Introduzione
In questo documento viene descritto come testare la connettività dell'infrastruttura tra due VTEP (Virtual Tunnel End Point) nella VLAN (Virtual Extensible LAN).
Prerequisiti
Requisiti
Cisco raccomanda la conoscenza dei seguenti argomenti:
- Software Nexus NX-OS
- Border Gateway Protocol (BGP)
- VxLAN
Componenti usati
Il riferimento delle informazioni contenute in questo documento è Cisco Nexus N9K-C93180YC-EX con NXOS versione 10.3(3).
Le informazioni discusse in questo documento fanno riferimento a dispositivi usati in uno specifico ambiente di emulazione. Su tutti i dispositivi menzionati nel documento la configurazione è stata ripristinata ai valori predefiniti. Se la rete è operativa, valutare attentamente eventuali conseguenze derivanti dall'uso dei comandi.
Configurazione
Una volta configurata la VxLAN, gli utenti in genere desiderano verificare se funziona come previsto. Sebbene il modo consigliato per eseguire questa operazione sia un test ping tra due host terminali, connessi a VTEP diversi, è anche possibile testare la connettività della struttura utilizzando le interfacce di loopback sui VTEP.

Nota: l'uso dell'interfaccia virtuale dello switch (SVI) come origine o destinazione del test ping non è un test valido per la connettività dell'infrastruttura. Il motivo è che disponiamo della stessa IP sulle SVI fabric a causa della funzionalità di Anycast Gateway.
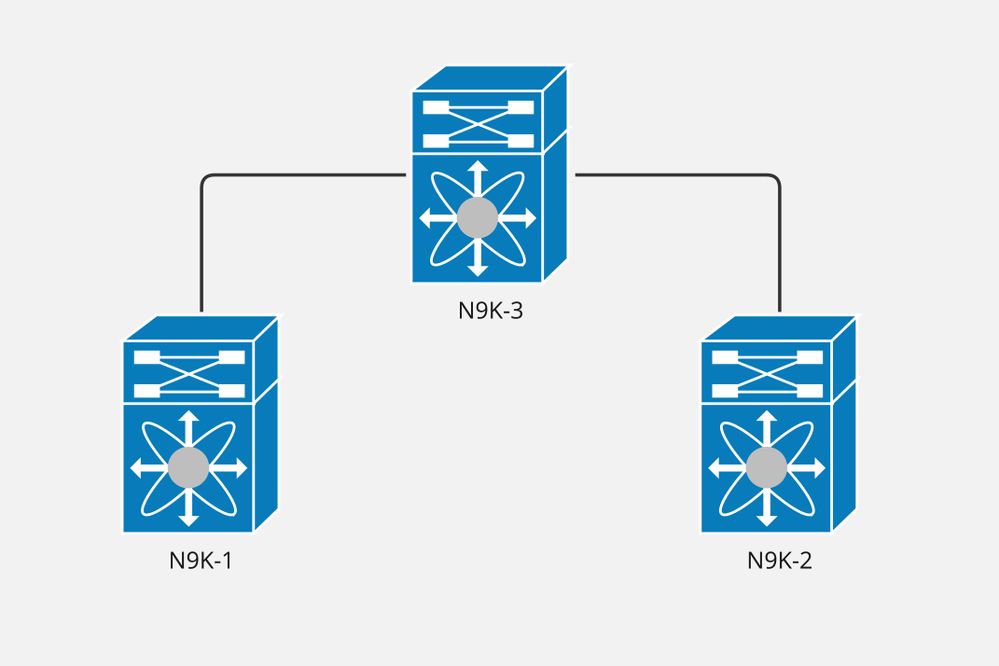
Esempio di rete
Configurazioni
Nexus N9K-2 è configurato come SPINE, mentre N9K-1 e N9K-2 sono configurati come VTEP in questa implementazione VxLAN.
Il layer 3 è esteso, quindi abbiamo un VNI (Virtual Network Interface) di layer 3 su entrambi i VTEP per ciascun VRF (Virtual Routing and Forwarding).
Il VNI di layer 3 configurato per VRF evpn_a è 50100.
N9K-1
Passaggio 1. Il loopback viene configurato come parte del VRF da testare.
N9K-1(config)# interface loopback50
N9K-1(config-if)# vrf member evpn_a
Message reported by command :: vrf member evpn_a
Warning: Deleted all L3 config on interface loopback50
N9K-1(config-if)# ip address 10.255.255.1/32
Passaggio 2. Noi pubblicizziamo questo loopback nel tessuto. In caso contrario, anche se la richiesta ICMP raggiunge un dispositivo di destinazione, la destinazione stessa non sarà in grado di restituire la risposta ICMP.
N9K-1(config)# router bgp 65522
N9K-1(config-router)# vrf evpn_a
N9K-1(config-router-vrf)# address-family ipv4 unicast
N9K-1(config-router-vrf-af)# network 10.255.255.1/32
N9K-2
Passaggio 1. Il loopback viene configurato come parte del VRF da testare.
N9K-2(config)# interface loopback50
N9K-2(config-if)# vrf member evpn_a
Message reported by command :: vrf member evpn_a
Warning: Deleted all L3 config on interface loopback50
N9K-2(config-if)# ip address 10.255.255.2/32
Passaggio 2. Noi pubblicizziamo questo loopback nel tessuto. In caso contrario, anche se la richiesta ICMP raggiunge un dispositivo di destinazione, la destinazione stessa non sarà in grado di restituire la risposta ICMP.
N9K-2(config)# router bgp 65522
N9K-2(config-router)# vrf evpn_a
N9K-2(config-router-vrf)# address-family ipv4 unicast
N9K-2(config-router-vrf-af)# network 10.255.255.2/32
Verifica
Passaggio 1. Verificare che il loopback sia presente nella tabella BGP locale per la famiglia di indirizzi IPv4 Unicast.
N9K-1# show ip bgp 10.255.255.1/32 vrf evpn_a
BGP routing table information for VRF evpn_a, address family IPv4 Unicast
BGP routing table entry for 10.255.255.1/32, version 732
Paths: (1 available, best #1)
Flags: (0x80c0002) (high32 0x000020) on xmit-list, is not in urib, exported
vpn: version 1053, (0x00000000100002) on xmit-list
Multipath: eBGP iBGP
Advertised path-id 1, VPN AF advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop, is extd
AS-Path: NONE, path locally originated
0.0.0.0 (metric 0) from 0.0.0.0 (10.2.254.100)
Origin IGP, MED not set, localpref 100, weight 32768
Extcommunity: RT:65522:50100
VRF advertise information:
Path-id 1 not advertised to any peer
VPN AF advertise information:
Path-id 1 not advertised to any peer
N9K-2# show ip bgp 10.255.255.2/32 vrf evpn_a
BGP routing table information for VRF evpn_a, address family IPv4 Unicast
BGP routing table entry for 10.255.255.2/32, version 241
Paths: (1 available, best #1)
Flags: (0x80c0002) (high32 0x000020) on xmit-list, is not in urib, exported
vpn: version 417, (0x00000000100002) on xmit-list
Multipath: eBGP iBGP
Advertised path-id 1, VPN AF advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop, is extd
AS-Path: NONE, path locally originated
0.0.0.0 (metric 0) from 0.0.0.0 (10.2.254.100)
Origin IGP, MED not set, localpref 100, weight 32768
Extcommunity: RT:65522:50100
VRF advertise information:
Path-id 1 not advertised to any peer
VPN AF advertise information:
Path-id 1 not advertised to any peer
Passaggio 2. Confermare che il loopback sia presente nella tabella BGP locale per la famiglia di indirizzi L2VPN EVPN e venga annunciato ai peer NVE (Network Virtual Interface) previsti.
N9K-1# show bgp l2vpn evpn 10.255.255.1 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.49:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.1]/224, version 36993
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn
Advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop
Gateway IP: 0.0.0.0
AS-Path: NONE, path locally originated
10.2.1.49 (metric 0) from 0.0.0.0 (10.2.0.49)
Origin IGP, MED not set, localpref 100, weight 32768
Received label 50100
Extcommunity: RT:65522:50100 ENCAP:8 Router MAC:a0e0.af67.511d
Path-id 1 advertised to peers:
10.2.0.33 10.2.0.34
N9K-2#
LEAF48# show bgp l2vpn evpn 10.255.255.2 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.48:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.2]/224, version 13373
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn
Advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop
Gateway IP: 0.0.0.0
AS-Path: NONE, path locally originated
10.2.1.48 (metric 0) from 0.0.0.0 (10.2.0.48)
Origin IGP, MED not set, localpref 100, weight 32768
Received label 50100
Extcommunity: RT:65522:50100 ENCAP:8 Router MAC:6cb2.aeee.5a97
Path-id 1 advertised to peers:
10.2.0.33 10.2.0.34
Passaggio 3. È stato ricevuto l'aggiornamento di conferma dal peer NVE remoto.
N9K-1# show bgp l2vpn evpn 10.255.255.2 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.49:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.2]/224, version 36995
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Advertised path-id 1
Path type: internal, path is valid, is best path, no labeled nexthop
Imported from 10.2.0.48:4:[5]:[0]:[0]:[32]:[10.255.255.2]/224
Gateway IP: 0.0.0.0
AS-Path: NONE, path sourced internal to AS
10.2.1.48 (metric 6) from 10.2.0.33 (10.2.0.33)
Origin IGP, MED not set, localpref 100, weight 0
Received label 50100
Extcommunity: RT:65522:50100 Route-Import:10.2.1.147:3100 Source AS:65522:0
ENCAP:8 Router MAC:6cb2.aeee.5a97
Originator: 10.2.0.48 Cluster list: 0.0.255.242
Path-id 1 not advertised to any peer
N9K-2# show bgp l2vpn evpn 10.255.255.1 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.48:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.1]/224, version 13372
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Advertised path-id 1
Path type: internal, path is valid, is best path, no labeled nexthop
Imported from 10.2.0.49:4:[5]:[0]:[0]:[32]:[10.255.255.1]/224
Gateway IP: 0.0.0.0
AS-Path: NONE, path sourced internal to AS
10.2.1.49 (metric 6) from 10.2.0.33 (10.2.0.33)
Origin IGP, MED not set, localpref 100, weight 0
Received label 50100
Extcommunity: RT:65522:50100 Route-Import:10.2.1.49:3100 Source AS:65522:0
ENCAP:8 Router MAC:a0e0.af67.511d
Originator: 10.2.0.49 Cluster list: 0.0.255.242
Path-id 1 not advertised to any peer
Passaggio 4. Verificare che nella tabella di routing sia presente una route per il loopback remoto e che l'hop successivo sia il peer NVE previsto.
N9K-1# show ip route 10.255.255.2 vrf evpn_a
IP Route Table for VRF "evpn_a"
'*' denotes best ucast next-hop
'**' denotes best mcast next-hop
'[x/y]' denotes [preference/metric]
'%
' in via output denotes VRF
10.255.255.2/32, ubest/mbest: 1/0 *via 10.2.1.48%default, [200/0], 00:12:39, bgp-65522, internal, tag 65522, segid: 50100 tunnelid: 0xa020130 encap: VXLAN N9K-2# show ip route 10.255.255.1 vrf evpn_a IP Route Table for VRF "evpn_a" '*' denotes best ucast next-hop '**' denotes best mcast next-hop '[x/y]' denotes [preference/metric] '%
' in via output denotes VRF
10.255.255.1/32, ubest/mbest: 1/0 *via 10.2.1.49%default, [200/0], 00:15:36, bgp-65522, internal, tag 65522, segid: 50100 tunnelid: 0xa020131 encap: VXLAN
Passaggio 5. Inviare una richiesta ICMP al loopback remoto utilizzando come origine il loopback locale.
N9K-1# ping 10.255.255.2 source-interface loopback 50
PING 10.255.255.2 (10.255.255.2): 56 data bytes
64 bytes from 10.255.255.2: icmp_seq=0 ttl=254 time=2.009 ms
64 bytes from 10.255.255.2: icmp_seq=1 ttl=254 time=1.26 ms
64 bytes from 10.255.255.2: icmp_seq=2 ttl=254 time=1.231 ms
64 bytes from 10.255.255.2: icmp_seq=3 ttl=254 time=1.142 ms
64 bytes from 10.255.255.2: icmp_seq=4 ttl=254 time=1.127 ms
--- 10.255.255.2 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 1.127/1.353/2.009 ms
N9K-2# ping 10.255.255.1 source-interface loopback 50
PING 10.255.255.1 (10.255.255.1): 56 data bytes
64 bytes from 10.255.255.1: icmp_seq=0 ttl=254 time=1.47 ms
64 bytes from 10.255.255.1: icmp_seq=1 ttl=254 time=1.396 ms
64 bytes from 10.255.255.1: icmp_seq=2 ttl=254 time=1.327 ms
64 bytes from 10.255.255.1: icmp_seq=3 ttl=254 time=1.451 ms
64 bytes from 10.255.255.1: icmp_seq=4 ttl=254 time=1.366 ms
--- 10.255.255.1 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 1.327/1.402/1.47 ms
Informazioni correlate
Configurazione di VXLAN BGP VPN


 Feedback
Feedback