.
- CLUSTERSET - Set how scanconfig is configured in a cluster.
- CLUSTERSHOW - Display how scanconfig is configured in a cluster.
[]> password_list_size
Enter maximum number of passwords to process:
[5]> 1000
Value must be an integer from 1 to 10.
Enter maximum number of passwords to process:
[5]> 10
Password list size is changed.문제 해결 및 확인
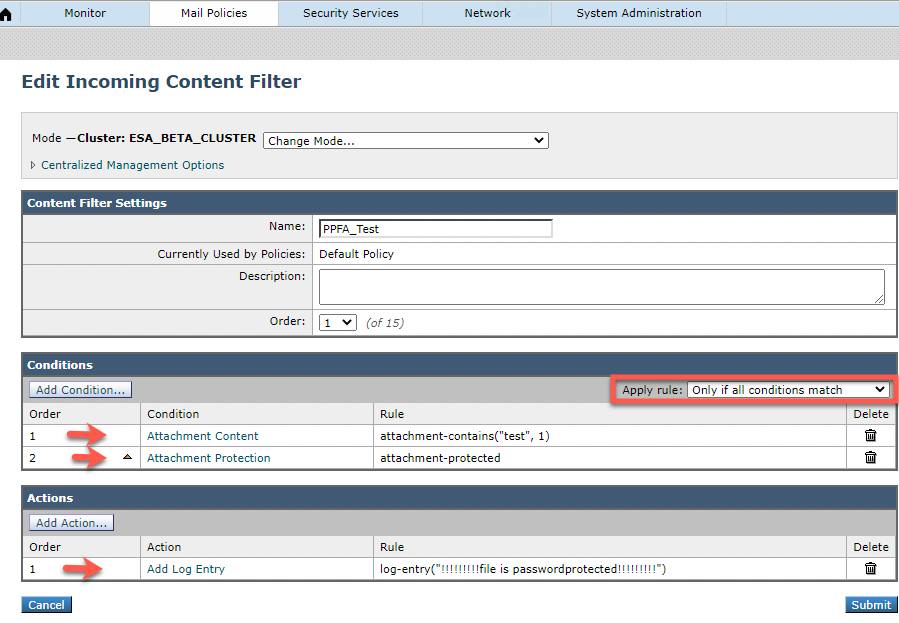
이 예에서는 조건이 있는 콘텐츠 필터를 사용합니다.
- 첨부 파일 콘텐츠에 "test" 및
- 첨부 파일이 비밀번호로 보호된 경우
그러면 작업은 "!!!!!file is passwordprotected!!!!!!!" 로그입니다.
성공적인 프로세스를 위해 CLI에서 확인
a) mail_logs의 CLI에서 다음 사항을 볼 수 있습니다.
Wed Feb 24 12:11:59 2022 Info: Start MID 22178287 ICID 122555
Wed Feb 24 12:11:59 2022 Info: MID 22178287 ICID 122555 From:
Wed Feb 24 12:11:59 2022 Info: MID 22178287 ICID 122555 RID 0 To:
Wed Feb 24 12:11:59 2022 Info: MID 22178287 using engine: SPF Verdict Cache using cached verdict Wed Feb 24 12:11:59 2022 Info: MID 22178287 SPF: helo identity postmaster@[10.0.201.16] None Wed Feb 24 12:11:59 2022 Info: MID 22178287 using engine: SPF Verdict Cache using cached verdict Wed Feb 24 12:11:59 2022 Info: MID 22178287 SPF: mailfrom identity test@lab.cisco.com Pass (v=spf1) Wed Feb 24 12:11:59 2022 Info: MID 22178287 using engine: SPF Verdict Cache using cached verdict Wed Feb 24 12:11:59 2022 Info: MID 22178287 SPF: pra identity test@lab.cisco.com None headers from Wed Feb 24 12:11:59 2022 Info: MID 22178287 DMARC: Message from domain lab.cisco.com, DMARC pass (SPF aligned True, DKIM aligned False) Wed Feb 24 12:11:59 2022 Info: MID 22178287 DMARC: Verification passed Wed Feb 24 12:11:59 2022 Info: MID 22178287 Message-ID '<4be194cc-4c95-9d15-6528-81a05dc56a66@lab.cisco.com>' Wed Feb 24 12:11:59 2022 Info: MID 22178287 Subject ppfa test with xls Wed Feb 24 12:11:59 2022 Info: MID 22178287 SDR: Domains for which SDR is requested: reverse DNS host: Not Present, helo: [10.0.201.16], env-from: lab.cisco, header-from: lab.cisco.com, reply-to: Not Present Wed Feb 24 12:11:59 2022 Info: MID 22178287 SDR: Consolidated Sender Reputation: Tainted, Threat Category: N/A, Suspected Domain(s) : test@lab.cisco.com. Youngest Domain Age: 4 months 14 days for domain: test@lab.cisco.com Wed Feb 24 12:11:59 2022 Info: MID 22178287 SDR: Tracker Header : 1+lIjVgkzfH9oTTP+SaBrzZC3Gs6TTYhJbW8D/pjF0eP1U48Yn65OgvVF9VjL6RgIIYi/H6sTg4VSq/leHowYXwYz/1wmYQCDwFFhTTfkLqs/GuqB1ynXwqZRXi2TiSkkHHrJbo+6IUpze9pVWWlgvZomvY7LindREsvoMzHCYesMkNci5Ko0u0m9D1Fz5SoCuVsofk0dbf9rjydhcP4aGxNOTd99njpfkGqdTbZIBv1mBsIS5fRYaDSEEntbcJkuVq3V5ShYK2HZPfKAbzllBxstwYWM0kRe8uIFfiGuCFqDtPaQ1Fb2avNo1MKwLKL Wed Feb 24 12:11:59 2022 Info: MID 22178287 ready 22082 bytes from
Wed Feb 24 12:11:59 2022 Info: LDAP: Masquerade query LDAP.masquerade MID 22178287 address test@lab.cisco.com to test@lab.cisco.com Wed Feb 24 12:11:59 2022 Info: LDAP: Masquerade query LDAP.masquerade MID 22178287 address test@lab.cisco.com to test@lab.cisco.com Wed Feb 24 12:11:59 2022 Info: MID 22178287 attachment 'testfile.xlsx' Wed Feb 24 12:12:01 2022 Info: MID 22178287 matched all recipients for per-recipient policy test1 in the inbound table Wed Feb 24 12:12:04 2022 Info: MID 22178287 interim verdict using engine: CASE spam negative Wed Feb 24 12:12:04 2022 Info: MID 22178287 using engine: CASE spam negative Wed Feb 24 12:12:04 2022 Info: MID 22178287 interim AV verdict using McAfee ENCRYPTED Wed Feb 24 12:12:04 2022 Info: MID 22178287 interim AV verdict using Sophos ENCRYPTED Wed Feb 24 12:12:04 2022 Info: MID 22178287 antivirus encrypted Wed Feb 24 12:12:04 2022 Info: MID 22178287 AMP file reputation verdict : UNKNOWN(File analysis pending) Wed Feb 24 12:12:04 2022 Info: MID 22178287 SHA d1e67e9640c598162b891028d967d2e5621d0c1bc1141ef2cec21a0ee1087349 filename testfile.xlsx queued for possible file analysis upload Wed Feb 24 12:12:04 2022 Info: MID 22178287 using engine: GRAYMAIL negative Wed Feb 24 12:12:04 2022 Info: MID 22178287 Custom Log Entry: !!!!!!!!!file is passwordprotected!!!!!!!!! Wed Feb 24 12:12:04 2022 Info: MID 22178287 Unable to safe print the attachment, Filename: testfile.xlsx, Reason: The attachment is encrypted, Action: The attachment is stripped Wed Feb 24 12:12:04 2022 Info: MID 22178287 rewritten to MID 22178289 by safeprint-all-attachments-strip-unscan filter 'PDF-Safeprint' Wed Feb 24 12:12:04 2022 Info: Message finished MID 22178287 done
b) content_scanner 로그에서 파일의 압축이 성공적으로 풀렸는지 확인할 수 있습니다.
Wed Feb 24 12:12:01 2022 Info: PF: MID 22178287 The password-protected file - "testfile.xlsx" is scanned successfully.c) amp_logs에서 추출된 파일이 분석을 위해 AMP(Advanced Malware Protection) 및 File Analysis(파일 분석)로 전송되는 것을 확인할 수 있습니다.
Tue Mar 16 11:21:03 2022 Info: File reputation query initiating. File Name = 'testfile.zip', MID = 22194509, File Size = 706376 bytes, File Type = application/zip
Tue Mar 16 11:21:03 2022 Info: Response received for file reputation query from Cloud. File Name = 'testfile.zip', MID = 22194509, Disposition = FILE UNKNOWN, Malware = None, Analysis Score = 0, sha256 = fb997bf3891f81edc3a4292c22d9fa7fbfc652756eec5e9b7ffd431581694f5b, upload_action = Reco
mmended to send the file for analysis, verdict_source = None
Tue Mar 16 11:21:03 2022 Info: Compressed/Archive File: sha256 = fb997bf3891f81edc3a4292c22d9fa7fbfc652756eec5e9b7ffd431581694f5b MID = 22194509, Extracted File: File Name = 'testfile.exe', File Type = 'application/x-dosexec', sha256 = f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb
962427f8aa, Disposition = FILE UNKNOWN, Response received from = Cloud, Malware = None, Analysis Score = 0, upload_action = Recommended to send the file for analysis
Tue Mar 16 11:21:04 2022 Info: File uploaded for preclassification. SHA256: f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa, file name: testfile.exe
Tue Mar 16 11:21:31 2022 Info: File uploaded for analysis. SHA256: f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa, file name: testfile.exed) amp_logs가 Debug 레벨에 있는 경우 비밀번호로 보호된 파일과 관련된 추가 정보를 볼 수 있습니다.
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_supported_file_mime: Supported mime : application/zip
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: _amp_unarchv_mem2file - in_buf=0x96682000, size=706376, ctext=0x0, parent=0x0
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: password is Cisco
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_context_create - ctext=0x96610ec0
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: archive size = 706376, max archive size=14127520
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: password is Cisco
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_context_create - ctext=0x96610ec0
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: archive size = 706376, max archive size=14127520
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_make_dated_dir - path=/data/tmp/amp/2022_03_16
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: update_full_pathname entered - path=/data/tmp/amp/2022_03_16, filename=testfile.exe, suffix=#amp_1_1615911663
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: update_full_pathname - archive_entry_set_pathname, /data/tmp/amp/2022_03_16/testfile.exe#amp_1_1615911663
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_queue_entry_insert - ctext=0x96610ec0, parent=0x0, pathname=/data/tmp/amp/2022_03_16/testfile.exe#amp_1_1615911663
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: _amp_unarchv_file2file - ctext=0x96610ec0, parent_qe=0x9666a2e0, filename=/data/tmp/amp/2022_03_16/testfile.exe#amp_1_1615911663
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: Unsupported file type: application/x-dosexec
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: _amp_unarchv_mem2file - in_buf=0x97284000, size=1096080, ctext=0x96610ec0, parent=0x9666a2e0
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: _amp_unarchv_mem2file - decode depth (0)
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: _amp_unarchv_file2file - archive cumulative size=1096080 no.of files=1
Tue Mar 16 11:21:03 2022 AMPPyrex:- AMP-INFO: set_analysis_params do_sandbox=0, do_analysis=0,file_mime=application/zip, file priortiy=0 preclass_type=2
Tue Mar 16 11:21:03 2022 AMPPyrex:- AMP-INFO: set_analysis_params do_sandbox=1, do_analysis=1,file_mime=application/x-dosexec, file priortiy=0 preclass_type=4
Tue Mar 16 11:21:03 2022 AMPCloudIF:- AMP-DEBUG: AMP Query Request, FileType[0] SHA256[fb997bf3891f81edc3a4292c22d9fa7fbfc652756eec5e9b7ffd431581694f5b]
......
ue Mar 16 11:21:03 2022 CloudPool:- AMP-DEBUG: cb in callback_thread
Tue Mar 16 11:21:03 2022 AMPCloudIF:- AMP-DEBUG: AMP Query Response[Cloud], SHA256[fb997bf3891f81edc3a4292c22d9fa7fbfc652756eec5e9b7ffd431581694f5b], disposition[1] score[0] score_tg[0] score_type[0] SpyName[] action[1]
Tue Mar 16 11:21:03 2022 CacheUtils:- AMP-DEBUG: Found SHA256: - SHA256::fb997bf3891f81edc3a4292c22d9fa7fbfc652756eec5e9b7ffd431581694f5b
Tue Mar 16 11:21:03 2022 CloudPool:- AMP-DEBUG: imcloud callback thread going to sleep
Tue Mar 16 11:21:03 2022 VRTCloudIF:- AMP-DEBUG: Status List, Server Response HTTP code:[200]
Tue Mar 16 11:21:03 2022 CacheUtils:- AMP-DEBUG: Found SHA256: - SHA256::f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa
Tue Mar 16 11:21:03 2022 VRTCloudIF:- AMP-DEBUG: File SHA256[f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa] pri - [0] is enqueued to vrt
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_entry_preserve_file - ctext=0x96610ec0, pathname=/data/tmp/amp/2022_03_16/testfile.exe#amp_1_1615911663
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_entry_preserve_file - preserved pathname=/data/tmp/amp/2022_03_16/testfile.exe#amp_1_1615911663
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_context_delete - ctext=0x96610ec0
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_queue_entry_free - entry=0x9666a2e0, pathname=/data/tmp/amp/2022_03_16/testfile.exe#amp_1_1615911663 file_mime =application/x-dosexec, preserved=1
Tue Mar 16 11:21:03 2022 Unarchive:- AMP-DEBUG: amp_context_free - ctext=0x96610ec0
Tue Mar 16 11:21:03 2022 AMPRPC:- AMP-INFO: Adjusted verdict - {'file_type': 'application/zip', 'file_name': 'testfile.zip', 'verdict_source': None, 'spyname': '', 'custom_threshold': None, 'unscan_category': None, 'category': 'amp', 'original_verdict': 'FILE UNKNOWN', 'analysis_statu
s': 1, 'analysis_score': 0, 'score': 0, 'sha256': 'fb997bf3891f81edc3a4292c22d9fa7fbfc652756eec5e9b7ffd431581694f5b', 'verdict_str': 'FILE UNKNOWN', 'uploaded': False, 'verdict_from': 'Cloud', 'xid': 22194509, 'verdict_num': 1, 'blacklisted': False, 'extract_file_verdict_list': deque([{'c
ategory': 'amp', 'uploaded': True, 'original_verdict': 'FILE UNKNOWN', 'analysis_status': 4, 'verdict_num': 1, 'analysis_score': 0, 'file_type': 'application/x-dosexec', 'file_name': 'testfile.exe', 'verdict_source': None, 'verdict_from': 'Cloud', 'spyname': '', 'score': 0, 'unscan_category'
: None, 'upload_reason': None, 'sha256': 'f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa', 'verdict_str': 'FILE UNKNOWN', 'analysis_action': 1, 'blacklisted': False}]), 'analysis_action': 1, 'verdict': 'FILE UNKNOWN', 'error': None}
Tue Mar 16 11:21:03 2022 VRTCloudIF:- AMP-DEBUG: Set curl options URL[https://tg1-clean.lab.cisco.com/csa/v3/run/file?apikey=qg8ecq3n5c9ld4inbps783g263&async=true&classify=true], Trust Store[/data/fire_amp/db/preserve/private_cert.pem]
Tue Mar 16 11:21:03 2022 VRTCloudIF:- AMP-DEBUG: {"message":"Success","hash":"f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa","base_url":"https://tg1-clean.lab.cisco.com","entitlement_buffer_info":{"used":0,"available":true,"available_on":"2022-03-16T16:21:03Z"},"anal
yzing":"unknown","sample":"d5c8d83543d92c0cc428d6377d1c665d","query":"https://tg1-clean.lab.cisco.com/csa/v3/report?sample=d5c8d83543d92c0cc428d6377d1c665d"}
Tue Mar 16 11:21:03 2022 VRTCloudIF:- AMP-DEBUG: File upload successful filename testfile.exe
Tue Mar 16 11:21:03 2022 CacheUtils:- AMP-DEBUG: Found SHA256: - SHA256::f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa
Tue Mar 16 11:21:03 2022 VRTCloudIF:- AMP-DEBUG: File SHA256[f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa], file mime[application/x-dosexec], upload priority[High] successfully uploaded to the VRT server.
Tue Mar 16 11:21:03 2022 AMPPyrex:- AMP-INFO: Upload SHA[f2d2638afb528c7476c9ee8e83ddb20e686b0b05f53f2f966fd9eb962427f8aa] runid=0 sampleid = timestamp=1615911663
Tue Mar 16 11:21:17 2022 AMPPyrex:- AMP-DEBUG: AMP Extraction monitoring thread entering into sleep. Thread pool length=19 free pool size=1
성공적인 프로세스를 위해 GUI에서 확인
Message Tracking(메시지 추적)으로 이동하고 메시지 ID를 필터링합니다.
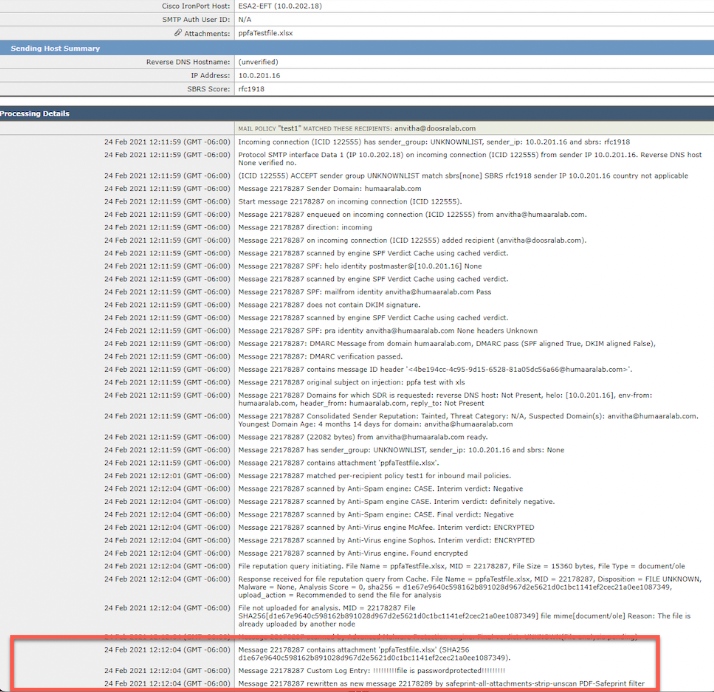
CLI에서 실패한 프로세스에 대한 확인
조건: 잘못된 암호 또는 암호를 찾을 수 없습니다.
a) CLI의 mail_logs에서
Wed Feb 24 12:24:40 2022 Info: MID 22178297 ICID 122563 From:
Wed Feb 24 12:24:40 2022 Info: MID 22178297 ICID 122563 RID 0 To:
Wed Feb 24 12:24:40 2022 Info: MID 22178297 using engine: SPF Verdict Cache using cached verdict Wed Feb 24 12:24:40 2022 Info: SPF Verdict Cache cache status: hits = 10, misses = 531, expires = 318, adds = 531, seconds saved = 0.04, total seconds = 9.69 Wed Feb 24 12:24:40 2022 Info: MID 22178297 SPF: helo identity postmaster@[10.0.201.16] None Wed Feb 24 12:24:40 2022 Info: MID 22178297 using engine: SPF Verdict Cache using cached verdict Wed Feb 24 12:24:40 2022 Info: MID 22178297 SPF: mailfrom identity test@lab.cisco.com Pass (v=spf1) Wed Feb 24 12:24:40 2022 Info: MID 22178297 using engine: SPF Verdict Cache using cached verdict Wed Feb 24 12:24:40 2022 Info: MID 22178297 SPF: pra identity test@lab.cisco.com None headers from Wed Feb 24 12:24:40 2022 Info: MID 22178297 DMARC: Message from domain lab.cisco.com, DMARC pass (SPF aligned True, DKIM aligned False) Wed Feb 24 12:24:40 2022 Info: MID 22178297 DMARC: Verification passed Wed Feb 24 12:24:40 2022 Info: MID 22178297 Message-ID '<825ab100-3066-e35e-148e-9ea08cb2fb28@lab.cisco.com>' Wed Feb 24 12:24:40 2022 Info: MID 22178297 Subject ppfa test without password Wed Feb 24 12:24:40 2022 Info: MID 22178297 SDR: Domains for which SDR is requested: reverse DNS host: Not Present, helo: [10.0.201.16], env-from: lab.cisco.com, header-from: lab.cisco.com, reply-to: Not Present Wed Feb 24 12:24:40 2022 Info: MID 22178297 SDR: Consolidated Sender Reputation: Tainted, Threat Category: N/A, Suspected Domain(s) : test@lab.cisco.com. Youngest Domain Age: 4 months 14 days for domain: test@lab.cisco.com Wed Feb 24 12:24:40 2022 Info: MID 22178297 SDR: Tracker Header : jiOYjEFgtyhTbL9t0GE5obyJYv3d6lj/sYLgchp5eutSz6X67FGFv3IHCBbU5wQBlYXe8Bv/r+uhxP6VIAXvyXSt35AAGc5hkANFBHB0v/PJzmLg4sd2yacAozybm9ITPJKTdj+4cQtIrgZxBJtCuBoBQ9Y4v00rdaaYT15VZ3CLjypIvVIZeImiTGR1OwocHluoZrdecXFIT3Lo9lTBsJVPbIkyI3AU0Z82nQPgkCsp8CVAQYYlQXqd7ObrcFIsfX6NHZ+Z22kXaRlBd7FMk4PJ6u8X3R9B1vP+bJoM5Cxx15ZHNkgD49u8PJT2ags4 Wed Feb 24 12:24:40 2022 Info: MID 22178297 ready 22089 bytes from
Wed Feb 24 12:24:40 2022 Info: LDAP: Masquerade query LDAP.masquerade MID 22178297 address test@lab.cisco.com to test@lab.cisco.com Wed Feb 24 12:24:40 2022 Info: ICID 122563 close Wed Feb 24 12:24:40 2022 Info: LDAP: Masquerade query LDAP.masquerade MID 22178297 address test@lab.cisco.com to test@lab.cisco.com Wed Feb 24 12:24:40 2022 Info: MID 22178297 attachment 'testfile.xlsx' Wed Feb 24 12:24:42 2022 Info: MID 22178297 was marked unscannable due to extraction failures. Reason: The password protected attachment 'testfile.xlsx' could not be scanned successfully. Wed Feb 24 12:24:42 2022 Warning: MID 22178297: scanning error (name='testfile.xlsx', type=document/xls): Extraction failure of password protected attachment Wed Feb 24 12:24:42 2022 Info: MID 22178297 matched all recipients for per-recipient policy test1 in the inbound table Wed Feb 24 12:24:46 2022 Info: MID 22178297 interim verdict using engine: CASE spam negative Wed Feb 24 12:24:46 2022 Info: MID 22178297 using engine: CASE spam negative Wed Feb 24 12:24:46 2022 Info: MID 22178297 interim AV verdict using McAfee ENCRYPTED Wed Feb 24 12:24:46 2022 Info: MID 22178297 interim AV verdict using Sophos ENCRYPTED Wed Feb 24 12:24:46 2022 Info: MID 22178297 antivirus encrypted Wed Feb 24 12:24:46 2022 Info: MID 22178297 AMP file reputation verdict : UNKNOWN Wed Feb 24 12:24:46 2022 Info: MID 22178297 using engine: GRAYMAIL negative Wed Feb 24 12:24:46 2022 Info: MID 22178297 Unable to safe print the attachment, Filename: testfile.xlsx, Reason: The attachment is encrypted, Action: The attachment is stripped Wed Feb 24 12:24:46 2022 Info: MID 22178297 rewritten to MID 22178298 by safeprint-all-attachments-strip-unscan filter 'PDF-Safeprint' Wed Feb 24 12:24:46 2022 Info: Message finished MID 22178297 done
b) content_scanner에서 다음을 볼 수 있습니다.
Wed Feb 24 12:24:42 2022 Info: PF: MID 22178297 Failed to open document - 'testfile.xlsx' because it is password protected.GUI에서 실패한 프로세스에 대한 확인
a) 메시지 추적의 GUI에서 메시지 ID에 대한 필터
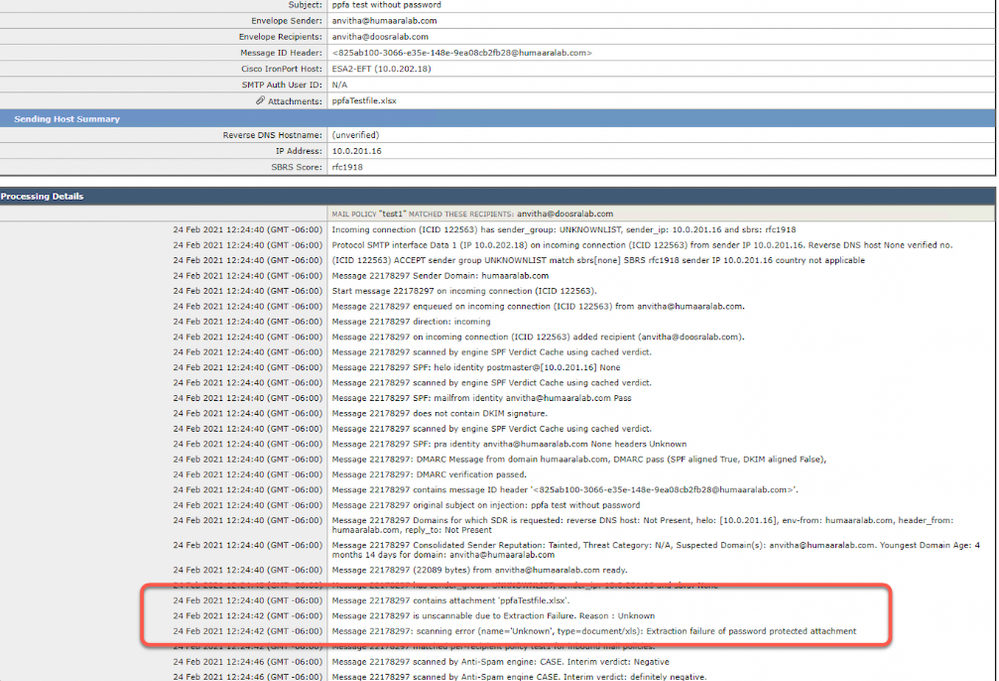
중첩된 암호 보호 파일
중첩된 암호로 보호된 파일은 추출할 수 없습니다. 현재는 지원되지 않습니다.
mail_logs에서 이 오류를 볼 수 있습니다
Sun Nov 22 21:09:31 2022 Info: MID 19597596 attachment 'testfile.zip'
Sun Nov 22 21:09:31 2022 Info: ICID 465893 close
Sun Nov 22 21:09:41 2022 Info: MID 19597596 was marked unscannable due to extraction failures. Reason: The attachment could not be decrypted for scanning.상태 보기
CLI에서 "ppfastats" 명령을 사용하여 암호로 보호된 첨부 파일이 있고 ESA에서 스캔한 메시지의 요약을 볼 수 있습니다.

참고: ppfastats는 숨겨진 명령입니다.
(Machine esa1.lab.cisco.com)> ppfastats
Incoming PPFA Statistics:
Total number of Password Protected Attachments : 425
Total number of Sucessfully scanned Password Protected Attachments : 386
Total number of Protected PDF Attachments : 136
Total number of Sucessfully scanned PDF Attachments : 136
Total number of Protected Office Attachments (XLS, PPT, DOC) : 36
Total number of Sucessfully scanned Office Attachments : 36
Total number of Protected Archive Attachments : 253
Total number of Sucessfully scanned Archive Attachments (ZIP) : 214
Outgoing PPFA Statistics:
PPFA Statistics data not available for Outgoing Mails.
관련 정보
개정 이력
| 개정 | 게시 날짜 | 의견 |
|---|---|---|
1.0 |
14-Jul-2023 |
최초 릴리스 |
 피드백
피드백