First Published: 2024-03-07
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
New and Changed Information
The following table provides an overview of the significant changes up to the current release. The table does not provide an exhaustive list of all changes or the new features up to this release.
| Feature | Description | Release | Where Documented |
|---|---|---|---|
|
No updates |
There were no major changes from the previous release. |
6.4.1 |
This document is available from your Cisco Nexus Dashboard Insights GUI as well as online at www.cisco.com. For the latest version of this document, visit Cisco Nexus Dashboard Insights Documentation.
Explore
About Explore
Explore analyzes a policy snapshot from the Cisco APIC to enable data center operators and architects to:
-
Explore the ACI object models and associations
-
Verify connectivity and segmentation between network assets
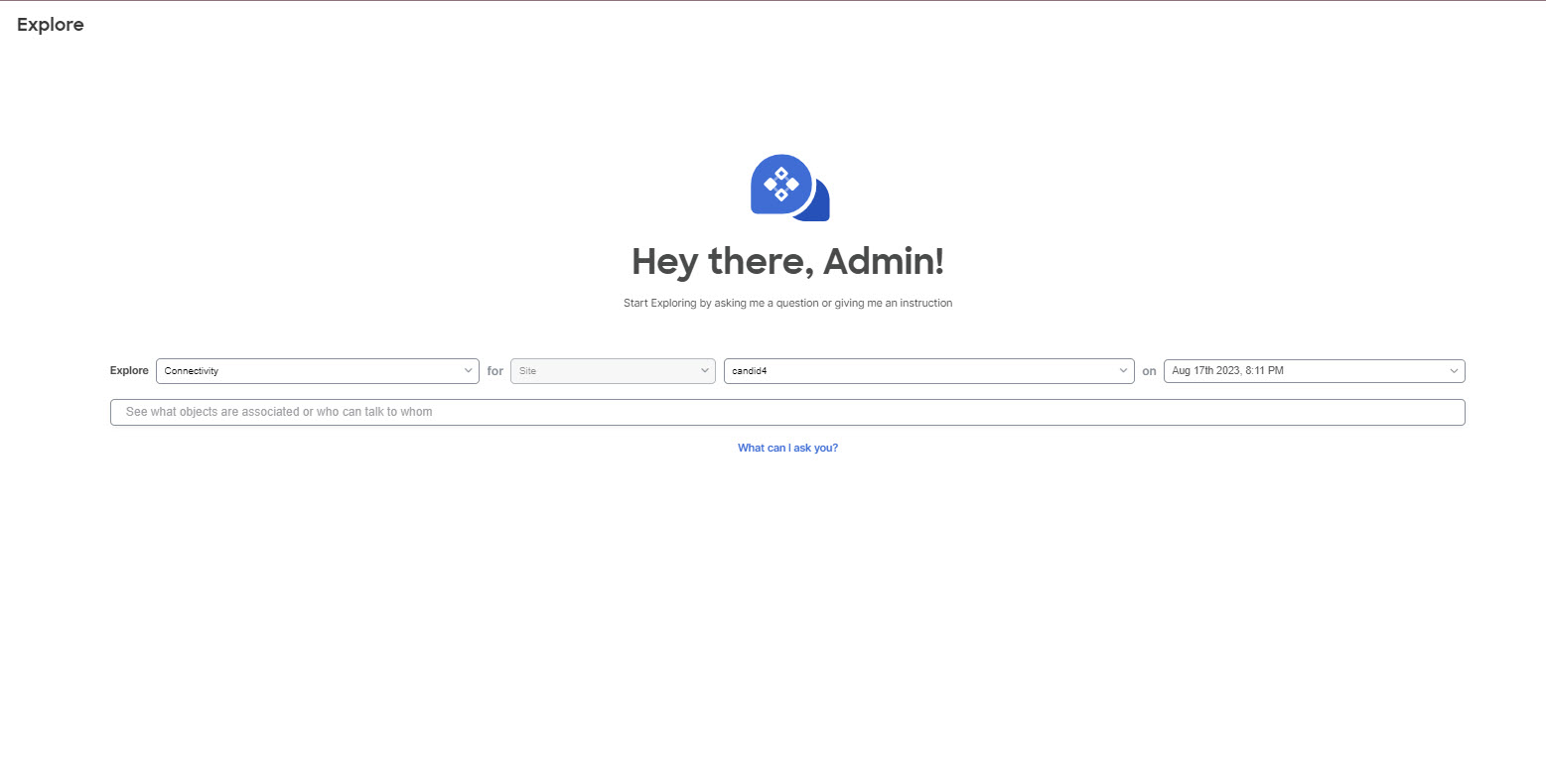
Explore allows network operators to discover assets and their object associations in an easy-to-consume natural language query format. Operators can quickly get visibility into their infrastructure and connectivity or segmentation between assets.
It allows you to select Connectivity or Flow (Beta) on any selected site on a timeline which could be a snapshot of the mode, Latest, Last, Date range, or Time Window.
It also allows operators to easily discover associations between traditional networking constructs such as VRFs, endpoints, and VLANs to the ACI object model.
Explore is based on a natural language query interface. The types of queries supported by the feature include:
-
What Query: Answers how the different networking entities are related to each other.
Examples:
-
What EPGS are associated with VRF: /uni/tn-secure/ctx-secure
-
What EPs are associated with INF: topology/pod-1/paths-101/pathep-[eth1/3] or VRF:uni/tn-secure/ctx-ctx1
-
What EPGs are associated with BD: uni/tn-secure/BD-BD1 and LEAF: :topology/pod-1/node-103
-
-
Can Query: Answers whether the entities in the ACI policy can communicate with each other. Can queries can also be used to determine if the entities in the ACI policy can communicate using protocols such as TCP, UDP, or ICMP and the source and destination ports used for communication.
Example:
-
Can entity A talk to entity B.
-
Can EPG: uni/tn-secure/ap-AP0/epg-B talk to EPG: uni/tn-secure/ap-AP0/epg-A on tcp dport: 80 sport: 10
-
You can also click What Can I ask you? to view the entire list of the pre defined queries. When you click any one of the queries and click Enter, it displays the corresponding details page for that search.
The What and Can queries are supported only for connectivity.
-
View Flows from IP: Query - You start a query with View Flows from IP: followed by the IP address. This displays the details page for that search.
The View Flows from IP: Query is available only for Flow (Beta).
What Can I Ask You?
Click What can I ask you? , to display the page where all possible explore queries are listed. Use this page to determine the list of queries you can explore. Click Get Started button to go back to Explore.
Ask for Associations - An example of such a query would be Can X talk to Y.
Use Cases
-
Design verification: Ad-hoc query model enables operators to quickly understand and reason about their infrastructure. The natural language query model returns search results and associations in an easy to understand tabular format. In a single concise view, operators are able to answer design verification questions or discover deviations from organizational best practices.
-
Lightweight book-keeping: Administration and maintenance teams can provide on demand visibility into the current state of their policy and networking infrastructure allowing inventory, book-keeping, and asset tracking procedures to be lightweight.
-
Connectivity and Segmentation: Easily answer connectivity questions between a pair of assets or containers of assets. For example, if a group of EPGs needs to be quarantined, the Can query can quickly answer if policy has been correctly setup.
Can Query Results
Explore provides a consolidated view of all the security, forwarding, and endpoint issues based on the query.
It enables you to explore the connectivity between entities by creating a query. The Can query determines if the entities can communicate with each other and the health of the connectivity. The How do they talk? area displays the configuration used for communication between the entities and the health of the connectivity.
In Explore, you default to the first site in the selected sites that is found in the header. Choose the latest snapshot for the site, and generate a model. Assuming the model has enough data, you can then start a query by typing into the input box.
The results of the Can query are displayed in the Radial View. The Radial View displays the association view and the connectivity view for a Can query. The default radial view displays the connectivity and the health of the EPGs.
In the association view, you can use the inner and outer radial bands to explore the associations between the different objects.
In the connectivity view, you can use the single radial band to view the prefixes or EPGs as entities.
The View Controls enables you to filter the information displayed in the radial view.
The EPG view displays connectivity information between different EPGs as configured in the APIC policy.
The prefix view displays connectivity information between prefixes as configured in the APIC policy or learnt prefixes.
The object view displays the associations between the different objects such as tenants and VRFs.
The health view displays the health of the connectivity. The connectivity can be healthy or unhealthy.
The different components of the radial view represent different types of information under View Controls:
-
If you select EPGs, Tenants, and Both, the outer ring represents the tenants, the inner ring represents the application profiles, and arced lines in the middle show the health of the contracts.
-
If you select EPGs, VRFs, and Both, the outer ring represents the VRFs, the inner ring represents the bridge domains, and arced lines in the middle show the health of the contracts.
-
If you select Prefixes and VRFs, and Both, the outer ring represents the VRFs, the inner ring represents the bridge domains or L3Outs, and arced lines in the middle show the health of the contracts.
In How do they talk?, the results display in the Connectivity Table, Prefix Table, and Anomalies table.
The connectivity can be healthy or unhealthy. If the connectivity is healthy, using the Connectivity Table you can determine the health of the connectivity.
If the connectivity is unhealthy, you can use the Policy, Forwarding, and Endpoints tabs to determine the possible cause.
Related Policy, Forwarding, and Endpoint information is displayed in a table with associated anomalies.
Policy enables you to explore the security policy issues based on the query.
Forwarding enables you explore a prefix or pair of prefixes issues based on the query.
Endpoints allows you to explore the endpoint issues based on the query.
If the query results are large, the message “The query returned too much data to display” is displayed.
Use the View Controls > Advanced > From EPG and To EPG Search bar to create a more specific query for the results to be displayed.
Can queries containing large associations such as vzAny may timeout. Use the View Controls > Advanced > From EPG and To EPG Search bar to create a more specific query.
For a query between prefixes, if the number of EPGs shared by the prefixes is greater than 25, the Endpoint table fails to load the data and displays an error message. Create an EPG to EPG query to display the results in the Endpoint table.
The possible causes for unhealthy connectivity include security violations, forwarding violations, and endpoint violations.
The color of the flow between the EPG pair indicates the maximum severity of anomalies across Policy, Forwarding, and Endpoints.
-
Red Color indicates critical anomalies
-
Orange color indicates major anomalies
-
Yellow color indicates warning anomalies
For example if the issues are related to security violations, you can use the Connectivity Table, Prefix Table, and Anomalies table to determine the anomalies associated with the security issue.
In the Prefix Table, you can click Subnet/Route to see information regarding the prefixes.
In the Anomalies table you can click the anomaly to determine the objects in your fabric that are affected by the issue. Pass or Fail checks are performed on the anomaly and the suggested steps to resolve the issue are displayed. See Creating a Can Query.
Guidelines and Limitations
-
You can explore for endpoints using the MAC or IP addresses as well.
-
If your searched query falls into a broad category, Explore will show a list of all the items matching that criteria.
-
Explore is case sensitive.
-
In Explore, four active snapshots to explore across all sites is supported. The snapshots can be used for exploration by either the same user or by multiple users. To explore additional snapshots, you must offload an existing snapshot before exploring. In Offload Snapshot From Explore you can select the snapshots to offload. This dialog box displays automatically when you load 4 snapshots in memory.
-
The Explore feature is supported only for IPv4 prefixes.
-
All queries created using the Explore feature are unidirectional.
-
In Explore, if the analysis fails, the error message Analysis has failed is displayed. Download the tech support logs for Explore and contact Cisco TAC to resolve the issue.
-
In Cisco Nexus Dashboard, choose Operations > Tech Support, choose Actions > Collect Tech Support > and choose the appropriate service for Cisco Nexus Dashboard Insights to download the tech support logs.
-
Navigate to /data/services/app_logs/cisco-nir-logger/nae/nae/explorerService/ directory to locate the logs for the Explore feature. If there are multiple Explore instances running, the logs for each instance will be located in a separate directory.
-
nae-policyexplorer-0/explorer.log nae-policyexplorer-1/explorer.log nae-policyexplorer-2/explorer.log nae-policyexplorer-3/explorer.log
-
Prefixes configured under L3extSubnet without their learnt route will not be listed as part of the auto-suggestions when you enter a query in the Search bar.
-
To explore the APIC resources successfully using the Explore feature, the APIC policy must contain either valid endpoints such as fv:CEp or valid EPGs.
-
In Compliance, the policy intent based on contracts is used to determine the compliance.
-
Explore has the following scale limits:
-
On virtual Nexus Dashboard we support snapshots with 100,000 logical rules and 350,000 (Vertices + Edges).
-
On physical Nexus Dashboard we support snapshots with 300,000 logical rules and 1000,000 (Vertices + Edges).
-
Creating a What Query
This query helps answer the question, "What entities are associated with each other?"
-
In the Navigation, click Explorer.
-
In the Timeline select a snapshot for analysis. When you select a snapshot, the data to explore is loaded on demand.
-
Generate a model and when there is enough data, you will be able to type in a query in the input field.
-
In the query selector field, enter a What query. The query must include two groups of one or more entities available in the Search bar. See Supported Queries.
RESULTS
By default, What endpoints are associated with the Any query view. The Query results are displayed on the page, and you can drill further to see the associated entities. You can also add to the source and destination list. (Can source talk to destination?)
In the What entities can talk? area, the radial is displayed with View Controls for additional filtering.
-
Click inside the radial to get more information as required.
-
Click an entity in the Query Results table to view details.
-
Click a number in the results table to view details about the entity in the ACI policy.
Creating a Can Query
The can query will provide information that answers the question, can two entities communicate with each other?
-
In the Navigation, click Explorer.
-
In the Timeline, select a snapshot for analysis. When you select a snapshot, the data to explore is loaded on demand.
-
Generate a model and when there is enough data, perform the following actions.
-
In the query selector field, enter a Can query. The query must include two groups of one or more entities from the ACI policy. For details, see Supported Queries.
An automatic check is performed to see if the source entity can talk to the destination entity. You can click Reverse Query to reverse the source and destination entities for a query.
-
Use View Controls to choose different entities for more information.
See 'Can Query Results' for more details about the query results and the How do they talk? area.
Supported Queries
The following table lists the queries supported by the Explore feature for ACI.
Supported What Queries
| Query | Entity | Operator | Entity |
|---|---|---|---|
|
What BDs are associated with |
|
|
|
|
What ENCAPs are associated with |
|
|
|
|
What EPGs are associated with |
|
|
|
|
What EPs are associated with |
|
|
|
|
What INFs are associated with |
|
|
|
|
What Inventory is associated with |
|
|
|
|
What Leafs are associated with |
|
|
|
|
What VRFs are associated with |
|
|
|
Supported Can Queries
| Query | Entity | Operator | Protocol | Destination Port | Source Port |
|---|---|---|---|---|---|
|
Can BD |
|
On |
|
|
|
|
Can ENCAP |
|
On |
|
|
|
|
Can EP |
|
On |
|
|
|
|
Can EPG |
|
On |
|
|
|
|
Can INF |
|
On |
|
|
|
|
Can LEAF |
|
On |
|
|
|
|
Can VRF |
|
On |
|
|
|
|
Can Subnet |
|
On |
|
|
|
|
Can ANY talk to |
|
— |
— |
— |
— |
The Operator, Protocol, Destination Port, and Source Port are not supported in CAN queries for these ANY entities.
Explore for Nexus Dashboard Orchestrator
Review About Nexus Dashboard Orchestrator Integration prior to reading this section. See Integrations for more information.
The Explore feature in Nexus Dashboard Insights allows network operators to discover assets and their object associations in an easy-to-consume natural language query format. Nexus Dashboard Orchestrator assurance for Explore workflows currently supports a Can EPG talk to EPG query where the query must include two distinct Nexus Dashboard Orchestrator policy entities to view their connectivity.
After you run assurance analyses against the sites in your Nexus Dashboard Orchestrator deployment, you will be able to navigate associations between EPGs, explore EPG to EPG communication, and enable visibility and troubleshooting across sites.
Explore provides you with EPG details from your programmed Nexus Dashboard Orchestrator templates or schemas. You can view which EPG entities can communicate. The entities stretch across the sites. If there are anomalies raised in these connections, those anomalies are also displayed here.
Currently, only Can EPG to EPG queries are supported for Nexus Dashboard Orchestrator assurance. What queries are not supported. For Can EPG to EPG queries, additional filtering based on protocols and port is not supported.
Examples:
-
This is an example of a query that is supported: Can EPG: uni/tn-secure/ap-AP0/epg-B talk to EPG: uni/tn-secure/ap-AP0/epg-A
-
This is an example of a query that is not supported: Can EPG: uni/tn-secure/ap-AP0/epg-B talk to EPG: uni/tn-secure/ap-AP0/epg-A on tcp dport: 80
You can choose from the auto-suggested query-list of all EPGs within the Nexus Dashboard Orchestrator assurance sites. Can query results are available as an aggregated view across all sites within the Nexus Dashboard Orchestrator assurance sites and not per ACI site. All queries are across-site queries, and the maximum severity of assets and associations across all sites is shown in the results.
Guidelines and Limitations for Nexus Dashboard Orchestrator
-
After running your query, when you view the Connectivity Table and the Policy Table, in the Source EPG and Destination EPG columns a shadow tag to an EPG will be displayed if the EPG is a shadow in the corresponding site. For example, <epgname>(shadow). If an EPG is not a shadow, there will be no shadow tag after the EPG name. However, if you have a version of APIC/Nexus Dashboard Orchestrator that does not have the shadow annotation, the shadow tag will not display even for shadow EPGs.
-
In the Endpoints, Forwarding, and the Policy tables, you can click a site for specific anomaly details.
-
The Anomalies table displays individual, aggregated, or inter-site anomalies based on the queries that you have selected.
Use Cases For Nexus Dashboard Orchestrator Assurance of the Explore Workflow
-
Design verification: The impromptu query model enables operators to quickly understand and reason about their infrastructure. The natural language query model returns search results and associations in an easy-to-understand tabular format. In a single concise view, operators can answer design verification questions or discover deviations from organizational best practices.
-
Lightweight book-keeping: Administration and maintenance teams can provide on demand visibility into the current state of their policy and networking infrastructure allowing inventory, book-keeping, and asset tracking procedures to be lightweight.
-
Connectivity and Segmentation: Easily answer connectivity questions between a pair of assets or containers of assets. For example, if a group of EPGs must be quarantined, the Can query can quickly reveal if the policy is correctly setup.
Creating a Can Query in Nexus Dashboard Orchestrator Inter-Site
Complete running assurance analyses against the sites in your Nexus Dashboard Orchestrator deployment.
-
In the Navigation, choose Explorer.
-
In the Explore pane, select Orchestrator. Choose one of the integrations available from the drop down.
-
In the Snapshot field, choose the appropriate snapshot for your analysis. The data to explore is loaded on demand. This enables you to query the specific snapshot you’ve selected.
Nexus Dashboard Orchestrator assurance for Explore workflows currently supports a Can EPG talk to EPG query where the query must include two groups of one or more entities from the Nexus Dashboard Orchestrator policy to check their connectivity.
-
In the Search bar, enter a Can query. The query must include two groups of one or more supported entities. By default, the Any to Any query view is displayed.
-
In the Can Source Talk to Destination area, you can confirm whether source can talk to destination.
-
(Optional) Click Reverse Query to reverse the source and destination entities for a query.
-
In the Which entities Can Talk? area, under View Control, click EPGs to view the communication between the EPGs. The EPG view displays connectivity information between different EPGs.
-
Click the appropriate arrow inside the radial to view further details in the page.
-
In the How do they talk? area, view how the entities communicate with one another.
RESULTS
For a Can Query, the results are displayed in a radial in the Which Entities Can Talk area.
The results display if the queried EPGs can communicate with one another. The color of the arrow represents the maximum severity for the connection. If the query results are large, the message “The query returned too much data to display” is shown.
Select a single resource from the Would you like to check connectivity of a single resource drop-down list to create a specific query. When you click a specific connection in the radial view, you view the details for the connection in the tables that follow.
You can see the policy that is programmed as part of the EPG. You can verify the prefixes that are part of the connection. You can also view which endpoints are affected because of this communication.
For Nexus Dashboard Orchestrator Inter-Site Assurance Explore, the Policy, Forwarding, and Endpoints tables, display an additional Sites column. The connectivity information for each site, that is part of your query, is displayed here. For each of these sites, if there are any anomalies that are generated, you can view them here. For example, as a part of endpoints if there is a Major anomaly, you can click to choose it and click Analyze to view the details for the anomaly.
The details are provided in the Nexus Dashboard Orchestrator context. You can learn what is being programmed by Nexus Dashboard Orchestrator across multiple sites and you can verify the query and check the communication between different EPGs that are used. The inter-site view displays Nexus Dashboard Orchestrator associated Site anomalies.
Supported Queries for Nexus Dashboard Orchestrator
The following table lists the queries that Nexus Dashboard Orchestrator assurance supports for the Explore feature.
Supported Can Queries
| Query | Entity | Operator | Protocol | Destination Port | Source Port |
|---|---|---|---|---|---|
|
Can EPG |
EPG |
— |
— |
— |
— |
|
Can ANY talk to |
|
— |
— |
— |
— |
The Operator Protocol, Destination Port, and Source Port are not supported.
Copyright
THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: http://www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
© 2017-2024 Cisco Systems, Inc. All rights reserved.