Instructions for Addressing the Cisco Secure Boot Hardware Tampering Vulnerability on Cisco ASR 1000 Series Routers
Information about Upgrading ASR 1000 Modular Chassis
Upgrading the router to fix this hardware vulnerability involves two steps:
-
Running an IOS XE tool to fix the vulnerability - As part of this step, download the tool from the Cisco software downloads page. The name of this tool is asr1000rpx86-universalk9.V1612_1_CVE_2019_1649.SPA.bin.This tool installs an IOS XE image on the active and standby RP cards. During installation of this tool, all the RPs, ESP’s and carrier cards are automatically detected and the CPLD version is checked. If the CPLD version is found to be vulnerable to the security vulnerability, the CPLD is automatically upgraded. This IOS XE tool covers the upgrade needs of all the three field replaceable units – Route Processor, Embedded Service Processors and Ethernet Line Cards.
-
Booting the router - To confirm that upgrading was successful and that the vulnerability was fixed, boot the router with the existing IOS XE image and verify the version of CPLD with details given in Table 1.

Note
The platforms that are affected by this hardware vulnerability are listed in Table 1. It is strongly recommended to not run the IOS XE tool on any other platforms. If you are on an ASR 1000 modular chassis and have installed an ASR1000-RP2 module, then the IOS XE tool upgrades the CPLD for rest of the line cards, but skips updating the CPLD for the ASR1000-RP2 module.
Prerequisites for Upgrading FPGA for ASR 1000 Modular Chassis
-
If you are upgrading ASR1000-RP2, download asr1000rpx86-universalk9.V1612_1_CVE_2019_1649.SPA.bin from https://software.cisco.com/download/home/282450665/type/283425232/release/16.0.0 and copy it to the USB or bootflash of the router that is scheduled for upgrade.
If you are upgrading ASR1000-RP3, download asr1000rpx86-universalk9.V1612_1_CVE_2019_1649.SPA.bin from https://software.cisco.com/download/home/286308009/type/283425232/release/16.0.0 and copy it to the USB or bootflash of the router that is scheduled for upgrade.
-
The upgrade procedure is required only if the CPLD version of the FRU is below the recommended version. Before you attempt to upgrade the router, see Checking the CPLD version section for the recommended CPLD version.
-
Run the show platform command and verify the output to ensure that all the FRU’s are in
ok,ok,activeorok,standbystate. -
It is extremely important to ensure there is power redundancy to run the IOS XE tool on all the cards in the chassis. You can check this by using the show platform command.
Figure 1. Example of a show platform command with all modules and FRU's working correctly 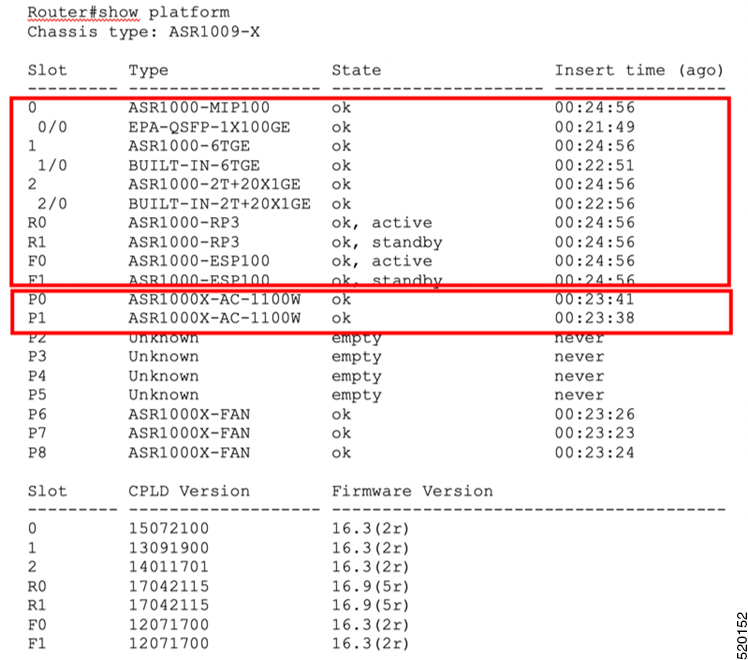
-
Ensure that all the FRU’s are on the latest recommended ROMmon software before triggering the upgrade using the IOS XE tool
-
On a chassis with ASR1000-RP2 the recommended ROMmon version is 16.9(5r). In addition to this, also ensure that the FPGA version is greater than or equal to 17071402. This is required for loading the latest IOS images on the router
-
If you are on ASR1000-RP3, run the show diag slot R0 eeprom command and in the output look for Top Assy. Part Number. If the last part of this value is less than or equal to 05, then a manual power-cycle is required at step 7 of the upgrade procedure.
Router#show diag slot R0 eeprom Slot R0 EEPROM data: Product Identifier (PID) : ASR1000-RP3 Version Identifier (VID) : V03 PCB Serial Number : JAE23110JQJ Top Assy. Part Number : 68-5621-07 Hardware Revision : 1.0 CLEI Code : COUCAVLCAB Router# Router#sh diag slot R1 eeprom Slot R1 EEPROM data: Product Identifier (PID) : ASR1000-RP3 Version Identifier (VID) : V01 PCB Serial Number : JAE204603RL Top Assy. Part Number : 68-5621-05 Hardware Revision : 1.0 CLEI Code : COUCAVBCAA
Upgrading FPGA for ASR 1000 Modular Chassis
 Note |
If you attempt to boot a chassis that has an FRU with an FPGA version that is lower than expected you will see the following error: To resolve this issue, upgrade the FPGA as per details in the following procedure: |
To upgrade FPGA, run the upgrade utility image:
Procedure
| Step 1 |
Confirm that both the RP 0 and RP 1 are in ISSU ready state. This state can be confirmed by using the show redundancy command. |
||||
| Step 2 |
Save the current running configuration and backup it to bootflash. |
||||
| Step 3 |
Note down the configuration register value and change it to |
||||
| Step 4 |
Copy the IOS XE utility to USB or to bootflash: using FTP or TFTP command to both RP slot 0 and RP slot 1: RP Slot 0
RP Slot 1
|
||||
| Step 5 |
Issue the router reload command on RP slot 0 and 1and ensure that the ROMmon prompt is displayed on the router RP Slot 0
RP Slot 1
|
||||
| Step 6 |
RP 0
RP slot 1 |
||||
| Step 7 |
(Optional) Ensure you have physical access to the router and manually power cyle the router. This step is only required if as part of the prerequisite you have determined that the Top Assy. Part Number value is less than 05. |
||||
| Step 8 |
After the CPLD upgrade, boot the router with the previously loaded IOS XE software image. For example : asr1000rpx86-universalk9.16.12.01.SPA.bin |
||||
| Step 9 |
Change the configuration register value to the value noted in step 2 |
Verifying CPLD Upgrade for ASR 1000 Modular Chassis
To verify the FPGA upgrade, use the following command:
Router#show platform
Chassis type: ASR1009-X
Slot Type State Insert time (ago)
--------- ------------------- --------------------- -----------------
0 ASR1000-MIP100 ok 00:33:39
0/0 EPA-QSFP-1X100GE ok 00:30:43
1 ASR1000-6TGE ok 00:33:39
1/0 BUILT-IN-6TGE ok 00:31:40
2 ASR1000-2T+20X1GE ok 00:33:39
2/0 BUILT-IN-2T+20X1GE ok 00:31:38
R0 ASR1000-RP3 ok, active 00:33:39
R1 ASR1000-RP3 ok, standby 00:33:39
F0 ASR1000-ESP100 ok, active 00:33:39
F1 ASR1000-ESP100 ok, standby 00:33:39
P0 ASR1000X-AC-1100W ok 00:32:28
P1 ASR1000X-AC-1100W ok 00:32:26
P2 Unknown empty never
P3 Unknown empty never
P4 Unknown empty never
P5 Unknown empty never
P6 ASR1000X-FAN ok 00:32:17
P7 ASR1000X-FAN ok 00:32:16
P8 ASR1000X-FAN ok 00:32:18
Slot CPLD Version Firmware Version
--------- ------------------- ---------------------------------------
0 19041800 16.3(2r)
1 19041600 16.3(2r)
2 19041600 16.3(2r)
R0 19091111 16.9(5r)
R1 19091111 16.9(5r)
F0 19051700 16.3(2r)
F1 19051700 16.3(2r)
 Note |
Verify the CPLD version with the platforms given in Check the CPLD Version for ASR 1000 Modular Chassis. |
Check the CPLD Version for ASR 1000 Modular Chassis
|
PIDs |
CPLD Versions |
|---|---|
|
ASR1000-RP3 |
19091111 |
|
ASR1000-ESP100 |
19051700 |
|
ASR1000-ESP200 |
19051700 |
|
ASR1000-ESP200-X |
19041811 |
|
ASR1000-ESP100-X |
19041811 |
|
ASR1000-MIP100 |
19041800 |
|
ASR1000-2T+20X1GE |
19041600 |
|
ASR1000-6TGE |
19041600 |
 Note |
Do not perform power cycle or remove the power cable during the upgrade. If there is a power loss during the upgrade, it may result in corruption of the boot image and it may require RMA of the equipment. |
Information about Upgrading Cisco ASR 1000 Consolidated Chassis
This section provides instructions on how to address the Cisco Secure Boot Hardware Tampering Vulnerability on Cisco ASR 1000 consolidated chassis.
 Note |
Complex Programmable Logic Device ( CPLD) is also refered to as Field Programmable Gate Arrays (FPGA) and you find either CPLD or FPGA is used interchangeable in the folloing sections. |
Prerequisites for Upgrading CPLD for ASR 1000 Consolidated Chassis
-
Download the image from the CCO website and copy it to USB or bootflash of the router which is scheduled for the upgrade.
-
Cisco ASR1001, ASR1002, and ASR1002-X Series routers are not affected by this PSIRT.
 Note |
The platforms that are affected by this hardware vulnerability are listed in Table 1. It is strongly recommended to not run the IOS XE tool on any other platforms. |
Upgrading CPLD for ASR 1000 Consolidated Chassis
 Note |
Cisco recommends upgrading CPLD as a solution for the Cisco Secure Boot Hardware Tampering Vulnerability. For more details of the vulnerability and affected products, refer https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190513-secureboot. |
To upgrade CPLD, run the upgrade utility image:
Procedure
| Step 1 |
Copy the utility to USB or to bootflash: using FTP or TFTP. |
||||
| Step 2 |
Save the current running configurations and backup it to bootflash. |
||||
| Step 3 |
Note down the configuration register value and change it to 0x0.. |
||||
| Step 4 |
Issue the router reload command and ensure that the Rommon prompt is displayed on the router. |
||||
| Step 5 |
Initiate the upgrade using the following CLI, and follow the instructions from the tool.
|
||||
| Step 6 |
If the Upgrade is not successful, the following message appears: CPLD image failed to verify correctly !! Retry the upgrade by issuing Yes. |
||||
| Step 7 |
After the retry, if the upgrade still fails, reach out to Cisco TAC for further assistance. |
||||
| Step 8 |
After the upgrade is complete, device power cycles automatically, and the rommon prompt is displayed to boot the IOS image. |
||||
| Step 9 |
Revert back the configuration register value to its original value. |
Verifying CPLd Upgrade for ASR 1000 Consolidated Chassis
To verify the CPLD upgrade, use the following command:
Router#show hw-programmable 0
Hw-programmable versions
Slot CPLD version FPGA version
-----------------------------------------------------------
0 19030215 16051716  Note |
Verify the CPLD version with the platforms given in the CPLD Versions and Images table. |
|
S. No |
Platforms |
CPLD Version |
CCO URL for the CPLD Image |
|---|---|---|---|
|
1 |
ASR1001-X |
19060309 |
|
|
2 |
ASR1002-HX |
19030211 |
|
|
3 |
ASR1001-HX |
19030215 |
 Note |
Do not perform any power cycle or remove the power cable during the FPGA upgrade. If there is a power loss during the upgrade, it may result in corruption of the boot image and it may require RMA of the equipment. |
 Feedback
Feedback