Introducción
Este documento describe cómo probar la conectividad de fabric entre dos puntos finales de túnel virtual (VTEP) en Virtual Extensible LAN (VxLAN).
Prerequisites
Requirements
Cisco recomienda que tenga conocimiento sobre estos temas:
- Software Nexus NX-OS
- Border Gateway Protocol (BGP)
- VxLAN
Componentes Utilizados
La información de este documento se basa en Cisco Nexus N9K-C93180YC-EX con NXOS versión 10.3(3).
La información que contiene este documento se creó a partir de los dispositivos en un ambiente de laboratorio específico. Todos los dispositivos que se utilizan en este documento se pusieron en funcionamiento con una configuración verificada (predeterminada). Si tiene una red en vivo, asegúrese de entender el posible impacto de cualquier comando.
Configurar
Una vez que VxLAN está configurado, los usuarios normalmente quieren probar si funciona como se espera. Si bien la manera recomendada de hacer esto es hacer una prueba de ping entre dos hosts extremos, que están conectados a diferentes VTEP, también es posible probar la conectividad del fabric mediante interfaces de loopback en los VTEP.

Nota: el uso de la interfaz virtual del switch (SVI) como origen o destino de la prueba de ping no es una prueba válida para la conectividad de fabric. La razón es que tenemos la misma IP en las SVI de fabric gracias a la función Anycast Gateway.
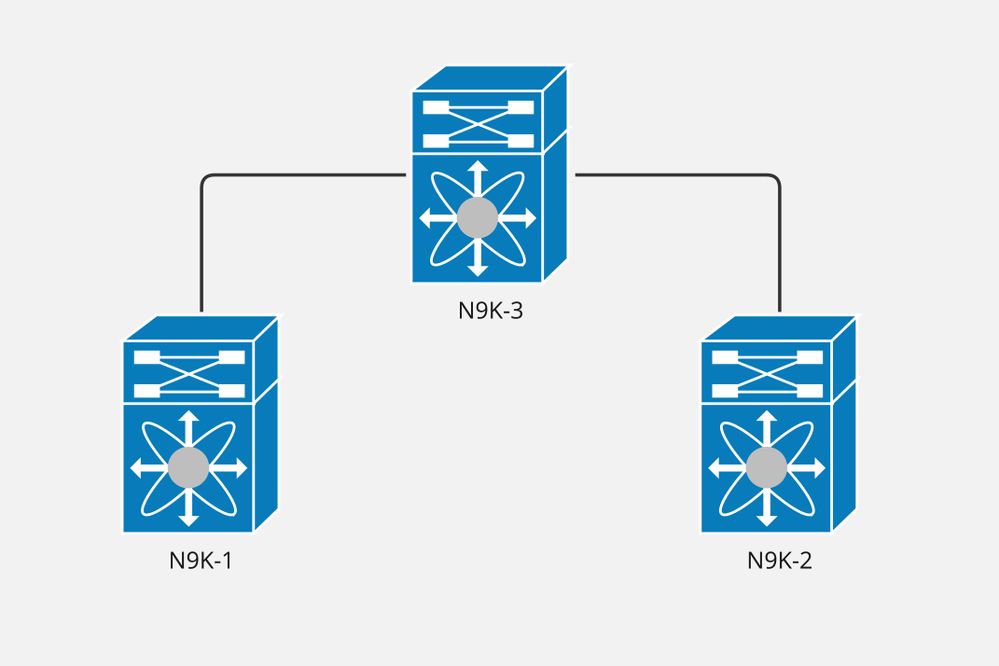
Diagrama de la red
Configuraciones
Nexus N9K-2 se configura como SPINE, mientras que N9K-1 y N9K-2 se configuran como VTEP en esta implementación de VxLAN.
La capa 3 se amplía, por lo que disponemos de una interfaz de red virtual (VNI) de capa 3 en ambos VTEP para cada routing y reenvío virtual (VRF).
El VNI de capa 3 configurado para VRF evpn_a es 50100.
N9K-1
Paso 1. Configuramos un loopback como parte del VRF que queremos probar.
N9K-1(config)# interface loopback50
N9K-1(config-if)# vrf member evpn_a
Message reported by command :: vrf member evpn_a
Warning: Deleted all L3 config on interface loopback50
N9K-1(config-if)# ip address 10.255.255.1/32
Paso 2. Anunciamos este loopback en el fabric. De lo contrario, incluso si la solicitud ICMP llega al destino, el destino mismo no puede devolver la respuesta ICMP.
N9K-1(config)# router bgp 65522
N9K-1(config-router)# vrf evpn_a
N9K-1(config-router-vrf)# address-family ipv4 unicast
N9K-1(config-router-vrf-af)# network 10.255.255.1/32
N9K-2
Paso 1. Configuramos un loopback como parte del VRF que queremos probar.
N9K-2(config)# interface loopback50
N9K-2(config-if)# vrf member evpn_a
Message reported by command :: vrf member evpn_a
Warning: Deleted all L3 config on interface loopback50
N9K-2(config-if)# ip address 10.255.255.2/32
Paso 2. Anunciamos este loopback en el fabric. De lo contrario, incluso si la solicitud ICMP llega al destino, el destino mismo no puede devolver la respuesta ICMP.
N9K-2(config)# router bgp 65522
N9K-2(config-router)# vrf evpn_a
N9K-2(config-router-vrf)# address-family ipv4 unicast
N9K-2(config-router-vrf-af)# network 10.255.255.2/32
Verificación
Paso 1. Confirme que el loopback está presente en la tabla BGP local para la unidifusión IPv4 de la familia de direcciones.
N9K-1# show ip bgp 10.255.255.1/32 vrf evpn_a
BGP routing table information for VRF evpn_a, address family IPv4 Unicast
BGP routing table entry for 10.255.255.1/32, version 732
Paths: (1 available, best #1)
Flags: (0x80c0002) (high32 0x000020) on xmit-list, is not in urib, exported
vpn: version 1053, (0x00000000100002) on xmit-list
Multipath: eBGP iBGP
Advertised path-id 1, VPN AF advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop, is extd
AS-Path: NONE, path locally originated
0.0.0.0 (metric 0) from 0.0.0.0 (10.2.254.100)
Origin IGP, MED not set, localpref 100, weight 32768
Extcommunity: RT:65522:50100
VRF advertise information:
Path-id 1 not advertised to any peer
VPN AF advertise information:
Path-id 1 not advertised to any peer
N9K-2# show ip bgp 10.255.255.2/32 vrf evpn_a
BGP routing table information for VRF evpn_a, address family IPv4 Unicast
BGP routing table entry for 10.255.255.2/32, version 241
Paths: (1 available, best #1)
Flags: (0x80c0002) (high32 0x000020) on xmit-list, is not in urib, exported
vpn: version 417, (0x00000000100002) on xmit-list
Multipath: eBGP iBGP
Advertised path-id 1, VPN AF advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop, is extd
AS-Path: NONE, path locally originated
0.0.0.0 (metric 0) from 0.0.0.0 (10.2.254.100)
Origin IGP, MED not set, localpref 100, weight 32768
Extcommunity: RT:65522:50100
VRF advertise information:
Path-id 1 not advertised to any peer
VPN AF advertise information:
Path-id 1 not advertised to any peer
Paso 2. Confirmar que el loopback está presente en la tabla de BGP local para la familia de direcciones L2VPN EVPN y se anuncia a los peers esperados de la Interfaz Virtual de Red (NVE).
N9K-1# show bgp l2vpn evpn 10.255.255.1 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.49:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.1]/224, version 36993
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn
Advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop
Gateway IP: 0.0.0.0
AS-Path: NONE, path locally originated
10.2.1.49 (metric 0) from 0.0.0.0 (10.2.0.49)
Origin IGP, MED not set, localpref 100, weight 32768
Received label 50100
Extcommunity: RT:65522:50100 ENCAP:8 Router MAC:a0e0.af67.511d
Path-id 1 advertised to peers:
10.2.0.33 10.2.0.34
N9K-2#
LEAF48# show bgp l2vpn evpn 10.255.255.2 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.48:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.2]/224, version 13373
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn
Advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop
Gateway IP: 0.0.0.0
AS-Path: NONE, path locally originated
10.2.1.48 (metric 0) from 0.0.0.0 (10.2.0.48)
Origin IGP, MED not set, localpref 100, weight 32768
Received label 50100
Extcommunity: RT:65522:50100 ENCAP:8 Router MAC:6cb2.aeee.5a97
Path-id 1 advertised to peers:
10.2.0.33 10.2.0.34
Paso 3. Se recibió una actualización de confirmación del par NVE remoto.
N9K-1# show bgp l2vpn evpn 10.255.255.2 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.49:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.2]/224, version 36995
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Advertised path-id 1
Path type: internal, path is valid, is best path, no labeled nexthop
Imported from 10.2.0.48:4:[5]:[0]:[0]:[32]:[10.255.255.2]/224
Gateway IP: 0.0.0.0
AS-Path: NONE, path sourced internal to AS
10.2.1.48 (metric 6) from 10.2.0.33 (10.2.0.33)
Origin IGP, MED not set, localpref 100, weight 0
Received label 50100
Extcommunity: RT:65522:50100 Route-Import:10.2.1.147:3100 Source AS:65522:0
ENCAP:8 Router MAC:6cb2.aeee.5a97
Originator: 10.2.0.48 Cluster list: 0.0.255.242
Path-id 1 not advertised to any peer
N9K-2# show bgp l2vpn evpn 10.255.255.1 vrf evpn_a
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.2.0.48:4 (L3VNI 50100)
BGP routing table entry for [5]:[0]:[0]:[32]:[10.255.255.1]/224, version 13372
Paths: (1 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Advertised path-id 1
Path type: internal, path is valid, is best path, no labeled nexthop
Imported from 10.2.0.49:4:[5]:[0]:[0]:[32]:[10.255.255.1]/224
Gateway IP: 0.0.0.0
AS-Path: NONE, path sourced internal to AS
10.2.1.49 (metric 6) from 10.2.0.33 (10.2.0.33)
Origin IGP, MED not set, localpref 100, weight 0
Received label 50100
Extcommunity: RT:65522:50100 Route-Import:10.2.1.49:3100 Source AS:65522:0
ENCAP:8 Router MAC:a0e0.af67.511d
Originator: 10.2.0.49 Cluster list: 0.0.255.242
Path-id 1 not advertised to any peer
Paso 4. Confirme que haya una ruta para el loopback remoto en la tabla de ruteo y que el salto siguiente sea el par NVE esperado.
N9K-1# show ip route 10.255.255.2 vrf evpn_a
IP Route Table for VRF "evpn_a"
'*' denotes best ucast next-hop
'**' denotes best mcast next-hop
'[x/y]' denotes [preference/metric]
'%
' in via output denotes VRF
10.255.255.2/32, ubest/mbest: 1/0 *via 10.2.1.48%default, [200/0], 00:12:39, bgp-65522, internal, tag 65522, segid: 50100 tunnelid: 0xa020130 encap: VXLAN N9K-2# show ip route 10.255.255.1 vrf evpn_a IP Route Table for VRF "evpn_a" '*' denotes best ucast next-hop '**' denotes best mcast next-hop '[x/y]' denotes [preference/metric] '%
' in via output denotes VRF
10.255.255.1/32, ubest/mbest: 1/0 *via 10.2.1.49%default, [200/0], 00:15:36, bgp-65522, internal, tag 65522, segid: 50100 tunnelid: 0xa020131 encap: VXLAN
Paso 5. Envíe la solicitud ICMP al loopback remoto, utilizando como origen el loopback local.
N9K-1# ping 10.255.255.2 source-interface loopback 50
PING 10.255.255.2 (10.255.255.2): 56 data bytes
64 bytes from 10.255.255.2: icmp_seq=0 ttl=254 time=2.009 ms
64 bytes from 10.255.255.2: icmp_seq=1 ttl=254 time=1.26 ms
64 bytes from 10.255.255.2: icmp_seq=2 ttl=254 time=1.231 ms
64 bytes from 10.255.255.2: icmp_seq=3 ttl=254 time=1.142 ms
64 bytes from 10.255.255.2: icmp_seq=4 ttl=254 time=1.127 ms
--- 10.255.255.2 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 1.127/1.353/2.009 ms
N9K-2# ping 10.255.255.1 source-interface loopback 50
PING 10.255.255.1 (10.255.255.1): 56 data bytes
64 bytes from 10.255.255.1: icmp_seq=0 ttl=254 time=1.47 ms
64 bytes from 10.255.255.1: icmp_seq=1 ttl=254 time=1.396 ms
64 bytes from 10.255.255.1: icmp_seq=2 ttl=254 time=1.327 ms
64 bytes from 10.255.255.1: icmp_seq=3 ttl=254 time=1.451 ms
64 bytes from 10.255.255.1: icmp_seq=4 ttl=254 time=1.366 ms
--- 10.255.255.1 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 1.327/1.402/1.47 ms
Información Relacionada
Configuración de VXLAN BGP EVPN



 Comentarios
Comentarios