SD 액세스 패브릭에서 ARP 확인 문제 해결
다운로드 옵션
편견 없는 언어
본 제품에 대한 문서 세트는 편견 없는 언어를 사용하기 위해 노력합니다. 본 설명서 세트의 목적상, 편견 없는 언어는 나이, 장애, 성별, 인종 정체성, 민족 정체성, 성적 지향성, 사회 경제적 지위 및 교차성에 기초한 차별을 의미하지 않는 언어로 정의됩니다. 제품 소프트웨어의 사용자 인터페이스에서 하드코딩된 언어, RFP 설명서에 기초한 언어 또는 참조된 서드파티 제품에서 사용하는 언어로 인해 설명서에 예외가 있을 수 있습니다. 시스코에서 어떤 방식으로 포용적인 언어를 사용하고 있는지 자세히 알아보세요.
이 번역에 관하여
Cisco는 전 세계 사용자에게 다양한 언어로 지원 콘텐츠를 제공하기 위해 기계 번역 기술과 수작업 번역을 병행하여 이 문서를 번역했습니다. 아무리 품질이 높은 기계 번역이라도 전문 번역가의 번역 결과물만큼 정확하지는 않습니다. Cisco Systems, Inc.는 이 같은 번역에 대해 어떠한 책임도 지지 않으며 항상 원본 영문 문서(링크 제공됨)를 참조할 것을 권장합니다.
목차
소개
이 문서에서는 SD 액세스 패브릭에서 ARP(Address Resolution Protocol) 문제를 해결하는 방법에 대해 설명합니다.
사전 요구 사항
요구 사항
다음 주제에 대한 지식을 보유하고 있으면 유용합니다.
- IP(인터넷 프로토콜) 포워딩
- LISP(Locator/ID Separation Protocol)
- ARP(Address Resolution Protocol)
사용되는 구성 요소
이 문서의 정보는 다음 소프트웨어 및 하드웨어 버전을 기반으로 합니다.
- Cisco IOS® XE 17.10.1의 C9000v
- SDA 1.0(LISP PubSub 아님)
이 문서의 정보는 특정 랩 환경의 디바이스를 토대로 작성되었습니다. 이 문서에 사용된 모든 디바이스는 초기화된(기본) 컨피그레이션으로 시작되었습니다. 현재 네트워크가 작동 중인 경우 모든 명령의 잠재적인 영향을 미리 숙지하시기 바랍니다.
이 문서는 다음과 같은 하드웨어 및 소프트웨어 버전에서도 사용할 수 있습니다.
- C9200
- C9300
- C9400
- C9500
- C9600
- Cisco IOS® XE 16.12 이상
토폴로지
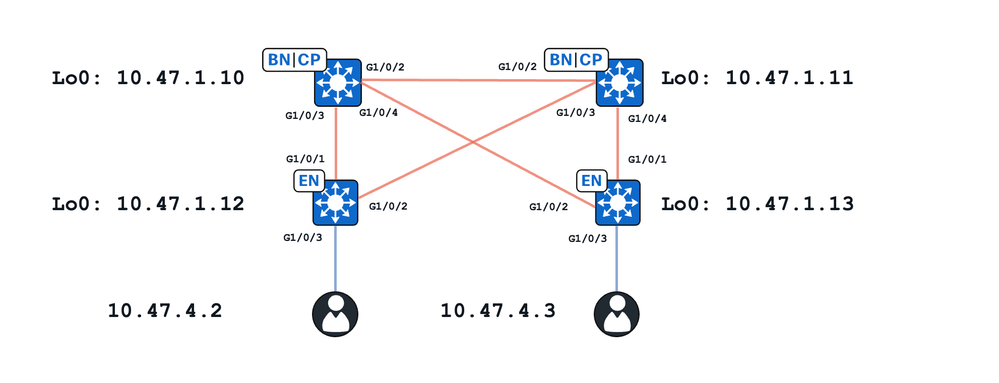
이 연습에서는
- 10.47.1.10 및 10.47.1.11은 공동 경계입니다.
- 10.47.1.12 및 10.47.1.13은 패브릭 에지 노드입니다.
- 10.47.4.2 및 10.47.4.3은 SDA 패브릭 내의 엔드포인트이며 동일한 VLAN/서브넷 및 동일한 VN(red_vn)에 있습니다.
이 문서에는 두 가지 주요 활용 사례가 나와 있습니다.
- 유니캐스트 경로를 통한 10.47.4.2와 10.47.4.3 사이의 ARP 해상도
- 플러딩 경로를 통한 10.47.4.2~10.47.4.3 ARP 해상도
유니캐스트 경로 초기 상태
SDA 내에서는 패브릭 내에서 ARP를 확인하는 두 가지 주요 방법이 있습니다. 유니캐스트 경로라고 하는 것은 레이어 2(L2) ARP 플러딩의 컨피그레이션이 없거나 해당 VLAN에 해당하는 LISP L2 인스턴스 ID(IID)에 "플러드 arp nd"가 구성되어 있지 않음을 나타냅니다. 이 주의 사항 외에도 유니캐스트 ARP 경로를 검증하기 위해 "IP 로컬 프록시 ARP"의 컨피그레이션이나 레이어 3 전용 풀이 없습니다.
이러한 주의 사항이 충족되면 이 트러블슈팅 섹션을 계속합니다. 두 엔드포인트(10.47.4.2 및 10.47.4.3)가 10.47.4.1로 존재하는 패브릭 에지 스위치에 있는 각각의 기본 게이트웨이에 도달할 수 있다고 가정합니다
Edge-1#ping vrf red_vn 10.47.4.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.47.4.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 257/292/344 ms
Edge-2#ping vrf red_vn 10.47.4.3 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.47.4.3, timeout is 2 seconds: !!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 221/321/566 ms
팁: 엔드-호스트 디바이스의 방화벽에 의해 삭제되는 ICMP 패킷과 관련된 잘못된 결론을 피하려면 엔드-호스트에서 에지 스위치로 향하는 기본 게이트웨이를 ping하는 것이 좋습니다.
그런 다음 각 패브릭 에지 노드에 IP 장치 추적(IPDT), LISP L2 데이터베이스, L2 AR(Address Resolution) 데이터베이스 및 L3 데이터베이스 내의 각 엔드포인트가 있는지 확인합니다.
Edge-1:
IPDT 내에서 엔드포인트를 확인하려면 show device-tracking database interface <interface connecting to endpoint> 명령을 사용합니다.
Edge-1#show device-tracking database interface g1/0/3
portDB has 2 entries for interface Gi1/0/3, 2 dynamic
Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created
Preflevel flags (prlvl):
0001:MAC and LLA match 0002:Orig trunk 0004:Orig access
0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned
0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
DH4 10.47.4.2 5254.0019.93e9 Gi1/0/3 1026 0024 15s REACHABLE 228 s try 0(6374 s)
LISP L2 데이터베이스에서 엔드포인트를 확인하려면 show lisp eid-table vlan <vlan id> ethernet database <mac address> 명령을 사용하여 이전 명령의 VLAN과 MAC 주소를 사용합니다
Edge-1#show lisp eid-table vlan 1026 ethernet database 5254.0019.93e9 LISP ETR MAC Mapping Database for LISP 0 EID-table Vlan 1026 (IID 8190), LSBs: 0x1 Entries total 1, no-route 0, inactive 0, do-not-register 2 5254.0019.93e9/48, dynamic-eid Auto-L2-group-8190, inherited from default locator-set rloc_222e1707-175d-4019-a783-060404f8bc2f Uptime: 3w5d, Last-change: 3w5d Domain-ID: local Service-Insertion: N/A Locator Pri/Wgt Source State 10.47.1.12 10/10 cfg-intf site-self, reachable <-- Edge-1's RLOC Map-server Uptime ACK Domain-ID 10.47.1.10 1w3d Yes 0 10.47.1.11 3w5d Yes 0
L2 AR 데이터베이스를 확인하려면 show lisp eid-table vlan <vlan-id> ethernet database address-resolution <mac address> 명령을 사용합니다
Edge-1#show lisp eid-table vlan 1026 ethernet database address-resolution 5254.0019.93e9 LISP ETR Address Resolution for LISP 0 EID-table Vlan 1026 (IID 8190) (*) -> entry being deleted Hardware Address L3 InstID Host Address 5254.0019.93e9 4099 10.47.4.2/32 <-- Endpoint MAC address, LISP L3 IID, and IPv4 address, respectively
LISP L3 데이터베이스를 확인하려면 show lisp instance-id <L3 IID> ipv4 database <IPv4 address>/subnet mask 명령에서 이전 명령의 LISP L3 IID를 사용합니다
Edge-1#show lisp instance-id 4099 ipv4 database 10.47.4.2/32 LISP ETR IPv4 Mapping Database for LISP 0 EID-table vrf red_vn (IID 4099), LSBs: 0x1 Entries total 1, no-route 0, inactive 0, do-not-register 1 10.47.4.2/32, dynamic-eid red-IPV4, inherited from default locator-set rloc_222e1707-175d-4019-a783-060404f8bc2f Uptime: 3w5d, Last-change: 3w5d Domain-ID: local Service-Insertion: N/A Locator Pri/Wgt Source State 10.47.1.12 10/10 cfg-intf site-self, reachable <-- Edge-1's own RLOC Map-server Uptime ACK Domain-ID 10.47.1.10 1w0d Yes 0 10.47.1.11 1w0d Yes 0
에지-2:
IPDT 내에서 엔드포인트를 확인하려면 show device-tracking database interface <interface connecting to local endpoint> 명령을 사용합니다.
Edge-2#show device-tracking database interface g1/0/3
portDB has 3 entries for interface Gi1/0/3, 3 dynamic
Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created
Preflevel flags (prlvl):
0001:MAC and LLA match 0002:Orig trunk 0004:Orig access
0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned
0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
DH4 10.47.4.3 5254.001e.ad00 Gi1/0/3 1026 0024 122s REACHABLE 124 s try 0(5810 s)
LISP L2 데이터베이스에서 엔드포인트를 확인하려면 show lisp eid-table vlan <vlan id> ethernet database <mac address> 명령을 사용하여 이전 명령의 VLAN 및 MAC 주소를 사용합니다
Edge-2#show lisp eid-table vlan 1026 ethernet database 5254.001e.ad00 LISP ETR MAC Mapping Database for LISP 0 EID-table Vlan 1026 (IID 8190), LSBs: 0x1 Entries total 1, no-route 0, inactive 0, do-not-register 2 5254.001e.ad00/48, dynamic-eid Auto-L2-group-8190, inherited from default locator-set rloc_691b1fe4-5264-44c2-bb1b-0903b3eb2c51 Uptime: 3w5d, Last-change: 3w5d Domain-ID: local Service-Insertion: N/A Locator Pri/Wgt Source State 10.47.1.13 10/10 cfg-intf site-self, reachable <-- Edge-2's RLOC Map-server Uptime ACK Domain-ID 10.47.1.10 1w2d Yes 0 10.47.1.11 1w2d Yes 0
L2 AR 데이터베이스를 확인하려면 show lisp eid-table vlan <vlan-id> ethernet database address-resolution <mac address> 명령을 사용합니다
Edge-2#show lisp eid-table vlan 1026 ethernet database address-resolution 5254.001e.ad00 LISP ETR Address Resolution for LISP 0 EID-table Vlan 1026 (IID 8190) (*) -> entry being deleted Hardware Address L3 InstID Host Address 5254.001e.ad00 4099 10.47.4.3/32 <-- Endpoint MAC address, LISP L3 IID, and IPv4 address, respectively
LISP L3 데이터베이스를 확인하려면 show lisp instance-id <L3 IID> ipv4 database <IPv4 address>/subnet mask 명령에서 이전 명령의 LISP L3 IID를 사용합니다
Edge-2#show lisp instance-id 4099 ipv4 database 10.47.4.3/32 LISP ETR IPv4 Mapping Database for LISP 0 EID-table vrf ed_vn (IID 4099), LSBs: 0x1 Entries total 1, no-route 0, inactive 0, do-not-register 2 10.47.4.3/32, dynamic-eid red-IPV4, inherited from default locator-set rloc_691b1fe4-5264-44c2-bb1b-0903b3eb2c51 Uptime: 1w0d, Last-change: 1w0d Domain-ID: local Service-Insertion: N/A Locator Pri/Wgt Source State 10.47.1.13 10/10 cfg-intf site-self, reachable <-- Edge-2, RLOC Map-server Uptime ACK Domain-ID 10.47.1.10 1w0d Yes 0 10.47.1.11 1w0d Yes 0
배치된 테두리:
두 엔드포인트 모두 L2 LISP, L2 AR 및 L3 관점에서 양쪽 패브릭 컨트롤 플레인(Border-1 및 Border-2)에 등록되는 것이 좋습니다. L2 LISP ID를 파생하려면 패브릭 에지 노드를 확인하고 show vlan id <vlan id> 명령을 사용합니다
Edge-1#show vlan id 1026 VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1026 red active L2LI0:8190, Gi1/0/3 <-- L2 LISP IID VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2 ---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1026 enet 101026 1500 - - - - - 0 0 Remote SPAN VLAN ---------------- Disabled Primary Secondary Type Ports ------- --------- ----------------- ------------------------------------------
show lisp instance-id <L2 IID> ethernet server 명령에서 L2 IID를 사용하여 L2 LISP 관점에서 서버를 확인합니다
Border-1#show lisp instance-id 8190 ethernet server
LISP Site Registration Information
* = Some locators are down or unreachable
# = Some registrations are sourced by reliable transport
Site Name Last Up Who Last Inst EID Prefix
Register Registered ID
site_uci never no -- 8190 any-mac
1w3d yes# 10.47.1.12:21038 8190 5254.0019.93e9/48 <-- RLOC of the FE node, EID prefix that was registered
1w2d yes# 10.47.1.13:16056 8190 5254.001e.ad00/48 <-- RLOC of the FE node, EID prefix that was registered
L2 AR 서버를 확인하려면 show lisp instance-id <L2 IID> ethernet server address-resolution 명령을 사용합니다
Border-1#show lisp instance-id 8190 ethernet server address-resolution
Address-resolution data for router lisp 0 instance-id 8190
L3 InstID Host Address Hardware Address
4099 10.47.4.2/32 5254.0019.93e9 <-- L3 LISP IID, Endpoint IPv4 Address, MAC Address, respectively
4099 10.47.4.3/32 5254.001e.ad00 <-- L3 LISP IID, Endpoint IPv4 Address, MAC Address, respectively
L3 서버를 확인하려면 show lisp instance-id <L3 IID> ipv4 server 명령을 사용합니다
Border-1#show lisp instance-id 4099 ipv4 server
LISP Site Registration Information
* = Some locators are down or unreachable
# = Some registrations are sourced by reliable transport
Site Name Last Up Who Last Inst EID Prefix
Register Registered ID
site_uci never no -- 4099 0.0.0.0/0
6d01h yes# 10.47.1.11:22876 4099 8.8.8.8/32
1w0d yes# 10.47.1.10:21610 4099 10.47.2.4/30
1w0d yes# 10.47.1.11:22876 4099 10.47.2.12/30
never no -- 4099 10.47.4.0/24
1w0d yes# 10.47.1.12:21038 4099 10.47.4.2/32
1w0d yes# 10.47.1.13:16056 4099 10.47.4.3/32
1w0d yes# 10.47.1.11:22876 4099 10.47.6.0/24
1w0d yes# 10.47.1.11:22876 4099 10.47.7.0/24
1w0d yes# 10.47.1.11:22876 4099 10.47.9.8/29
never no -- 4099 10.47.10.0/24
1w0d yes# 10.47.1.13:16056 4099 10.47.10.2/32
컨트롤 플레인에는 L3, L2 및 AR 항목에 대한 등록 이벤트에 대한 간략한 기록이 있습니다. 이는 로밍 클라이언트 또는 클라이언트가 매우 짧은 시간에 여러 패브릭 에지에 의해 예기치 않게 등록되는 가능한 루프를 트러블슈팅할 때 유용할 수 있습니다.
Border-1#show lisp instance-id 8190 ethernet server resolution registration-history | include Timestamp|10.47.4.2|10.47.4.3
Timestamp (UTC) Instance Proto Roam WLC Source
*Oct 9 19:14:39.183 8190 TCP No No 10.47.1.12
+*10.47.4.2/32 / 5254.0019.93e9 <-- Last registered at Oct 9 19:14:39
*Oct 9 19:14:41.183 8190 TCP No No 10.47.1.13
+*10.47.4.3/32 / 5254.001e.ad00 <-- Last registered at OCt 9 19:14:31
유니캐스트 경로 ARP 요청 상위 레벨 워크플로
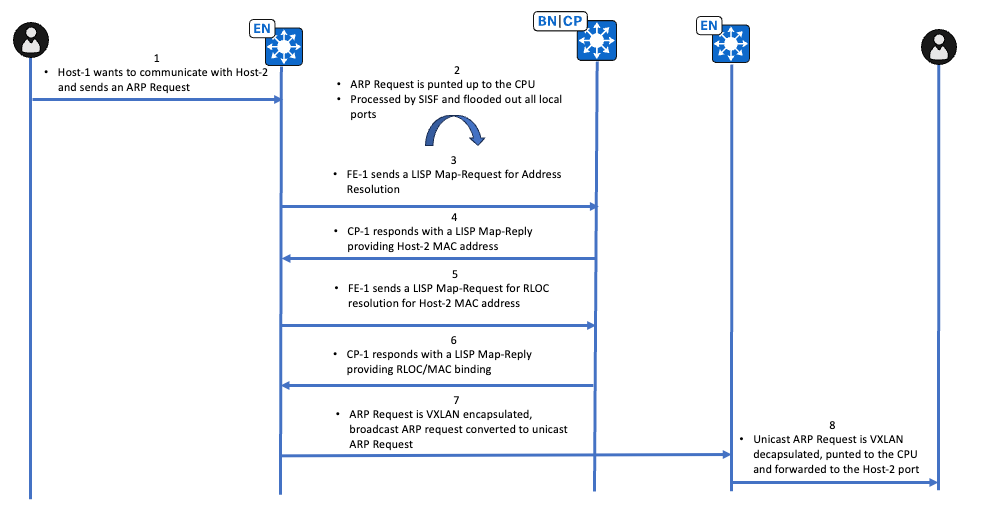
유니캐스트 경로 ARP 요청 확인
IP 주소 10.47.4.2를 소유한 엔드포인트는 Edge-1의 EPC(Embedded Packet Capture)를 통해 확인된 브로드캐스트 ARP 요청을 보냅니다
Edge-1(10.47.1.12)
Edge-1#monitor capture 1 interface g1/0/3 in match any
Edge-1#monitor capture 1 start
Edge-1#monitor capture 1 stop
Capture statistics collected at software:
Capture duration - 39 seconds
Packets received - 21
Packets dropped - 0
Packets oversized - 0
Number of Bytes dropped at asic not collected
Capture buffer will exists till exported or cleared
Stopped capture point : 1
Edge-1#show monitor capture 1 buffer brief
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
1 0.000000 52:54:00:19:93:e9 -> ff:ff:ff:ff:ff:ff ARP 60 Who has 10.47.4.3? Tell 10.47.4.
Edge-1#show monitor capture 1 buffer detailed
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
Frame 1: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Interface id: 0 (/tmp/epc_ws/wif_to_ts_pipe)
Interface name: /tmp/epc_ws/wif_to_ts_pipe
Encapsulation type: Ethernet (1)
Arrival Time: Oct 19, 2023 23:43:31.893095000 UTC
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1697759011.893095000 seconds
[Time delta from previous captured frame: 0.000000000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 0.000000000 seconds]
Frame Number: 1
Frame Length: 60 bytes (480 bits)
Capture Length: 60 bytes (480 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:arp]
Ethernet II, Src: 52:54:00:19:93:e9 (52:54:00:19:93:e9), Dst: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff)
Destination: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff)
Address: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...1 .... .... .... .... = IG bit: Group address (multicast/broadcast)
Source: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
Address: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: ARP (0x0806)
Padding: 000000000000000000000000000000000000
Address Resolution Protocol (request)
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
Sender IP address: 10.47.4.2
Target MAC address: 00:00:00:00:00:00 (00:00:00:00:00:00)
Target IP address: 10.47.4.3
이 ARP 요청은 추가 처리를 위해 CPU에 대해 적용됩니다. FED Punject Capture를 활용하여 추가 정보를 얻습니다.
Edge-1#debug platform software fed switch active punt packet-capture set-filter “arp" Edge-1#debug platform software fed switch active punt packet-capture start Edge-1#debug platform software fed switch active punt packet-capture stop Edge-1#show platform software fed switch active punt packet-capture brief Punt packet capturing: disabled. Buffer wrapping: disabled Total captured so far: 8 packets. Capture capacity : 4096 packets Capture filter : "arp" ------ Punt Packet Number: 1, Timestamp: 2023/10/19 23:55:03.552 ------ interface : physical: GigabitEthernet1/0/3[if-id: 0x0000000b], pal: GigabitEthernet1/0/3 [if-id: 0x0000000b] <-- Physical interface the ARP Request was received from metadata : cause: 109 [snoop packets], sub-cause: 1, q-no: 16, linktype: MCP_LINK_TYPE_IP [1] <-- Punted for cause snoop packets to CPU queue 16 ether hdr : dest mac: ffff.ffff.ffff, src mac: 5254.0019.93e9 ether hdr : ethertype: 0x0806 (ARP)
어떤 CPU 큐(16)인지 보려면 명령 show platform software fed switch active punt cpu 16을 사용합니다
Edge-1#show platform software fed switch active punt cpuq 16 Punt CPU Q Statistics =========================================== CPU Q Id : 16 CPU Q Name : CPU_Q_PROTO_SNOOPING Packets received from ASIC : 49054 Send to IOSd total attempts : 49054 <-- Same number as received from ASIC
Send to IOSd failed count : 0 <-- No failures
CPU 폴리서(Queue 16)의 Proto Snooping Queue(Proto 스누핑 큐)에 삭제되는 항목이 없는 것이 이상적입니다. 명령 show platform hardware fed switch active qos queue stats internal cpu policer를 사용합니다
Edge-1#show platform hardware fed switch active qos queue stats internal cpu policer | include QId|Proto QId PlcIdx Queue Name Enabled Rate Rate Drop(Bytes) Drop(Frames) 16 12 Proto Snooping No 2000 2000 0 0 <-- No drops
그런 다음 Punt Service에서 펀트된 ARP 요청을 처리합니다. debug, debug platform software infrastructure punt에서 이 동작을 볼 수 있습니다
Edge-1#debug platform software infrastructure punt
*Oct 20 00:07:01.509: PUNT RX: mcprp_process_receive_packet: pak->vlan_id: 1026 *Oct 20 00:07:01.509: Punt: IP proto src 147.233.10.47, dst 4.2.0.0, from table 0, intf Gi1/0/3, encap ARPA, size 60, cause snoop packets(L3) <-- The IP address is obscured, but it is 10.47.4.2 *Oct 20 00:07:01.509: punt cause:snoop packets invoking reg_invoke_mcprp_punt_feature_msg *Oct 20 00:07:01.509: punt cause:snoop packets MCPRP_PUNT_PAK_PROC_OK_DONE
주의: 이 디버그는 수다스러우므로 주의해서 사용하십시오.
Punt Service는 패킷을 처리한 후 Proto Snoop 및 Proto ARP 스누프 프로세스에 패킷을 전달합니다. 그러면 ARP 스누핑 테이블에 항목이 생성되고 패킷이 Device-Tracking/SISF로 전송됩니다. 이를 보려면 debug arp 및 debug platform fhs all
Edge-1#debug arp
Edge-1#debug platform fhs all
*Oct 20 00:12:06.908: ARP packet received from ARP snooper(Gi1/0/3 10.47.4.2 (5254.0019.93e9) VLAN:1026)
주의: 이러한 디버그는 수다스러우므로 신중하게 사용하십시오.
명령 show platform arpsnooping client <MAC address>를 사용하여 ARP 요청에 어떤 일이 발생하는지 확인합니다
Edge-1#show platform arpsnooping client 5254.0019.93e9 PLAT_DAI : Platform DAI shim FWDPLANE : Dataplane forwarding BRIDGE : Packet to be bridged ARPSN : Arp Snooping Packet Trace for client MAC 5254.0019.93E9: Timestamp Sender Mac Sender IP Target Mac Target IP Opcode VLAN Handler:Action ----------------------- --------------- ------------- ----------------- -------------- ------------ ------- ------------------------------ 2023/10/24 14:37:15.045 5254.0019.93e9 10.47.4.2 0000.0000.0000 10.47.4.3 ARP_REQUEST 1026 PSISF_PRE:PSP_BRNEUTRAL 2023/10/24 14:37:15.045 5254.0019.93e9 10.47.4.2 0000.0000.0000 10.47.4.3 ARP_REQUEST 1026 INJECT:INJ_VLAN_IFINPUT_TO_BDI 2023/10/24 14:37:15.045 5254.0019.93e9 10.47.4.2 0000.0000.0000 10.47.4.3 ARP_REQUEST 1026 INJECT:BD_DPIDX_TO_FWDPLANE
IPDT/SISF는 패킷을 처리할 때 ARP 요청의 내용을 확인하고 LISP를 통해 해결을 기다리는 동안 임시 항목을 만듭니다.
Edge-1#show device-tracking messages detailed 255 | i 5254.0019.93e9 [Tue Oct 24 14:37:12.000] VLAN 1026, From Gi1/0/3 seclvl [guard], MAC 5254.0019.93e9: ARP::REQ, [Tue Oct 24 14:37:13.000] VLAN 1026, From Gi1/0/3 seclvl [guard], MAC 5254.0019.93e9: ARP::REQ,
debug device-tracking(디바이스 추적 디버그)을 사용하는 경우 디바이스 추적에서 0000.0000.00fd를 가리키는 항목이 있음을 확인할 수 있습니다. 이 모든 것은 Gi1/0/3 뒤에 있는 호스트가 아직 해결되지 않은 호스트를 쿼리하고 있다는 것입니다. 이 호스트는 일시적인 상태이거나 존재하지 않는 호스트를 쿼리하는 경우 영구적인 것이며, 반드시 나쁜 것은 아닙니다
Edge-1#debug device-tracking Device-tracking - General debugging is on *Oct 24 14:55:02.967: SISF[POL]: vlan 1026 matches vlan list on policy IPDT_POLICY for target Gi1/0/3 *Oct 24 14:55:02.967: SISF[POL]: Found matching policy IPDT_POLICY for feature Device-tracking on Gi1/0/3
*Oct 24 14:55:02.967:SISF[GLN]: Checking if ARP ownership can be taken by device-tracking
*Oct 24 14:55:02.967:SISF[GLN]: Not an ARP reply, do not take over
*Oct 24 14:55:02.967:SISF[POL]: Found matching policy LISP-AR-RELAY-VLAN for feature Address Resolution Relay on vlan 1026 *Oct 24 14:55:02.967: SISF[MAC]: Creating new MAC entry for 0000.0000.00fd on interface if none exists *Oct 24 14:55:02.967: SISF[MAC]: Number of MAC entries in MAC-CREATING state incremented to 1 *Oct 24 14:55:02.968: SISF[BT ]: Attaching 0000.0000.00fd entry in MacAdrDB for 10.47.4.3 *Oct 24 14:55:02.968: SISF[GLN]: Binding entry event 1 for 10.47.4.3
LISP-AR-RELAY-VLAN 정책에 따라 SISF는 LISP를 사용하여 ARP 확인을 트리거하며, 이 LISP 컨트롤 플레인 프로세스가 이를 대신할 수 있습니다.
Edge-1#debug lisp control-plane all Edge-1#debug l2lisp all *Oct 24 15:10:27.677: LISP Client 'SISF client': SISF request to resolve 10.47.4.3 in Vlan 1026.
Edge-1은 LISP Control-Plane을 통해 MAC 주소 10.47.4.3을 확인하기 위해 LISP Map-Request를 전송합니다
Edge-1#debug lisp control-plane all Edge-1#debug l2lisp all *Oct 24 15:10:27.681: LISP[REMT ]-0: Map Request: Delay is over for IID 8190 EID 10.47.4.3/32, requester 'AR'. *Oct 24 15:10:27.681: LISP[REMT ]-0 IID 8190: Schedule processing of Map-Requests from 'remote EID prefix' in IPv4. *Oct 24 15:10:27.681: LISP[REMT ]-0: Map Request: Sending request for IID 8190 EID 10.47.4.3/32, requester 'AR'.
Edge-1의 CPU(컨트롤 플레인)에서 양방향 EPC(Embedded Packet Capture)를 수행하면 수신 ARP 요청과 후속 LISP 맵 요청이 표시됩니다
Edge-1#monitor capture 1 control-plane both match any Edge-1#monitor capture 1 start Started capture point : 1 Edge-1#monitor capture 1 stop Edge-1#show monitor capture 1 buffer display-filter "arp.dst.proto_ipv4==10.47.4.3 or lisp" Starting the packet display ........ Press Ctrl + Shift + 6 to exit 60 10.110293 52:54:00:19:93:e9 -> ff:ff:ff:ff:ff:ff ARP 60 Who has 10.47.4.3? Tell 10.47.4.2 61 10.111714 10.47.4.3 -> 10.47.4.3 LISP 114 Encapsulated Map-Request for Unknown LCAF Type (53)/32
LISP Map-Request를 더 자세히 볼 수 있습니다
Edge-1#show monitor capture 1 buffer display-filter "frame.number==61" detailed
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
Frame 61: 114 bytes on wire (912 bits), 114 bytes captured (912 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Interface id: 0 (/tmp/epc_ws/wif_to_ts_pipe)
Interface name: /tmp/epc_ws/wif_to_ts_pipe
Encapsulation type: Ethernet (1)
Arrival Time: Oct 24, 2023 15:20:08.948469000 UTC
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1698160808.948469000 seconds
[Time delta from previous captured frame: 0.001421000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 10.111714000 seconds]
Frame Number: 61
Frame Length: 114 bytes (912 bits)
Capture Length: 114 bytes (912 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:udp:lisp:ip:udp:lisp]
Ethernet II, Src: 00:00:00:00:00:00 (00:00:00:00:00:00), Dst: 00:00:00:00:00:00 (00:00:00:00:00:00) <-- Ignore the SMAC/DMAC this is done up at the CPU, not final MAC addresses
Destination: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.47.1.12, Dst: 10.47.1.10 <-- Edge-1 RLOC and one of the collocated border RLOC, respectively
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT)
1100 00.. = Differentiated Services Codepoint: Class Selector 6 (48)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 100
Identification: 0x599c (22940)
Flags: 0x0000
0... .... .... .... = Reserved bit: Not set
.0.. .... .... .... = Don't fragment: Not set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0x4ab9 [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.1.12
Destination: 10.47.1.10
User Datagram Protocol, Src Port: 4342, Dst Port: 4342
Source Port: 4342
Destination Port: 4342
Length: 80
Checksum: 0x6393 [unverified]
[Checksum Status: Unverified]
[Stream index: 0]
[Timestamps]
[Time since first frame: 0.000000000 seconds]
[Time since previous frame: 0.000000000 seconds]
Locator/ID Separation Protocol
1000 .... .... .... .... .... = Type: Encapsulated Control Message (8)
.... 0... .... .... .... .... .... .... = S bit (LISP-SEC capable): Not set
.... .0.. .... .... .... .... .... .... = D bit (DDT-originated): Not set
.... ..00 0000 0000 0000 0000 0000 0000 = Reserved bits: 0x0000000
Internet Protocol Version 4, Src: 10.47.4.3, Dst: 10.47.4.3 <-- MAP Request to resolve the MAC address tied to 10.47.4.3
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT)
1100 00.. = Differentiated Services Codepoint: Class Selector 6 (48)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 68
Identification: 0x599b (22939)
Flags: 0x0000
0... .... .... .... = Reserved bit: Not set
.0.. .... .... .... = Don't fragment: Not set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0x44ea [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.4.3
Destination: 10.47.4.3
User Datagram Protocol, Src Port: 4342, Dst Port: 4342
Source Port: 4342
Destination Port: 4342
Length: 48
Checksum: 0x9622 [unverified]
[Checksum Status: Unverified]
[Stream index: 1]
[Timestamps]
[Time since first frame: 0.000000000 seconds]
[Time since previous frame: 0.000000000 seconds]
Locator/ID Separation Protocol
0001 .... .... .... .... .... = Type: Map-Request (1)
.... 0000 00.. .... .... .... = Flags: 0x00
.... 0... .... .... .... .... = A bit (Authoritative): Not set
.... .0.. .... .... .... .... = M bit (Map-Reply present): Not set
.... ..0. .... .... .... .... = P bit (Probe): Not set
.... ...0 .... .... .... .... = S bit (Solicit-Map-Request): Not set
.... .... 0... .... .... .... = p bit (Proxy ITR): Not set
.... .... .0.. .... .... .... = s bit (SMR-invoked): Not set
.... .... ..00 0000 000. .... = Reserved bits: 0x000
.... .... .... .... ...0 0000 = ITR-RLOC Count: 0
Record Count: 1
Nonce: 0xcffee30fb39a05b7
Source EID AFI: Reserved (0)
Source EID: not set
ITR-RLOC 1: 10.47.1.12
ITR-RLOC AFI: IPv4 (1)
ITR-RLOC Address: 10.47.1.12
Map-Request Record 1: Unknown LCAF Type (53)/32
Reserved: 0x00
Prefix Length: 32
Prefix AFI: LISP Canonical Address Format (LCAF) (16387)
Prefix: Unknown LCAF Type (53)
LCAF: Unknown (53)
LCAF Header: 00003520000a
Reserved bits: 0x00
Flags: 0x00
Type: Unknown (53)
Reserved bits: 0x20
Length: 10
[Expert Info (Error/Protocol): LCAF type 53 is not defined in draft-ietf-lisp-lcaf-05]
[LCAF type 53 is not defined in draft-ietf-lisp-lcaf-05]
[Severity level: Error]
[Group: Protocol]
배치된 테두리(10.47.1.10 및 10.47.1.11)
다음으로 LISP Control-Plane은 LISP Map-Reply로 Edge-1에 응답합니다. 이는 디버그뿐만 아니라 CPU EPC에서도 확인할 수 있습니다.
Border-2#show monitor capture 1 buffer display-filter lisp Starting the packet display ........ Press Ctrl + Shift + 6 to exit 113 12.767420 10.47.4.3 -> 10.47.4.3 LISP 114 Encapsulated Map-Request for Unknown LCAF Type (53)/32 114 12.774428 10.47.1.11 -> 10.47.1.12 LISP 96 Map-Reply for Unknown LCAF Type (53)/32
패킷을 자세히 살펴볼 때 LISP Map-Request 및 후속 LISP Map-Reply를 확인할 수 있습니다
Border-2#show monitor capture 1 buffer display-filter frame.number==113 detailed
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
Frame 113: 114 bytes on wire (912 bits), 114 bytes captured (912 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Interface id: 0 (/tmp/epc_ws/wif_to_ts_pipe)
Interface name: /tmp/epc_ws/wif_to_ts_pipe
Encapsulation type: Ethernet (1)
Arrival Time: Oct 24, 2023 15:41:06.566253000 UTC
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1698162066.566253000 seconds
[Time delta from previous captured frame: 0.013424000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 12.767420000 seconds]
Frame Number: 113
Frame Length: 114 bytes (912 bits)
Capture Length: 114 bytes (912 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:udp:lisp:ip:udp:lisp]
Ethernet II, Src: 52:54:00:04:84:a3 (52:54:00:04:84:a3), Dst: 52:54:00:1c:7d:e0 (52:54:00:1c:7d:e0) <-- True MAC addresses
Destination: 52:54:00:1c:7d:e0 (52:54:00:1c:7d:e0)
Address: 52:54:00:1c:7d:e0 (52:54:00:1c:7d:e0)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 52:54:00:04:84:a3 (52:54:00:04:84:a3)
Address: 52:54:00:04:84:a3 (52:54:00:04:84:a3)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.47.1.12, Dst: 10.47.1.11 <-- Edge-1 RLOC and Border-2 RLOC, respectively
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT)
1100 00.. = Differentiated Services Codepoint: Class Selector 6 (48)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 100
Identification: 0x5e19 (24089)
Flags: 0x0000
0... .... .... .... = Reserved bit: Not set
.0.. .... .... .... = Don't fragment: Not set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0x463b [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.1.12
Destination: 10.47.1.11
User Datagram Protocol, Src Port: 4342, Dst Port: 4342
Source Port: 4342
Destination Port: 4342
Length: 80
Checksum: 0x6392 [unverified]
[Checksum Status: Unverified]
[Stream index: 1]
[Timestamps]
[Time since first frame: 0.000000000 seconds]
[Time since previous frame: 0.000000000 seconds]
Locator/ID Separation Protocol
1000 .... .... .... .... .... = Type: Encapsulated Control Message (8)
.... 0... .... .... .... .... .... .... = S bit (LISP-SEC capable): Not set
.... .0.. .... .... .... .... .... .... = D bit (DDT-originated): Not set
.... ..00 0000 0000 0000 0000 0000 0000 = Reserved bits: 0x0000000
Internet Protocol Version 4, Src: 10.47.4.3, Dst: 10.47.4.3 <-- LISP MAP Request for 10.47.4.3
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT)
1100 00.. = Differentiated Services Codepoint: Class Selector 6 (48)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 68
Identification: 0x5e18 (24088)
Flags: 0x0000
0... .... .... .... = Reserved bit: Not set
.0.. .... .... .... = Don't fragment: Not set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0x406d [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.4.3
Destination: 10.47.4.3
User Datagram Protocol, Src Port: 4342, Dst Port: 4342
Source Port: 4342
Destination Port: 4342
Length: 48
Checksum: 0xe9a8 [unverified]
[Checksum Status: Unverified]
[Stream index: 2]
[Timestamps]
[Time since first frame: 0.000000000 seconds]
[Time since previous frame: 0.000000000 seconds]
Locator/ID Separation Protocol
0001 .... .... .... .... .... = Type: Map-Request (1)
.... 0000 00.. .... .... .... = Flags: 0x00
.... 0... .... .... .... .... = A bit (Authoritative): Not set
.... .0.. .... .... .... .... = M bit (Map-Reply present): Not set
.... ..0. .... .... .... .... = P bit (Probe): Not set
.... ...0 .... .... .... .... = S bit (Solicit-Map-Request): Not set
.... .... 0... .... .... .... = p bit (Proxy ITR): Not set
.... .... .0.. .... .... .... = s bit (SMR-invoked): Not set
.... .... ..00 0000 000. .... = Reserved bits: 0x000
.... .... .... .... ...0 0000 = ITR-RLOC Count: 0
Record Count: 1
Nonce: 0x50c5f2b60b41ca1c
Source EID AFI: Reserved (0)
Source EID: not set
ITR-RLOC 1: 10.47.1.12
ITR-RLOC AFI: IPv4 (1)
ITR-RLOC Address: 10.47.1.12
Map-Request Record 1: Unknown LCAF Type (53)/32
Reserved: 0x00
Prefix Length: 32
Prefix AFI: LISP Canonical Address Format (LCAF) (16387)
Prefix: Unknown LCAF Type (53)
LCAF: Unknown (53)
LCAF Header: 00003520000a
Reserved bits: 0x00
Flags: 0x00
Type: Unknown (53)
Reserved bits: 0x20
Length: 10
[Expert Info (Error/Protocol): LCAF type 53 is not defined in draft-ietf-lisp-lcaf-05]
[LCAF type 53 is not defined in draft-ietf-lisp-lcaf-05]
[Severity level: Error]
[Group: Protocol]
또한 LISP Map-Reply가 다시 전송되는지 확인할 수 있습니다.
Border-2#show monitor capture 1 buffer display-filter frame.number==114 detailed
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
Frame 114: 96 bytes on wire (768 bits), 96 bytes captured (768 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Interface id: 0 (/tmp/epc_ws/wif_to_ts_pipe)
Interface name: /tmp/epc_ws/wif_to_ts_pipe
Encapsulation type: Ethernet (1)
Arrival Time: Oct 24, 2023 15:41:06.573261000 UTC
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1698162066.573261000 seconds
[Time delta from previous captured frame: 0.007008000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 12.774428000 seconds]
Frame Number: 114
Frame Length: 96 bytes (768 bits)
Capture Length: 96 bytes (768 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:udp:lisp]
Ethernet II, Src: 00:00:00:00:00:00 (00:00:00:00:00:00), Dst: 00:00:00:00:00:00 (00:00:00:00:00:00) <-- CPU Inject does not properly show MAC addresses
Destination: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.47.1.11, Dst: 10.47.1.12 <-- Border-2 RLOC and Edge-1 RLOC, respectively
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT)
1100 00.. = Differentiated Services Codepoint: Class Selector 6 (48)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 82
Identification: 0xe231 (57905)
Flags: 0x0000
0... .... .... .... = Reserved bit: Not set
.0.. .... .... .... = Don't fragment: Not set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0xc234 [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.1.11
Destination: 10.47.1.12
User Datagram Protocol, Src Port: 4342, Dst Port: 4342
Source Port: 4342
Destination Port: 4342
Length: 62
Checksum: 0xe1d6 [unverified]
[Checksum Status: Unverified]
[Stream index: 1]
[Timestamps]
[Time since first frame: 0.007008000 seconds]
[Time since previous frame: 0.007008000 seconds]
Locator/ID Separation Protocol
0010 .... .... .... .... .... = Type: Map-Reply (2)
.... 0... .... .... .... .... = P bit (Probe): Not set
.... .0.. .... .... .... .... = E bit (Echo-Nonce locator reachability algorithm enabled): Not set
.... ..0. .... .... .... .... = S bit (LISP-SEC capable): Not set
.... ...0 0000 0000 0000 0000 = Reserved bits: 0x00000
Record Count: 1
Nonce: 0x50c5f2b60b41ca1c
Mapping Record 1, EID Prefix: Unknown LCAF Type (53)/32, TTL: 1440, Action: No-Action, Not Authoritative
Record TTL: 1440
Locator Count: 1
EID Mask Length: 32
000. .... .... .... = Action: No-Action (0)
...0 .... .... .... = Authoritative bit: Not set
.... .000 0000 0000 = Reserved: 0x000
0000 .... .... .... = Reserved: 0x0
.... 0000 0000 0000 = Mapping Version: 0
EID Prefix AFI: LISP Canonical Address Format (LCAF) (16387)
EID Prefix: Unknown LCAF Type (53)
LCAF: Unknown (53)
LCAF Header: 00003520000a
Reserved bits: 0x00
Flags: 0x00
Type: Unknown (53)
Reserved bits: 0x20
Length: 10
[Expert Info (Error/Protocol): LCAF type 53 is not defined in draft-ietf-lisp-lcaf-05]
[LCAF type 53 is not defined in draft-ietf-lisp-lcaf-05]
[Severity level: Error]
[Group: Protocol]
Locator Record 1, RLOC: 52:54:00:1e:ad:00, Unreachable, Priority/Weight: 1/100, Multicast Priority/Weight: 1/100
Priority: 1
Weight: 100
Multicast Priority: 1
Multicast Weight: 100
Flags: 0x0000
0000 0000 0000 0... = Reserved: 0x0000
.... .... .... .0.. = Local: Not set
.... .... .... ..0. = Probe: Not set
.... .... .... ...0 = Reachable: Not set
AFI: 802 (includes all 802 media plus Ethernet) (6)
Locator: 52:54:00:1e:ad:00
Border-2#debug lisp control-plane all All LISP control debugging is on at verbose level Border-2#debug l2lisp all All L2Lisp debugging is on *Oct 24 16:02:17.854: LISP[TRNSP]-0: Processing received Encap-Control(8) message on GigabitEthernet1/0/3 from 10.47.1.12:4342 to 10.47.1.11:4342. *Oct 24 16:02:17.854: LISP[TRNSP]-0: Processing received Map-Request(1) message on GigabitEthernet1/0/3 from 10.47.4.3:4342 to 10.47.4.3:4342. *Oct 24 16:02:17.855: LISP[MR ]-0: Received Map-Request with 1 records, first EID IID 8190 10.47.4.3/32, source EID UNSPEC, nonce 0x3847C91F-0xA966DDEA. *Oct 24 16:02:17.855: LISP[MR ]-0 IID 8190 Eth-ARP: MS EID 10.47.4.3/32: Sending proxy reply to 10.47.1.12.
이제 Edge-1이 10.47.4.3이 5254.001e.ad00이라고 하는 AR(Address Resolution) 요청에 대한 LISP Map-Reply를 받았으므로, Edge-1은 엔드포인트 MAC 주소에 대한 RLOC를 결정하기 위해 다른 LISP Map-Request를 생성합니다
Edge-1#debug lisp control-plane all
Edge-1#debug l2lisp all
*Oct 24 16:19:54.843: LISP[REMT ]-0: Received Map-Reply with nonce 0x37F890B9-0xAC60D2B9, 1 records.
*Oct 24 16:19:54.843: LISP[MS ]-0: This is a Address Resolution message.
*Oct 24 16:19:54.843: LISP[REMT ]-0: Map-Reply nonce matches pending request for IID 8190 EID 10.47.4.3/32, requester 'AR'.
*Oct 24 16:19:54.843: LISP[REMT ]-0: Processing Map-Reply mapping record for IID 8190 Eth-ARP 10.47.4.3/32 LCAF 53, ttl 1440, action none, not authoritative, 1 locator.
*Oct 24 16:19:54.843: LISP[REMT ]-0: 5254.001e.ad00 pri/wei/dID/mID/met/si_type/si_id/si_flg/afn_id=1/100/0/0/4294967295/none/0/UNSPEC/UNSPEC lpr.
*Oct 24 17:11:24.056: LISP[REMT ]-0 IID 8190: Schedule processing of Map-Requests from 'remote EID prefix' in IPv4. *Oct 24 17:11:24.056: LISP[REMT ]-0:
Map Request: Sending request for IID 8190 EID 5254.001e.ad00/48, requester 'remote EID prefix'.>
LISP Control-Plane은 MAC 주소 10.47.4.3에 대한 LISP Map-Request를 수신하고, L2 LISP IID 8190에 대해 이더넷 서버 테이블을 참조하고 MAC-RLOC 바인딩이 포함된 LISP Map-Reply를 전송합니다
Border-1#show monitor capture 1 buff display-filter lisp brief Starting the packet display ........ Press Ctrl + Shift + 6 to exit
250 28.656076 0.0.0.0 -> 0.0.0.0 LISP 176 Encapsulated Map-Request for [8190] 52:54:00:1e:ad:00/48 251 28.658851 10.47.1.10 -> 10.47.1.12 LISP 96 Map-Reply for [8190] 52:54:00:1e:ad:00/48
LISP Map-Request와 Map-Reply를 자세히 살펴볼 수 있습니다
Border-1#show monitor capture 1 buffer display-filter frame.number==250 detailed
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
Frame 250: 176 bytes on wire (1408 bits), 176 bytes captured (1408 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Interface id: 0 (/tmp/epc_ws/wif_to_ts_pipe)
Interface name: /tmp/epc_ws/wif_to_ts_pipe
Encapsulation type: Ethernet (1)
Arrival Time: Oct 24, 2023 17:37:11.647755000 UTC
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1698169031.647755000 seconds
[Time delta from previous captured frame: 0.315724000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 28.656076000 seconds]
Frame Number: 250
Frame Length: 176 bytes (1408 bits)
Capture Length: 176 bytes (1408 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:udp:lisp:ip:udp:lisp]
Ethernet II, Src: 52:54:00:04:84:b1 (52:54:00:04:84:b1), Dst: 52:54:00:0a:42:f3 (52:54:00:0a:42:f3)
Destination: 52:54:00:0a:42:f3 (52:54:00:0a:42:f3)
Address: 52:54:00:0a:42:f3 (52:54:00:0a:42:f3)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 52:54:00:04:84:b1 (52:54:00:04:84:b1)
Address: 52:54:00:04:84:b1 (52:54:00:04:84:b1)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.47.1.12, Dst: 10.47.1.10 <-- Edge-1 RLOC and Border-1 RLOC, respectively
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT)
1100 00.. = Differentiated Services Codepoint: Class Selector 6 (48)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 162
Identification: 0x75e5 (30181)
Flags: 0x0000
0... .... .... .... = Reserved bit: Not set
.0.. .... .... .... = Don't fragment: Not set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0x2e32 [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.1.12
Destination: 10.47.1.10
User Datagram Protocol, Src Port: 4342, Dst Port: 4342
Source Port: 4342
Destination Port: 4342
Length: 142
Checksum: 0x46f1 [unverified]
[Checksum Status: Unverified]
[Stream index: 4]
[Timestamps]
[Time since first frame: 0.000000000 seconds]
[Time since previous frame: 0.000000000 seconds]
Locator/ID Separation Protocol
1000 .... .... .... .... .... = Type: Encapsulated Control Message (8)
.... 0... .... .... .... .... .... .... = S bit (LISP-SEC capable): Not set
.... .0.. .... .... .... .... .... .... = D bit (DDT-originated): Not set
.... ..00 0000 0000 0000 0000 0000 0000 = Reserved bits: 0x0000000
Internet Protocol Version 4, Src: 0.0.0.0, Dst: 0.0.0.0
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT)
1100 00.. = Differentiated Services Codepoint: Class Selector 6 (48)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 130
Identification: 0x75e4 (30180)
Flags: 0x0000
0... .... .... .... = Reserved bit: Not set
.0.. .... .... .... = Don't fragment: Not set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0x44c7 [validation disabled]
[Header checksum status: Unverified]
Source: 0.0.0.0
Destination: 0.0.0.0
User Datagram Protocol, Src Port: 4342, Dst Port: 4342
Source Port: 4342
Destination Port: 4342
Length: 110
Checksum: 0x18bb [unverified]
[Checksum Status: Unverified]
[Stream index: 5]
[Timestamps]
[Time since first frame: 0.000000000 seconds]
[Time since previous frame: 0.000000000 seconds]
Locator/ID Separation Protocol
0001 .... .... .... .... .... = Type: Map-Request (1)
.... 0100 00.. .... .... .... = Flags: 0x10
.... 0... .... .... .... .... = A bit (Authoritative): Not set
.... .1.. .... .... .... .... = M bit (Map-Reply present): Set
.... ..0. .... .... .... .... = P bit (Probe): Not set
.... ...0 .... .... .... .... = S bit (Solicit-Map-Request): Not set
.... .... 0... .... .... .... = p bit (Proxy ITR): Not set
.... .... .0.. .... .... .... = s bit (SMR-invoked): Not set
.... .... ..00 0000 000. .... = Reserved bits: 0x000
.... .... .... .... ...0 0000 = ITR-RLOC Count: 0
Record Count: 1
Nonce: 0x86438e956066d3ca
Source EID AFI: LISP Canonical Address Format (LCAF) (16387)
Source EID: [8190] 00:00:0c:9f:f3:41
LCAF: Instance ID: 8190, Address: 00:00:0c:9f:f3:41
LCAF Header: 00000220000c
Reserved bits: 0x00
Flags: 0x00
Type: Instance ID (2)
Reserved bits: 0x20
Length: 12
Instance ID: 8190
Address AFI: 802 (includes all 802 media plus Ethernet) (6)
Address: 00:00:0c:9f:f3:41 (00:00:0c:9f:f3:41)
ITR-RLOC 1: 10.47.1.12
ITR-RLOC AFI: IPv4 (1)
ITR-RLOC Address: 10.47.1.12
Map-Request Record 1: [8190] 52:54:00:1e:ad:00/48 <-- Map-Request for this specific MAC address
Reserved: 0x00
Prefix Length: 48
Prefix AFI: LISP Canonical Address Format (LCAF) (16387)
Prefix: [8190] 52:54:00:1e:ad:00
LCAF: Instance ID: 8190, Address: 52:54:00:1e:ad:00
LCAF Header: 00000220000c
Reserved bits: 0x00
Flags: 0x00
Type: Instance ID (2)
Reserved bits: 0x20
Length: 12
Instance ID: 8190
Address AFI: 802 (includes all 802 media plus Ethernet) (6)
Address: 52:54:00:1e:ad:00 (52:54:00:1e:ad:00)
Map-Reply Record
Mapping Record 1, EID Prefix: [8190] 00:00:0c:9f:f3:41/48, TTL: 1440, Action: No-Action, Authoritative
Record TTL: 1440
Locator Count: 1
EID Mask Length: 48
000. .... .... .... = Action: No-Action (0)
...1 .... .... .... = Authoritative bit: Set
.... .000 0000 0000 = Reserved: 0x000
0000 .... .... .... = Reserved: 0x0
.... 0000 0000 0000 = Mapping Version: 0
EID Prefix AFI: LISP Canonical Address Format (LCAF) (16387)
EID Prefix: [8190] 00:00:0c:9f:f3:41
LCAF: Instance ID: 8190, Address: 00:00:0c:9f:f3:41
LCAF Header: 00000220000c
Reserved bits: 0x00
Flags: 0x00
Type: Instance ID (2)
Reserved bits: 0x20
Length: 12
Instance ID: 8190
Address AFI: 802 (includes all 802 media plus Ethernet) (6)
Address: 00:00:0c:9f:f3:41 (00:00:0c:9f:f3:41)
Locator Record 1, Local RLOC: 10.47.1.12, Reachable, Priority/Weight: 10/10, Multicast Priority/Weight: 10/10
Priority: 10
Weight: 10
Multicast Priority: 10
Multicast Weight: 10
Flags: 0x0005
0000 0000 0000 0... = Reserved: 0x0000
.... .... .... .1.. = Local: Set
.... .... .... ..0. = Probe: Not set
.... .... .... ...1 = Reachable: Set
AFI: IPv4 (1)
Locator: 10.47.1.12
Border-1#show monitor capture 1 buffer display-filter frame.number==251 detailed
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
Frame 251: 96 bytes on wire (768 bits), 96 bytes captured (768 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Interface id: 0 (/tmp/epc_ws/wif_to_ts_pipe)
Interface name: /tmp/epc_ws/wif_to_ts_pipe
Encapsulation type: Ethernet (1)
Arrival Time: Oct 24, 2023 17:37:11.650530000 UTC
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1698169031.650530000 seconds
[Time delta from previous captured frame: 0.002775000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 28.658851000 seconds]
Frame Number: 251
Frame Length: 96 bytes (768 bits)
Capture Length: 96 bytes (768 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:udp:lisp]
Ethernet II, Src: 00:00:00:00:00:00 (00:00:00:00:00:00), Dst: 00:00:00:00:00:00 (00:00:00:00:00:00)
Destination: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.47.1.10, Dst: 10.47.1.12 <-- Border-1 RLOC, Edge-1 RLOC, respectively
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT)
1100 00.. = Differentiated Services Codepoint: Class Selector 6 (48)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 82
Identification: 0x12a9 (4777)
Flags: 0x0000
0... .... .... .... = Reserved bit: Not set
.0.. .... .... .... = Don't fragment: Not set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0x91be [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.1.10
Destination: 10.47.1.12
User Datagram Protocol, Src Port: 4342, Dst Port: 4342
Source Port: 4342
Destination Port: 4342
Length: 62
Checksum: 0xd63e [unverified]
[Checksum Status: Unverified]
[Stream index: 4]
[Timestamps]
[Time since first frame: 0.002775000 seconds]
[Time since previous frame: 0.002775000 seconds]
Locator/ID Separation Protocol
0010 .... .... .... .... .... = Type: Map-Reply (2)
.... 0... .... .... .... .... = P bit (Probe): Not set
.... .0.. .... .... .... .... = E bit (Echo-Nonce locator reachability algorithm enabled): Not set
.... ..0. .... .... .... .... = S bit (LISP-SEC capable): Not set
.... ...0 0000 0000 0000 0000 = Reserved bits: 0x00000
Record Count: 1
Nonce: 0x86438e956066d3ca
Mapping Record 1, EID Prefix: [8190] 52:54:00:1e:ad:00/48, TTL: 1440, Action: No-Action, Not Authoritative
Record TTL: 1440
Locator Count: 1
EID Mask Length: 48
000. .... .... .... = Action: No-Action (0)
...0 .... .... .... = Authoritative bit: Not set
.... .000 0000 0000 = Reserved: 0x000
0000 .... .... .... = Reserved: 0x0
.... 0000 0000 0000 = Mapping Version: 0
EID Prefix AFI: LISP Canonical Address Format (LCAF) (16387)
EID Prefix: [8190] 52:54:00:1e:ad:00
LCAF: Instance ID: 8190, Address: 52:54:00:1e:ad:00
LCAF Header: 00000220000c
Reserved bits: 0x00
Flags: 0x00
Type: Instance ID (2)
Reserved bits: 0x20
Length: 12
Instance ID: 8190
Address AFI: 802 (includes all 802 media plus Ethernet) (6)
Address: 52:54:00:1e:ad:00 (52:54:00:1e:ad:00)
Locator Record 1, RLOC: 10.47.1.13, Reachable, Priority/Weight: 10/10, Multicast Priority/Weight: 10/10
Priority: 10
Weight: 10
Multicast Priority: 10
Multicast Weight: 10
Flags: 0x0001
0000 0000 0000 0... = Reserved: 0x0000
.... .... .... .0.. = Local: Not set
.... .... .... ..0. = Probe: Not set
.... .... .... ...1 = Reachable: Set
AFI: IPv4 (1)
Locator: 10.47.1.13 <-- This RLOC owns the MAC address
Border-1#debug lisp control-plane all
Border-1#debug l2lisp all
*Oct 24 18:03:00.361: LISP[TRNSP]-0: Processing received Map-Request(1) message on GigabitEthernet1/0/3 from 0.0.0.0:4342 to 0.0.0.0:4342. *Oct 24 18:03:00.361: LISP[MR ]-0: Received Map-Request with 1 records, first EID IID 8190 5254.001e.ad00/48, source EID 0000.0c9f.f341, nonce 0xAD90C521-0x348A478D. *Oct 24 18:03:00.361: LISP[MR ]-0 IID 8190 MAC: MS EID 5254.001e.ad00/48: Sending proxy reply to 10.47.1.12.
Edge-1이 Border-1에서 LISP 맵 회신 수신
Edge-1#debug lisp control-plane all
Edge-1#debug l2lisp all
*Oct 24 17:11:24.558: LISP[TRNSP]-0: Processing received Map-Reply(2) message on GigabitEthernet1/0/1 from 10.47.1.10:4342 to 10.47.1.12:4342. *Oct 24 17:11:24.558: LISP[REMT ]-0: Received Map-Reply with nonce 0x38A78BA8-0xC378149D, 1 records. *Oct 24 17:11:24.558: LISP[REMT ]-0: Map-Reply nonce matches pending request for IID 8190 EID 5254.001e.ad00/48, requester 'remote EID prefix'. *Oct 24 17:11:24.558: LISP[REMT ]-0: Processing Map-Reply mapping record for IID 8190 MAC 5254.001e.ad00/48 LCAF 2, ttl 1440, action none, not authoritative, 1 locator. *Oct 24 17:11:24.559: LISP[REMT ]-0: 10.47.1.13 pri/wei/dID/mID/met/si_type/si_id/si_flg/afn_id=10/10/0/0/4294967295/none/0/UNSPEC/UNSPEC lpR.
LISP/SISF 교환을 통한 전체 ARP 요청은 CPU EPC를 통해 Edge-1에서 볼 수 있습니다
Edge-1#show monitor capture 1 buffer display-filter "arp.dst.proto_ipv4==10.47.4.3 or lisp" Starting the packet display ........ Press Ctrl + Shift + 6 to exit
120 18.415474 52:54:00:19:93:e9 -> ff:ff:ff:ff:ff:ff ARP 60 Who has 10.47.4.3? Tell 10.47.4.2 <-- Broadcast ARP Request punted up to the CPU 121 18.416092 10.47.4.3 -> 10.47.4.3 LISP 114 Encapsulated Map-Request for Unknown LCAF Type (53)/32 <-- LISP Map-Request to obtain the MAC address of 10.47.4.3 135 19.598041 10.47.1.11 -> 10.47.1.12 LISP 96 Map-Reply for Unknown LCAF Type (53)/32 <-- LISP Map-Reply providing the MAC address of 10.47.4.3 136 19.613072 0.0.0.0 -> 0.0.0.0 LISP 176 Encapsulated Map-Request for [8190] 52:54:00:1e:ad:00/48 <-- LISP Map-Request to obtain the RLOC for MAC address 5254.001e.ad00 138 20.119722 10.47.1.10 -> 10.47.1.12 LISP 96 Map-Reply for [8190] 52:54:00:1e:ad:00/48 <-- LISP Map-Reply for the RLOC that owns MAC address 5254.001e.ad00 143 20.477618 52:54:00:19:93:e9 -> 52:54:00:1e:ad:00 ARP 60 Who has 10.47.4.3? Tell 10.47.4.2 <-- Unicast ARP Request injected down from the CPU
Edge-1의 컨트롤 플레인이 통합되면 맵 캐시 엔트리와 SISF RMT(Remote Entry)가 있습니다
Edge-1#show lisp instance-id 8190 ethernet map-cache 5254.001e.ad00
LISP MAC Mapping Cache for LISP 0 EID-table Vlan 1026 (IID 8190), 1 entries
5254.001e.ad00/48, uptime: 00:06:26, expires: 23:53:34, via map-reply, complete
Sources: map-reply
State: complete, last modified: 00:06:26, map-source: 10.47.1.13
Active, Packets out: 11(0 bytes), counters are not accurate (~ 00:00:00 ago)
Encapsulating dynamic-EID traffic
Locator Uptime State Pri/Wgt Encap-IID
10.47.1.13 00:06:26 up 10/10 -
Last up-down state change: 00:06:26, state change count: 1
Last route reachability change: 2w0d, state change count: 1
Last priority / weight change: never/never
RLOC-probing loc-status algorithm:
Last RLOC-probe sent: 00:06:25 (rtt 1104ms)
Edge-1#show device-tracking database address 10.47.4.3
Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created
Preflevel flags (prlvl):
0001:MAC and LLA match 0002:Orig trunk 0004:Orig access
0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned
0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
RMT 10.47.4.3 5254.001e.ad00 L2LI0 1026 0005 7mn STALE try 0 731 s
그런 다음 유니캐스트 ARP 요청이 CPU에서 아래로 주입됩니다. CPU 주입 패킷은 이그레스 방향으로 캡처할 수 없습니다. 물리적 인터페이스의 EPC, SPAN(Switchport Port Analyzer) 또는 수신 패브릭 에지 노드의 인그레스 EPC를 사용하여 VXLAN 캡슐화 유니캐스트 ARP 요청의 수신을 확인할 수 있습니다
Edge-2(10.47.1.13)
먼저 LISP 또는 터널 인터페이스가 VLAN 1026의 VLAN ID 출력에 나열되는지 확인합니다
Edge-2#show vlan id 1026 VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1026 red active L2LI0:8190, Gi1/0/3 <-- L2 LISP IID is associated VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2 ---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1026 enet 101026 1500 - - - - - 0 0 Remote SPAN VLAN ---------------- Disabled Primary Secondary Type Ports ------- --------- ----------------- ------------------------------------------
이제 Edge-2의 인그레스 EPC에서 수신된 VXLAN 캡슐화된 ARP 응답을 보여줍니다. 유니캐스트 ARP 요청이 VXLAN에서 캡슐화되었으므로 IP ACL을 활용하여 Edge-2 RLOC에 대한 Edge-1 RLOC 전송(각각 10.47.1.12에서 10.47.1.13으로 전송)과 일치시킴으로써 트래픽을 필터링할 수 있습니다.
Edge-2(config)#ip access-list extended tac Edge-2(config-ext-nacl)#permit ip host 10.47.1.12 host 10.47.1.13
Edge-2#monitor capture 1 interface g1/0/1 in access-list tac Edge-2#monitor capture 1 interface g1/0/2 in access-list tac Edge-2#monitor capture 1 start Started capture point : 1 Edge-2#monitor capture 1 stop Capture statistics collected at software: Capture duration - 20 seconds Packets received - 10 Packets dropped - 0 Packets oversized - 0 Number of Bytes dropped at asic not collected Capture buffer will exists till exported or cleared Stopped capture point : 1
Edge-2#show monitor capture 1 buffer brief Starting the packet display ........ Press Ctrl + Shift + 6 to exit 1 0.000000 52:54:00:19:93:e9 -> 52:54:00:1e:ad:00 ARP 110 Who has 10.47.4.3? Tell 10.47.4.2
이 ARP 요청을 자세히 검사하면 VXLAN 캡슐화, UDP 헤더 및 기타 헤더가 있음을 알 수 있습니다. ARP 프레임이 작으므로 일반적으로 60바이트입니다.
Edge-2#show monitor capture 1 buffer display-filter frame.number==1 detailed
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
Frame 1: 110 bytes on wire (880 bits), 110 bytes captured (880 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Interface id: 0 (/tmp/epc_ws/wif_to_ts_pipe)
Interface name: /tmp/epc_ws/wif_to_ts_pipe
Encapsulation type: Ethernet (1)
Arrival Time: Oct 24, 2023 18:57:34.642468000 UTC
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1698173854.642468000 seconds
[Time delta from previous captured frame: 0.000000000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 0.000000000 seconds]
Frame Number: 1
Frame Length: 110 bytes (880 bits)
Capture Length: 110 bytes (880 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:udp:vxlan:eth:ethertype:arp]
Ethernet II, Src: 52:54:00:0a:42:11 (52:54:00:0a:42:11), Dst: 52:54:00:17:fe:65 (52:54:00:17:fe:65)
Destination: 52:54:00:17:fe:65 (52:54:00:17:fe:65)
Address: 52:54:00:17:fe:65 (52:54:00:17:fe:65)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 52:54:00:0a:42:11 (52:54:00:0a:42:11)
Address: 52:54:00:0a:42:11 (52:54:00:0a:42:11)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.47.1.12, Dst: 10.47.1.13 <-- Edge-1 RLOC and Edge-2 RLOC, respectively
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 96
Identification: 0x798a (31114)
Flags: 0x4000, Don't fragment
0... .... .... .... = Reserved bit: Not set
.1.. .... .... .... = Don't fragment: Set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 253
Protocol: UDP (17)
Header checksum: 0xed8b [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.1.12
Destination: 10.47.1.13
User Datagram Protocol, Src Port: 65354, Dst Port: 4789
Source Port: 65354
Destination Port: 4789
Length: 76
[Checksum: [missing]]
[Checksum Status: Not present]
[Stream index: 0]
[Timestamps]
[Time since first frame: 0.000000000 seconds]
[Time since previous frame: 0.000000000 seconds]
Virtual eXtensible Local Area Network
Flags: 0x8800, GBP Extension, VXLAN Network ID (VNI)
1... .... .... .... = GBP Extension: Defined
.... .... .0.. .... = Don't Learn: False
.... 1... .... .... = VXLAN Network ID (VNI): True
.... .... .... 0... = Policy Applied: False
.000 .000 0.00 .000 = Reserved(R): 0x0000
Group Policy ID: 0
VXLAN Network Identifier (VNI): 8190 <-- LISP L2 IID
Reserved: 0
Ethernet II, Src: 52:54:00:19:93:e9 (52:54:00:19:93:e9), Dst: 52:54:00:1e:ad:00 (52:54:00:1e:ad:00) <-- True source and destination endpoint MAC address
Destination: 52:54:00:1e:ad:00 (52:54:00:1e:ad:00)
Address: 52:54:00:1e:ad:00 (52:54:00:1e:ad:00)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
Address: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: ARP (0x0806)
Trailer: 000000000000000000000000000000000000
Address Resolution Protocol (request)
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
Sender IP address: 10.47.4.2
Target MAC address: 00:00:00:00:00:00 (00:00:00:00:00:00)
Target IP address: 10.47.4.3
Edge-2는 VXLAN 캡슐화를 해제한 다음 추가 처리를 위해 유니캐스트 ARP 요청을 CPU에 적용합니다. 이는 FED Punject 캡처에서 확인할 수 있습니다.
Edge-2#debug platform software fed switch active punt packet-capture start Punt packet capturing started. Edge-2#debug platform software fed switch active punt packet-capture stop Punt packet capturing stopped. Captured 21 packet(s) Edge-2#show platform software fed sw active punt packet-capture display-filter "arp" brief Punt packet capturing: disabled. Buffer wrapping: disabled Total captured so far: 21 packets. Capture capacity : 4096 packets ------ Punt Packet Number: 6, Timestamp: 2023/10/24 19:14:32.930 ------ interface : physical: [if-id: 0x00000000], pal: L2LISP0 [if-id: 0x00000017] metadata : cause: 109 [snoop packets], sub-cause: 1, q-no: 16, linktype: MCP_LINK_TYPE_IP [1] ether hdr : dest mac: 5254.001e.ad00, src mac: 5254.0019.93e9 ether hdr : ethertype: 0x0806 (ARP)
ARP 요청은 ARP 스누퍼 프로세스로 전송됩니다.
Edge-2#debug platform software infrastructure punt
*Oct 24 19:18:38.916: PUNT RX: mcprp_process_receive_packet: pak->vlan_id: 1026 *Oct 24 19:18:38.916: Punt: IP proto src 147.233.10.47, dst 4.2.0.0, from table 0, intf L2LI0, encap LISP, size 60, cause snoop packets(L3) <-- You can see the 10.47.4.2 *Oct 24 19:18:38.916: punt cause:snoop packets invoking reg_invoke_mcprp_punt_feature_msg *Oct 24 19:18:38.916: punt cause:snoop packets MCPRP_PUNT_PAK_PROC_OK_DONE
주의: 이 디버그는 수다스럽습니다. 주의해서 사용하십시오.
이 ARP 요청은 L2 LISP/터널 인터페이스에서 제공되므로 Edge-2는 LISP에서 동적 EID의 로컬 엔드포인트로 10.47.4.2를 학습하지 않습니다
Edge-2#show platform arpsnooping client 5254.0019.93e9 PLAT_DAI : Platform DAI shim FWDPLANE : Dataplane forwarding BRIDGE : Packet to be bridged ARPSN : Arp Snooping Packet Trace for client MAC 5254.0019.93E9: Timestamp Sender Mac Sender IP Target Mac Target IP Opcode VLAN Handler:Action ----------------------- --------------- ------------- ----------------- -------------- ------------ ------- ------------------------------ 2023/10/24 15:57:01.129 5254.0019.93e9 10.47.4.2 0000.0000.0000 10.47.4.3 ARP_REQUEST 1026 PLATF_DAI:RECEIVED INPUT 2023/10/24 15:57:01.129 5254.0019.93e9 10.47.4.2 0000.0000.0000 10.47.4.3 ARP_REQUEST 1026 PLATF_DAI:RECEIVED_TUNNEL 2023/10/24 15:57:01.129 5254.0019.93e9 10.47.4.2 0000.0000.0000 10.47.4.3 ARP_REQUEST 1026 PLATF_DAI:SHUNTED
이제 ARP 요청이 CPU에서 VLAN 1026, 특히 Gi1/0/3으로 주입됩니다. 여기서 10.47.4.3이 연결됩니다.
Edge-2#show mac address-table address 5254.001e.ad00
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1026 5254.001e.ad00 DYNAMIC Gi1/0/3
Total Mac Addresses for this criterion: 1
Edge-2#show platform arpsnooping client 5254.001e.ad00
PLAT_DAI : Platform DAI shim
FWDPLANE : Dataplane forwarding
BRIDGE : Packet to be bridged
ARPSN : Arp Snooping
Packet Trace for client MAC 5254.001E.AD00:
Timestamp Sender Mac Sender IP Target Mac Target IP Opcode VLAN Handler:Action
----------------------- --------------- ------------- ----------------- -------------- ------------ ------- ------------------------------
2023/10/24 15:57:01.129 5254.0019.93e9 10.47.4.2 0000.0000.0000 10.47.4.3 ARP_REQUEST 1026 INJECT:INJ_VLAN_IFINPUT_TO_BDI
2023/10/24 15:57:01.129 5254.0019.93e9 10.47.4.2 0000.0000.0000 10.47.4.3 ARP_REQUEST 1026 INJECT:BD_DPIDX_TO_FWDPLANE
유니캐스트 경로 ARP 회신 상위 레벨 워크플로
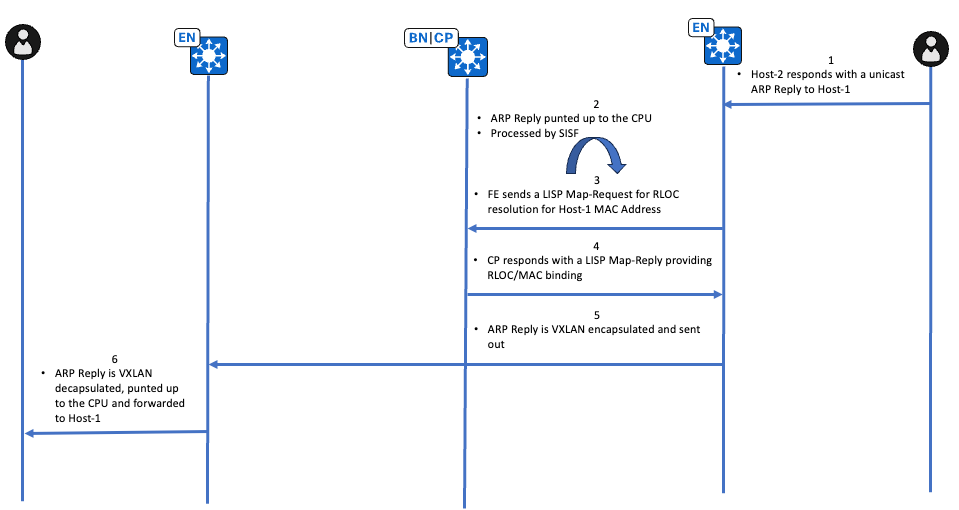
유니캐스트 경로 ARP 회신 확인
Edge-2(10.47.1.13)
10.47.4.3을 소유하는 엔드포인트는 유니캐스트 ARP 회신으로 응답하며, IPDT가 있기 때문에 ARP 회신은 CPU까지 적용됩니다. 엔드포인트를 향하는 인터페이스에서 EPC를 통해 초기 확인이 수행됩니다.
Edge-2#show monitor capture 1 buffer display-filter arp
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
2 88.712035 52:54:00:1e:ad:00 -> 00:00:0c:9f:f3:41 ARP 60 10.47.4.3 is at 52:54:00:1e:ad:00
다음으로, FED Punject로 펀트 동작을 확인합니다.
Edge-2#debug platform software fed sw active punt packet-capture start Punt packet capturing started. Edge-2#debug platform software fed sw active punt packet-capture stop Punt packet capturing stopped. Captured 22 packet(s) Edge-2#show platform software fed sw active punt packet-capture display-filter "arp" brief Punt packet capturing: disabled. Buffer wrapping: disabled Total captured so far: 22 packets. Capture capacity : 4096 packets ------ Punt Packet Number: 6, Timestamp: 2023/10/24 20:32:35.634 ------ interface : physical: [if-id: 0x00000000], pal: L2LISP0 [if-id: 0x00000017] metadata : cause: 109 [snoop packets], sub-cause: 1, q-no: 16, linktype: MCP_LINK_TYPE_IP [1] <-- Punted for Snoop Packets to CPU queue 16 ether hdr : dest mac: 5254.001e.ad00, src mac: 5254.0019.93e9 ether hdr : ethertype: 0x0806 (ARP)
그런 다음 ARP 회신은 ARP 스누퍼 및 디바이스 추적에 전달됩니다
Edge-2#debug platform software infrastructure punt
*Oct 24 19:18:39.101: PUNT RX: mcprp_process_receive_packet: pak->vlan_id: 1026 *Oct 24 19:18:39.101: Punt: IP proto src 173.0.10.47, dst 4.3.82.84, from table 0, intf Gi1/0/3, encap ARPA, size 60, cause snoop packets(L3) <-- 10.47.4.3 is obscured *Oct 24 19:18:39.101: punt cause:snoop packets invoking reg_invoke_mcprp_punt_feature_msg *Oct 24 19:18:39.101: punt cause:snoop packets MCPRP_PUNT_PAK_PROC_OK_DONE
Edge-2#debug platform fhs Edge-2#debug platform fhs all ARP packet received from ARP snooper(Gi1/0/3 10.47.4.3 (5254.001e.ad00) VLAN:10
주의: 이러한 디버그는 수다스럽습니다. 신중하게 사용하십시오.
Edge-2#debug device-tracking
*Oct 24 20:42:22.554: SISF[CLA]: Interest on target vlan 1026 *Oct 24 20:42:22.554: SISF[CLA]: feature Device-tracking *Oct 24 20:42:22.554: SISF[CLA]: feature Address Resolution Relay
*Oct 24 20:42:22.555: SISF[SWI]: Gi1/0/3 vlan 1026 Feature_0 Device-tracking priority 128 *Oct 24 20:42:22.555: SISF[SWI]: Gi1/0/3 vlan 1026 Feature_1 Address Resolution Relay priority 81 *Oct 24 20:42:22.555: SISF[PRS]: ARP-REPLY target set to 10.47.4.2 *Oct 24 20:42:22.556: SISF[SWI]: Gi1/0/3 vlan 1026 Feature Device-tracking rc: OK *Oct 24 20:42:22.556: SISF[ARR]: Gi1/0/3 vlan 1026 Receive a msg in AR *Oct 24 20:42:22.557: SISF[ARR]: Gi1/0/3 vlan 1026 Not ARP Request or NS, return OK *Oct 24 20:42:22.557: SISF[SWI]: Gi1/0/3 vlan 1026 Feature Address Resolution Relay rc: OK *Oct 24 20:42:22.557: SISF[SWI]: Gi1/0/3 vlan 1026 Features execution OK
ARP 회신이 이미 실제 대상 MAC 주소를 가리키므로(Edge-1에서 임시로 표시되는 자리 표시자와 같지 않음) Edge-2는 RLOC-MAC 연결을 확인하기 위해 LISP 맵 요청을 트리거할 수 있습니다.
Edge-2#debug lisp control-plane all
Edge-2#debug l2lisp all
*Oct 24 20:47:34.400: LISP[REMT ]-0 IID 8190: Schedule processing of Map-Requests from 'remote EID prefix' in IPv4. *Oct 24 20:47:34.401: LISP[REMT ]-0: Map Request: Sending request for IID 8190 EID 5254.0019.93e9/48, requester 'remote EID prefix'. *Oct 24 20:47:35.166: LISP[TRNSP]-0: Processing received Map-Reply(2) message on GigabitEthernet1/0/1 from 10.47.1.11:4342 to 10.47.1.13:4342. *Oct 24 20:47:35.166: LISP[REMT ]-0: Received Map-Reply with nonce 0x5879579E-0xCAFC0AA5, 1 records. *Oct 24 20:47:35.166: LISP[REMT ]-0: Processing Map-Reply mapping record for IID 8190 MAC 5254.0019.93e9/48 LCAF 2, ttl 1440, action none, not authoritative, 1 locator. *Oct 24 20:47:35.166: LISP[REMT ]-0: 10.47.1.12 pri/wei/dID/mID/met/si_type/si_id/si_flg/afn_id=10/10/0/0/4294967295/none/0/UNSPEC/UNSPEC lpR.
show lisp instance-id <L2 IID> ethernet map-cache <destination MAC address> 명령을 사용하여 VXLAN 캡슐화를 통해 이 ARP 회신이 전송되는 RLOC를 확인합니다
Edge-2#show lisp instance-id 8190 ethernet map-cache 5254.0019.93e9
LISP MAC Mapping Cache for LISP 0 EID-table Vlan 1026 (IID 8190), 1 entries
5254.0019.93e9/48, uptime: 00:03:45, expires: 23:56:15, via map-reply, complete
Sources: map-reply
State: complete, last modified: 00:03:45, map-source: 10.47.1.12
Active, Packets out: 6(0 bytes), counters are not accurate (~ 00:00:59 ago)
Encapsulating dynamic-EID traffic
Locator Uptime State Pri/Wgt Encap-IID
10.47.1.12 00:03:45 up 10/10 -
Last up-down state change: 00:03:45, state change count: 1
Last route reachability change: 2w0d, state change count: 1
Last priority / weight change: never/never
RLOC-probing loc-status algorithm:
Last RLOC-probe sent: 00:03:45 (rtt 861ms)
LISP 확인 후 ARP 회신은 CPU에서 언더레이의 10.47.1.12 RLOC으로 주입될 수 있습니다
Edge-2#show ip cef 10.47.1.12 10.47.1.12/32 nexthop 10.47.1.2 GigabitEthernet1/0/2 nexthop 10.47.1.6 GigabitEthernet1/0/1
EPC를 통해 Edge-2 CPU에서 전체 플로우를 볼 수 있습니다. ARP 응답과 ARP 요청의 차이점은 이 플로우에 LISP AR 해상도가 없다는 것입니다.
Edge-2#show monitor capture 1 buffer display-filter "arp.src.proto_ipv4==10.47.4.3 or lisp" Starting the packet display ........ Press Ctrl + Shift + 6 to exit 62 9.355185 52:54:00:1e:ad:00 -> 52:54:00:19:93:e9 ARP 60 10.47.4.3 is at 52:54:00:1e:ad:00 <-- ARP Reply punted up to the CPU 63 9.355486 0.0.0.0 -> 0.0.0.0 LISP 176 Encapsulated Map-Request for [8190] 52:54:00:19:93:e9/48 <-- LISP Map-Request to resolve RLOC-MAC association 88 12.058412 10.47.1.10 -> 10.47.1.13 LISP 96 Map-Reply for [8190] 52:54:00:19:93:e9/48 <-- LISP Map-Reply providing the RLOC-MAC association 90 12.072455 52:54:00:1e:ad:00 -> 52:54:00:19:93:e9 ARP 110 10.47.4.3 is at 52:54:00:1e:ad:00 <-- VXLAN Encapsulated ARP Reply that is injected by the CPU
팁: FED Punject 캡처는 삽입된 ARP 응답을 캡처하지 않습니다. 자세한 정보를 보려면 FED 삽입 추적을 사용하십시오.
명령 show platform arpsnooping client <source MAC address>를 사용하여 ARP 회신과 관련하여 Edge-2에서 수행한 작업을 확인할 수 있습니다
Edge-2#show platform arpsnooping client 5254.001e.ad00 PLAT_DAI : Platform DAI shim FWDPLANE : Dataplane forwarding BRIDGE : Packet to be bridged ARPSN : Arp Snooping Packet Trace for client MAC 5254.001E.AD00: Timestamp Sender Mac Sender IP Target Mac Target IP Opcode VLAN Handler:Action ----------------------- --------------- ------------- ----------------- -------------- ------------ ------- ------------------------------
2023/10/24 20:47:38.151 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 PLATF_DAI:RECEIVED INPUT 2023/10/24 20:47:38.151 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 PLATF_DAI:RECEIVED 2023/10/24 20:47:38.152 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 PLATF_DAI:TO_ARPSND 2023/10/24 20:47:38.152 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 PSISF_PRE:PSP_INJNEUTRAL 2023/10/24 20:47:38.152 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 INJECT:INJ_VLAN_IFINPUT_TO_BDI 2023/10/24 20:47:38.152 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 INJECT:BD_DPIDX_TO_FWDPLANE
Edge-1(10.47.1.12)
Edge-1은 VXLAN 캡슐화된 ARP 응답을 수신하고, VXLAN 헤더를 꺼낸 다음 추가 처리를 위해 ARP 응답을 CPU에 적용합니다.
Edge-1#debug platform software infrastructure punt
*Oct 24 21:42:11.303: PUNT RX: mcprp_process_receive_packet: pak->vlan_id: 1026 *Oct 24 21:42:11.303: Punt: IP proto src 173.0.10.47, dst 4.3.82.84, from table 0, intf L2LI0, encap LISP, size 60, cause snoop packets(L3) <-- Can see 10.47.4.3 IP address that has been obscured *Oct 24 21:42:11.303: punt cause:snoop packets invoking reg_invoke_mcprp_punt_feature_msg *Oct 24 21:42:11.303: punt cause:snoop packets MCPRP_PUNT_PAK_PROC_OK_DONE
show platform arpsnooping client <source MAC address> 명령을 사용하여 Edge-1에서 ARP 회신이 처리되는 방식에 대한 추가 정보를 얻을 수 있습니다
Edge-1#show platform arpsnooping client 5254.001e.ad00 PLAT_DAI : Platform DAI shim FWDPLANE : Dataplane forwarding BRIDGE : Packet to be bridged ARPSN : Arp Snooping Packet Trace for client MAC 5254.001E.AD00: Timestamp Sender Mac Sender IP Target Mac Target IP Opcode VLAN Handler:Action ----------------------- --------------- ------------- ----------------- -------------- ------------ ------- ------------------------------
2023/10/24 20:40:33.741 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 PLATF_DAI:RECEIVED INPUT 2023/10/24 20:40:33.741 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 PLATF_DAI:RECEIVED_TUNNEL 2023/10/24 20:40:33.741 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 PLATF_DAI:SHUNTED 2023/10/24 20:40:33.741 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 INJECT:INJ_VLAN_IFINPUT_TO_BDI 2023/10/24 20:40:33.741 5254.001e.ad00 10.47.4.3 5254.0019.93e9 10.47.4.2 ARP_REPLY 1026 INJECT:BD_DPIDX_TO_FWDPLANE
Edge-1은 펀트된 ARP Reply(ARP 회신)를 가져와 VLAN 1026에 ARP Reply(ARP 회신)를 보내고 엔드포인트 10.47.4.2가 있는 포트로 보냅니다
Edge-1#show mac address-table address 5254.0019.93e9
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1026 5254.0019.93e9 DYNAMIC Gi1/0/3
Total Mac Addresses for this criterion: 1
ARP 플러딩(L2 플러딩) 경로
L2 플러딩을 사용하면 패브릭의 모든 패브릭 에지 노드 및 L2 Handoff/IP Directed Broadcast 지원 경계가 공통 언더레이 멀티캐스트 그룹에 조인하는 경우에도 ARP 확인이 발생할 수 있습니다. 플러딩할 수 있는 패킷/프레임이 에지 노드에 도달할 때마다 언더레이 멀티캐스트 그룹의 목적지 IP 주소로 캡슐화된 VXLAN이 됩니다. L2 플러딩은 특정 시나리오에서 ARP 확인에 적용될 수 있습니다.
- 명령 플러드 arp-nd는 VLAN의 L2 LISP 인스턴스에 구성되며, 브로드캐스트 ARP 프레임은 브로드캐스트 언더레이 멀티캐스트 그룹을 사용하여 모든 패브릭 에지에 플러딩됩니다.
- 명령 flood arp-nd는 풀에서 L2 플러딩이 활성화되고 풀이 무선 풀로 표시되지 않는 경우 Cisco Catalyst Center에서 구성됩니다
- 언더레이 멀티캐스트는 LAN 자동화 또는 수동 컨피그레이션을 통해 구성해야 합니다. 패브릭 멀티캐스트 워크플로 중 언더레이 멀티캐스트를 자동으로 구성하는 워크플로는 없습니다.
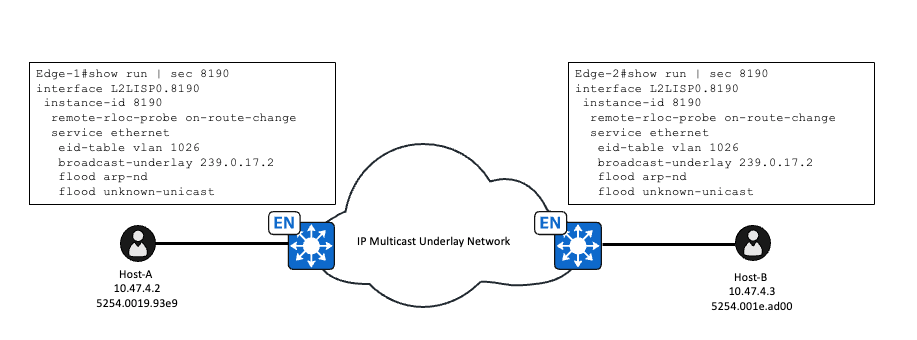
언더레이 멀티캐스트가 구성되고 플러드 arp-nd가 활성화되면, 이는 ARP 요청 처리 방법을 변경하며, 이는 원래 LISP/SISF 기반 해상도를 사용했습니다. 플러드 arp-nd가 L2 LISP 인스턴스에 구성되면 VLAN에 대한 LISP-ARP-RELAY-VLAN IPDT 정책이 비활성화되고 사용되지 않습니다.
Edge-1#show device-tracking policies vlan 1026 Target Type Policy Feature Target range vlan 1026 VLAN DT-PROGRAMMATIC Device-tracking vlan all vlan 1026 VLAN LISP-DT-GLEAN-VLAN-MULTI-IP Device-tracking vlan all
플러딩 경로 ARP 요청 확인
Edge-1(10.47.1.12)
플러드 arp-nd가 구성된 L2 플러딩 지원 VLAN에서 클라이언트에서 ARP 요청을 수신한 후에는 더 이상 ARP 스누핑으로 처리되지 않습니다. ARP 요청은 IPDT 학습 목적이지만 전달을 위한 것은 아닙니다.
ARP 스누퍼는 ARP 요청을 처리하지 않습니다. 이는 show platform arpsnooping client <MAC address> 명령을 통해 확인할 수 있습니다.
Edge-1#show platform arpsnooping client 5254.0019.93e9
PLAT_DAI : Platform DAI shim
FWDPLANE : Dataplane forwarding
BRIDGE : Packet to be bridged
ARPSN : Arp Snooping
Packet Trace for client MAC 5254.0019.93E9:
Timestamp Sender Mac Sender IP Target Mac Target IP Opcode VLAN Handler:Action
----------------------- --------------- ------------- ----------------- -------------- ------------ ------- ------------------------------
Filtered entries counters:
ARPSN_FILTER_SVI: 0
Edge-1은 출력에 표시된 대로 엔드포인트 10.47.4.3에 대한 RMT IPDT 항목을 생성하지 않습니다
Edge-1#show monitor capture 1 buffer display-filter arp brief
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
1 0.000000 52:54:00:19:93:e9 -> ff:ff:ff:ff:ff:ff ARP 60 Who has 10.47.4.3? Tell 10.47.4.2
Edge-1#show device-tracking database address 10.47.4.3
Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created
Preflevel flags (prlvl):
0001:MAC and LLA match 0002:Orig trunk 0004:Orig access
0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned
0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
이제 ARP 요청은 브로드캐스트 언더레이 멀티캐스트 그룹에 캡슐화된 VXLAN입니다. Edge-1에는 Loopback0을 소스로 하는 mroute와 브로드캐스트 언더레이 그룹의 그룹이 있습니다.
Edge-1#show run int lo0 Building configuration... Current configuration : 135 bytes ! interface Loopback0 ip address 10.47.1.12 255.255.255.255 no ip redirects ip pim sparse-mode <-- PIM must be enabled ip router isis clns mtu 1400 end
Edge-1#show ip mroute 239.0.17.2
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 239.0.17.2), 5w1d/00:02:05, RP 10.47.1.14, flags: SJC
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.47.1.4
Outgoing interface list:
L2LISP0.8190, Forward/Sparse-Dense, 01:56:41/00:00:18, flags:
L2LISP0.8192, Forward/Sparse-Dense, 2w2d/00:00:58, flags:
L2LISP0.8188, Forward/Sparse-Dense, 5w1d/00:01:58, flags:
(10.47.1.12, 239.0.17.2), 00:02:53/00:00:06, flags: PFT <-- Lo0 interface of Edge-1
Incoming interface: Null0, RPF nbr 0.0.0.0, <-- Incoming interface Null0 is expected
Outgoing interface list:
GigabitEthernet1/0/2, Forward/Sparse, 00:04:40/00:02:45, flags: <-- Outgoing interface Gig1/0/2 faces the fabric underlay
실제로 플러드 arp-nd는 플러딩이 아니라 IPDT/SISF를 토글합니다. L2 플러딩은 이미 브로드캐스트를 플러딩하지만 트릭은 장치 추적에서 LISP AR 정책을 비활성화하는 것입니다. 이제 ARP 소유권이 해제되어 다른 브로드캐스트와 마찬가지로 플러딩될 수 있습니다.
L2 플러딩에 대한 하드웨어 프로그래밍을 확인하려면 show platform software dpidb l2lisp <L2 LISP IID> 명령을 사용합니다
Edge-1#show platform software dpidb l2lisp 8190 Instance Id:8190, dpidx:25, vlan:1026, Parent Interface:L2LISP0(if_id:23) <-- dpidx value used in the next command
이전 명령의 dpidx 값을 가져와 show platform software fed switch active ifm if-id <dpidx value> 명령에서 사용합니다.
Edge-1#show platform software fed switch active ifm if-id 25 Interface IF_ID : 0x0000000000000019 Interface Name : L2LISP0.8190 Interface Block Pointer : 0x7f65ec85ba78 Interface Block State : READY Interface State : Enabled Interface Status : ADD, UPD Interface Ref-Cnt : 2 Interface Type : L2_LISP Created Time : 2023/09/19 17:57:32.046 Last Modified Time : 2023/10/25 17:59:09.265 Current Time : 2023/10/25 20:15:44.624 Is top interface : FALSE Asic_num : 0 Switch_num : 0 AAL port Handle : 7a00003a Parent interface id : 17 Multicast Tunnel IP : 239.0.17.2 Mcast Tunnel Handle : 0x7f65ed356918 L2 Multicast Tunnel IP : 0.0.0.0 L2 Multicast Vlan Id : 0 L2 Multicast Tunnel Hdl : NULL Vlan Id : 1026 Instance Id : 8190 Dest Port : 4789 SGT : Enable Underlay VRF (V4) : 0 Underlay VRF (V6) : 0 Flood Access-tunnel : Disable Flood unknown ucast : Enable Broadcast : Enable Multicast Flood : Enable L2 Multicast Flood : Disable Host Activity report: Enabled <snip>
Gi1/0/2에서 이그레스 방향으로 EPC를 활용할 수 있습니다. 이 ARP 요청은 CPU 삽입 없이 수신 및 발신 상태이므로 이번에는 이그레스 결정에 EPC 캡처를 신뢰할 수 있습니다.
Edge-1#monitor capture 1 start Started capture point : 1 Edge-1#monitor capture 1 stop Capture statistics collected at software: Capture duration - 22 seconds Packets received - 5 Packets dropped - 0 Packets oversized - 0 Number of Bytes dropped at asic not collected Capture buffer will exists till exported or cleared Stopped capture point : 1
Edge-1#show monitor capture 1 buffer brief Starting the packet display ........ Press Ctrl + Shift + 6 to exit 1 0.000000 52:54:00:19:93:e9 -> ff:ff:ff:ff:ff:ff ARP 110 Who has 10.47.4.3? Tell 10.47.4.2 <-- Size 110 because VXLAN, UDP, and other headers
VXLAN 캡슐화된 ARP 요청을 자세히 살펴볼 수 있습니다
Edge-1#show monitor capture 1 buffer display-filter frame.number==1 detailed
Starting the packet display ........ Press Ctrl + Shift + 6 to exit
Frame 1: 110 bytes on wire (880 bits), 110 bytes captured (880 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Interface id: 0 (/tmp/epc_ws/wif_to_ts_pipe)
Interface name: /tmp/epc_ws/wif_to_ts_pipe
Encapsulation type: Ethernet (1)
Arrival Time: Oct 25, 2023 20:44:36.578645000 UTC
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1698266676.578645000 seconds
[Time delta from previous captured frame: 0.000000000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 0.000000000 seconds]
Frame Number: 1
Frame Length: 110 bytes (880 bits)
Capture Length: 110 bytes (880 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:udp:vxlan:eth:ethertype:arp]
Ethernet II, Src: 00:00:00:00:00:00 (00:00:00:00:00:00), Dst: 00:00:00:00:00:00 (00:00:00:00:00:00) <-- Ignore the all 0s MAC, not accurate
Destination: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.47.1.12, Dst: 239.0.17.2 <-- Source is Edge-1 RLOC, Destination is the broadcast underlay group
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 96
Identification: 0x8dab (36267)
Flags: 0x4000, Don't fragment
0... .... .... .... = Reserved bit: Not set
.1.. .... .... .... = Don't fragment: Set
..0. .... .... .... = More fragments: Not set
Fragment offset: 0
Time to live: 255
Protocol: UDP (17)
Header checksum: 0xe2a3 [validation disabled]
[Header checksum status: Unverified]
Source: 10.47.1.12
Destination: 239.0.17.2
User Datagram Protocol, Src Port: 65280, Dst Port: 4789
Source Port: 65280
Destination Port: 4789
Length: 76
[Checksum: [missing]]
[Checksum Status: Not present]
[Stream index: 0]
[Timestamps]
[Time since first frame: 0.000000000 seconds]
[Time since previous frame: 0.000000000 seconds]
Virtual eXtensible Local Area Network
Flags: 0x8800, GBP Extension, VXLAN Network ID (VNI)
1... .... .... .... = GBP Extension: Defined
.... .... .0.. .... = Don't Learn: False
.... 1... .... .... = VXLAN Network ID (VNI): True
.... .... .... 0... = Policy Applied: False
.000 .000 0.00 .000 = Reserved(R): 0x0000
Group Policy ID: 0
VXLAN Network Identifier (VNI): 8190 <-- L2 LISP IID
Reserved: 0
Ethernet II, Src: 52:54:00:19:93:e9 (52:54:00:19:93:e9), Dst: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff) <-- SMAC and DMAC of the ARP Request
Destination: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff)
Address: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...1 .... .... .... .... = IG bit: Group address (multicast/broadcast)
Source: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
Address: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: ARP (0x0806)
Trailer: 000000000000000000000000000000000000
Address Resolution Protocol (request)
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: 52:54:00:19:93:e9 (52:54:00:19:93:e9)
Sender IP address: 10.47.4.2
Target MAC address: 00:00:00:00:00:00 (00:00:00:00:00:00)
Target IP address: 10.47.4.3
Edge-2(10.47.1.13)
Edge-2는 브로드캐스트 언더레이 그룹인 239.0.17.2에 참여하며 Edge-1에 대해 S,G를 가지고 있으며 Gig1/0/1에서 VXLAN 캡슐화된 멀티캐스트 패킷을 수신합니다. LISP0.8190 하위 인터페이스는 발신 인터페이스 목록에 있습니다. 17.3 이전 버전과 같은 코드 이전 버전에서는 LISP0 하위 인터페이스 대신 터널 인터페이스를 사용합니다.
Edge-2#show ip mroute 239.0.17.2
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 239.0.17.2), 5w1d/stopped, RP 10.47.1.14, flags: SJC
Incoming interface: GigabitEthernet1/0/1, RPF nbr 10.47.1.6
Outgoing interface list:
L2LISP0.8190, Forward/Sparse-Dense, 02:28:57/00:01:02, flags:
L2LISP0.8192, Forward/Sparse-Dense, 2w2d/00:00:32, flags:
L2LISP0.8188, Forward/Sparse-Dense, 5w1d/00:02:54, flags:
(10.47.1.12, 239.0.17.2), 00:00:03/00:02:56, flags: JT
Incoming interface: GigabitEthernet1/0/1, RPF nbr 10.47.1.6 <-- Interface that faces the fabric underlay and the RPF interface towards 10.47.1.12
Outgoing interface list:
L2LISP0.8188, Forward/Sparse-Dense, 00:00:03/00:02:56, flags:
L2LISP0.8192, Forward/Sparse-Dense, 00:00:03/00:02:56, flags:
L2LISP0.8190, Forward/Sparse-Dense, 00:00:03/00:02:56, flags:
Edge-2는 VXLAN 캡슐화된 패킷을 수신하고, VXLAN 헤더를 분리하여 VLAN 1026에 플러딩합니다. 이는 수신 인터페이스의 EPC 및 엔드포인트를 향하는 인터페이스에서 볼 수 있습니다.
Edge-2#monitor capture 1 interface gig1/0/1 in match any Edge-2#monitor capture 1 int g1/0/3 out Edge-2#monitor capture 1 start Started capture point : 1 Edge-2#monitor capture 1 stop Capture statistics collected at software: Capture duration - 22 seconds Packets received - 43 Packets dropped - 0 Packets oversized - 0 Number of Bytes dropped at asic not collected Capture buffer will exists till exported or cleared Stopped capture point : 1 Edge-2#show monitor capture 1 buffer display-filter arp Starting the packet display ........ Press Ctrl + Shift + 6 to exit 10 6.230153 52:54:00:19:93:e9 -> ff:ff:ff:ff:ff:ff ARP 110 Who has 10.47.4.3? Tell 10.47.4.2 <-- Size 110 is the VXLAN encapsulated ARP Request 11 6.404781 52:54:00:19:93:e9 -> ff:ff:ff:ff:ff:ff ARP 60 Who has 10.47.4.3? Tell 10.47.4.2 <-- Size 60 is the original ARP Request
플러딩 경로 ARP 회신 확인
ARP 회신은 불필요한 ARP가 아닌 경우 거의 항상 유니캐스트됩니다. 유니캐스트 ARP 응답의 경우, LISP/SISF 기반 유니캐스트 경로의 워크플로와 플러드 arp-nd 기반 플러딩 경로 사이에는 차이가 없으며 둘 다 SISF/IPDT 탐지를 포함하는 동일한 유니캐스트 경로를 사용합니다. 트러블슈팅을 위해 유니캐스트 경로 ARP 회신 확인 섹션을 활용할 수 있습니다.
개정 이력
| 개정 | 게시 날짜 | 의견 |
|---|---|---|
2.0 |
26-Oct-2023 |
최초 릴리스 |
1.0 |
12-Aug-2020 |
최초 릴리스 |
 피드백
피드백