VPDN 向け RADIUS 認証の設定方法
目次
概要
Virtual Private Dial-up Network(VPDN)を使用すると、プライベート ネットワークのダイヤルイン サービスをリモート アクセス サーバ(L2TP Access Concentrator [LAC] として定義されている)にまで広げることができます。 Point-to-Point Protocol(PPP)クライアントが LAC にダイヤルすると、LAC はその PPP セッションを発信元クライアント用の L2TP Network Server(LNS; L2TP ネットワーク サーバ)に転送する必要があると判断します。続いて、LNS によってユーザが認証され、PPP ネゴシエーションが開始されます。 PPP 設定が完了した後は、すべてのフレームが LAC を経由してクライアントと LNS に送信されます。
この設定例では、VPDN による RADIUS 認証を使用することができます。 LAC は RADIUS サーバにクエリを実行し、ユーザを転送する LNS を決定し、適切なトンネルを確立します。
VPDN の詳細については、VPDN について(英語)を参照してください。
前提条件
要件
このドキュメントに関する固有の要件はありません。
使用するコンポーネント
このドキュメントの情報は、次のソフトウェアとハードウェアのバージョンに基づくものです。
-
Cisco Secure ACS UNIX バージョン 2.x.x 以降または Merit RADIUS
-
Cisco IOS® ソフトウェア リリース 11.2 以降
このドキュメントの情報は、特定のラボ環境にあるデバイスに基づいて作成されたものです。 このドキュメントで使用するすべてのデバイスは、クリアな(デフォルト)設定で作業を開始しています。 ネットワークが稼働中の場合は、コマンドが及ぼす潜在的な影響を十分に理解しておく必要があります。
表記法
ドキュメント表記の詳細は、『シスコ テクニカル ティップスの表記法』を参照してください。
背景説明
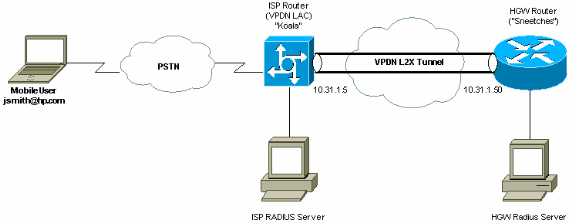
この例では、ユーザは「jsmith@hp.com」、パスワードは「test」とします。 「jsmith@hp.com」が ISP ルータにダイヤルすると、ISP ルータは「hp.com」userid を ISP RADIUS サーバに送信します。 ISP サーバは「hp.com」userid を検索してその tunnel-id("isp")、home gateway(HGW; ホーム ゲートウェイ)ルータ(10.31.1.50)の IP アドレス、Network Access Server(NAS; ネットワーク アクセスサーバ)のパスワード(「hello」)、およびゲートウェイのパスワード(「there」)を ISP ルータに返信します。
ISP ルータはトンネルを開始して、10.31.1.50 HGW ルータに接続し、このルータがローカルでユーザ「hp-gw」を認証して userid「isp」用パスワード(「hello」)を HGW RADIUS サーバに転送します。 トンネルが確立されると、ISP ルータが HGW ルータへの転送を実行し、このユーザのユーザ ダイヤルの userid(「jsmith@hp.com」)とパスワード(「test」)が HGW サーバで認証されます。 この例では、ISP ルータは「Koala」と呼ばれ、HGW ルータは「sneetches」と呼ばれます。
設定
この項では、このドキュメントで説明する機能の設定に必要な情報を提供します。
ネットワーク図
このドキュメントでは、次の図で示されるネットワーク構成を使用しています。
サーバ設定
Merit RADIUS の設定
!--- The RADIUS Server must support Cisco av-pairs. !--- This user is on the ISP RADIUS server. hp.com Password = "cisco" Service-Type = Outbound-User, cisco-avpair = "vpdn:tunnel-id=isp", cisco-avpair = "vpdn:ip-addresses=10.31.1.50", cisco-avpair = "vpdn:nas-password=hello", cisco-avpair = "vpdn:gw-password=there" !--- The next two users are on the HGW Server. isp Password = "hello", Service-Type = Framed, Framed-Protocol = PPP jsmith@hp.com Password = "test", Service-Type = Framed, Framed-Protocol = PPP
Cisco Secure ACS UNIX 2.x.x の設定
!--- This user is on the ISP server.
# ./ViewProfile -p 9900 -u hp.com
User Profile Information
user = hp.com{
profile_id = 86
profile_cycle = 1
RADIUS=Cisco {
check_items= {
2="cisco"
}
reply_attributes= {
9,1="vpdn:tunnel-id=isp"
9,1="vpdn:ip-addresses=10.31.1.50"
9,1="vpdn:NAS-password=hello"
9,1="vpdn:gw-password=there"
}
}
}
!--- The next two users are on the HGW Server.
# ./ViewProfile -p 9900 -u isp
User Profile Information
user = isp{
profile_id = 70
profile_cycle = 1
RADIUS=Cisco {
check_items= {
2="hello"
}
reply_attributes= {
6=2
7=1
}
}
}
# ./ViewProfile -p 9900 -u jsmith@hp.com
User Profile Information
user = jsmith@hp.com{
profile_id = 84
profile_cycle = 1
RADIUS=Cisco {
check_items= {
2="test"
}
reply_attributes= {
6=2
7=1
}
}
}
ルータの設定
| ISP ルータの設定 |
|---|
koala#show running config Building configuration... Current configuration: ! version 11.3 no service password-encryption service udp-small-servers service tcp-small-servers ! hostname koala ! aaa new-model aaa authentication ppp default if-needed RADIUS aaa authorization network default RADIUS aaa accounting network default start-stop RADIUS enable password ww ! vpdn enable !--- VPDN is enabled. ! interface Ethernet0 ip address 10.31.1.5 255.255.255.0 ! interface Serial0 shutdown ! interface Serial1 shutdown ! interface Async1 ip unnumbered Ethernet0 encapsulation ppp async mode dedicated no peer default ip address no cdp enable ppp authentication chap ! ip default-gateway 10.31.1.1 no ip classless ip route 0.0.0.0 0.0.0.0 10.31.1.1 logging trap debugging logging 171.68.118.101 snmp-server community public RW snmp-server enable traps config snmp-server host 171.68.118.105 traps public RADIUS-server host 171.68.120.194 auth-port 1645 acct-port 1646 RADIUS-server key cisco !--- Specify RADIUS server information on the NAS. ! line con 0 password WW line 1 password WW autoselect ppp modem InOut transport input all stopbits 1 speed 115200 flowcontrol hardware line 2 16 autoselect during-login line aux 0 line vty 0 4 exec-timeout 0 0 password WW ! end |
| HGW ルータの設定 |
|---|
Sneetches#show running config Building configuration... Current configuration: ! version 11.3 no service password-encryption service udp-small-servers service tcp-small-servers ! hostname Sneetches ! aaa new-model aaa authentication ppp default RADIUS local aaa authorization network default RADIUS local aaa accounting network default start-stop RADIUS ! username hp-gw password 0 there username isp password 0 hello vpdn enable !--- Enable VPDN. vpdn incoming isp hp-gw virtual-template 1 !--- Specify the remote host (the network access server) !--- the local name (the home gateway) to use for authenticating !--- and the virtual template to use. ! interface Ethernet0 ip address 10.31.1.50 255.255.255.0 ! interface Ethernet1 no ip address shutdown ! interface Virtual-Template1 !--- Create a virtual template interface. ip unnumbered Ethernet0 !--- Un-number the Virtual interface to an available LAN interface. peer default ip address pool async !--- Use the pool "async" to assign the IP address for incoming connections. ppp authentication chap !--- Use CHAP authentication for the incoming connection. ! interface Serial0 shutdown ! interface Serial1 shutdown ! ip local pool async 1.1.1.1 1.1.1.6 ip default-gateway 10.31.1.1 no ip classless ip route 0.0.0.0 0.0.0.0 10.31.1.1 RADIUS-server host 171.68.118.101 auth-port 1645 acct-port 1646 RADIUS-server timeout 20 RADIUS-server key cisco !--- Specify RADIUS server information on the NAS. ! line con 0 exec-timeout 3600 0 line aux 0 line vty 0 4 password WW ! end |
確認
現在、この設定に使用できる確認手順はありません。
トラブルシューティング
ここでは、設定のトラブルシューティングに役立つ情報について説明します。
トラブルシューティングのためのコマンド
特定の show コマンドは、アウトプット インタープリタでサポートされています。このツールを使用すると、show コマンド出力を分析できます。
注: debug コマンドを使用する前に、『debug コマンドに関する重要な情報』を参照してください。
-
debug aaa authentication:AAA/Terminal Access Controller Access Control System Plus(TACACS+)認証に関する情報を表示します。
-
debug aaa authorization:AAA/TACACS+ 許可に関する情報を表示します。
-
debug ppp negotiation - PPP の開始時に送信される PPP パケットを表示します。PPP の開始時には PPP オプションがネゴシエートされます。
-
debug radius - RADIUS に関連する詳細なデバッグ情報を表示します。
-
debug vpdn errors:PPP トンネルの確立を阻止するエラー、または確立されたトンネルをクローズするエラーを表示します。
-
debug vpdn events:通常の PPP トンネル確立またはシャットダウンの一部であるイベントに関するメッセージを表示します。
-
debug vpdn l2f-errors:レイヤ 2 の確立を阻害したり、または通常動作を阻害したりするレイヤ 2 プロトコルのエラーを表示します。
-
debug vpdn l2f-events:レイヤ 2 の通常の PPP トンネル確立またはシャットダウンの一部であるイベントに関するメッセージを表示します。
-
debug vpdn l2f-packets:レイヤ 2 の転送プロコトル ヘッダーとステータスに関するメッセージを表示します。
-
debug vpdn packets:VPDN の通常のトンネル確立またはシャットダウンの一貫で発生するレイヤ 2 トンネル プロトコル エラーおよびイベントを表示します。
-
debug vtemplate:仮想テンプレートからクローニングされた時点から、コールが終了して仮想アクセス インターフェイスがダウン状態になるまでの、仮想アクセス インターフェイスのクローニング情報を表示します。
デバッグ出力
ISP ルータの良いデバッグ例
koala#show debug General OS: AAA Authentication debugging is on AAA Authorization debugging is on AAA Accounting debugging is on VPN: VPN events debugging is on VPN errors debugging is on RADIUS protocol debugging is on koala# %LINK-3-UPDOWN: Interface Async1, changed state to up 17:28:19: VPDN: Looking for tunnel -- hp.com -- 17:28:19: AAA/AUTHEN: create_user (0x15D28C) user='hp.com' ruser='' port='Async1' rem_addr='' authen_type=NONE service=LOGIN priv=0 17:28:19: AAA/AUTHOR/VPDN (982041598): Port='Async1' list='default' service=NET 17:28:19: AAA/AUTHOR/VPDN: (982041598) user='hp.com' 17:28:19: AAA/AUTHOR/VPDN: (982041598) send AV service=ppp 17:28:19: AAA/AUTHOR/VPDN: (982041598) send AV protocol=vpdn 17:28:19: AAA/AUTHOR/VPDN (982041598) found list "default" 17:28:19: AAA/AUTHOR/VPDN: (982041598) Method=RADIUS 17:28:19: RADIUS: authenticating to get author data 17:28:19: RADIUS: Computed extended port value 0:1: 17:28:19: RADIUS: Initial Transmit id 62 171.68.120.194:1645, Access-Request, len 70 17:28:19: Attribute 4 6 0A1F0105 17:28:19: Attribute 5 6 00000001 17:28:19: Attribute 61 6 00000000 17:28:19: Attribute 1 8 68702E63 17:28:19: Attribute 2 18 8070079C 17:28:19: Attribute 6 6 00000005 17:28:19: RADIUS: Received from id 62 171.68.120.194:1645, Access-Accept, len 143 17:28:19: Attribute 26 26 0000000901147670 17:28:19: Attribute 26 36 00000009011E7670 17:28:19: Attribute 26 31 0000000901197670 17:28:19: Attribute 26 30 0000000901187670 !--- These messages can be decrypted using the OI tool. !--- As of Cisco IOS Software Release 12.2(11)T, !--- the output was changed to be readable. 17:28:19: RADIUS: saved authorization data for user 15D28C at 10EE74 17:28:19: RADIUS: cisco AVPair "vpdn:tunnel-id=isp" 17:28:19: RADIUS: cisco AVPair "vpdn:ip-addresses=10.31.1.50" 17:28:19: RADIUS: cisco AVPair "vpdn:nas-password=hello" 17:28:19: RADIUS: cisco AVPair "vpdn:gw-password=there" 17:28:19: AAA/AUTHOR (982041598): Post authorization status = PASS_ADD 17:28:19: AAA/AUTHOR/VPDN: Processing AV service=ppp 17:28:19: AAA/AUTHOR/VPDN: Processing AV protocol=vpdn 17:28:19: AAA/AUTHOR/VPDN: Processing AV tunnel-id=isp 17:28:19: AAA/AUTHOR/VPDN: Processing AV ip-addresses=10.31.1.50 17:28:19: AAA/AUTHOR/VPDN: Processing AV nas-password=hello 17:28:19: AAA/AUTHOR/VPDN: Processing AV gw-password=there 17:28:19: VPDN: Get tunnel info with NAS isp GW hp.com, IP 10.31.1.50 !--- The RADIUS server returns the attributes the !--- NAS should use for the tunnel. !--- Tunnel-id is "ISP" and the IP address of HGW is 10.31.1.50. 17:28:19: AAA/AUTHEN: free_user (0x15D28C) user='hp.com' ruser='' port='Async1' rem_addr='' authen_type=NONE service=LOGIN priv=0 17:28:19: VPDN: Forward to address 10.31.1.50 17:28:19: As1 VPDN: Forwarding... 17:28:19: AAA/AUTHEN: create_user (0x15D334) user='jsmith@hp.com' ruser='' port='Async1' rem_addr='async' authen_type=CHAP service=PPP priv=1 17:28:19: As1 VPDN: Bind interface direction=1 17:28:19: As1 VPDN: jsmith@hp.com is forwarded 17:28:19: AAA/ACCT/NET/START User jsmith@hp.com, Port Async1, List "" 17:28:19: AAA/ACCT/NET: Found list "default" 17:28:19: RADIUS: Computed extended port value 0:1: 17:28:19: RADIUS: Initial Transmit id 63 171.68.120.194:1646, Accounting-Request, len 93 17:28:19: Attribute 4 6 0A1F0105 17:28:19: Attribute 5 6 00000001 17:28:19: Attribute 61 6 00000000 17:28:19: Attribute 1 15 6A736D69 17:28:19: Attribute 40 6 00000001 17:28:19: Attribute 45 6 00000002 17:28:19: Attribute 6 6 00000002 17:28:19: Attribute 44 10 30303030 17:28:19: Attribute 7 6 7670646E 17:28:19: Attribute 41 6 00000000 17:28:19: RADIUS: Received from id 63 171.68.120.194:1646, Accounting-response, len 20 %LINEPROTO-5-UPDOWN: Line protocol on Interface Async1, changed state to up koala# !--- The user finishes and disconnects. %LINEPROTO-5-UPDOWN: Line protocol on Interface Async1, changed state to down %LINK-5-CHANGED: Interface Async1, changed state to reset 17:28:48: As1 VPDN: Cleanup 17:28:48: As1 VPDN: Reset 17:28:48: As1 VPDN: Reset 17:28:48: As1 VPDN: Unbind interface 17:28:48: AAA/ACCT/NET/STOP User jsmith@hp.com, Port Async1: task_id=20 start_time=900759730 timezone=UTC service=vpdn disc-cause=2 disc-cause-ext=1011 pre-bytes-in=-226131998 pre-bytes-out=-1034130241 pre-paks-in=-63570 pre-paks-out=-64410 bytes_in=1999 bytes_out=364 paks_in=29 paks_out=12 pre-session-time=5 elapsed_time=29 data-rate=0 xmit-rate=0 17:28:48: RADIUS: Computed extended port value 0:1: 17:28:48: RADIUS: Initial Transmit id 64 171.68.120.194:1646, Accounting-Request, len 129 17:28:48: Attribute 4 6 0A1F0105 17:28:48: Attribute 5 6 00000001 17:28:48: Attribute 61 6 00000000 17:28:48: Attribute 1 15 6A736D69 17:28:48: Attribute 40 6 00000002 17:28:48: Attribute 45 6 00000002 17:28:48: Attribute 6 6 00000002 17:28:48: Attribute 44 10 30303030 17:28:48: Attribute 7 6 7670646E 17:28:48: Attribute 49 6 00000002 17:28:48: Attribute 42 6 000007CF 17:28:48: Attribute 43 6 0000016C 17:28:48: Attribute 47 6 0000001D 17:28:48: Attribute 48 6 0000000C 17:28:48: Attribute 46 6 0000001D 17:28:48: Attribute 41 6 00000000 17:28:48: RADIUS: Received from id 64 171.68.120.194:1646, Accounting-response, len 20 %LINK-3-UPDOWN: Interface Async1, changed state to down 17:28:51: AAA/AUTHEN: free_user (0x15D334) user='jsmith@hp.com' ruser='' port='Async1' rem_addr='async' authen_type=CHAP service=PPP priv=1 koala#
HGW ルータの良いデバッグ例
Sneetches#show debug General OS: AAA Authentication debugging is on AAA Authorization debugging is on AAA Accounting debugging is on VPN: VPN events debugging is on VPN errors debugging is on RADIUS protocol debugging is on Sneetches# 17:28:21: AAA/AUTHEN: create_user (0x14A914) user='hp-gw' ruser='' port='' rem_addr='' authen_type=CHAP service=PPP priv=1 17:28:21: AAA/AUTHEN/START (496523999): port='' list='default' action=SENDAUTH service=PPP 17:28:21: AAA/AUTHEN/START (496523999): found list default 17:28:21: AAA/AUTHEN/START (496523999): Method=RADIUS 17:28:21: RADIUS: SENDPASS not supported (action=4) 17:28:21: AAA/AUTHEN (496523999): status = ERROR 17:28:21: AAA/AUTHEN/START (496523999): Method=LOCAL 17:28:21: AAA/AUTHEN (496523999): status = PASS 17:28:21: AAA/AUTHEN: free_user (0x14A914) user='hp-gw' ruser='' port='' rem_addr='' authen_type=CHAP service=PPP priv=1 17:28:21: AAA/AUTHEN: create_user (0x14A914) user='isp' ruser='' port='' rem_addr='' authen_type=CHAP service=PPP priv=1 17:28:21: AAA/AUTHEN/START (3095573082): port='' list='default' action=SENDAUTH service=PPP 17:28:21: AAA/AUTHEN/START (3095573082): found list default 17:28:21: AAA/AUTHEN/START (3095573082): Method=RADIUS 17:28:21: RADIUS: SENDPASS not supported (action=4) 17:28:21: AAA/AUTHEN (3095573082): status = ERROR 17:28:21: AAA/AUTHEN/START (3095573082): Method=LOCAL 17:28:21: AAA/AUTHEN (3095573082): status = PASS 17:28:21: AAA/AUTHEN: free_user (0x14A914) user='isp' ruser='' port='' rem_addr='' authen_type=CHAP service=PPP priv=1 17:28:21: AAA/AUTHEN: create_user (0x14ADB4) user='isp' ruser='' port='' rem_addr='' authen_type=CHAP service=PPP priv=1 17:28:21: AAA/AUTHEN/START (3506257139): port='' list='default' action=LOGIN service=PPP 17:28:21: AAA/AUTHEN/START (3506257139): found list default 17:28:21: AAA/AUTHEN/START (3506257139): Method=RADIUS 17:28:21: RADIUS: Initial Transmit id 53 171.68.118.101:1645, Access-Request, len 68 17:28:21: Attribute 4 6 0A1F0132 17:28:21: Attribute 61 6 00000000 17:28:21: Attribute 1 5 69737003 17:28:21: Attribute 3 19 10C82B7A 17:28:21: Attribute 6 6 00000002 17:28:21: Attribute 7 6 00000001 17:28:21: RADIUS: Received from id 53 171.68.118.101:1645, Access-Accept, len 32 17:28:21: Attribute 6 6 00000002 17:28:21: Attribute 7 6 00000001 17:28:21: AAA/AUTHEN (3506257139): status = PASS 17:28:21: VPDN: Chap authentication succeeded for isp 17:28:21: AAA/AUTHEN: free_user (0x14ADB4) user='isp' ruser='' port='' rem_addr='' authen_type=CHAP service=PPP priv=1 17:28:21: Vi1 VPDN: Virtual interface created for jsmith@hp.com 17:28:21: Vi1 VPDN: Set to Async interface 17:28:21: Vi1 VPDN: Clone from Vtemplate 1 filterPPP=0 blocking %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to up 17:28:23: Vi1 VPDN: Bind interface direction=2 17:28:23: Vi1 VPDN: PPP LCP accepted sent & rcv CONFACK 17:28:23: AAA/AUTHEN: create_user (0x143368) user='jsmith@hp.com' ruser='' port='Virtual-Access1' rem_addr='async' authen_type=CHAP service=PPP priv=1 17:28:23: AAA/AUTHEN/START (637397616): port='Virtual-Access1' list='' action=LOGIN service=PPP 17:28:23: AAA/AUTHEN/START (637397616): using "default" list 17:28:23: AAA/AUTHEN/START (637397616): Method=RADIUS 17:28:23: RADIUS: Computed extended port value 0:60100: 17:28:23: RADIUS: Initial Transmit id 54 171.68.118.101:1645, Access-Request, len 78 17:28:23: Attribute 4 6 0A1F0132 17:28:23: Attribute 5 6 0000EAC4 17:28:23: Attribute 1 15 6A736D69 17:28:23: Attribute 3 19 186C2AC9 17:28:23: Attribute 6 6 00000002 17:28:23: Attribute 7 6 00000001 17:28:23: RADIUS: Received from id 54 171.68.118.101:1645, Access-Accept, len 32 17:28:23: Attribute 6 6 00000002 17:28:23: Attribute 7 6 00000001 17:28:23: AAA/AUTHEN (637397616): status = PASS 17:28:23: AAA/AUTHOR/LCP Vi1: Authorize LCP 17:28:23: AAA/AUTHOR/LCP Vi1 (1528831370): Port='Virtual-Access1' list='' service=NET 17:28:23: AAA/AUTHOR/LCP: Vi1 (1528831370) user='jsmith@hp.com' 17:28:23: AAA/AUTHOR/LCP: Vi1 (1528831370) send AV service=ppp 17:28:23: AAA/AUTHOR/LCP: Vi1 (1528831370) send AV protocol=lcp 17:28:23: AAA/AUTHOR/LCP (1528831370) found list "default" 17:28:23: AAA/AUTHOR/LCP: Vi1 (1528831370) Method=RADIUS 17:28:23: AAA/AUTHOR (1528831370): Post authorization status = PASS_REPL 17:28:23: AAA/AUTHOR/LCP Vi1: Processing AV service=ppp 17:28:23: AAA/ACCT/NET/START User jsmith@hp.com, Port Virtual-Access1, List "" 17:28:23: AAA/ACCT/NET: Found list "default" 17:28:23: AAA/AUTHOR/FSM Vi1: (0): Can we start IPCP? 17:28:23: AAA/AUTHOR/FSM Vi1 (4249637449): Port='Virtual-Access1' list='' service=NET 17:28:23: AAA/AUTHOR/FSM: Vi1 (4249637449) user='jsmith@hp.com' 17:28:23: AAA/AUTHOR/FSM: Vi1 (4249637449) send AV service=ppp 17:28:23: AAA/AUTHOR/FSM: Vi1 (4249637449) send AV protocol=ip 17:28:23: AAA/AUTHOR/FSM (4249637449) found list "default" 17:28:23: AAA/AUTHOR/FSM: Vi1 (4249637449) Method=RADIUS 17:28:23: AAA/AUTHOR (4249637449): Post authorization status = PASS_REPL 17:28:23: AAA/AUTHOR/FSM Vi1: We can start IPCP 17:28:23: RADIUS: Computed extended port value 0:60100: 17:28:23: RADIUS: Initial Transmit id 55 171.68.118.101:1646, Accounting-Request, len 87 17:28:23: Attribute 4 6 0A1F0132 17:28:23: Attribute 5 6 0000EAC4 17:28:23: Attribute 1 15 6A736D69 17:28:23: Attribute 40 6 00000001 17:28:23: Attribute 45 6 00000001 17:28:23: Attribute 6 6 00000002 17:28:23: Attribute 44 10 30303030 17:28:23: Attribute 7 6 00000001 17:28:23: Attribute 41 6 00000000 17:28:23: RADIUS: Received from id 55 171.68.118.101:1646, Accounting-response, len 20 17:28:23: AAA/AUTHOR/IPCP Vi1: Start. Her address 0.0.0.0, we want 0.0.0.0 17:28:23: AAA/AUTHOR/IPCP Vi1: Processing AV service=ppp 17:28:23: AAA/AUTHOR/IPCP Vi1: Authorization succeeded 17:28:23: AAA/AUTHOR/IPCP Vi1: Done. Her address 0.0.0.0, we want 0.0.0.0 17:28:23: AAA/AUTHOR/IPCP Vi1: Start. Her address 0.0.0.0, we want 1.1.1.1 17:28:23: AAA/AUTHOR/IPCP Vi1: Processing AV service=ppp 17:28:23: AAA/AUTHOR/IPCP Vi1: Authorization succeeded 17:28:23: AAA/AUTHOR/IPCP Vi1: Done. Her address 0.0.0.0, we want 1.1.1.1 17:28:24: AAA/AUTHOR/IPCP Vi1: Start. Her address 1.1.1.1, we want 1.1.1.1 17:28:24: AAA/AUTHOR/IPCP Vi1 (923857566): Port='Virtual-Access1' list='' service=NET 17:28:24: AAA/AUTHOR/IPCP: Vi1 (923857566) user='jsmith@hp.com' 17:28:24: AAA/AUTHOR/IPCP: Vi1 (923857566) send AV service=ppp 17:28:24: AAA/AUTHOR/IPCP: Vi1 (923857566) send AV protocol=ip 17:28:24: AAA/AUTHOR/IPCP: Vi1 (923857566) send AV addr*1.1.1.1 17:28:24: AAA/AUTHOR/IPCP (923857566) found list "default" 17:28:24: AAA/AUTHOR/IPCP: Vi1 (923857566) Method=RADIUS 17:28:24: AAA/AUTHOR (923857566): Post authorization status = PASS_REPL 17:28:24: AAA/AUTHOR/IPCP Vi1: Reject 1.1.1.1, using 1.1.1.1 17:28:24: AAA/AUTHOR/IPCP Vi1: Processing AV service=ppp 17:28:24: AAA/AUTHOR/IPCP Vi1: Processing AV addr*1.1.1.1 17:28:24: AAA/AUTHOR/IPCP Vi1: Authorization succeeded 17:28:24: AAA/AUTHOR/IPCP Vi1: Done. Her address 1.1.1.1, we want 1.1.1.1 %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up Sneetches# !--- The user finishes and disconnects. Sneetches# 17:28:50: Vi1 VPDN: Reset 17:28:50: Vi1 VPDN: Reset %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to down 17:28:50: Vi1 VPDN: Cleanup 17:28:50: Vi1 VPDN: Reset 17:28:50: Vi1 VPDN: Reset 17:28:50: Vi1 VPDN: Unbind interface 17:28:50: Vi1 VPDN: Reset 17:28:50: Vi1 VPDN: Reset 17:28:50: AAA/ACCT/NET/STOP User jsmith@hp.com, Port Virtual-Access1: task_id=14 start_time=900759731 timezone=UTC service=ppp protocol=ip addr=1.1.1.1 disc-cause=2 disc-cause-ext=1011 pre-bytes-in=0 pre-bytes-out=42 pre-paks-in=0 pre-paks-out=2 bytes_in=882 bytes_out=356 paks_in=17 paks_out=11 pre-session-time=0 elapsed_time=27 data-rate=0 xmit-rate=0 17:28:50: RADIUS: Computed extended port value 0:60100: 17:28:50: RADIUS: Initial Transmit id 56 171.68.118.101:1646, Accounting-Request, len 129 17:28:50: Attribute 4 6 0A1F0132 17:28:50: Attribute 5 6 0000EAC4 17:28:50: Attribute 1 15 6A736D69 17:28:50: Attribute 40 6 00000002 17:28:50: Attribute 45 6 00000001 17:28:50: Attribute 6 6 00000002 17:28:50: Attribute 44 10 30303030 17:28:50: Attribute 7 6 00000001 17:28:50: Attribute 8 6 01010101 17:28:50: Attribute 49 6 00000002 17:28:50: Attribute 42 6 00000372 17:28:50: Attribute 43 6 00000164 17:28:50: Attribute 47 6 00000011 17:28:50: Attribute 48 6 0000000B 17:28:50: Attribute 46 6 0000001B 17:28:50: Attribute 41 6 00000000 17:28:50: RADIUS: Received from id 56 171.68.118.101:1646, Accounting-response, len 20 17:28:50: AAA/AUTHEN: free_user (0x143368) user='jsmith@hp.com' ruser='' port='Virtual-Access1' rem_addr='async' authen_type=CHAP service=PPP priv=1 %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to down Sneetches#
ISP ルータで失敗した接続のデバッグ
koala#show debug General OS: AAA Authentication debugging is on AAA Authorization debugging is on AAA Accounting debugging is on VPN: VPN events debugging is on VPN errors debugging is on RADIUS protocol debugging is on koala# !--- Problem 1: !--- User hp.com is not in the ISP server: !--- There is no output on HGW router because the call has not gone that far. RADIUS: Received from id 83 171.68.120.194:1645, Access-Reject, len 20 18:43:18: AAA/AUTHEN (4063976505): status = FAIL !--- Problem 2: !--- User hp.com is not in the ISP server. !--- There is no output on HGW router because !--- the call has not gone that far. RADIUS: Received from id 83 171.68.120.194:1645, Access-Reject, len 20 18:43:18: AAA/AUTHEN (4063976505): status = FAIL !--- Problem 3: !--- Problem in tunnel definition on HGW router; in HGW configuration !--- vpdn incoming hp-gw isp virtual-template 1 is inserted !--- instead of vpdn incoming isp hp-gw virtual-template 1. %VPDN-5-UNREACH: L2F HGW 10.31.1.50 is unreachable VPDN: Timeout opening tunnel to 10.31.1.50 VPDN: Free busy address 10.31.1.50 !--- Problem 4: !--- User "isp" or "hp-gw" is removed from HGW router. %VPDN-6-AUTHENFAIL: L2F NAS koala, authentication failure for tunnel hp-gw; Invalid key !--- Problem 5: !--- User "isp" is not in the HGW server. %VPDN-6-AUTHENFAIL: L2F HGW , AAA authentication failure for tunnel hp-gw !--- Problem 6: !--- User jsmith@hp.com is not in the HGW server. %VPDN-6-AUTHENFAIL: L2F HGW hp-gw, AAA authentication failure for As1 user jsmith@hp.com; Authentication failure
HGW ルータで失敗した接続のデバッグ
Sneetches#show debug General OS: AAA Authentication debugging is on AAA Authorization debugging is on AAA Accounting debugging is on VPN: VPN events debugging is on VPN errors debugging is on RADIUS protocol debugging is on Sneetches# !--- Problem 1: !--- Problem in tunnel definition on the HGW router; in HGW configuration !--- vpdn incoming hp-gw isp virtual-template 1 is inserted !--- instead of vpdn incoming isp hp-gw virtual-template 1 !--- debug vpdn l2f-errors display. 19:25:27: L2F: Couldn't find tunnel named isp 19:25:30: L2F: Couldn't find tunnel named isp !--- Problem 2: !--- User "isp" is removed from the HGW router. AAA/AUTHEN (3372073334): SENDAUTH no password for isp AAA/AUTHEN (3372073334): status = ERROR AAA/AUTHEN/START (3372073334): no methods left to try AAA/AUTHEN (3372073334): status = ERROR AAA/AUTHEN/START (3372073334): failed to authenticate !--- Problem 3: !--- User "hp-gw" is removed from the HGW router. AAA/AUTHEN (3999868118): SENDAUTH no password for hp-gw AAA/AUTHEN (3999868118): status = ERROR AAA/AUTHEN/START (3999868118): no methods left to try AAA/AUTHEN (3999868118): status = ERROR AAA/AUTHEN/START (3999868118): failed to authenticate !--- Problem 4: !--- User "isp" is removed from HGW RADIUS server. RADIUS: Received from id 107 171.68.118.101:1645, Access-Reject, len 46 Attribute 18 26 41757468 AAA/AUTHEN (2759462034): status = FAIL VPDN: Chap authentication failed for isp %VPDN-6-AUTHENFAIL: L2F HGW , AAA authentication failure for tunnel isp !--- Problem 5: !--- User "jsmith@hp.com" is not in the HGW server. RADIUS: Received from id 109 171.68.118.101:1645, Access-Reject, len 46 Attribute 18 26 41757468 AAA/AUTHEN (2765235576): status = FAIL %VPDN-6-AUTHENFAIL: L2F HGW hp-gw, AAA authentication failure for Vi1 user jsmith@hp.com; Authentication failure
 フィードバック
フィードバック